nextwavepc
asked on
SonicWall TZ210 w SonicPoint mulitiple SSID - corporate and guest setup
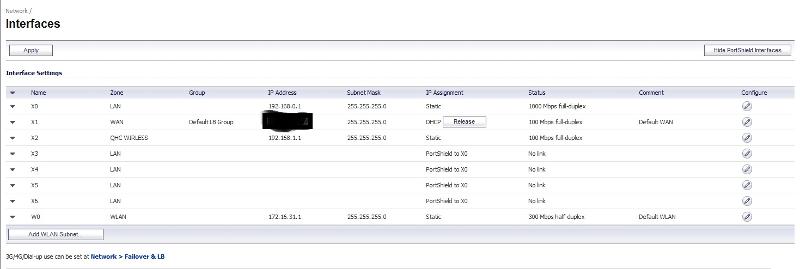
I have setup a TZ210 and 8 SonicPoint Ni, the LAN works flawless, and I then added the Sonic Points to a switch and used interface X2 for the SonicPoints, they are working flawless for the corporate wifi. Now we need to add guest access. I am having issues following the manual. I do not have the ability to add a new Network Interface. When I break the bridge from X2 to X0 I still dont have the abilty to add an interface.
To sum it up I need the SonicPoint to broadcast 2 SSIP - one for corporate with access to the LAN devices, resources, and internet, one for Guest with access to internet only.
The TZ20 is the wireless model, with the built in WIFI radio currently disabled. Firmware is Current (has to be to recognize the SonicPoint Ni.)
To sum it up I need the SonicPoint to broadcast 2 SSIP - one for corporate with access to the LAN devices, resources, and internet, one for Guest with access to internet only.
The TZ20 is the wireless model, with the built in WIFI radio currently disabled. Firmware is Current (has to be to recognize the SonicPoint Ni.)
ok...now that the bridge is broken, can you post a sanitized screen shot of your interface page again?
are you running the standard OS? i didn't think you could get the 210 with anything but enhanced. go to system > status. you should see it right there with the version of OS.
i'm looking into other reasons why you'd be missing that Add Interface button.
i'm looking into other reasons why you'd be missing that Add Interface button.
ASKER
I do believe it is the enhanced.
Firmware Version: SonicOS Enhanced 5.6.0.10-52o
Safemode Version: Safemode 5.0.1.13
ROM Version: SonicROM 5.0.2.11
CPUs: 1.33% - 500 MHz Mips64 Octeon Processor
Total Memory: 256 MB RAM, 32 MB Flash
System Time: 03/23/2011 14:41:59
Up Time: 0 Days 01:12:49
Connections: Max: 10000 Peak: 107 Current: 50
Connection Usage: 0.500%
Firmware Version: SonicOS Enhanced 5.6.0.10-52o
Safemode Version: Safemode 5.0.1.13
ROM Version: SonicROM 5.0.2.11
CPUs: 1.33% - 500 MHz Mips64 Octeon Processor
Total Memory: 256 MB RAM, 32 MB Flash
System Time: 03/23/2011 14:41:59
Up Time: 0 Days 01:12:49
Connections: Max: 10000 Peak: 107 Current: 50
Connection Usage: 0.500%
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
that was it. take your 210 to version 5.8.0.2. i now have the Add Interface button. this should allow you to complete the steps referenced above.
ASKER
I am attempting that now. I will let you know how that goes. Should have thought of that. I had terrible issues with adding the Ni's and it was all due to the firmware not being current. sigh.
yes. there has been several firmware "transition" issue that i've encountered with the sonicpoints between 5.0 and 5.8. it's been a real pain.
ASKER
Firmware Version: SonicOS Enhanced 5.8.0.2-37o
Safemode Version: SafeMode 5.0.1.13
ROM Version: SonicROM 5.0.2.11
We are now updated. Now where do I head? To the manual?
Safemode Version: SafeMode 5.0.1.13
ROM Version: SonicROM 5.0.2.11
We are now updated. Now where do I head? To the manual?
yep....the manual is the best place to start. how are your sonicpoints connecting to your sonicwall presently?
my advice, which isn't in the KBs, is to completely segregate your sonicpoints. if you have a switch you are not using, then i'd connect ONLY the sonicpoints to it. if you don't and you need to setup vlans to segregate your sonicpoint vlan traffic from the rest of your network, you'll make the ports the sonicpoints connect to and the sonicwall X2 interface "untagged" members of the BOTH vlans you create on the X2 interface.
my advice, which isn't in the KBs, is to completely segregate your sonicpoints. if you have a switch you are not using, then i'd connect ONLY the sonicpoints to it. if you don't and you need to setup vlans to segregate your sonicpoint vlan traffic from the rest of your network, you'll make the ports the sonicpoints connect to and the sonicwall X2 interface "untagged" members of the BOTH vlans you create on the X2 interface.
ASKER
I do have a seperate switch for only the SoincPoints. I was running every thing perfect till this.
Configuring it all now. Ill let you know how it works out.
Thanks.
Configuring it all now. Ill let you know how it works out.
Thanks.
cool.
Here is what you need to do.
You will need to setup virtual access points. There are many steps to doing this. I may not have them in the right order, but it won't let you setup some of these things until you have the other ones setup.
1. create VLANs for each of your wireless networks. Depending on your network setup there are different ways to do this. If your soincpoints are going to have a dedicated interface on the firewall (not used by LAN traffic) then that interface needs to have DHCP, allow sonicpoints, etc. This interface will be your sonicpoint provisioning interface. The DHCP server for this segment will only give out IPs to sonicpoints (not wifi users). You will then need to make VLANs using this interface as your parent interface. 1 VLAN for each wifi network.
