Browse All Articles > How to Survive the Cloud Security Minefield
In today's information driven age, entrepreneurs have so many great tools and options at their disposal to help turn good ideas into a thriving business. With cloud-based online services, such as Amazon's Web Services (AWS) or Microsoft's Azure, business startups and founders can ramp up with new web servers, blogs and data stores more rapidly and affordable than ever before.
![Cloud Security]()
The cloud presents great business opportunities, but it can also lead to legal and financial hot water if you cut corners. Skipping or glossing over data protection safeguards can of course lead to brand damage, financial penalties, loss of customer trust and even put you out of business.
To help startups and entrepreneurs launching or expanding their small businesses into the cloud, I will walk through a "real world" example of how to deploy a more secure solution for your business using Amazon's AWS cloud platform.
I will also include some non-technical guidance that should be applicable to any cloud service provider you choose.
Amazon Web Services (AWS) Overview
You may first find the AWS cloud service is flexible and broad, to include security, automation and management tools within a click of the mouse. You can purchase what you need by 'renting' a smaller server or two with lower capacity (e.g., memory, CPU, etc.), but also scale out to more systems and greater capacity as your business needs and web traffic grow.
![AWS Console]()
To help get things started, AWS even offers 12 months of access free for a smaller tier system. AWS also offers many other services to include shared database, shared disk storage, and network load balancing to name a few.
We will walk through several steps below using AWS and some of the security safeguards you may want to first focus on. We will then wrap up with some non-technical recommendations to help with your business startup or security program.
Setting up Access to the Cloud
One could argue access control is the most important security control to protect your business. Many security breaches have been caused by poor account passwords and lack of two-factor authentication.
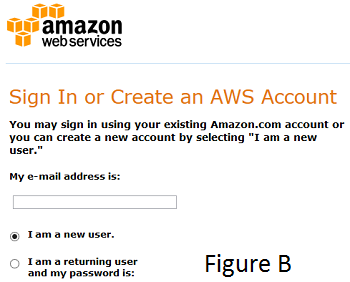
When setting up your first account in AWS, register with a unique e-mail address for your business (such as <your_name>@<your_business.com>) instead of a personal e-mail account that may be used for personal sites (see figure B). Also, choose a strong password with at least 10 characters.
![AWS Registration]()
After registering, setup security for your account. The first thing I would recommend is to setup multi-factor authentication (MFA) for each user, using Google's Authenticator application (see Figure C for iPhone example).
This requires installation of Authenticator on your mobile phone but will offer much stronger protection to prevent hackers from stealing your password and logging into the AWS console.
MFA is similar to "two-factor authentication" and is simply the process of requiring two or more credentials to login to a website, such as something you know (e.g., your password) and something you have (e.g., your mobile phone with one-time password). Hardware tokens are also available for a nominal cost.
![Google Authenticator]()
Remember these three stories that highlight what may happen without good access controls, such as lacking two-factor authentication?
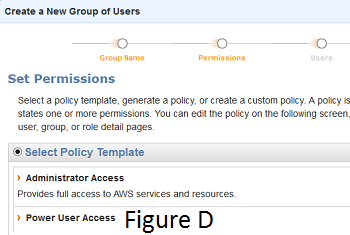
The second step is to setup users and groups (see Figure D) that specify appropriate level of permissions for your users, based on their role in the company.
![AWS Groups]()
For instance, the owner or head IT/Security manager may setup one group of users called "Cloud Access Administrators" and another group "AWS Systems Administrators", and then assign permissions and users to each group. That way, you can immediately setup a form of segregation of duties between different roles within your company.
Also, review and remove access at least annually or as soon as someone changes roles in (or leaves) the company. Even if you only have 2 or 3 employees, you will want to do this to put checks and balances and lay a good security foundation as your company grows.
Deploy and Harden New System
Many cloud providers make it easy for you to deploy a new web or database server. Don't be fooled though -- if you simply deploy new systems "out of the box", you may easily be susceptible to an online attack until you harden your system.
We will use a Windows server as an example of a system to provision here, but the same concepts should apply to any OS when hardening your virtual systems. Follow these steps to harden your system:
![AWS EC2 Instances]()
Network Cloud Controls
Now that you have hardened your system, setup an AWS security group (an entry level form of "firewall") to restrict only the minimum ports and access into and out of your systems hosted on the internet.
