VPN SECURITY BETWEEN A CLOUD AND A COMPUTER
 This is related to my earlier question: https://www.experts-exchange.com/questions/27804218/Tracert-Details.html
This is related to my earlier question: https://www.experts-exchange.com/questions/27804218/Tracert-Details.htmlPlease tell if one of my cloud is in australia and other system is in US. Now I want to make a proper security channel between them then how should I proceed. I need to use a VPN. I am studying cloud and I am unable to find a proper answer to a scenario in my mind. What networking part plays a role in it. Shall I be denying any IP address. Shall I be following any encryption method that is public key and private key or shall I be using any firewall VPN setup.
ASKER
There is no onsite server, One laptop or system and one cloud, cloud is made of its own infra.
Now I have to make the connection between the two, the connection is between the computer and the cloud.
I know is this that:-
Authentication
The authentication of virtual private network (VPN) clients by the VPN server is a vital security concern. Authentication takes place at two levels:
1.Computer-level authentication
When Internet Protocol security (IPSec) is used for a Layer Two Tunneling Protocol (L2TP) over IPSec (L2TP/IPSec) VPN connection, computer-level authentication is performed through the exchange of computer certificates or a preshared key during the establishment of the IPSec security association.
2.User-level authentication
Before data can be sent over the Point-to-Point Tunneling Protocol (PPTP) or L2TP tunnel, the remote access client or demand-dial router that requests the VPN connection must be authenticated. User-level authentication occurs through the use of a Point-to-Point Protocol (PPP) authentication method
//////////////////////////
However I have the issue is here that how shall I design, there are many vpn technology supports, however I am unable to understand the Intro>Requirements>methodo
I need just a body of my advancement, things that I have mentioned are just the diagram not sure if right that I need, I have just thought of this project. I spoke to one of the expert in my organisation. They need a diagram how where to start and the detail of this and the issues and then ending. I just need small brief of my thought
I do not know the procedure to start and continue, I had an idea I presented. I just need the diagram from experts here. Remaining I shall ask later in next question.
Now I have to make the connection between the two, the connection is between the computer and the cloud.
I know is this that:-
Authentication
The authentication of virtual private network (VPN) clients by the VPN server is a vital security concern. Authentication takes place at two levels:
1.Computer-level authentication
When Internet Protocol security (IPSec) is used for a Layer Two Tunneling Protocol (L2TP) over IPSec (L2TP/IPSec) VPN connection, computer-level authentication is performed through the exchange of computer certificates or a preshared key during the establishment of the IPSec security association.
2.User-level authentication
Before data can be sent over the Point-to-Point Tunneling Protocol (PPTP) or L2TP tunnel, the remote access client or demand-dial router that requests the VPN connection must be authenticated. User-level authentication occurs through the use of a Point-to-Point Protocol (PPP) authentication method
//////////////////////////
However I have the issue is here that how shall I design, there are many vpn technology supports, however I am unable to understand the Intro>Requirements>methodo
I need just a body of my advancement, things that I have mentioned are just the diagram not sure if right that I need, I have just thought of this project. I spoke to one of the expert in my organisation. They need a diagram how where to start and the detail of this and the issues and then ending. I just need small brief of my thought
I do not know the procedure to start and continue, I had an idea I presented. I just need the diagram from experts here. Remaining I shall ask later in next question.
You do not appear to be asking a question.
Are you using a machine translation service?
Is this for an actual requirement, or for "homework" on a course ?
Are you using a machine translation service?
Is this for an actual requirement, or for "homework" on a course ?
ASKER
I do not know what is machine translation service if you know please tell me, this is an actual requirement about that I presented an idea. Now the research team needs me to present some data to this idea. I know it is very common thing and organisations have implemented vpn between the cloud and one system (laptop or desktop). I need to know how can we create a secure environment between the two using VPN.
I meant machine translation to English..
What operating system are the "cloud" servers running ?
Are the "cloud" servers using public IP addresses or are they behind NAT (such as Amazon) ?
What operating system are on the laptops/desktops that are used to connect to them ?
What traffic do you need to secure between the laptop/desktops and the server ?
What operating system are the "cloud" servers running ?
Are the "cloud" servers using public IP addresses or are they behind NAT (such as Amazon) ?
What operating system are on the laptops/desktops that are used to connect to them ?
What traffic do you need to secure between the laptop/desktops and the server ?
ASKER
Cloud systems are running on windows 2008 OS, Yes the servers are using the public IP address. Laptops and desktops are using XP and window7. I need to secure the traffic customer information in banking, data is carried on secure VLANs, and must pass through a firewall to access other cloud VLANs or physical networks. Same goes here when the person is logging in from home to check his account in cloud server.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
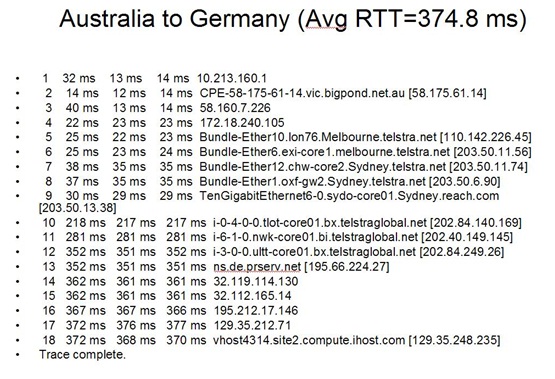
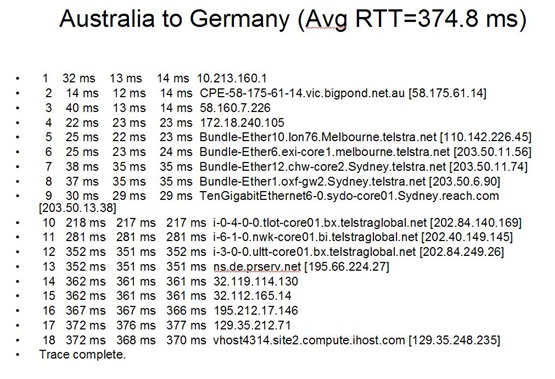 Thanks a lot ve3ofa, I am closing the question however opening a new one since it is related to it.
Thanks a lot ve3ofa, I am closing the question however opening a new one since it is related to it.My goal is to ping a machine from germany to australia, but the machine I want to ping is sitting behind a router, hence has a private address. How can I ping the machine. Germany vm ip =129.35.248.235
pLEASE REFER https://www.experts-exchange.com/questions/27825887/PING-IN-CLOUD.html
ASKER
Thanks please help https://www.experts-exchange.com/questions/27825887/PING-IN-CLOUD.html
The VPN method you use should be driven by what you need from the VPN and the technologies that you have available on each end.
As a for instance, if you need to have a VPN between a "cloud" server and an "on site" server, then you might be limited to VPN technologies that work across address translation, such as an SSL VPN.
How a VPN is authenticated should also be driven by what you need from the VPN. You have compared public and private key with "firewall VPN setup" which could be anything...