Browse All Articles > Don't Let These 5 Security Threats Sink Your Business
There has been no shortage this year of ominous headlines describing new data breaches and security threats affecting all kinds and sizes of businesses and government entities. As more bad news unfolds, hackers appear to have the advantage over those organizations that let their guard down against the constant barrage of threats. New vulnerabilities and ways to exploit them emerge just about every day it seems.
![Cyber-Threats.jpg]()
This healthy sense of paranoia has also contributed to a fear of "when is it going to happen to me?" In this article, I have outlined 5 top security threats that every small business (or any business for that matter) should be keenly aware of and protect against. For each threat, there are recommended safeguards your business can implement to help put those fears to rest.
Most of these threats can be easily remedied without significant investment, yet have been the root cause for many of the breaches and attacks companies have been victim to this year.
1 - Legacy Operating System Threats
Does your business still happen to run Windows 2003 or Windows XP? As most folks already know, support for Windows XP ended on April 8, nearly 12 years after the Operating System (OS) was launched. Did you also know that the popular server OS, Windows 2003, will also go off life support next year (July 14, 2015 to be exact)? No support, no patches, plenty of easy targets for hackers.
Similar to XP, businesses have had plenty of time to migrate their older servers to a newer OS. Needless to say, it is highly encouraged to retire those legacy systems as soon as possible. Apply this same approach to other legacy systems and applications that are not supported by your software and hardware vendors. This will also help increase availability to your business systems and add peace of mind so that you can focus on securing and running the rest of your business. This should be an easy "check" to mark off your list.
One of the first attacks that tried to take advantage of Windows XP earlier this year was described in article Hackers ZERO IN on ZOMBIE XP boxes: Get patching, Internet Explorer 8 users (The Register). This was the first of the "in the wild" XP attacks, but was not the last.
For more information related to the upcoming Windows 2003 threat, read the article Windows 2003: Microsoft's next support sinkhole (by Infoworld). For some sample lifecycle support websites, see Microsoft's Product Lifecycle Search website and also RedHat's Enterprise Linux Life Cycle.
2 - Third Party Software Threats
Are you running WordPress, Drupal or other popular third party blogging or content management system software to power your website? Have you installed third party plug-ins to allow greater functionality and features?
If you do, ensure you or your IT/security experts stay on top of security advisories and are aware of new software updates to those third party platforms. Most often you can sign up for advisories to get automatic updates via e-mail or you can follow via twitter. When new updates are announced, test and upgrade your systems immediately. Also, scan your websites for vulnerabilities and address both application and network vulnerabilities in a timely manner.
For more related to this threat, read this article: Assume ‘Every Drupal 7 Site Was Compromised’ Unless Patched By Oct. 15 (by Threatpost) or Thousands of WordPress Sites With Old Plugins Targeted and Compromised with Malware. You can also check out Securi's blog with new advisories related to third party plug-ins and website security.
3 - Crypto Threats (e.g., old encryption, SSL certs)
Encryption is a critical control to help ensure confidentiality and integrity of your most sensitive customer and company data. Encryption uses an "algorithm" (e.g., AES-256) to convert sensitive clear text (like a payment card or personal information) to ciphertext that is unreadable by unauthorized users or attackers. Other forms of cryptography ("crypto") include hashing used for file integrity and password protection and also Secure Sockets Layer (SSL) used for secure transport of data, such as used in SSL certificates.
However, older crypto algorithms can be cracked and be a threat to your business. In August, Google announced it was intending to deprecate SHA-1 within use of TLS certificates as soon as early 2016. This came after Microsoft similarly announced plans to move away from the SHA-1 Hashing Algorithm used in their Microsoft Root Certificate Program. The move to more secure certificates and hashing could be partly accelerated by attacks like Heartbleed.
Just this past week, Microsoft discovered through an internal security assessment a flaw in their Secure Channel (Schannel) security package used to implement SSL and TLS in every version of Windows. The vulnerability (CVE-2014-6321) was fixed via patch MS14-066 and also includes support for stronger crypto ciphers for older Windows versions.
Do you use any of the "old crypto" controls listed in table below (see Figure A)? If you do, work with your security or IT support team and ensure they get upgraded to newer more secure crypto algorithms as soon as possible.
![Crypto-Cheatsheet.png]() Figure A.
Figure A.