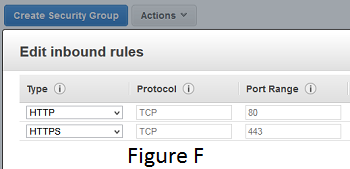
For example, only allow HTTP (port 80) and HTTPS (port 443) traffic to your web system (see Figure F). You may also require inbound access from web server to your database server or other needed ports depending on the applications installed.
![AWS Security Groups]()
Also, restrict Remote Desktop Protocol (RDP) or SSH access to only trusted IP addresses that are allowed to remotely manage your cloud systems. RDP and SSH typically run on ports 3389 and 22, respectively.
Warning: default AWS setting allows wide open RDP access to your systems from the internet!
See "Additional Cloud Safeguards" for more advanced network controls, such as dedicated firewalls and monitoring tools, that you may want to consider as well.
Backup and Recovery
Setup a backup and restore process to ensure your important data and configurations are backed up and secured. AWS has some excellent tools to help with backups and storage. Ensure you also have backups offsite beyond the cloud in case a disaster were to strike your cloud or application service provider. Also, ensure restore processes are tested regularly.
Don't wait for a disaster to strike or for a data breach to test your disaster recovery plan for the first time!
Encryption of Customer Data
Do you store customer data such as names, e-mails, addresses, card numbers, in the cloud (e.g., via a database or file system)? If so, please ensure your data is encrypted via strong cryptographic algorithms such as AES256. Ensure passwords are also encrypted or hashed (e.g., SHA2 or stronger). The primary goal here is to ensure confidentiality and integrity of your confidential data and passwords.
Even in the event of a systems breach, the likelihood of a data breach would be minimized with strong encryption. This is also often required to meet regulatory requirements and can help avoid costly fines or lawsuits. Finally, don't collect or store what's not critical to run your business. For example, you should never store credit card numbers if you can use a reputable payment provider to process payments for your website. Don't collect every single piece of personal information as a "nice to have", if you only need a few data elements to meet your business requirements.
Application Security
Reach out to a reputable security vendor and have them perform a vulnerability scan of your website code, software or system. Ensure your web code is securely coded to prevent such vulnerabilities (such as SQL Injection or Cross-Site Scripting). See OWASP site for more details on types of vulnerabilities you want to prevent. Fix vulnerabilities ASAP, preferably before your new website application "goes live" on the internet. If you like to do it yourself, check out this article "6 Free Vulnerability Scanners" that may work for you.
Does your company use WordPress? This is also a common attack vector. Check out this good article "Keep Attackers Away From Your WordPress Site" on some helpful tips to secure your blog application.
Privacy Policy
Ensure you have a good privacy policy published on your website. Reach out to your attorney to help develop as needed.
The privacy policy is critical to describe to your customers what data you collect, what you intend to do with the data and how you will protect it, just to name a few. Be very careful on what data you share in accordance to your privacy policy. For instance, personal data that can be used to identify your customers should never be shared with third parties unless it's clearly described in your privacy policy and you have a strong business justification to do so.
A 'Terms and Conditions' page may also be important to add legal terms and conditions for use of the website, as well as any links to content on other websites.
Additional Cloud Safeguards
As your business and budget grows, you may also consider some of these security controls for your cloud solution:
a) Network segregation of critical systems (e.g.,split up your web, database systems onto dedicated network).
b) Create a "utility" network used to host tools servers used for remote access, patching automation, Active Directory, etc.
c) Network firewalls, Intrusion Detection Systems (IDS) and other security monitoring systems such as SIEMs.
d) Setup network load balancing to spread web traffic across multiple servers (to increase availability) and better hide internal server information.
e) Setup a Virtual Private Network (VPN) encrypted connection between your business and your cloud provider (to protect sensitive data in transit).
Beyond the Cloud - Security Policies and Awareness
As you begin your entrepreneur journey towards that next successful powerhouse website, don't forget to draft information security policies for your business and employees. Ensure your employees are aware of the policies and their legal obligations to protect your data and brand.
Also, implement a security awareness program (to include training) for new hires and existing employees and contractors. See these two additional articles for more ideas to help you develop policies and an awareness training program.
Conclusion
These cloud controls are just a start to help move your startup or small business in the right direction. By focusing just a little more time upfront on security, this may help you free up more time on increasing revenue and retaining loyal customers.
I hope this article helps you in your security quest to improve your business.
Remember, be secure. It's a zoo other there.
(This article was originally published on Securezoo.com)

The cloud presents great business opportunities, but it can also lead to legal and financial hot water if you cut corners. Skipping or glossing over data protection safeguards can of course lead to brand damage, financial penalties, loss of customer trust and even put you out of business.
