Browse All Articles > Troubleshooting Browser Hijacking/Redirection
Unfortunately, one of the common effects of a malicious infection on systems today is the prevention of a computer's ability to browse to specific web sites, especially those sites associated with downloading security patches and anti-virus software updates. Commonly referred to as Browser Hijacking, this malicious technique can be used by hackers to control how your computer accesses the Internet as well as change various settings within your web browser. While Windows-based systems using Internet Explorer as the web browser are typically targeted, other browsers and operating systems are susceptible to similar Hijacking attacks.
It is important to remember that, once a system is compromised, the only true way to guarantee that the system is free of infection is to re-install the system's operating system from valid installation media. Attempting to resolve various symptoms and effects of an infection can still leave the system affected and possibly vulnerable to further compromise.
A successful hijacking of a system can redirect the system's browser by using several techniques which can include any of the following, but are not limited to:
- Changing the system's browser settings (Homepage, bookmarks, etc)
- Modifying the system's local HOSTS file
- Updating the system's local Registry
NOTE - Before using any of the following suggestions to resolve the effects of Browser Hijacking on a system, it is important that the machine's infection be removed. Otherwise, any manual changes made during the resolution process will more than likely be overridden by the malicious process. Please follow standard anti-virus and anti-spyware procedures when attempting to remove an infection.
Resolving Browser Setting Changes
Typically the easiest of the malicious changes to address, most browser settings that were changed by the Browser Hijacking can be resolved by resetting the browser's settings manually. For instance, if a browser's homepage was changed to point to a different site such as maliciousdomain.com rather than its default of msn.com, the browser's homepage can be manually updated to once again point to msn.com. Fortunately, most current versions of browsers today prevent unauthorized changes to a browser's settings.
Additionally, some hijacking attacks add favorite links to your browsers list of "Bookmarks" or "Favorites". Make sure to delete these entries as they could point your browser to a website for further compromising your system or some other nefarious purpose.
Examining your HOSTS File
One of the main changes made to a compromised system by Browser Hijacking is preventing the affected system from being able to access websites associated with anti-virus providers. For example, if a system is installed with a Trend Micro anti-virus client, the system is prevented from receiving virus signature updates or performing online virus scans using Trend Micro's online anti-virus scanner 'House Call'.
In these instances, typically the compromised system's HOSTS file has been edited without the knowledge of the system's user. The HOSTS file is responsible for assisting with the resolution of Internet domain and computer names to IP addresses which a browser needs to access websites remotely over the Internet. For example, if you attempt to access windowsupdate.microsoft.com with your browser, your system will consult the local HOSTS file to see if your computer already has an IP address for windowsupdate.microsoft.com. If the information is listed in the HOSTS file, then your browser will use this information in an attempt to load the website rather than attempting to consult your ISP's DNS servers for resolution.
In Windows, the HOSTS file is stored by default in the C:\WINDOWS\System32\Drivers\etc folder. Note that the HOSTS file does not have an extension such as .txt to indicate it is a text file, but you can open it in Notepad for examination.
![Compromised HOSTS File]()
In the above example, you can see that the HOSTS file has been maliciously changed to not only redirect windowsupdate.microsoft.com to the local machine, effectively disabling access to the website, but the file also redirects www.google.com to an IP address in China which could host a malicious copy of the Google homepage. Additionally, access to windowsupdate.microsoft.com has been prevented by resolving the domain name to the local machine's IP address.
To resolve any malicious entries in the HOSTS file, remove each line that is not needed and save the file, remembering to save the file as HOSTS - without any extension.
Reviewing your Registry
Often, many of the settings that have been changed by a successful Browser Hijacking can be found in the Windows' Registry. After manually resetting your browser and inspecting your HOSTS file, you should run a search within your compromised system's Registry for the presence of any domain names your system is having issues accessing or that is has been re-directed to. For example, if your browser has been redirected to maliciousdomain.com, you'll want to run a search for maliciousdomain.com in your Registry and delete any instances you might find (see below).
![Searching the Windows' Registry]()
As you can see, Browser Hijacking can not only be annoying to computer users, but can also indicate that a system's security has been severely compromised. While various effects of a successful Hijacking attack can be resolved, a compromised system should have its operating system installed from official media to ensure the system is no longer affected by a malicious party.
It is important to remember that, once a system is compromised, the only true way to guarantee that the system is free of infection is to re-install the system's operating system from valid installation media. Attempting to resolve various symptoms and effects of an infection can still leave the system affected and possibly vulnerable to further compromise.