For more information, you may also refer to NIST SP800-131A, Transitions: Recommendation for Transitioning the Use of Cryptographic Algorithms and Key Lengths.
4 - Malware Threats
If you run a retail business, or even shopped in many of the major retailers or read the paper lately, you probably have already heard of the Point-of-Sale (POS) malware plaguing many of the larger retail chains and even small business stores. Retailers such as Target, Marshalls, Home Depot, UPS Stores, Dairy Queen, Albertsons and many more have been victims to attacks that have used POS malware such as "BackOff" or "BlackPOS."
To help thwart this nemesis, ensure your POS systems are updated with latest OS, payment terminals, and anti-malware software.
We also highlighted some previous guidance to help secure POS environment here. The US Homeland Security wrote a nice ten page report titled Backoff: New Point of Sale Malware that included some good guidance for retail security to help combat the POS malware threat.
You may also use the above guidance for non-retail businesses since similar system anti-malware safeguards apply. Scan your systems frequently and on a scheduled basis for malware and stay vigilant by monitoring your environment for suspicious activity.
5 - Remote Access Threats
Access control, to include remote access, is one of the most important security controls used to protect your business. Many security breaches have been caused by poor account passwords and lack of two-factor authentication (or 2FA).
2FA is simply the process of requiring two or more credentials to login to a website or remote network, such as something you know (e.g., your password) and something you have (e.g., your mobile phone with one-time password). 2FA should be used when accessing your business remotely, logging in to cloud systems via admin console and sensitive systems used to host or process sensitive information.
A source code hosting company, Code Spaces, was quickly put out of business after the company discovered all of its backups and data were deleted by a hacker. Unauthorized access was obtained to a cloud console by stealing credentials from one of the cloud administrators. The disaster is an important reminder to ensure 2FA is used for access to AWS or other cloud administrator consoles used for managing systems, data backups, etc.
Conclusion
In conclusion, small businesses can implement effective measures as stated above to mitigate or reduce the likelihood of these threats. This is not a complete list, but a good start.
Remember, be secure. It's a zoo out there.
(This article was originally published on Securezoo.com)

This healthy sense of paranoia has also contributed to a fear of "when is it going to happen to me?" In this article, I have outlined 5 top security threats that every small business (or any business for that matter) should be keenly aware of and protect against. For each threat, there are recommended safeguards your business can implement to help put those fears to rest.
Most of these threats can be easily remedied without significant investment, yet have been the root cause for many of the breaches and attacks companies have been victim to this year.
1 - Legacy Operating System Threats
Does your business still happen to run Windows 2003 or Windows XP? As most folks already know, support for Windows XP ended on April 8, nearly 12 years after the Operating System (OS) was launched. Did you also know that the popular server OS, Windows 2003, will also go off life support next year (July 14, 2015 to be exact)? No support, no patches, plenty of easy targets for hackers.
Similar to XP, businesses have had plenty of time to migrate their older servers to a newer OS. Needless to say, it is highly encouraged to retire those legacy systems as soon as possible. Apply this same approach to other legacy systems and applications that are not supported by your software and hardware vendors. This will also help increase availability to your business systems and add peace of mind so that you can focus on securing and running the rest of your business. This should be an easy "check" to mark off your list.
One of the first attacks that tried to take advantage of Windows XP earlier this year was described in article Hackers ZERO IN on ZOMBIE XP boxes: Get patching, Internet Explorer 8 users (The Register). This was the first of the "in the wild" XP attacks, but was not the last.
For more information related to the upcoming Windows 2003 threat, read the article Windows 2003: Microsoft's next support sinkhole (by Infoworld). For some sample lifecycle support websites, see Microsoft's Product Lifecycle Search website and also RedHat's Enterprise Linux Life Cycle.
2 - Third Party Software Threats
Are you running WordPress, Drupal or other popular third party blogging or content management system software to power your website? Have you installed third party plug-ins to allow greater functionality and features?
If you do, ensure you or your IT/security experts stay on top of security advisories and are aware of new software updates to those third party platforms. Most often you can sign up for advisories to get automatic updates via e-mail or you can follow via twitter. When new updates are announced, test and upgrade your systems immediately. Also, scan your websites for vulnerabilities and address both application and network vulnerabilities in a timely manner.
