Coldfusion server hijacked to send email spam!!
Coldfusion 9
Windows Server 2008
I noticed yesterday that emails were not being sent from my CF server so I checked the EmailSent log. This is what I saw in the following 2 log lines
"Information","scheduler-2
"Information","scheduler-2
"Information","scheduler-0
followed by what is seemingly spam going to completely unknown addresses (4 emails per second!!)
"Information","scheduler-0
"Information","scheduler-0
"Information","scheduler-0
"Information","scheduler-0
"Information","scheduler-0
The only way I can stop it from happening is to shut down the CF service ... which shuts down our website. Can anyone help me figure out how to stop this??
Max
Windows Server 2008
I noticed yesterday that emails were not being sent from my CF server so I checked the EmailSent log. This is what I saw in the following 2 log lines
"Information","scheduler-2
"Information","scheduler-2
"Information","scheduler-0
followed by what is seemingly spam going to completely unknown addresses (4 emails per second!!)
"Information","scheduler-0
"Information","scheduler-0
"Information","scheduler-0
"Information","scheduler-0
"Information","scheduler-0
The only way I can stop it from happening is to shut down the CF service ... which shuts down our website. Can anyone help me figure out how to stop this??
Max
Turn off allowing a smtp relay on the server. Or at least require authentication.
I don't know know CF. Is this windows or linux?
How do you use CF to send mail. Is it configured in the CF administrator or do you configure it in your <cfmail> tag?
Is the SMTP server local? Do you have to use authentication for the mail server or is it trusted?
Is the SMTP server local? Do you have to use authentication for the mail server or is it trusted?
ASKER
I have the email server and authentication set up in CF Administrator. I put a bogus email server in there and the 'connection failed' but the email logs still keep showing successful email sent - 4 per second. Yes the SMTP server is local, but on a separate server (Server Exchange 2007). Both servers run Win 2008. In the CF Mail-Spool folder I found a copy of the email being sent ... in what appears to be a header, it includes our:
-email server name port 25
-a legit server username
-and some bogus password
It is in french and I cannot read it, but it appears to be a bank spam prompting you the click on a link to confirm something.
-email server name port 25
-a legit server username
-and some bogus password
It is in french and I cannot read it, but it appears to be a bank spam prompting you the click on a link to confirm something.
ASKER
This is what the email looks like when I changed the extension to .txt and opened it in notepad:
type: text/html; charset=UTF-8
server: xxxx:25 - it is using the correct server
server-username: xxxx - it is using a legit username
server-password: ajFhM3c1czc= - this is a bogus password!!!
from: Support <id@pandawill.com>
to: vier.jouanjean@orange.fr
subject: Suspension, Facturat¿on mensuelle inadaptée
X-Mailer: ColdFusion 9 Application Server
body: <div><br />
body: <table class="mail-content-readon
body: <tbody style="margin: 0px; padding: 0px; border: 0px;">
body: <tr style="margin: 0px; padding: 0px; border: 0px;">
body: <td style="margin: 0px; padding: 0px; border: 0px; vertical-align: top;">
body: <div class="mail-content-read" id="message" style="margin: 0px; padding: 0px; border: 0px; min-height: 200px; width: 1006px;">
body: <p align="center" style="border: 0px; line-height: 1.3em; width: auto; height: auto; float: none;">Bonjour</p>
body: <p align="center" style="border: 0px; line-height: 1.3em; width: auto; height: auto; float: none;"><a href="http://www.electromecanicoelruly.com/confirmation.html" target="_blank" style="margin: 0px; padding: 0px; border: 0px; color: rgb(68, 68, 68); text-decoration: none;"><img border="0" src="http://www.nautic-direct.com/src.jpg" style="margin: 0px; padding: 0px; border: 0px;" alt="" /></a></p>
body: </div>
body: </td>
body: </tr>
body: </tbody>
body: </table>
body: </div>
Max
type: text/html; charset=UTF-8
server: xxxx:25 - it is using the correct server
server-username: xxxx - it is using a legit username
server-password: ajFhM3c1czc= - this is a bogus password!!!
from: Support <id@pandawill.com>
to: vier.jouanjean@orange.fr
subject: Suspension, Facturat¿on mensuelle inadaptée
X-Mailer: ColdFusion 9 Application Server
body: <div><br />
body: <table class="mail-content-readon
body: <tbody style="margin: 0px; padding: 0px; border: 0px;">
body: <tr style="margin: 0px; padding: 0px; border: 0px;">
body: <td style="margin: 0px; padding: 0px; border: 0px; vertical-align: top;">
body: <div class="mail-content-read" id="message" style="margin: 0px; padding: 0px; border: 0px; min-height: 200px; width: 1006px;">
body: <p align="center" style="border: 0px; line-height: 1.3em; width: auto; height: auto; float: none;">Bonjour</p>
body: <p align="center" style="border: 0px; line-height: 1.3em; width: auto; height: auto; float: none;"><a href="http://www.electromecanicoelruly.com/confirmation.html" target="_blank" style="margin: 0px; padding: 0px; border: 0px; color: rgb(68, 68, 68); text-decoration: none;"><img border="0" src="http://www.nautic-direct.com/src.jpg" style="margin: 0px; padding: 0px; border: 0px;" alt="" /></a></p>
body: </div>
body: </td>
body: </tr>
body: </tbody>
body: </table>
body: </div>
Max
I don't know exchange, but I do know you have to set your email server to require authentication, not CF. You will need to change your CF script to use authentication though.
ASKER
I'm not sure if I am understanding correctly, but the CF server sends an email in examples like:
- A customer places an order on our site, the office gets emailed.
- A customer places a support request, the support staff get an email
I couldn't a place authentication requirement in those cases ... have no idea who the customer might be & certainly don't want to share that info with them ...
Max
- A customer places an order on our site, the office gets emailed.
- A customer places a support request, the support staff get an email
I couldn't a place authentication requirement in those cases ... have no idea who the customer might be & certainly don't want to share that info with them ...
Max
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
I'm sure Rick is more fluent in this. But I believe you want to make sure your mail server requires authentication regardless if you send via your CF or .NET or PHP etc. But you do want to make sure your CF does not have any holes.
ASKER
UPDATE: I called in an emergency IT guy who blocked everything to and from orange.fr on our firewall and that has stopped the email spamming temporarily ... still have work to do to secure things up ...
Scott: I'm afraid I'm still not sure what you mean. Our mail server requires authentication to log into it. Our CF aministrater has the mail server listed, plus a username and password in order to connect to the mail server. Are you suggesting that everytime and email gets sent through our website, I require the user to enter a username or password? ... or am I way off here ...
Rick: Thanks, I ran hackmycf and found several critial errors and am working throught them ... I disabled 'Robust Exception Information' and there is a hotix I can apply. It also tells me that several folders are open to the public:
/CFIDE/componentutils/
/CFIDE/adminapi/
... I thought I had directory browing turned off in IIS and I cannot access them when I add them to the end of my website domain ...? How do I make it so these are not exposed to public?
Also it tells me that ColdFusion Administrator is Public and should be restricted by IP ... any idea on how I do that?
Thats most of the critical issues ... I will go throught the important ones one by one ...
Thanks,
Max
Scott: I'm afraid I'm still not sure what you mean. Our mail server requires authentication to log into it. Our CF aministrater has the mail server listed, plus a username and password in order to connect to the mail server. Are you suggesting that everytime and email gets sent through our website, I require the user to enter a username or password? ... or am I way off here ...
Rick: Thanks, I ran hackmycf and found several critial errors and am working throught them ... I disabled 'Robust Exception Information' and there is a hotix I can apply. It also tells me that several folders are open to the public:
/CFIDE/componentutils/
/CFIDE/adminapi/
... I thought I had directory browing turned off in IIS and I cannot access them when I add them to the end of my website domain ...? How do I make it so these are not exposed to public?
Also it tells me that ColdFusion Administrator is Public and should be restricted by IP ... any idea on how I do that?
Thats most of the critical issues ... I will go throught the important ones one by one ...
Thanks,
Max
You need to block the folders via IIS.
In IIS manager click on Request Filtering in the root machine not in on the web sites.*
Then the URL tab. Add these entries. See attach screen shot.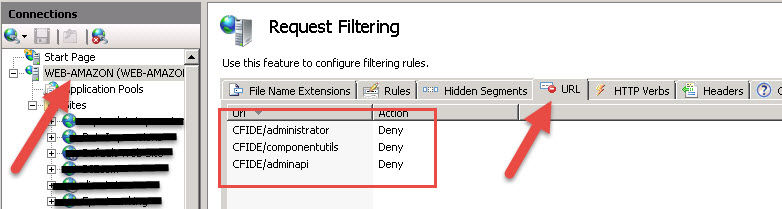
* If you are using IIS7 not 7.5 you may need to install the Admin Pack if you do not see the Request Filtering icon. See this link.
http://blogs.msdn.com/b/carlosag/archive/2008/03/24/iisadminpackrequestfiltering.aspx
Just a note: Sometimes hackers can use your own forms against you in sending mail out. I have seen that.
In IIS manager click on Request Filtering in the root machine not in on the web sites.*
Then the URL tab. Add these entries. See attach screen shot.

* If you are using IIS7 not 7.5 you may need to install the Admin Pack if you do not see the Request Filtering icon. See this link.
http://blogs.msdn.com/b/carlosag/archive/2008/03/24/iisadminpackrequestfiltering.aspx
Just a note: Sometimes hackers can use your own forms against you in sending mail out. I have seen that.
ASKER
Whew! Thanks Rick for http://hackmycf.com/! I have now taken care of all citical issues, and have a couple important ones and a few warnings to deal with, but I think I have things locked up pretty good. Well, way better than before!
I admitedly had a weak CF Administrator password, so I changed that too. They had stolen my username and password so that also got changed.
One probelm I found with denying /CFIDE/admistrator is that I myself cannot access the administrator unless I remove that url. That is a minor issue though ... I can just remove that url when I need to get into the administrator then hopefully remember to put it back once I am done.
Thanks a bunch! I would not have had any idea where to start securing my CF server without that tool!
6Gun
I admitedly had a weak CF Administrator password, so I changed that too. They had stolen my username and password so that also got changed.
One probelm I found with denying /CFIDE/admistrator is that I myself cannot access the administrator unless I remove that url. That is a minor issue though ... I can just remove that url when I need to get into the administrator then hopefully remember to put it back once I am done.
Thanks a bunch! I would not have had any idea where to start securing my CF server without that tool!
6Gun
Create another web site with another IP address it should be a internal only web site then remove the Deny from just that web site.
ASKER
Hmmm okay, I sort of understand ... just to be sure ... r-click on sites, New Website ... Just any IP address? Do I need to actually create a site to point to or can I just create some folder somwhere? How do I make it internal only? ... IP 127.0.0.1?
Sorry if I'm getting greedy with questions ... this has been a very eye opening & great learning experience.
Max
Sorry if I'm getting greedy with questions ... this has been a very eye opening & great learning experience.
Max
Does you web server using internal IP addresses like 10.x.x.x or 192.168.x.x or does it use public IP addresses. Most web server have an internal address with en external address pointing to the internal. In other word most web server on behind a NAT / Firewall.
ASKER
Yeah we're 192.168 internally ... pretty sure our firewall (physical) resolves the IP as people hit the site ... the site in question has 192.168 bindings. Hmmm I think I'm figuring this out as I type ... as long as I don't configure the firewall, I can use any available IP in the 192.168 range and it will be 'local only' ... am I correct? And if so, does the new site need to have any content, or just a folder with and index.htm file? A dummy site if you will ...
Max
Max
Correct.
ASKER
Lol ... sometimes I just need to talk (type) it out! I'm also assuming that I change the CF administrator icon path to the IP of the dummy site's IP ...
You my friend are a saviour! I am very grateful for you taking time to help! I walk away a much wiser person!
Max
You my friend are a saviour! I am very grateful for you taking time to help! I walk away a much wiser person!
Max
ASKER
A+
Hi MaxwellTurner, RickEpnet , i happen to have the very same issue with our CF server, and i really appreciate the valuable amount of info and knowledge you have put in this thread. However i would like to ask what was it exactly that solved the problem and stopped the bogus emails from being sent ??
ASKER
Hey RickEpnet, first with the help of my IT guy, we identified and blocked the offending IP on our firewall to stop the emails, changed the CF server admin passwords, then I ran HackMyCF which found a couple dozen 'holes' in the CF server security. Most issues HackMyCF found were fairly straightforward to fix, however when preforming the upgrades you make sure you back old folders up before you apply the updated files!
My CF server was VERY unsecure ... simply didn't know better ... now that I have all the security holes fixed and updated with the lastest hotfixes, things seem fine.
Max
My CF server was VERY unsecure ... simply didn't know better ... now that I have all the security holes fixed and updated with the lastest hotfixes, things seem fine.
Max
MaxwellTurner thank you very much for such a quick response, however excuse me if I'm being naive with my questions, but how do i identify the offending IP ? here is a bit of the log of the email activity on our gateway :
I have applied some changes as advised by HackMyCf and we are waiting to install a security update patch however that will take a while until we get approved. in the meantime i will definitely consider changing the administrator password . However does changing that along with the authentication (please see pic ) help stop the bogus emails ?
 because it seems in the bogus emails being sent this username and password ( in pic) are being used in every single one of the emails...
because it seems in the bogus emails being sent this username and password ( in pic) are being used in every single one of the emails...
Aug 12 04:16:51 xena sendmail[29699]: [ID 801593 mail.info] s7C3GowY029699: from=<info73821@uel.ac.uk>, size=1021, class=0, nrcpts=1, msgid=<1919670134.204585.1407813410900.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29717]: [ID 801593 mail.info] s7C3Go7N029717: from=<info73821@uel.ac.uk>, size=1015, class=0, nrcpts=1, msgid=<234618192.204588.1407813410916.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29668]: [ID 801593 mail.info] s7C3GoXq029668: from=<info73821@uel.ac.uk>, size=1021, class=0, nrcpts=1, msgid=<101629610.204586.1407813410900.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29634]: [ID 801593 mail.info] s7C3GnNS029634: from=<info73821@uel.ac.uk>, size=1016, class=0, nrcpts=1, msgid=<447977052.204589.1407813410947.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29636]: [ID 801593 mail.info] s7C3GntC029636: from=<info73821@uel.ac.uk>, size=1026, class=0, nrcpts=1, msgid=<1529955728.204592.1407813410947.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29637]: [ID 801593 mail.info] s7C3GnuP029637: from=<info73821@uel.ac.uk>, size=1023, class=0, nrcpts=1, msgid=<72646582.204590.1407813410947.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29681]: [ID 801593 mail.info] s7C3Goje029681: from=<info73821@uel.ac.uk>, size=1018, class=0, nrcpts=1, msgid=<897836448.204594.1407813410947.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29633]: [ID 801593 mail.info] s7C3GnJE029633: from=<info73821@uel.ac.uk>, size=1023, class=0, nrcpts=1, msgid=<1717077714.204595.1407813410963.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29635]: [ID 801593 mail.info] s7C3GnaU029635: from=<info73821@uel.ac.uk>, size=1026, class=0, nrcpts=1, msgid=<2144214965.204593.1407813410947.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29717]: [ID 801593 mail.info] s7C3Go7O029717: from=<info73821@uel.ac.uk>, size=1021, class=0, nrcpts=1, msgid=<1039890812.204596.1407813410963.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29635]: [ID 801593 mail.info] s7C3GnaV029635: from=<info73821@uel.ac.uk>, size=1024, class=0, nrcpts=1, I have applied some changes as advised by HackMyCf and we are waiting to install a security update patch however that will take a while until we get approved. in the meantime i will definitely consider changing the administrator password . However does changing that along with the authentication (please see pic ) help stop the bogus emails ?
 because it seems in the bogus emails being sent this username and password ( in pic) are being used in every single one of the emails...
because it seems in the bogus emails being sent this username and password ( in pic) are being used in every single one of the emails...
ASKER
I am not sure how my IT guy blocked the IP ... I sent him the mail log (as you have shown above), he emailed me back and said he needed and actual IP. I told him that is all I had and eventually he 'figured' it out ... he finally emailed me back and told me he found the IP and instructed me to reboot our firewall ... emails finally stopped. My server was sending out 4 emails per second so I assume he identified an IP that was generating ALOT of activity. I have sent him an email asking how he did it ... hopefully he remembers and replys (he is very busy and sometimes dosen't reply if not an emergency).
The above was the ONLY thing that stopped the emails. I first changed the password to access CF admin, then changed the mail authentication password (as per your pic) and neither stopped the emails. I finally stopped the CF Server service for a couple hours just to stop the emails, but when I started it again, the emails also started again.
You need to identify that IP and block it to stop the emails as far as I know ... good luck, this really sucks as I'm sure your finding out!
Max
The above was the ONLY thing that stopped the emails. I first changed the password to access CF admin, then changed the mail authentication password (as per your pic) and neither stopped the emails. I finally stopped the CF Server service for a couple hours just to stop the emails, but when I started it again, the emails also started again.
You need to identify that IP and block it to stop the emails as far as I know ... good luck, this really sucks as I'm sure your finding out!
Max
ASKER
Just looking closer at your log ... could the IP at the end of each line be the offending IP?
Max
Max
I'm afraid not, that IP takes me to our homepage, which worries me more, because i need to solve this tonight before tomorrow...
ASKER
My IT guys response:
"The firewall has a built in network sniffer” so all I do it turn on monitoring and it says originating IP and destination IP
That can be rather tricky to find without the appropriate tool
You MAY be able to find the culprit if you have access to the email server logs"
Not sure if that helps ... hopefully ...
Max
"The firewall has a built in network sniffer” so all I do it turn on monitoring and it says originating IP and destination IP
That can be rather tricky to find without the appropriate tool
You MAY be able to find the culprit if you have access to the email server logs"
Not sure if that helps ... hopefully ...
Max
Thanks very much MaxwellTurner you are doing magnificent job trying to help. given that the IT guy has replied swiftly to your inquiry, I'm wondering if you can show him that bit of the log and ask if blocking that IP address would solve the problem...
Thanks again, i have actually posted a question on this site waiting for expert opinion, because i am very anxious to solve, working out of hours 3 hours extra now to get to the bottom of this.
i really appreciate your help.
thank you
Thanks again, i have actually posted a question on this site waiting for expert opinion, because i am very anxious to solve, working out of hours 3 hours extra now to get to the bottom of this.
i really appreciate your help.
thank you
ASKER
You mentioned that IP on the log takes you to your home page, so that's YOUR domain ... definately don't want to block that. Good luck, I feel your pain. I'm lucky to have an awesome (but expensive) IT guy who saved my butt by blocking the IP.
6Gun
6Gun
MaxwellTurner going back to the answer you selected, were you able to actually track down any offending files? if yes where exactly ? was it on the server directory or the server installation files ? i address this question to RickEpnet as well if he would be a nice chap and contribute :)
ASKER
Now that you mention it, I remember coming across a thread about "h.cfm" which I promptly dealt with. I think this is the site I used as a resource, but there is plenty out there if you google that file name. I just searched my PC for it ... I think I found it in the /Coldfusion/Administrator folder (which I had wide open to the public! Doh!)
https://www.it.cornell.edu/services/alert.cfm?id=2419
Sorry I didn't think of this sooner ... it's been awhile already. Hopefully you have the emails stopped!
