Stop, Think, Decide THEN "Click".
Published:
Browse All Articles > Stop, Think, Decide THEN "Click".
This article summarizes using a simple matrix to map the different type of phishing attempts and its targeted victims. It also run through many scam scheme scenario with "real" phished emails. There are safeguards highlighted to stay vigilance and heighten one's vigilance.
You should not underestimate the power of your single mouse click.
Danger of just one (simple) click!
A recent "one-click" fraud in Japan (also targeting the Chinese) started a trail of nuisances and extortion experiences (see the persistent pop up window) for many who have regretted their action.
![nuisance-popup-pestering-forclick.png]() Even in mobile browsing the user is not spared. He browses for apps on his iPhone and downloads despite Apple's warning, and it is "Game Over" when the app demands payment to a subscription or service.
Even in mobile browsing the user is not spared. He browses for apps on his iPhone and downloads despite Apple's warning, and it is "Game Over" when the app demands payment to a subscription or service.
![mobile-app-ransom.JPG]()
In early January 2015, the sad story of the massacre at the Charlie Hebdo offices in Paris prompted hackers abusing the news to send out malicious emails to their pool of victims. They exploited the story by going viral with the #JeSuisCharlie twitter hashtag, setting the email's subject to "Jesuis Charlie" -- and attaching malware.
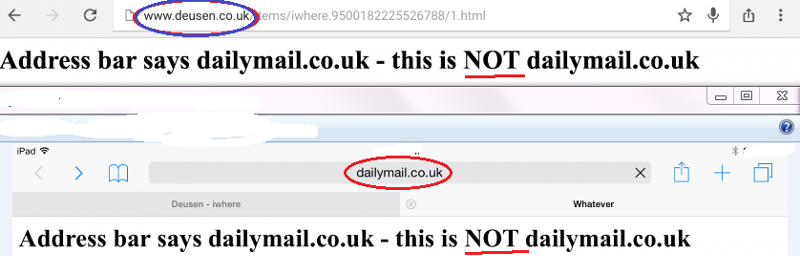
Users are not trained to identify phishing sites. See the image below. How do you know if this site is real (blue) or an imposter (red) site - simply seeing only the displayed URL. It is not easy. In fact, publicly released code exploits a Safari browser vulnerability to mislead the user to what "seems" to be an actual site but is not.
![realvsfake.png]() One wrong click is all it takes.
One wrong click is all it takes.
There are already many "success" stories (as APWG shared) of users falling into such traps across industry sectors. In the Sony Pictures case, the "phished" email also came with extortion in the strings of damaging outcomes.
![Extortion.JPG]()
A recent Verizon breach 2015 report (pdf) said that users open phishing emails and click on malicious links within the first hour they're sent out. More and more users are falling for such bait; ten emails have a 90% chance of at least one victim. The average time between a malicious email being sent and the first person clicking on a link is one minute and 22 seconds.
A study (pdf) by Proofpoint also highlighted such trends: email threats work around the clock (39% of malicious links are clicked in first 24 hours upon arrival and 65% clicked even after one week of receipt. There is no rest time (10am and 6pm ET are the "peak" hours though). In other words, everyone is vulnerable anytime and anywhere (home or office).
The "power" of our own click on that innocent email
There is a study on achieving higher success using much more "enriched" phishing email to alter recipients' cognitive processes. The long and short of it is that simply making an email message have its "presence" felt by recipient will cause the recipient to respond to such messages' demands. Human are vulnerable when emotion gets the better of their logical thought processes.
We need to stop and pause to filter out the red flags in email received. Below is a phisher's matrix on the likely phishing scheme (in orange) and type of victim (in blue) who will fall into the email traps.
![Phishing-Target-Matrix.JPG]()
Conscious Victim - Has good appreciation of the evolving phishing threat but is careless in the sense that they easily let their guard down and fall for the phishing email.
![DyerWolfAttackSteps.jpg]()
![Quick-Thorough--outlook-URL-.JPG]() Cynical Victim - Has poor appreciation and tends to be sceptical about known threats as they are not convinced they can be penetrated since they are diligent in in their constant threat mitgation and remediation exercises. They tend to be over-confident.
