TonyLc
asked on
How to ASA 9.1 Port Forward
Hello,
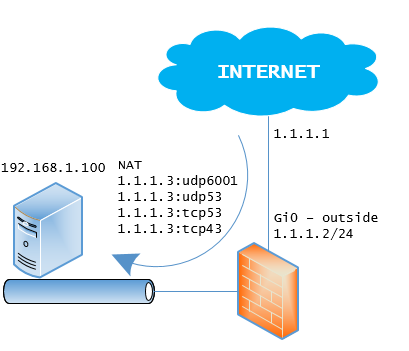
I want to use a public IP I have that is not the outside interface but in the same subnet range to forward to a internal server that has a private IP and I need 3 service ports ie: udp6001 tcp/udp53 and tcp443. So in short a outside vendor wants to be able to access this server using a public IP of mine and be able to utilize the above services unidirectional. I see some examples but not sure if they really fit my issue. Any help would be very appreciated.
Thanks
I want to use a public IP I have that is not the outside interface but in the same subnet range to forward to a internal server that has a private IP and I need 3 service ports ie: udp6001 tcp/udp53 and tcp443. So in short a outside vendor wants to be able to access this server using a public IP of mine and be able to utilize the above services unidirectional. I see some examples but not sure if they really fit my issue. Any help would be very appreciated.
Thanks
It would look something like this
object service PORTFORWARD_UDP6001
service udp destination eq 6001
!
object service PORTFORWARD_UDP53
service udp destination eq 53
!
object service PORTFORWARD_TCP53
service tcp destination eq 53
!
object service PORTFORWARD_TCP443
service tcp destination eq 443
!
object network OBJECT_EXTERNAL_IP
host 1.1.1.3
!
object network OBJECT_INTERNAL_IP
host 192.168.1.100
!
!
nat (outside,inside) 1 source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_UDP6001 PORTFORWARD_UDP6001 unidirectional
nat (outside,inside) 2 source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_UDP53 PORTFORWARD_UDP53 unidirectional
nat (outside,inside) 3 source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_TCP53 PORTFORWARD_TCP53 unidirectional
nat (outside,inside) 4 source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_TCP443 PORTFORWARD_TCP443 unidirectional
!
!
access-list outside_access_in line 1 extended permit udp any object OBJECT_INTERNAL_IP eq 6001
access-list outside_access_in line 2 extended permit udp any object OBJECT_INTERNAL_IP eq 53
access-list outside_access_in line 3 extended permit tcp any object OBJECT_INTERNAL_IP eq 53
access-list outside_access_in line 4 extended permit tcp any object OBJECT_INTERNAL_IP eq 443
!
access-group outside_access_in in interface outside
For ASA software 8.3 or higher, the NAT is done first in the order of operation. Hence you'll notice that the ACL pertains to the instenal IP and not the external IP.
ASKER
Thanks Max, I will give that config a try. I had a feeling I was looking at multiple nat's and access but wanted some confirmation. Anyway, thanks and I will get back with you. Appreciate it.
Forgot to add:, if you will dedicate the public IP to this particular server, the NAT statement would look like this instead.
 Lastly, the "nat (outside,inside)" might need to change to "nat (outside,dmz)" if the server is located on your dmz interface, or whatever your interface nameif is.
Lastly, the "nat (outside,inside)" might need to change to "nat (outside,dmz)" if the server is located on your dmz interface, or whatever your interface nameif is.
The NAT configuration I've given is for 8.3 above.
object network OBJECT_EXTERNAL_IP
host 1.1.1.3
!
object network OBJECT_INTERNAL_IP
host 192.168.1.100
!
nat (outside,inside) source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP unidirectional
But if not, in case you just want to accomplish port forwarding, the above configuration I gave should do the trick.
 Lastly, the "nat (outside,inside)" might need to change to "nat (outside,dmz)" if the server is located on your dmz interface, or whatever your interface nameif is.
Lastly, the "nat (outside,inside)" might need to change to "nat (outside,dmz)" if the server is located on your dmz interface, or whatever your interface nameif is.The NAT configuration I've given is for 8.3 above.
ASKER
Ok, I modified the nat to match the dedicated since that is my intention. Still gets dropped by nat on the packet trace but have not tested with the real device yet. Will try again as soon as I can.
Thanks,
Tony
Thanks,
Tony
I've tested this on GNS3 running 8.4 software (should be applicable for 9.1 as well)
So two things:
If you packet-tracer doesn't show PHASE1 as UN-NAT, then it might be a problem with your NAT configuration. Can you share your pack-tracer output? Another thing you can check is the NAT sequence number. A preceding NAT statement might be causing the problem. Ensure that the new NAT statement are placed in front of existing NAT configuration by specifying the number "nat (outside,dmz) 1".
interface GigabitEthernet0
nameif outside
security-level 0
ip address 1.1.1.2 255.255.255.0
!
interface GigabitEthernet2
nameif dmz
security-level 50
ip address 192.168.1.1 255.255.255.0
!
object service PORTFORWARD_UDP6001
service udp destination eq 6001
!
object service PORTFORWARD_UDP53
service udp destination eq domain
!
object service PORTFORWARD_TCP53
service tcp destination eq domain
!
object service PORTFORWARD_TCP443
service tcp destination eq https
!
object network OBJECT_EXTERNAL_IP
host 1.1.1.3
!
object network OBJECT_INTERNAL_IP
host 192.168.1.100
!
!
nat (outside,dmz) source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_UDP6001 PORTFORWARD_UDP6001 unidirectional
nat (outside,dmz) source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_UDP53 PORTFORWARD_UDP53 unidirectional
nat (outside,dmz) source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_TCP53 PORTFORWARD_TCP53 unidirectional
nat (outside,dmz) source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_TCP443 PORTFORWARD_TCP443 unidirectional
!
!
access-list outside_access_in extended permit udp any object OBJECT_INTERNAL_IP eq 6001
access-list outside_access_in extended permit udp any object OBJECT_INTERNAL_IP eq domain
access-list outside_access_in extended permit tcp any object OBJECT_INTERNAL_IP eq domain
access-list outside_access_in extended permit tcp any object OBJECT_INTERNAL_IP eq https
!
access-group outside_access_in in interface outside
!ciscoasa# packet-tracer input outside tcp 8.8.8.8 53 1.1.1.3 53
Phase: 1
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (outside,dmz) source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_TCP53 PORTFORWARD_TCP53 unidirectional
Additional Information:
NAT divert to egress interface dmz
Untranslate 1.1.1.3/53 to 192.168.1.100/53
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_access_in in interface outside
access-list outside_access_in extended permit tcp any object OBJECT_INTERNAL_IP eq domain
Additional Information:
Phase: 3
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (outside,dmz) source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_TCP53 PORTFORWARD_TCP53 unidirectional
Additional Information:
Static translate 8.8.8.8/53 to 8.8.8.8/53
Phase: 5
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (outside,dmz) source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_TCP53 PORTFORWARD_TCP53 unidirectional
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 2, packet dispatched to next module
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: dmz
output-status: up
output-line-status: up
Action: allow
ciscoasa#nat (outside,dmz) source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP unidirectionalciscoasa# packet-tracer input outside udp 8.8.8.8 6001 1.1.1.3 6001
Phase: 1
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (outside,dmz) source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP unidirectional
Additional Information:
NAT divert to egress interface dmz
Untranslate 1.1.1.3/6001 to 192.168.1.100/6001
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_access_in in interface outside
access-list outside_access_in extended permit udp any object OBJECT_INTERNAL_IP eq 6001
Additional Information:
Phase: 3
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (outside,dmz) source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP unidirectional
Additional Information:
Static translate 8.8.8.8/6001 to 8.8.8.8/6001
Phase: 5
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (outside,dmz) source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP unidirectional
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 3, packet dispatched to next module
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: dmz
output-status: up
output-line-status: up
Action: allow
ciscoasa#So two things:
NAT configuration, Static NAT or port forwarding configuration both tested.
ACL configuration on outside interface, should use the INTERNAL IP as destination.
If you packet-tracer doesn't show PHASE1 as UN-NAT, then it might be a problem with your NAT configuration. Can you share your pack-tracer output? Another thing you can check is the NAT sequence number. A preceding NAT statement might be causing the problem. Ensure that the new NAT statement are placed in front of existing NAT configuration by specifying the number "nat (outside,dmz) 1".
nat (outside,dmz) 1 source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_UDP6001 PORTFORWARD_UDP6001 unidirectional
nat (outside,dmz) 2 source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_UDP53 PORTFORWARD_UDP53 unidirectional
nat (outside,dmz) 3 source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_TCP53 PORTFORWARD_TCP53 unidirectional
nat (outside,dmz) 4 source static any any destination static OBJECT_EXTERNAL_IP OBJECT_INTERNAL_IP service PORTFORWARD_TCP443 PORTFORWARD_TCP443 unidirectionalASKER
Ok thank you. I have made sure the nat config goes above the others. I am working with outside and inside interfaces so I will change to (outside,inside) then utilize the rest and give that a try. If not successful this time - I will gladly share my results.
Thanks everybody.!
Thanks everybody.!
ASKER
Still dropped for me. So, since I am dedicating a Public for this at this time I have one nat stament and 4 acl's and then of course the defined ports and hosts.
DC-ASA5555-1# packet-tracer input outside udp 70.186.9.126 6001 172.16.15.156 $
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 172.16.0.0 255.248.0.0 inside
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_access_in in interface outside
access-list outside_access_in extended permit udp any object DEJERO-INSIDE eq 6001
Additional Information:
Phase: 4
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: FOVER
Subtype: standby-update
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: NAT
Subtype: rpf-check
Result: DROP
Config:
nat (outside,inside) source static any any destination static DEJERO-PUBLIC DEJERO-INSIDE unidirectional
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
Thanks,
Tony
DC-ASA5555-1# packet-tracer input outside udp 70.186.9.126 6001 172.16.15.156 $
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 172.16.0.0 255.248.0.0 inside
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_access_in in interface outside
access-list outside_access_in extended permit udp any object DEJERO-INSIDE eq 6001
Additional Information:
Phase: 4
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: FOVER
Subtype: standby-update
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: NAT
Subtype: rpf-check
Result: DROP
Config:
nat (outside,inside) source static any any destination static DEJERO-PUBLIC DEJERO-INSIDE unidirectional
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
Thanks,
Tony
ASKER
Sorry, will attach that next time. New to EE.
A few things to clarify.
Is "172.16.15.156" the internal IP of the server? If yes, then you should run the packet-tracer with external IP as the destination IP and not the internal IP.
packet-tracer input outside udp x.x.x.x 6001 EXTERNAL_IP 6001ASKER
ASKER
OK, re-did the packet trace - new to that also - took a couple years off of asa and was working on srx's and now the asa is like a new ball-game - sort of.
So I will attach the results but it passes almost all the way through this time.
except this:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (sp-security-failed) Slowpath security checks failed
Thanks,
Tony
packettrace-2.txt
So I will attach the results but it passes almost all the way through this time.
except this:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (sp-security-failed) Slowpath security checks failed
Thanks,
Tony
packettrace-2.txt
packet-tracer input outside udp 172.16.15.156 6001 70.186.9.126
You probably sourced it from the FW interface
try:
packet-tracer input outside udp 8.8.8.8 6001 70.186.9.126 6001
ASKER
Yep, that did it. I thank you all very much. I hope you all have a wonderful day.
Thanks again,
Tony
Thanks again,
Tony
ASKER
I've requested that this question be closed as follows:
Accepted answer: 0 points for TonyLc's comment #a40671801
Assisted answer: 167 points for max_the_king's comment #a40670818
Assisted answer: 167 points for ffleisma's comment #a40671397
Assisted answer: 166 points for ffleisma's comment #a40671634
for the following reason:
New at this - if I accidentally hit a wrong box sorry- Both Max and ffleisma were very helpful and ffleisma had the final. Thank you.
Accepted answer: 0 points for TonyLc's comment #a40671801
Assisted answer: 167 points for max_the_king's comment #a40670818
Assisted answer: 167 points for ffleisma's comment #a40671397
Assisted answer: 166 points for ffleisma's comment #a40671634
for the following reason:
New at this - if I accidentally hit a wrong box sorry- Both Max and ffleisma were very helpful and ffleisma had the final. Thank you.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Yes, while both was helpful ffleisma provided the final correct solution. I am new to this and if I assigned it wrong I did not mean too.
Thanks,
Tony
Thanks,
Tony
No worries, thanks Tony!
Hi,
I should object to this odd behaviour but I have already wasted enough time on it and I really do not care.
cheers
max
I should object to this odd behaviour but I have already wasted enough time on it and I really do not care.
cheers
max
My apologies to max and tony. Both solution provided can result to a working configuration and given max gave a working solution first, he must be credited with the correct answer.
I initially objected on closing the question due to no answer was accepted as correct.
I'm sorry for offending anyone, please credit max the correct solution and points as he was the first to give reply. My mistake here guys, my apologies for my behavior.
I initially objected on closing the question due to no answer was accepted as correct.
I'm sorry for offending anyone, please credit max the correct solution and points as he was the first to give reply. My mistake here guys, my apologies for my behavior.
suppose you want to nat your server (i.e.: 192.168.1.10) to public IP 1.2.3.4, and give anyone access to the ports you indicated above:
here is the code:
object-group service WEBPORTSTCP tcp
port-object eq 53
port-object eq 443
object-group service WEBPORTSUDP udp
port-object eq 53
port-object eq 6001
object network obj_Webserver
host 192.168.1.10
object network obj_Webserver
nat (inside,outside) static 1.2.3.4
access-list external_access extended permit tcp any host 192.168.1.10 object-group WEBPORTSTCP
access-list external_access extended permit udp any host 192.168.1.10 object-group WEBPORTSUDP
access-group external_access in interface outside
should you want to give only your vendor that access (i.e.: vendor public IP 5.6.7.8), than you should replace the above access-lists with the following:
access-list external_access extended permit tcp host 5.6.7.8 host 192.168.1.10 object-group WEBPORTSTCP
access-list external_access extended permit udp host 5.6.7.8 host 192.168.1.10 object-group WEBPORTSUDP
hope this helps
max