2. create a zone for each wifi network. each wifi network including the provisioning network needs to have a zone associated with it. I would recommend having a separate zone for each network to give you the most flexibility.
3. Create virtual access point (VAP) profiles. These are templates for your VAPs.
4. Create VAPs from your VAP profiles. Make sure each is assigned to the appropriate VLAN. VAPs should not be associated with the provisioning network. Your physical sonicpoints will use this for getting a management IP for themselves.
5. Put your VAPs in a VAP group
6. Assign that VAP group to your sonicpoints
That should get you running. Each zone (wifi network) can now be access controlled from your firewall access rules. If you are like us and want to use your corporate DHCP server to lease out IPs for your virtual access points there is one more step. Instead of having DHCP servers on each of your VLANs and the provisioning network you would want to put an IP helper rule in place for the DHCP protocol from the zone to the IP of the DHCP server. This will forward the DHCP request broadcast packets to your DHCP server. Assuming you have a DHCP scope in place for each of the subnets it will choose the correct one (by design of the DHCP request).
If you need to have a managed switch between your sonicpoint and sonicwall firewall let me know and I can go into detail on the setup required for that.
You will need to setup virtual access points. There are many steps to doing this. I may not have them in the right order, but it won't let you setup some of these things until you have the other ones setup.
1. create VLANs for each of your wireless networks. Depending on your network setup there are different ways to do this. If your soincpoints are going to have a dedicated interface on the firewall (not used by LAN traffic) then that interface needs to have DHCP, allow sonicpoints, etc. This interface will be your sonicpoint provisioning interface. The DHCP server for this segment will only give out IPs to sonicpoints (not wifi users). You will then need to make VLANs using this interface as your parent interface. 1 VLAN for each wifi network.
2. create a zone for each wifi network. each wifi network including the provisioning network needs to have a zone associated with it. I would recommend having a separate zone for each network to give you the most flexibility.
3. Create virtual access point (VAP) profiles. These are templates for your VAPs.
4. Create VAPs from your VAP profiles. Make sure each is assigned to the appropriate VLAN. VAPs should not be associated with the provisioning network. Your physical sonicpoints will use this for getting a management IP for themselves.
5. Put your VAPs in a VAP group
6. Assign that VAP group to your sonicpoints
That should get you running. Each zone (wifi network) can now be access controlled from your firewall access rules. If you are like us and want to use your corporate DHCP server to lease out IPs for your virtual access points there is one more step. Instead of having DHCP servers on each of your VLANs and the provisioning network you would want to put an IP helper rule in place for the DHCP protocol from the zone to the IP of the DHCP server. This will forward the DHCP request broadcast packets to your DHCP server. Assuming you have a DHCP scope in place for each of the subnets it will choose the correct one (by design of the DHCP request).
If you need to have a managed switch between your sonicpoint and sonicwall firewall let me know and I can go into detail on the setup required for that.
ASKER
Since I was not able to add VAPs - though I knew how, It was purely based on the firmware not being current - though I had stated it was. Go figure. Thanks, that was the key to proceeding further and adding my second SSID.
glad things worked out and i learned something in the process too. thanks for the points!
gilm0079
If you have documentation about utilizing a managed switch between the SonicWALL router and the SonicPointNi interfaces I'd be happy to see that.
Sorry about being off-topic...
If you have documentation about utilizing a managed switch between the SonicWALL router and the SonicPointNi interfaces I'd be happy to see that.
Sorry about being off-topic...
I don't have any documents on it. Most switches operate the same as far as VLAN memberships. If you are doing the setup like I am and your sonicpoint provisioning subnet plus each wifi subnet are VLANs of a physical interface on your sonicwall firewall then you switches will need to have the port going towards your sonicwall and towards your sonicpoints "Tagged" with the provisioning VLAN and each Wifi VLAN. The only difference is when you get to the managed switch directly connected to your sonicpoint. That's where your provisioning VLAN needs to be "Untagged".
As for DHCP routing, our sonicwall acts as the bridge between our VLANs so for us we put in iphelper policies on the sonicwall to help DHCP requests from each wifi subnet to the DHCP server. If your switches handle your VLAN bridging then you will need to put iphelper rules in on them to help the DHCP broadbast packets over to your DHCP server.
As for DHCP routing, our sonicwall acts as the bridge between our VLANs so for us we put in iphelper policies on the sonicwall to help DHCP requests from each wifi subnet to the DHCP server. If your switches handle your VLAN bridging then you will need to put iphelper rules in on them to help the DHCP broadbast packets over to your DHCP server.
I broke into the IP Helper but haven't had a chance to test my new configuration.
SonicWALL allows you to assign multiple VLAN's to the same SonicPoints so you can set up guest access AND secured/employee access simutaneously. This is very convenient but extremely inconvenient if you can't assign more than one VLAN to a managed switch port.
Easier to just replace the managed switch with a simple POE switch instead, it seems.
SonicWALL allows you to assign multiple VLAN's to the same SonicPoints so you can set up guest access AND secured/employee access simutaneously. This is very convenient but extremely inconvenient if you can't assign more than one VLAN to a managed switch port.
Easier to just replace the managed switch with a simple POE switch instead, it seems.
All managed switches should allow you to assign as many VLANs to a switch port as you want. You may be looking in the wrong place. You don't want to assign a "Customer VLAN" or "PVID" to the port. What that does is takes ingress untagged packets and assigns them to the PVID and takes tagged packets from that VLAN and untagges them egress from the port.
Usually switches call it VLAN membership or something like that. I would refer to your user manual for your specific switch on this.
Usually switches call it VLAN membership or something like that. I would refer to your user manual for your specific switch on this.