Cynical Victim - Has poor appreciation and tends to be sceptical about known threats as they are not convinced they can be penetrated since they are diligent in in their constant threat mitgation and remediation exercises. They tend to be over-confident.
![Learning-Fast--LinkedIn-Local-.JPG]()
The security company Phishme shared another obfuscation scheme in its blog where two emails are sent. The first email is an innocent non-malicious lure (building up rapport with target) and is followed up with a second malicious email (enticing target to click on embedded link or attachment). It attempts to lower the user's vigilance.![DoubleBarrel.JPG]() Complacent Victim - Has poor appreciation of threats and does not pay any attention to warnings or is even aware of what are those red flags in the first place. They trust others easily and very gullible and fearful.
Complacent Victim - Has poor appreciation of threats and does not pay any attention to warnings or is even aware of what are those red flags in the first place. They trust others easily and very gullible and fearful.
![Simple-Dangerous--helpdesk-.JPG]()
There are many red flags but the user falls for it still, most due to ignorance but for some of them, they simply too trustworthy as it seems to be "legit" on their used account. There are variants on this scheme. Recently one was shared seemingly from their "trusted" internal administrator with an email crafted from user's subscribed server provider. This user group has no chance against these phishers. One click on that link is just what it takes to allow the phisher free delivery of packed malicious exploits. Ouch!![Capture.JPG]() Competent Victim - Has good appreciation of threats and most diligent among all other victim types. They are proactive and readily defend and are alert to red flags detected in phishing emails. They stay guarded and likely warn others as security trainers or trusted advisors in their organisation.
Competent Victim - Has good appreciation of threats and most diligent among all other victim types. They are proactive and readily defend and are alert to red flags detected in phishing emails. They stay guarded and likely warn others as security trainers or trusted advisors in their organisation.
![Personalised-Targeted--URL-tricky-.JPG]()
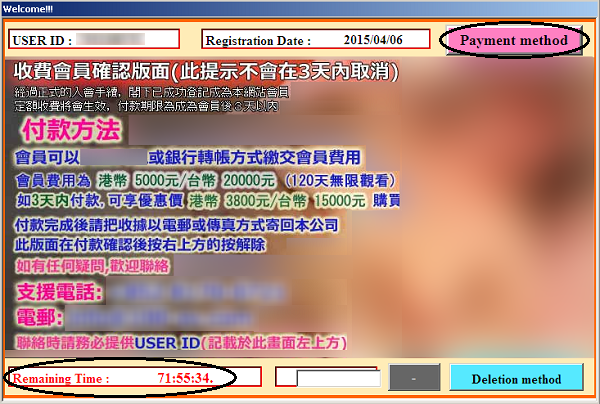
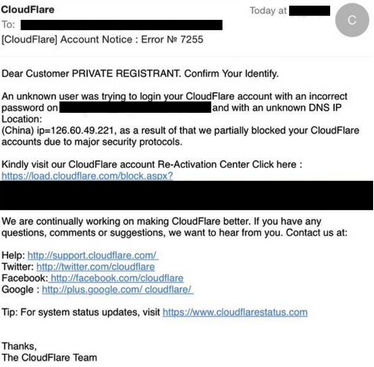
This email is especially crafted with many links presumably from Cloudflare saying your site acount is locked for time being. Fear and worry kicks in and follow through promises quick relief. The link leads to a compromised site hosted by other provider. What you see is not what you click sadly - a quick mouseover would reveal the link's mismatch. Behind the scene, the phisher is still gathering the victim's real Cloudflare login credentials.![cloudflarebased-phishEm.png]()
The CloudFlare blog shares some other good red flags to watch out for, but they require more technical knowledge that the normal user who just wants to surf safely might understand. Here is one take away: All the URLs below go to 74.125.131.105 - just hover to see if you see such links (before clicking. These links in this article below are edited as not "clickable" in case you hover over them):
Phishing kits (with PHP files used often) are readily available to make scammer pull off their campaign in quick fashion. One scheme is on local "drop box" creation instead of using the usual malicious web links in email.
Scheme - Use a HTML attachment that, when the victim opens it, is stored locally temporarily in victim machine. Present a clone of a legitimate site requesting their personal information. Victims fall for it by submitting the "online" form.
Beware - The data in the form are collected and send to phisher's drop box or repository for their future retrieval. Law enforcers cannot easily detect local content persistently stored within the machine.
Targets are specially chosen. HR staffs are gaining popularity among phishers. An email can be specially crafted to appeal to HR staffers and much of the time they will click open the email and its attachment of a "prospective employee". Otherwise, it will be the URL to Google Drive or OneDrive to download those resumes and supporting job credentials. Phishers understand this well and exploit it further. Below is an instance where the phishers do more than just being selective in the target; they create hops to evade security checks in place. Security engines miss these due to the use of known legitimate resources hosting the files. Ouch!
![mobile-app-ransom-1.JPG]() When the zipped file is opened locally, it all leads to some compromised website, and WordPress is popular due to the many low hanging vulnerabilities that are not readily patched. The malware is downloaded stealthily via an iFrame onto the machine. Gameover!
When the zipped file is opened locally, it all leads to some compromised website, and WordPress is popular due to the many low hanging vulnerabilities that are not readily patched. The malware is downloaded stealthily via an iFrame onto the machine. Gameover!
![phished-local-html-google-drv.JPG]() Smarter phishers go for bypasses exploiting design flaws. These measures include use of Sender Policy Framework (SPF) rules and Domain-based Message Authentication, Reporting and Conformance (DMARC) record for email services.
Smarter phishers go for bypasses exploiting design flaws. These measures include use of Sender Policy Framework (SPF) rules and Domain-based Message Authentication, Reporting and Conformance (DMARC) record for email services.
If possible, do not even think about clicking any link in the email. I know that can be impossible. KnowBe4, which specialises in security awareness active teaching, collated statistics for 30 days and listed a snapshot on types of email users usually will not even give a second thought, easily clicking as requested.
![C--Users-s7737795f-Desktop-phishFinalmsg]()
This "Dear Supplier" scam is a cybercriminal looking for all your possible ongoing official correpondence with customers engaged in a payment discussion. Upon finding it, they then give false account information to your customers, who will trust the email is from you and just send the payment to your stated company account, which is actually owned by the cybercriminal.
We can only stay vigilant and exercise caution when clicking on enticing links sent through emails. Institute one simple principle in the mindset - "If something looks too good to be true, then it likely is". One example below is a document asking user to enable the macros (not "macroses") to view the document (and unleash the malware onslaught):
![dyre-macro.JPG]()
Be realistic, exercise your senses and if a real phishing email or scam email shows up, remember the teachable moment. Ask yourself question before the next click.
![phishingcheck-showoriginal.JPG]()
You are the ultimate gatekeeper
Final points as parting "gifts" for your next "Stop, Decide and Then Click".
Safe email reading to all!
PS - If you are keen to know more real life experience sharing, I recommend this as reading "leisure". A lesson learned through hard truth. Also I see this sum up countermeasures that go beyond as an individual safeguards but for an organisation (worth considering to share with IT team).
Danger of just one (simple) click!
A recent "one-click" fraud in Japan (also targeting the Chinese) started a trail of nuisances and extortion experiences (see the persistent pop up window) for many who have regretted their action.
 Even in mobile browsing the user is not spared. He browses for apps on his iPhone and downloads despite Apple's warning, and it is "Game Over" when the app demands payment to a subscription or service.
Even in mobile browsing the user is not spared. He browses for apps on his iPhone and downloads despite Apple's warning, and it is "Game Over" when the app demands payment to a subscription or service.
In early January 2015, the sad story of the massacre at the Charlie Hebdo offices in Paris prompted hackers abusing the news to send out malicious emails to their pool of victims. They exploited the story by going viral with the #JeSuisCharlie twitter hashtag, setting the email's subject to "Jesuis Charlie" -- and attaching malware.
