Browse All Articles > Network Security Best Practices For NSX
NSX is a sort of virtualization platform that use of virtual switches. It is used widely in data centers; expanding data center network into virtualized platform is main feature.Smart phone cloud database security approach.
NSX is a sort of virtualization platform that use of virtual switches. It is used widely in data centers; expanding data center network into virtualized platform is main feature. Therefore operators prefer to use virtual switches in addition to physical switches. For both switches operator must manage multiple management interfaces.
Let's briefly explain role of virtualization practically; for a server virtualization platform the target is virtual switches while physical switches use a network management system.
A virtual network management system (VNMS) consists of a server virtualization platform, duplicate network switches and user clients. Here a question comes to mind. How does the VNMS communicate? The answer is by the help of network management interface (NMI) and device mangement interface (DMI). A DMI is a setting between the VNMS and network devices. A NMI is a setting between the network application and the VNMS.
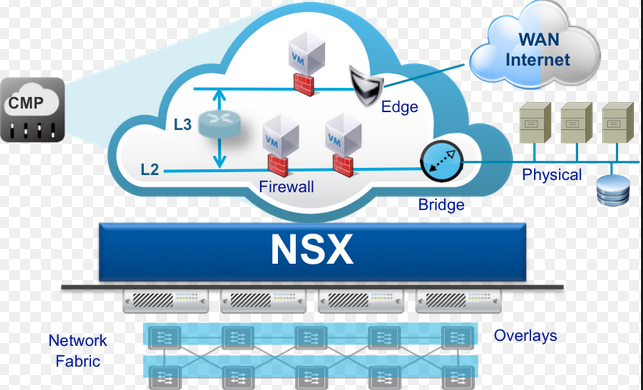 Figure: NSX Structure
Figure: NSX Structure
In terms of security, the VNMS contains information about virtual network management. Virtual network management information carries administrative knowledge about data center. Access attacks may be prevented by the control of the connections between the NMI and the DMI. This specific region of the virtual management network system that is the heart of security of NSX .
The other parts of system physical and virtual nodes are used for configuration of the management. The other role of virtual NMS is in integrating existing management of multiple interfaces into a single interface. The VNMS manages device connectivity in the managed target network. Performing this task, it stores network management information about configured virtual networks in the target network. As a briefly explained result is that security algorithm of NSX depends on multiple parameters such as NMI , DMI and VNMS structures over virtualized system.
The Typical NSX security algorithm consists of MD5 algorithm.The MD5 message-digest algorithm is a widely used cryptographic Hash function producing 128- bit (16-byte) hash value, typically expressed in text format as a 32 digit hexadecimal number.
 Figure:MD5 key Implementation example
Figure:MD5 key Implementation example
MD5 has been utilized in a wide variety of cryptographic applications, and is also commonly used to verify data integratiy of data centers .During network traffic security supplied by a MD5 algorithm ciphering over the platform.By usage of TCP protocol at the NSX makes necessary to use of firewalls too.
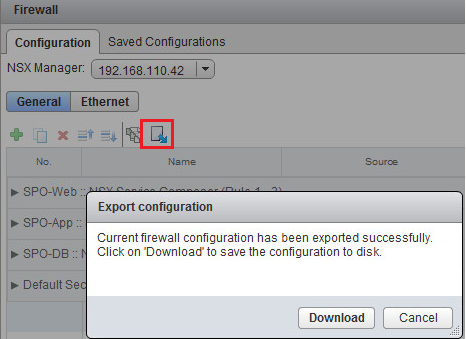 Figure: NSX versus Configuration Firewall
Figure: NSX versus Configuration Firewall
Related Helpful Sources ,Further Reading and Link;
For administration guide; http://www.vmware.com/support/pubs. EN-001269-01
Let's briefly explain role of virtualization practically; for a server virtualization platform the target is virtual switches while physical switches use a network management system.
A virtual network management system (VNMS) consists of a server virtualization platform, duplicate network switches and user clients. Here a question comes to mind. How does the VNMS communicate? The answer is by the help of network management interface (NMI) and device mangement interface (DMI). A DMI is a setting between the VNMS and network devices. A NMI is a setting between the network application and the VNMS.
 Figure: NSX Structure
Figure: NSX Structure
In terms of security, the VNMS contains information about virtual network management. Virtual network management information carries administrative knowledge about data center. Access attacks may be prevented by the control of the connections between the NMI and the DMI. This specific region of the virtual management network system that is the heart of security of NSX .
The other parts of system physical and virtual nodes are used for configuration of the management. The other role of virtual NMS is in integrating existing management of multiple interfaces into a single interface. The VNMS manages device connectivity in the managed target network. Performing this task, it stores network management information about configured virtual networks in the target network. As a briefly explained result is that security algorithm of NSX depends on multiple parameters such as NMI , DMI and VNMS structures over virtualized system.
The Typical NSX security algorithm consists of MD5 algorithm.The MD5 message-digest algorithm is a widely used cryptographic Hash function producing 128- bit (16-byte) hash value, typically expressed in text format as a 32 digit hexadecimal number.
 Figure:MD5 key Implementation example
Figure:MD5 key Implementation example
MD5 has been utilized in a wide variety of cryptographic applications, and is also commonly used to verify data integratiy of data centers .During network traffic security supplied by a MD5 algorithm ciphering over the platform.By usage of TCP protocol at the NSX makes necessary to use of firewalls too.
 Figure: NSX versus Configuration Firewall
Figure: NSX versus Configuration Firewall
Related Helpful Sources ,Further Reading and Link;
For administration guide; http://www.vmware.com/support/pubs. EN-001269-01
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (0)