To help startups and entrepreneurs launching or expanding their small businesses into the cloud, I will walk through a "real world" example of how to deploy a more secure solution for your business using Amazon's AWS cloud platform.
I will also include some non-technical guidance that should be applicable to any cloud service provider you choose.
Amazon Web Services (AWS) Overview
You may first find the AWS cloud service is flexible and broad, to include security, automation and management tools within a click of the mouse. You can purchase what you need by 'renting' a smaller server or two with lower capacity (e.g., memory, CPU, etc.), but also scale out to more systems and greater capacity as your business needs and web traffic grow.

To help get things started, AWS even offers 12 months of access free for a smaller tier system. AWS also offers many other services to include shared database, shared disk storage, and network load balancing to name a few.
We will walk through several steps below using AWS and some of the security safeguards you may want to first focus on. We will then wrap up with some non-technical recommendations to help with your business startup or security program.
Setting up Access to the Cloud
One could argue access control is the most important security control to protect your business. Many security breaches have been caused by poor account passwords and lack of two-factor authentication.
When setting up your first account in AWS, register with a unique e-mail address for your business (such as <your_name>@<your_business
After registering, setup security for your account. The first thing I would recommend is to setup multi-factor authentication (MFA) for each user, using Google's Authenticator application (see Figure C for iPhone example).
This requires installation of Authenticator on your mobile phone but will offer much stronger protection to prevent hackers from stealing your password and logging into the AWS console.
MFA is similar to "two-factor authentication" and is simply the process of requiring two or more credentials to login to a website, such as something you know (e.g., your password) and something you have (e.g., your mobile phone with one-time password). Hardware tokens are also available for a nominal cost.
Remember these three stories that highlight what may happen without good access controls, such as lacking two-factor authentication?
"Hosting Company Quickly Put Out of Business by Hacker" (securezoo.com, 6/19/14)
"Syrian Electronic Army hacks Forbes, steals user data" (news.cnet.com, 2/14/14)
"Syrian Electronic Army Hacks CNN Social Media, Microsoft Transparency Data" (threatpost.com, 1/27/14)
The second step is to setup users and groups (see Figure D) that specify appropriate level of permissions for your users, based on their role in the company.
For instance, the owner or head IT/Security manager may setup one group of users called "Cloud Access Administrators" and another group "AWS Systems Administrators", and then assign permissions and users to each group. That way, you can immediately setup a form of segregation of duties between different roles within your company.
Also, review and remove access at least annually or as soon as someone changes roles in (or leaves) the company. Even if you only have 2 or 3 employees, you will want to do this to put checks and balances and lay a good security foundation as your company grows.
Deploy and Harden New System
Many cloud providers make it easy for you to deploy a new web or database server. Don't be fooled though -- if you simply deploy new systems "out of the box", you may easily be susceptible to an online attack until you harden your system.
We will use a Windows server as an example of a system to provision here, but the same concepts should apply to any OS when hardening your virtual systems. Follow these steps to harden your system:
1.
Launch Elastic Compute Cloud (EC2) system instance to begin image process (see Figure E). After the image completes, use the private key to login as "Administrator". Note: take special care not to store any keys on your local system in plain text as keys must always be secured and encrypted.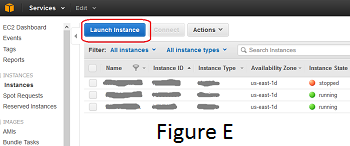
2.
Login to new system and deploy anti-virus application such as McAfee, Symantec, Kapersky or Microsoft's Essentials, to name a few.3.
Deploy needed packages, such as IIS, WordPress, SQL Server, etc.4.
Install software patches immediately after completing steps above.5.
Create new local administrator account for IT Administrator(s) responsible for managing your systems, even if it's just for your account. Create strong password and make sure to change the password every 90 days. As you grow, you may also use Active Directory to centrally manage users and access to systems.6.
Change default Administrator account name to something different (e.g., "Local_Admin"), but a name you can still remember. Remember attackers will try to use the default accounts to guess passwords, so your job is to make it more difficult for that to happen.7.
If you have WordPress or other web admin utilities used for Content Management System (CMS) or eCommerce, also change default account passwords as these can also be guessed by attackers to gain access to your systems remotely.8.
Deploy hardening scripts to "lock down" system to best practices (such as DISA STIG). See our Sept 2013 Newsletter for more details on how this can be done using something like Microsoft's Security Compliance Manager. You may also check with your local security consultant or advisor if you need assistance in this area.Network Cloud Controls
Now that you have hardened your system, setup an AWS security group (an entry level form of "firewall") to restrict only the minimum ports and access into and out of your systems hosted on the internet.
For example, only allow HTTP (port 80) and HTTPS (port 443) traffic to your web system (see Figure F). You may also require inbound access from web server to your database server or other needed ports depending on the applications installed.
Also, restrict Remote Desktop Protocol (RDP) or SSH access to only trusted IP addresses that are allowed to remotely manage your cloud systems. RDP and SSH typically run on ports 3389 and 22, respectively.
Warning: default AWS setting allows wide open RDP access to your systems from the internet!
See "Additional Cloud Safeguards" for more advanced network controls, such as dedicated firewalls and monitoring tools, that you may want to consider as well.
Backup and Recovery
Setup a backup and restore process to ensure your important data and configurations are backed up and secured. AWS has some excellent tools to help with backups and storage. Ensure you also have backups offsite beyond the cloud in case a disaster were to strike your cloud or application service provider. Also, ensure restore processes are tested regularly.
Don't wait for a disaster to strike or for a data breach to test your disaster recovery plan for the first time!
Encryption of Customer Data
Do you store customer data such as names, e-mails, addresses, card numbers, in the cloud (e.g., via a database or file system)? If so, please ensure your data is encrypted via strong cryptographic algorithms such as AES256. Ensure passwords are also encrypted or hashed (e.g., SHA2 or stronger). The primary goal here is to ensure confidentiality and integrity of your confidential data and passwords.
Even in the event of a systems breach, the likelihood of a data breach would be minimized with strong encryption. This is also often required to meet regulatory requirements and can help avoid costly fines or lawsuits. Finally, don't collect or store what's not critical to run your business. For example, you should never store credit card numbers if you can use a reputable payment provider to process payments for your website. Don't collect every single piece of personal information as a "nice to have", if you only need a few data elements to meet your business requirements.
Application Security
Reach out to a reputable security vendor and have them perform a vulnerability scan of your website code, software or system. Ensure your web code is securely coded to prevent such vulnerabilities (such as SQL Injection or Cross-Site Scripting). See OWASP site for more details on types of vulnerabilities you want to prevent. Fix vulnerabilities ASAP, preferably before your new website application "goes live" on the internet. If you like to do it yourself, check out this article "6 Free Vulnerability Scanners" that may work for you.
Does your company use WordPress? This is also a common attack vector. Check out this good article "Keep Attackers Away From Your WordPress Site" on some helpful tips to secure your blog application.
Privacy Policy
Ensure you have a good privacy policy published on your website. Reach out to your attorney to help develop as needed.
The privacy policy is critical to describe to your customers what data you collect, what you intend to do with the data and how you will protect it, just to name a few. Be very careful on what data you share in accordance to your privacy policy. For instance, personal data that can be used to identify your customers should never be shared with third parties unless it's clearly described in your privacy policy and you have a strong business justification to do so.
A 'Terms and Conditions' page may also be important to add legal terms and conditions for use of the website, as well as any links to content on other websites.
Additional Cloud Safeguards
As your business and budget grows, you may also consider some of these security controls for your cloud solution:
a) Network segregation of critical systems (e.g.,split up your web, database systems onto dedicated network).
b) Create a "utility" network used to host tools servers used for remote access, patching automation, Active Directory, etc.
c) Network firewalls, Intrusion Detection Systems (IDS) and other security monitoring systems such as SIEMs.
d) Setup network load balancing to spread web traffic across multiple servers (to increase availability) and better hide internal server information.
e) Setup a Virtual Private Network (VPN) encrypted connection between your business and your cloud provider (to protect sensitive data in transit).
Beyond the Cloud - Security Policies and Awareness
As you begin your entrepreneur journey towards that next successful powerhouse website, don't forget to draft information security policies for your business and employees. Ensure your employees are aware of the policies and their legal obligations to protect your data and brand.
Also, implement a security awareness program (to include training) for new hires and existing employees and contractors. See these two additional articles for more ideas to help you develop policies and an awareness training program.
Conclusion
These cloud controls are just a start to help move your startup or small business in the right direction. By focusing just a little more time upfront on security, this may help you free up more time on increasing revenue and retaining loyal customers.
I hope this article helps you in your security quest to improve your business.
Remember, be secure. It's a zoo other there.
(This article was originally published on Securezoo.com)
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (1)
Commented:
Thanks for the assist.
Frank,
Your article has been published, and we have awarded it EE-Approved status as well. Congratulations!
ericpete
Page Editor