Max
https://www.it.cornell.edu/services/alert.cfm?id=2419
Sorry I didn't think of this sooner ... it's been awhile already. Hopefully you have the emails stopped!
Max
MaxwellTurner Hi again, we haven't been able to find any files looking like what you suggested. however going back to the IP issue, was the IP you blocked an external IP or an internal IP ? I still don't know where to look and what to block . The IP in the email Log points to the CF server itself, if we block that we block all outgoing email..... Can we get you IT guys input on this again please. if he can have a look at this log that would be great :
Aug 12 04:16:51 xena sendmail[29699]: [ID 801593 mail.info] s7C3GowY029699: from=<info73821@uel.ac.uk>, size=1021, class=0, nrcpts=1, msgid=<1919670134.204585.1407813410900.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29717]: [ID 801593 mail.info] s7C3Go7N029717: from=<info73821@uel.ac.uk>, size=1015, class=0, nrcpts=1, msgid=<234618192.204588.1407813410916.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29668]: [ID 801593 mail.info] s7C3GoXq029668: from=<info73821@uel.ac.uk>, size=1021, class=0, nrcpts=1, msgid=<101629610.204586.1407813410900.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29634]: [ID 801593 mail.info] s7C3GnNS029634: from=<info73821@uel.ac.uk>, size=1016, class=0, nrcpts=1, msgid=<447977052.204589.1407813410947.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29636]: [ID 801593 mail.info] s7C3GntC029636: from=<info73821@uel.ac.uk>, size=1026, class=0, nrcpts=1, msgid=<1529955728.204592.1407813410947.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29637]: [ID 801593 mail.info] s7C3GnuP029637: from=<info73821@uel.ac.uk>, size=1023, class=0, nrcpts=1, msgid=<72646582.204590.1407813410947.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29681]: [ID 801593 mail.info] s7C3Goje029681: from=<info73821@uel.ac.uk>, size=1018, class=0, nrcpts=1, msgid=<897836448.204594.1407813410947.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29633]: [ID 801593 mail.info] s7C3GnJE029633: from=<info73821@uel.ac.uk>, size=1023, class=0, nrcpts=1, msgid=<1717077714.204595.1407813410963.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29635]: [ID 801593 mail.info] s7C3GnaU029635: from=<info73821@uel.ac.uk>, size=1026, class=0, nrcpts=1, msgid=<2144214965.204593.1407813410947.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]
Aug 12 04:16:51 xena sendmail[29717]: [ID 801593 mail.info] s7C3Go7O029717: from=<info73821@uel.ac.uk>, size=1021, class=0, nrcpts=1, msgid=<1039890812.204596.1407813410963.JavaMail.CFSERVER$@CFSERVER>, proto=ESMTP, daemon=MTA, relay=cfserver.uel.ac.uk [172.21.248.38]ASKER
I just had a chat with him this morning. Unfortunatley he is leaving town for a seminar for 3 days and mostly unavailable expect for emergencies. I showed him your log file and he told me the same thing as before ... he can't tell from the log file itself. He said it was not easy to find the offending IP but our firewall has a 'sniffer' that monitors the network activity and and shows the says originating IP and destination IP. I really did not understand most of the techncal jargon he told me. I will fire him another email to see if he can give me more info on which IP to block ... hopefully I catch him before he gets onto the plane ... what type of firewall do you have?
We have a physical firewall (like a router) called Fortinet. He needed to log into the router to block the IP ... this is really way over my head from this point, which is why I have this independant guy taking care of my network. In our case the hacker somehow entered our firewall (and changed the password). My guy had to somehow find a back way into it and reset the password, then find the offending IP ... I am assuming due to the fact that it was sending 4 emails per second, it must have stood out with a high level of activity on the network. Without him I would have been screwed!
The only thing I can suggest is that you call in a good IT guy who knows this stuff ... might cost some $$ but you really need to stop those emails sooner than later! Wish I could help more ...
Max
We have a physical firewall (like a router) called Fortinet. He needed to log into the router to block the IP ... this is really way over my head from this point, which is why I have this independant guy taking care of my network. In our case the hacker somehow entered our firewall (and changed the password). My guy had to somehow find a back way into it and reset the password, then find the offending IP ... I am assuming due to the fact that it was sending 4 emails per second, it must have stood out with a high level of activity on the network. Without him I would have been screwed!
The only thing I can suggest is that you call in a good IT guy who knows this stuff ... might cost some $$ but you really need to stop those emails sooner than later! Wish I could help more ...
Max
MaxwellTurner What you explained makes perfect sense to me, i have sniffed the network traffic today, however the attack is not ongoing so there is no way to find a trace of IPs in subject because as your IT guy said the log file doesn't tell much. However the network sniffer cannot be running all the time as it stores a lot of data and that consumes a lot of storage, so it wasn't running on the day the attack took place ( which was last week) . But i will try to set it to only monitor email activity or anything suspicious and keep it running. I am working with an in house network specialist I am sure with our collaborative efforts we can pull this off, I will try to secure the server further, and we will wait and see if any malicious traffic plays on the network. By the way do you happen to remember on what intervals of time did the attacks take place, was it daily or weekly or just on going ? Thank you very much for your help. It's rare to find people dedicated to helping others like yourself...
ASKER
Hey, I know how much a situation like this sucks, so hopefully I helped abit. I think that is good you couldn't find h.cfm (or a variant) ... that is a good sign.
In my case, I noticed the hack about 16 hours after it started (it began at midnight). By noon, site users were complaining that they were not receiving confirmation emails etc ... so I checked the logs and noticed that it was sending out 4 emails per second for the last 16 hours ... that's alot of emails. Viewing the log, it did not appear that there had been any 'break time' and didn't seem to be any end in sight as my spooler was over-flowing. My IT guy had the firewall secured and IP blocked within 2 hours. The emails were going strong and steady at that time so that probably made it easier to identify.
However, prior to calling my IT guy, I changed passwords and had fixed the !serious issues HackMyCFM had found ... that alone didn't stop the emails ... my log just kept growing. My feeling was that they were ALREADY IN so the above changes wouldn't help unless they 'disconnected' and tried to get in again. Perhaps you have inadvertantly blocked them already by securing your CF server during a break in the emails.
Anyways, good luck. Glad to hear you have a handle on things and some hands on help!
Max
In my case, I noticed the hack about 16 hours after it started (it began at midnight). By noon, site users were complaining that they were not receiving confirmation emails etc ... so I checked the logs and noticed that it was sending out 4 emails per second for the last 16 hours ... that's alot of emails. Viewing the log, it did not appear that there had been any 'break time' and didn't seem to be any end in sight as my spooler was over-flowing. My IT guy had the firewall secured and IP blocked within 2 hours. The emails were going strong and steady at that time so that probably made it easier to identify.
However, prior to calling my IT guy, I changed passwords and had fixed the !serious issues HackMyCFM had found ... that alone didn't stop the emails ... my log just kept growing. My feeling was that they were ALREADY IN so the above changes wouldn't help unless they 'disconnected' and tried to get in again. Perhaps you have inadvertantly blocked them already by securing your CF server during a break in the emails.
Anyways, good luck. Glad to hear you have a handle on things and some hands on help!
Max
This is happening to us now - any details on what you did to resolve it would be greatly appreciated. Trying to track down the attacking IP address at this time. We use a third party company to send emails and have CF server pointing to their SMTP so didn't think this would happen here
Gdemaria, the first thing you need to do is sniff the network , using wire shark or any other tool
can we communicate with a quicker means , i am really interested in participating in this and helping to find a solution, are you on Lync ?
I don't have Lync, but gotoMeeting or could connect to it perhaps?
ASKER
Hi sorry ... been dealing with other issues today ... installing new SSL certs and CF can really suck!
I'm not sure I can add much more than is stated in this thread: Stop the emails (we did this by identifying and blocking the offending IP), then run HackMyCF to determine areas where your CF server may be insecure and lock it up by following their recommendations (so it never happens again). Also search your system for a file called h.cfm and delete if present (see link in post above which explains more and lists variants of this file)
Max
I'm not sure I can add much more than is stated in this thread: Stop the emails (we did this by identifying and blocking the offending IP), then run HackMyCF to determine areas where your CF server may be insecure and lock it up by following their recommendations (so it never happens again). Also search your system for a file called h.cfm and delete if present (see link in post above which explains more and lists variants of this file)
Max
My company is experiencing the same issue. I will circle with my network tech to start monitoring the network for when the offending party enters.
Working issue in following steps:
1) Get network tech on monitoring activity to the server.
2) Change CF admin password.
3) Visit HackMyCF.com and work identified issues.
4) Visit https://www.it.cornell.edu/services/alert.cfm?id=2419 and review/apply fix.
Thanks for everyone's work here...
Working issue in following steps:
1) Get network tech on monitoring activity to the server.
2) Change CF admin password.
3) Visit HackMyCF.com and work identified issues.
4) Visit https://www.it.cornell.edu/services/alert.cfm?id=2419 and review/apply fix.
Thanks for everyone's work here...
Sorry for the delay in response. Please see below for what has become of this situation:
First off, the server is very far behind in patching and was compromised with glaring security holes that are just plain embarrassing. This is my first exposure to CF server and CF application development so please understand I inherited this mess from my company and an outsourced third party vendor you may have heard about - HCL (Indian company).
After running the HackMyCF.com probe we decided to build a new server as this server was just plain old and compromised.
1) We never setup network monitoring on the server due to the extensive security holes.
2) CF admin password has been changed to a strong password.
3) HackMyCF.com provided the reports needed to show just how bad our situation is. Please see below for report.
4) The server was compromised with the h.cfm backdoor script...ugly it is.
hackmycf
ColdFusion Server Security Report
ColdFusion Version: 9,0,0,251028
Operating System: Windows 2003
Web Server: Microsoft-IIS/6.0
Probe Error: A probe error occurred please login and click Probe Test, or contact us for help.
• coldfusion.tagext.net.Http
We found 16 security issues on your server 123.456.789
* CRITICAL
Backdoor Discovered
Found /CFIDE/h.cfm that matched the signature of a backdoor script capable of manipulating the file system, running executables and running database queries remotely. Your server appears to have been compromised by an attacker.
* CRITICAL
Robust Exception Information is Enabled
Robust Exception Information is enabled which leads to path disclosure and partial source code disclosure
* CRITICAL
Cross Site Scripting Vulnerability CVE-2011-0583
CVE-2011-0583 detected. Apply the hotfixes located in Adobe Security Notice apsb11-04. The detection of this vulnerability also indicates to a high degree of likelihood that the following vulnerabilities may also exist: CVE-2011-0580, CVE-2011-0581, CVE-2011-0582, CVE-2011-0584
More Information: http://www.adobe.com/support/security/bulletins/apsb11-04.html
* CRITICAL
SSL Version 2 Enabled
Your Web Server is accepting SSL V2 connections, a weak protocol. For PCI compliance, and strong security you must disable this protocol on your web server.
More Information: http://foundeo.com/products/iis-weak-ssl-ciphers/
* CRITICAL
ComponentUtils Exposed to the Public
The /CFIDE/componentutils/ directory is open to the public it should be locked down to prevent exploit.
* CRITICAL
AdminAPI Exposed to the Public
The /CFIDE/adminapi/ directory is open to the public it should be locked down to prevent exploit.
* IMPORTANT
ColdFusion Administrator is Public
ColdFusion Administrator should be restricted by IP or blocked with Web Server password protection. Also consider requiring a SSL connection.
More Information: http://www.petefreitag.com/item/750.cfm
* IMPORTANT
Hotfix APSB11-14 Not Installed
Apply the hotfixes located in Adobe Security Notice apsb11-14.
More Information: http://www.adobe.com/support/security/bulletins/apsb11-14.html
* IMPORTANT
CFTOKEN is not a UUID
CFTOKEN should be set to use a UUID in the ColdFusion Administrator. Session ids may be very easy to guess if UUID's are not used.
* WARNING
The /CFIDE/scripts directory is in default location.
Consider changing the default location of /CFIDE/scripts/ by changing the value of the Default Script Src setting in the ColdFusion Administrator.
More Information: http://www.petefreitag.com/item/774.cfm
* WARNING
ColdFusion Documentation Public
The ColdFusion Server Documentation is public at /cfdocs/dochome.htm this identifies the ColdFusion server version you are using.
* WARNING
JSON Prefix is disabled
The Prefix serialized JSON with: // setting is not enabled in the ColdFusion Administrator. This is recommended for preventing JSON hijacking.
More Information: http://www.petefreitag.com/item/720.cfm
* WARNING
Server Header Version Disclosure
The HTTP Server header is disclosing version numbers. An attacker may use this to identify your server as vulnerabilities become known matching the version you are using.
More Information: http://www.petefreitag.com/item/419.cfm
* WARNING
Server Software Disclosure
Your web server responds to each request with an unnecessary HTTP header X-Powered-By which contains information about software installed on the server. This information may be used to target your site as vulnerabilities become known.
More Information: http://www.petefreitag.com/item/722.cfm
* WARNING
Session Cookies are not marked HTTPOnly
Using HTTPOnly cookies prevents the session cookies from being hijacked via a javascript XSS attack on modern browsers.
More Information: http://www.petefreitag.com/item/764.cfm
* WARNING
ColdFusion 9 Update Available
You may not be running the latest version of ColdFusion 9, consider updating to ColdFusion 9.0.1
More Information: http://kb2.adobe.com/cps/849/cpsid_84973.html
Please note, this tool is not able to test for all potential security issues that may exist.
Severity Key
* CRITICAL
Found 6 Critical Issues
These issues pose a significant security risk. It is imperative that they are resolved at once.
* IMPORTANT
Found 3 Important Issues
These issues may have a security risk in certain conditions. It is recommended that you resolve them.
* WARNING
Found 7 Warnings
You should consider fixing these issues, however, they do not pose a large risk.
* ERROR
We experienced 1 error
Errors may occurr as a result of a connection problem.
After running the HackMyCF.com probe we decided to build a new server as this server was just plain old and compromised.
Thanks for everyone's post that assisted.
First off, the server is very far behind in patching and was compromised with glaring security holes that are just plain embarrassing. This is my first exposure to CF server and CF application development so please understand I inherited this mess from my company and an outsourced third party vendor you may have heard about - HCL (Indian company).