A successful hijacking of a system can redirect the system's browser by using several techniques which can include any of the following, but are not limited to:
- Changing the system's browser settings (Homepage, bookmarks, etc)
- Modifying the system's local HOSTS file
- Updating the system's local Registry
NOTE - Before using any of the following suggestions to resolve the effects of Browser Hijacking on a system, it is important that the machine's infection be removed. Otherwise, any manual changes made during the resolution process will more than likely be overridden by the malicious process. Please follow standard anti-virus and anti-spyware procedures when attempting to remove an infection.
Resolving Browser Setting Changes
Typically the easiest of the malicious changes to address, most browser settings that were changed by the Browser Hijacking can be resolved by resetting the browser's settings manually. For instance, if a browser's homepage was changed to point to a different site such as maliciousdomain.com rather than its default of msn.com, the browser's homepage can be manually updated to once again point to msn.com. Fortunately, most current versions of browsers today prevent unauthorized changes to a browser's settings.
Additionally, some hijacking attacks add favorite links to your browsers list of "Bookmarks" or "Favorites". Make sure to delete these entries as they could point your browser to a website for further compromising your system or some other nefarious purpose.
Examining your HOSTS File
One of the main changes made to a compromised system by Browser Hijacking is preventing the affected system from being able to access websites associated with anti-virus providers. For example, if a system is installed with a Trend Micro anti-virus client, the system is prevented from receiving virus signature updates or performing online virus scans using Trend Micro's online anti-virus scanner 'House Call'.
In these instances, typically the compromised system's HOSTS file has been edited without the knowledge of the system's user. The HOSTS file is responsible for assisting with the resolution of Internet domain and computer names to IP addresses which a browser needs to access websites remotely over the Internet. For example, if you attempt to access windowsupdate.microsoft.co
In Windows, the HOSTS file is stored by default in the C:\WINDOWS\System32\Driver
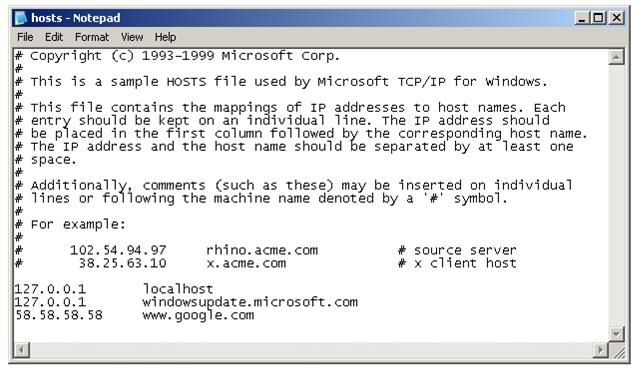
In the above example, you can see that the HOSTS file has been maliciously changed to not only redirect windowsupdate.microsoft.co
To resolve any malicious entries in the HOSTS file, remove each line that is not needed and save the file, remembering to save the file as HOSTS - without any extension.
Reviewing your Registry
Often, many of the settings that have been changed by a successful Browser Hijacking can be found in the Windows' Registry. After manually resetting your browser and inspecting your HOSTS file, you should run a search within your compromised system's Registry for the presence of any domain names your system is having issues accessing or that is has been re-directed to. For example, if your browser has been redirected to maliciousdomain.com, you'll want to run a search for maliciousdomain.com in your Registry and delete any instances you might find (see below).
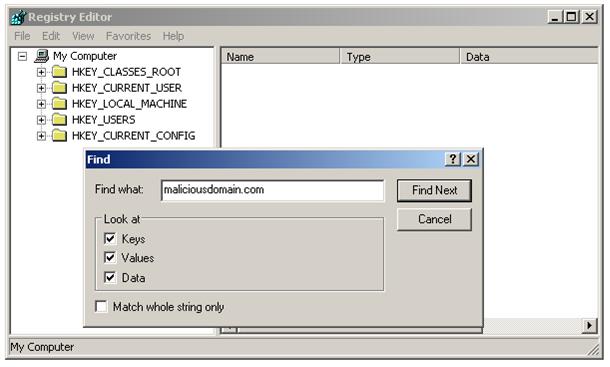
As you can see, Browser Hijacking can not only be annoying to computer users, but can also indicate that a system's security has been severely compromised. While various effects of a successful Hijacking attack can be resolved, a compromised system should have its operating system installed from official media to ensure the system is no longer affected by a malicious party.
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (1)
Commented: