Anthony Lucia
asked on
Digital signatures and asymetric keys
On a previous post, I had an excellent answer, but I did not understand it fully. The answer contained the following:
My confusion is the asymetric keys. The answer stated that you encypted the hash with the private key, and decrypt with the public key. This seems backwards to me
In SSL, I thought the client would encrypt the hash with the public key and the server would decrypt the hash with the private key
Or am I mistakeninly thinking of SSL with digital signatures. Does SSL make use of digital signatures
njd
Most cryptographic signatures are in fact the hash of the message encrypted with the signer's private asymmetric key. By decrypting the key using the matching public key, the verifier can obtain the original hash, and hence, match that to a locally calculated value of the message's hash.
My confusion is the asymetric keys. The answer stated that you encypted the hash with the private key, and decrypt with the public key. This seems backwards to me
In SSL, I thought the client would encrypt the hash with the public key and the server would decrypt the hash with the private key
Or am I mistakeninly thinking of SSL with digital signatures. Does SSL make use of digital signatures
njd
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Giovanni,
Nice diagram! Please provide a link to the web page for it. Thanks, Joe
NJDave,
Another nice diagram is this:
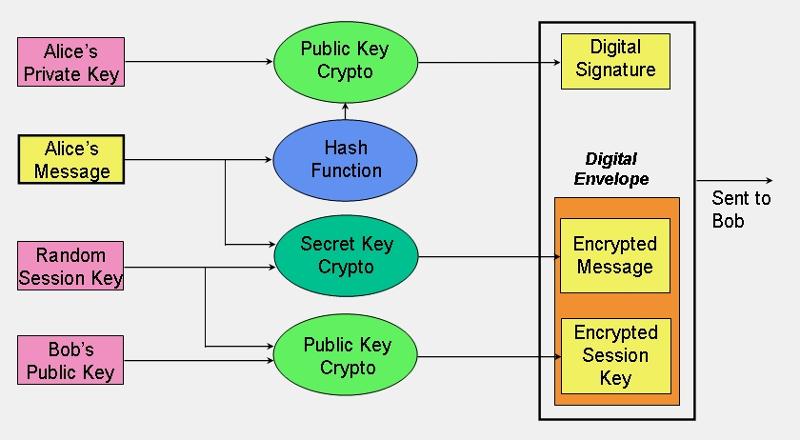 It is from another excellent paper, An Overview of Cryptography, by Gary Kessler:
It is from another excellent paper, An Overview of Cryptography, by Gary Kessler:
http://www.garykessler.net/library/crypto.html
Regards, Joe
Nice diagram! Please provide a link to the web page for it. Thanks, Joe
NJDave,
Another nice diagram is this:
 It is from another excellent paper, An Overview of Cryptography, by Gary Kessler:
It is from another excellent paper, An Overview of Cryptography, by Gary Kessler:http://www.garykessler.net/library/crypto.html
Regards, Joe
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
1
Alice wants to send a message to Bob and provide confidentiality, integrity, proof of origin and proof of receipt.
2
To protect the secrecy of her message contents, she uses a symmetric cipher to encrypt it. For that she uses a symmetric key. This produces a ciphertext message.
3
To protect the accuracy of the message, she uses a hashing algorithm that condenses the arbitrary-length message to a fixed-size message digest value.
4
To prove the message actually came from her, Alice signs the message by encrypting the hash value with her private key. The sum of the message digest encrypted with Alice's private key results in a digital signature.
5
This digital signature is then appended it to the bottom of the symmetrically encrypted message. Now in order for Bob to read, prove the origin, and check the accuracy of the message, he must reverse all of the encryption done above.
6
To read the message, Bob needs a copy of the symmetric key. Alice encrypts it using asymmetric encryption and encrypts the symmetric key with Bob's public key, producing a ciphertext key.
7
Bob decrypts the ciphertext key with his private key to give him his copy of the symmetric key.
8
Bob uses the symmetric key to decrypt the message with that key and read it.
9
Bob decrypts Alice's digital signature using Alice's public key. Once the decryption process is complete, he is left with the message digest.
10
But, he has yet to prove the integrity of the message or the proof of origin. He must prove the message digest value is correct. To do this, Bob must rehash the message that he has received and decrypted.
11
If the message digest that he generates from the message matches the message digest that he decrypted from Alice's digital signature, then he has proof of integrity and proof of origin.
12
To prove that he received the actual message Alice sent, Bob re-encrypts the message digest with his private key, which will result in his digital signature.
13
Bob sends his digital signature back to Alice.
14
Alice decrypts Bob's digital signature using his public key to produce the message digest.
15
She compares the message digest she just received to the message digest she originally generated. If these two message digests match, then she has proven that her message was received by Bob (proof of receipt) in its correct format (proof of integrity).