Users are not trained to identify phishing sites. See the image below. How do you know if this site is real (blue) or an imposter (red) site - simply seeing only the displayed URL. It is not easy. In fact, publicly released code exploits a Safari browser vulnerability to mislead the user to what "seems" to be an actual site but is not.
 One wrong click is all it takes.
One wrong click is all it takes.
There are already many "success" stories (as APWG shared) of users falling into such traps across industry sectors. In the Sony Pictures case, the "phished" email also came with extortion in the strings of damaging outcomes.
A recent Verizon breach 2015 report (pdf) said that users open phishing emails and click on malicious links within the first hour they're sent out. More and more users are falling for such bait; ten emails have a 90% chance of at least one victim. The average time between a malicious email being sent and the first person clicking on a link is one minute and 22 seconds.
A study (pdf) by Proofpoint also highlighted such trends: email threats work around the clock (39% of malicious links are clicked in first 24 hours upon arrival and 65% clicked even after one week of receipt. There is no rest time (10am and 6pm ET are the "peak" hours though). In other words, everyone is vulnerable anytime and anywhere (home or office).
The "power" of our own click on that innocent email
There is a study on achieving higher success using much more "enriched" phishing email to alter recipients' cognitive processes. The long and short of it is that simply making an email message have its "presence" felt by recipient will cause the recipient to respond to such messages' demands. Human are vulnerable when emotion gets the better of their logical thought processes.
We need to stop and pause to filter out the red flags in email received. Below is a phisher's matrix on the likely phishing scheme (in orange) and type of victim (in blue) who will fall into the email traps.
Conscious Victim - Has good appreciation of the evolving phishing threat but is careless in the sense that they easily let their guard down and fall for the phishing email.
Quick & Thorough Phishing Scheme - Hijackers use compromised accounts closely related to the victim to send out the phishing email. To avoid the victim's quick detection or recovery, they also have to quickly "vacuum" the victims' details (like bank or social media accounts) and often lock out victims out by changing logins and passwords. They can even go to the extent of hosting a call center to socially engineer victims. A recent IBM infographic on Dyre malware shows a good example of ongoing e-banking fraud involving millions of dollars.
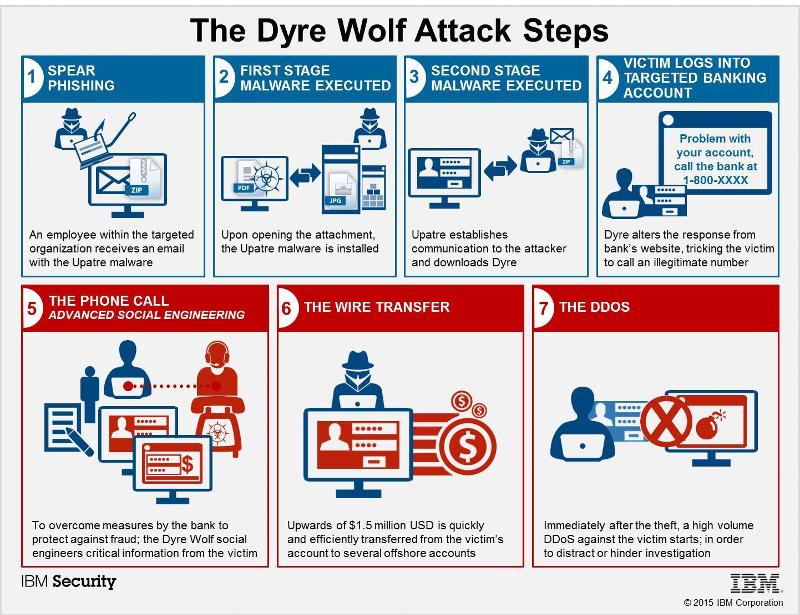
The wire transfer fraud has also been recently highlighted in Financial service Information Sharing and Analysis Center (FS-ISAC) alert (pdf), they alluded such scam as "Business E-mail Compromise" (BEC). In short, phisher use a compromise account and send a "High Importance" email asking for immediate wires transfer. The account is normally someone of high authority and "trust" whom the recipient without doubt may execute as instructed. One example of the phished email below.
![pphishedBECCapture.JPG]()
More often also, the phisher counts on victim carelesness in failing to spot a spoofed site's content that runs in non-secure mode, which is highly uncommon for money transfer sites. Below is a typical phishing email "toying" the victim's sense of urgency by warning his next payment to his loan may be lost or delayed if he does not update his login records at the phisher's "secure" fake website. Once the victim has been tricked into visiting the fake site, he will be prompted to enter information that can be used to steal the loan money as soon as it arrives in his bank account.
More often also, the phisher counts on victim carelesness in failing to spot a spoofed site's content that runs in non-secure mode, which is highly uncommon for money transfer sites. Below is a typical phishing email "toying" the victim's sense of urgency by warning his next payment to his loan may be lost or delayed if he does not update his login records at the phisher's "secure" fake website. Once the victim has been tricked into visiting the fake site, he will be prompted to enter information that can be used to steal the loan money as soon as it arrives in his bank account.
Learning Fast Phishing Scheme - Hijackers still use old tactics to scam this group, but need to adapt quickly to change their tactics as the victim is proactive on security alerts. The latter reacts diligently to security advisories published. One common approach is obscuring via URL shortening to hide the actual malicious URL. As below, attachment just add to further obscured those links.
The security company Phishme shared another obfuscation scheme in its blog where two emails are sent. The first email is an innocent non-malicious lure (building up rapport with target) and is followed up with a second malicious email (enticing target to click on embedded link or attachment). It attempts to lower the user's vigilance.
Simple & Dangerous Phishing Scheme - Hijackers see this group as easy kill. This gives them immediate rewards and they need not use any specialised phishing tools or custom hooks in their arsenal. They reuse, recycle (see below) and simply have phished email crafted to evoke strong emotions. The reason for targeting this victim group is really to build up hijacker's pool of money mule recruits and profitting using them to offer their "value add" cybercrime services offer to other phishers through covert dark marketplace.
There are many red flags but the user falls for it still, most due to ignorance but for some of them, they simply too trustworthy as it seems to be "legit" on their used account. There are variants on this scheme. Recently one was shared seemingly from their "trusted" internal administrator with an email crafted from user's subscribed server provider. This user group has no chance against these phishers. One click on that link is just what it takes to allow the phisher free delivery of packed malicious exploits. Ouch!
Personalised & Targeted Phishing Scheme - Hijackers need to do more homework against this victim group. They use lures from harvested close contacts, and reuse well-known global news to entice victims to fall for the email traps, and are not successful easily. Hence, more often than not, a personal touch is needed to engage and hook them. The crafted email can seemingly from the target's bosses, or can fake the recipient's internal mass mailing list to add some work related realism, causing victims to lower their guards.
This email is especially crafted with many links presumably from Cloudflare saying your site acount is locked for time being. Fear and worry kicks in and follow through promises quick relief. The link leads to a compromised site hosted by other provider. What you see is not what you click sadly - a quick mouseover would reveal the link's mismatch. Behind the scene, the phisher is still gathering the victim's real Cloudflare login credentials.
The CloudFlare blog shares some other good red flags to watch out for, but they require more technical knowledge that the normal user who just wants to surf safely might understand. Here is one take away: All the URLs below go to 74.125.131.105 - just hover to see if you see such links (before clicking. These links in this article below are edited as not "clickable" in case you hover over them):
http://www.safesite.com@74.125.131.105Phishing schemes are evolving!
http://www.safesite.com@1249739625/
http://www.safesite.com@0x4a.0x7d.0x83.0x69/
http://www.safesite.com@0112.0175.0203.0151/
Phishing kits (with PHP files used often) are readily available to make scammer pull off their campaign in quick fashion. One scheme is on local "drop box" creation instead of using the usual malicious web links in email.
Scheme - Use a HTML attachment that, when the victim opens it, is stored locally temporarily in victim machine. Present a clone of a legitimate site requesting their personal information. Victims fall for it by submitting the "online" form.