For more related to this threat, read this article: Assume ‘Every Drupal 7 Site Was Compromised’ Unless Patched By Oct. 15 (by Threatpost) or Thousands of WordPress Sites With Old Plugins Targeted and Compromised with Malware. You can also check out Securi's blog with new advisories related to third party plug-ins and website security.
3 - Crypto Threats (e.g., old encryption, SSL certs)
Encryption is a critical control to help ensure confidentiality and integrity of your most sensitive customer and company data. Encryption uses an "algorithm" (e.g., AES-256) to convert sensitive clear text (like a payment card or personal information) to ciphertext that is unreadable by unauthorized users or attackers. Other forms of cryptography ("crypto") include hashing used for file integrity and password protection and also Secure Sockets Layer (SSL) used for secure transport of data, such as used in SSL certificates.
However, older crypto algorithms can be cracked and be a threat to your business. In August, Google announced it was intending to deprecate SHA-1 within use of TLS certificates as soon as early 2016. This came after Microsoft similarly announced plans to move away from the SHA-1 Hashing Algorithm used in their Microsoft Root Certificate Program. The move to more secure certificates and hashing could be partly accelerated by attacks like Heartbleed.
Just this past week, Microsoft discovered through an internal security assessment a flaw in their Secure Channel (Schannel) security package used to implement SSL and TLS in every version of Windows. The vulnerability (CVE-2014-6321) was fixed via patch MS14-066 and also includes support for stronger crypto ciphers for older Windows versions.
Do you use any of the "old crypto" controls listed in table below (see Figure A)? If you do, work with your security or IT support team and ensure they get upgraded to newer more secure crypto algorithms as soon as possible.
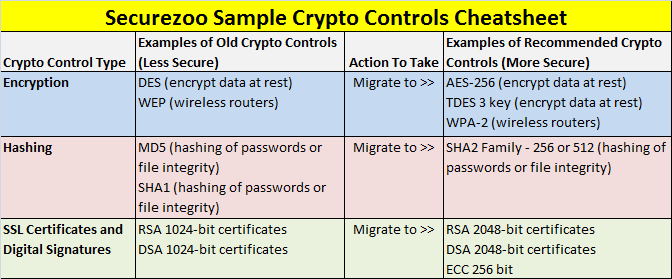 Figure A.
Figure A.
For more information, you may also refer to NIST SP800-131A, Transitions: Recommendation for Transitioning the Use of Cryptographic Algorithms and Key Lengths.
4 - Malware Threats
If you run a retail business, or even shopped in many of the major retailers or read the paper lately, you probably have already heard of the Point-of-Sale (POS) malware plaguing many of the larger retail chains and even small business stores. Retailers such as Target, Marshalls, Home Depot, UPS Stores, Dairy Queen, Albertsons and many more have been victims to attacks that have used POS malware such as "BackOff" or "BlackPOS."
To help thwart this nemesis, ensure your POS systems are updated with latest OS, payment terminals, and anti-malware software.
We also highlighted some previous guidance to help secure POS environment here. The US Homeland Security wrote a nice ten page report titled Backoff: New Point of Sale Malware that included some good guidance for retail security to help combat the POS malware threat.
You may also use the above guidance for non-retail businesses since similar system anti-malware safeguards apply. Scan your systems frequently and on a scheduled basis for malware and stay vigilant by monitoring your environment for suspicious activity.
5 - Remote Access Threats
Access control, to include remote access, is one of the most important security controls used to protect your business. Many security breaches have been caused by poor account passwords and lack of two-factor authentication (or 2FA).
2FA is simply the process of requiring two or more credentials to login to a website or remote network, such as something you know (e.g., your password) and something you have (e.g., your mobile phone with one-time password). 2FA should be used when accessing your business remotely, logging in to cloud systems via admin console and sensitive systems used to host or process sensitive information.
A source code hosting company, Code Spaces, was quickly put out of business after the company discovered all of its backups and data were deleted by a hacker. Unauthorized access was obtained to a cloud console by stealing credentials from one of the cloud administrators. The disaster is an important reminder to ensure 2FA is used for access to AWS or other cloud administrator consoles used for managing systems, data backups, etc.
Conclusion
In conclusion, small businesses can implement effective measures as stated above to mitigate or reduce the likelihood of these threats. This is not a complete list, but a good start.
Remember, be secure. It's a zoo out there.
(This article was originally published on Securezoo.com)
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (0)