After running the HackMyCF.com probe we decided to build a new server as this server was just plain old and compromised.
1) We never setup network monitoring on the server due to the extensive security holes.
2) CF admin password has been changed to a strong password.
3) HackMyCF.com provided the reports needed to show just how bad our situation is. Please see below for report.
4) The server was compromised with the h.cfm backdoor script...ugly it is.
hackmycf
ColdFusion Server Security Report
ColdFusion Version: 9,0,0,251028
Operating System: Windows 2003
Web Server: Microsoft-IIS/6.0
Probe Error: A probe error occurred please login and click Probe Test, or contact us for help.
• coldfusion.tagext.net.Http
We found 16 security issues on your server 123.456.789
* CRITICAL
Backdoor Discovered
Found /CFIDE/h.cfm that matched the signature of a backdoor script capable of manipulating the file system, running executables and running database queries remotely. Your server appears to have been compromised by an attacker.
* CRITICAL
Robust Exception Information is Enabled
Robust Exception Information is enabled which leads to path disclosure and partial source code disclosure
* CRITICAL
Cross Site Scripting Vulnerability CVE-2011-0583
CVE-2011-0583 detected. Apply the hotfixes located in Adobe Security Notice apsb11-04. The detection of this vulnerability also indicates to a high degree of likelihood that the following vulnerabilities may also exist: CVE-2011-0580, CVE-2011-0581, CVE-2011-0582, CVE-2011-0584
More Information: http://www.adobe.com/support/security/bulletins/apsb11-04.html
* CRITICAL
SSL Version 2 Enabled
Your Web Server is accepting SSL V2 connections, a weak protocol. For PCI compliance, and strong security you must disable this protocol on your web server.
More Information: http://foundeo.com/products/iis-weak-ssl-ciphers/
* CRITICAL
ComponentUtils Exposed to the Public
The /CFIDE/componentutils/ directory is open to the public it should be locked down to prevent exploit.
* CRITICAL
AdminAPI Exposed to the Public
The /CFIDE/adminapi/ directory is open to the public it should be locked down to prevent exploit.
* IMPORTANT
ColdFusion Administrator is Public
ColdFusion Administrator should be restricted by IP or blocked with Web Server password protection. Also consider requiring a SSL connection.
More Information: http://www.petefreitag.com/item/750.cfm
* IMPORTANT
Hotfix APSB11-14 Not Installed
Apply the hotfixes located in Adobe Security Notice apsb11-14.
More Information: http://www.adobe.com/support/security/bulletins/apsb11-14.html
* IMPORTANT
CFTOKEN is not a UUID
CFTOKEN should be set to use a UUID in the ColdFusion Administrator. Session ids may be very easy to guess if UUID's are not used.
* WARNING
The /CFIDE/scripts directory is in default location.
Consider changing the default location of /CFIDE/scripts/ by changing the value of the Default Script Src setting in the ColdFusion Administrator.
More Information: http://www.petefreitag.com/item/774.cfm
* WARNING
ColdFusion Documentation Public
The ColdFusion Server Documentation is public at /cfdocs/dochome.htm this identifies the ColdFusion server version you are using.
* WARNING
JSON Prefix is disabled
The Prefix serialized JSON with: // setting is not enabled in the ColdFusion Administrator. This is recommended for preventing JSON hijacking.
More Information: http://www.petefreitag.com/item/720.cfm
* WARNING
Server Header Version Disclosure
The HTTP Server header is disclosing version numbers. An attacker may use this to identify your server as vulnerabilities become known matching the version you are using.
More Information: http://www.petefreitag.com/item/419.cfm
* WARNING
Server Software Disclosure
Your web server responds to each request with an unnecessary HTTP header X-Powered-By which contains information about software installed on the server. This information may be used to target your site as vulnerabilities become known.
More Information: http://www.petefreitag.com/item/722.cfm
* WARNING
Session Cookies are not marked HTTPOnly
Using HTTPOnly cookies prevents the session cookies from being hijacked via a javascript XSS attack on modern browsers.
More Information: http://www.petefreitag.com/item/764.cfm
* WARNING
ColdFusion 9 Update Available
You may not be running the latest version of ColdFusion 9, consider updating to ColdFusion 9.0.1
More Information: http://kb2.adobe.com/cps/849/cpsid_84973.html
Please note, this tool is not able to test for all potential security issues that may exist.
Severity Key
* CRITICAL
Found 6 Critical Issues
These issues pose a significant security risk. It is imperative that they are resolved at once.
* IMPORTANT
Found 3 Important Issues
These issues may have a security risk in certain conditions. It is recommended that you resolve them.
* WARNING
Found 7 Warnings
You should consider fixing these issues, however, they do not pose a large risk.
* ERROR
We experienced 1 error
Errors may occurr as a result of a connection problem.
After running the HackMyCF.com probe we decided to build a new server as this server was just plain old and compromised.
Thanks for everyone's post that assisted.