Beware - The data in the form are collected and send to phisher's drop box or repository for their future retrieval. Law enforcers cannot easily detect local content persistently stored within the machine.
Targets are specially chosen. HR staffs are gaining popularity among phishers. An email can be specially crafted to appeal to HR staffers and much of the time they will click open the email and its attachment of a "prospective employee". Otherwise, it will be the URL to Google Drive or OneDrive to download those resumes and supporting job credentials. Phishers understand this well and exploit it further. Below is an instance where the phishers do more than just being selective in the target; they create hops to evade security checks in place. Security engines miss these due to the use of known legitimate resources hosting the files. Ouch!
- Scheme (1) - Source with SPF rules restrict who can send emails and appear to come from them.
- Beware - The key is this can be false impression as it "appear" to be from sender. Do we verify with sender?
- Scheme (2) - Source with a DMARC record act on forged emails that are outside actual real domain.
- Beware - This is effective but it is not necessarily implemented widely yet by all email providers. Forged emails instead phisher send out to victims DMARC "true" email statistics as if it is implemented, but not.
If possible, do not even think about clicking any link in the email. I know that can be impossible. KnowBe4, which specialises in security awareness active teaching, collated statistics for 30 days and listed a snapshot on types of email users usually will not even give a second thought, easily clicking as requested.
- Change Of Password Required Immediately - 16.49%
- Email Account Updates - 9.92%
- Low Balance Alert On Primary Savings - 7.59%
- Your Friend Tagged a Photo of You - 7.49%
- Join my network on LinkedIn - 7.45%
- "Hey, has your Adult Friend Finder Secret come out?" - 3.4%
This "Dear Supplier" scam is a cybercriminal looking for all your possible ongoing official correpondence with customers engaged in a payment discussion. Upon finding it, they then give false account information to your customers, who will trust the email is from you and just send the payment to your stated company account, which is actually owned by the cybercriminal.
We can only stay vigilant and exercise caution when clicking on enticing links sent through emails. Institute one simple principle in the mindset - "If something looks too good to be true, then it likely is". One example below is a document asking user to enable the macros (not "macroses") to view the document (and unleash the malware onslaught):
Be realistic, exercise your senses and if a real phishing email or scam email shows up, remember the teachable moment. Ask yourself question before the next click.
- Who are those weakest links e.g. user groups or user in specific?
- What phishing scheme are getting by controls not thoroughly tested and exercised?
- When has phishing scheme ever work successfully (debunk existing false impression the controls are effective)?
- Where is anti-phishing in the CIO priority list (is this a widely topic discussed at board meeting)?
- Why is a proactive anti-phishing campaign worthwhile?
You are the ultimate gatekeeper
Final points as parting "gifts" for your next "Stop, Decide and Then Click".
- Have I been pwned....? If you are interested to know if your email has been compromised and abused already, here is one site to check against reported breaches... pray it is alright ...
- Have I learned something after reading this article? So do you think the below is legitimate? ... Hopefully you got it right... (Yes it is obvious. Just avoid any click on ANY links in the email unless you really sure those are safe. Nothing beats having not doing anything uncertain.)
- Err on safe side - never trust these very common fake email tricks. The attack starts with click on an embedded link.
- Google Chrome email - As a browser update notification to download a fake "package" using the legitimate Chrome icon.
- Facebook email - As account suspension notification to change and reset the account for re-logon.
- PayPal email - As urgent "Take Action PayPal" email to re-logon and settle an urgent alert.
- Scratching your head on what to do next and what viable options are available? Check out this light-hearted means to get that "scratch" away and have your users really take the "Stop, Think, Decide Then Click" preaching seriously. This is definitely not the only instance you can explore. A simple browser extension can help to tell if a website is a potentially compromised site. One instance is the NetCraft extension. The coast is clear for EE itself (phew!).
Safe email reading to all!
PS - If you are keen to know more real life experience sharing, I recommend this as reading "leisure". A lesson learned through hard truth. Also I see this sum up countermeasures that go beyond as an individual safeguards but for an organisation (worth considering to share with IT team).
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.

Comments (2)
Commented:
Author
Commented: