Browse All Articles > Nmap: Host Discovery Basics
While most administrators use a security tool such as Nmap to perform a port scan to list available services on a remote system, Nmap can also be used to conduct a wide variety of functions that security and network administrators can find very helpful in discovering available hosts on the networks that they are responsible for. Discovering hosts can help system administrators ensure that they are monitoring all systems for availability while security administrators can ensure each system adheres to their company's security policy.
This article discusses host discovery features that are available in Nmap 5.0 and higher. For more information on Nmap as well as instructions on how to conduct a basic port scan with Nmap, please review the previous EE article Nmap: Performing a Basic Scan.
Listing Targets to be Scanned (List Scan)
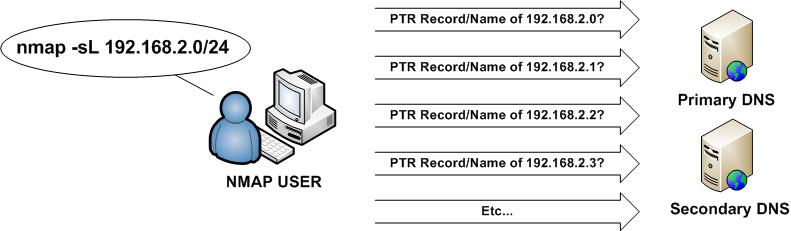
Before conducting a host discovery scan or sweep, an Nmap user may wish to examine the hosts that would be queried by the scan itself prior to conducting the scan. For example, a security professional conducting a penetration test may use this option to first check his work before performing a scan. This technique is referred to as a List Scan and is performed with the -sL option.
When a List Scan is performed, Nmap will attempt to perform a reverse DNS lookup to identify the FQDN of the host(s) to be scanned. Resolved names will be included as part of the scan results.
NOTE: If you have multiple DNS servers configured on the system conducting an Nmap scan, Nmap will use each of the DNS servers at the same time to help increase response time.
In the following example, Nmap is used to conduct a List Scan of the 192.168.2.0/24 (255.255.255.0) subnet.
![List Scan with Nmap]()
As you can see, the List Scan does not perform a scan of the remote system(s) as each port is listed as 'not scanned', but is used to perform a reverse DNS lookup against each host. In the above example, you can see that there are four hosts that had their system names resolved. For example, 192.168.2.5 is reported as being named payroll.company.net
Performing a Ping Scan/Sweep
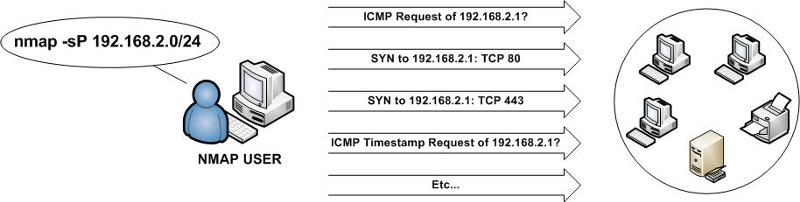
One method used traditionally by administrators to find online hosts is to perform a ping sweep of their networks. Using their system to send out an ICMP Echo Request packet to each possible host, the admin would then wait for any system to reply back with an ICMP Echo Reply packet. So, ideally, if a host was online, it would respond - if the ICMP Echo Request/Reply traffic wasn't blocked by some mechanism.
An Nmap Ping Scan not only attempts an ICMP Echo Request discovery, but also attempts several other methods for discovery hosts in case ICMP traffic is being blocked - typically by a router or firewall (either host- or network-based).
After Nmap uses ICMP Echo Requests to discover systems that are online and responding to the request, Nmap will then attempt to enumerate additional online systems by using a SYN scan on TCP port 443 and TCP port 80 for hosts not responding to the initial ICMP Echo Request. If a remote host responds to the SYN request, then Nmap will list the host as available on the network - even if it was blocking the ICMP request/reply traffic.
Finally, Nmap will attempt to use an ICMP Timestamp Request packet against remaining IP addresses that have not been detected as online. If an ICMP Timestamp Reply is received by Nmap, the responding system is then 'marked' as being online.
![Ping Scan/Sweep with Nmap]()
[u]Additional Options[/u]
Along with the List Scan and other scan types covered above, Nmap has additional options that are available for controlling which DNS servers are used by Nmap (--dns-servers), to disable name resolution (-r) complete and add the ability for Nmap to perform a traceroute to its targets (--traceroute).
Specifying DNS Servers
If you want to specify which DNS servers Nmap uses for name resolution, you can use the ' --dns-servers' switch.
Disable DNS Resolution
To not have Nmap perform name resolution for your scanned hosts, you can use the -n option to disable this functionality.
Performing a Traceroute
If you wish to identify the various "hops" or routers that your Nmap scan passes through to reach its target(s), you can use the -traceroute switch to provide this information. As you can see by the scan results below, this traceroute is completed using TCP 80 packets rather than traditional ICMP or UDP traffic.
In this article, we covered Nmap's basic host discovery options that are available to administrators for finding live network hosts.
For more information on Nmap as well as instructions on how to conduct a basic port scan with Nmap, please review my previous EE article Nmap: Performing a Basic Scan.
This article discusses host discovery features that are available in Nmap 5.0 and higher. For more information on Nmap as well as instructions on how to conduct a basic port scan with Nmap, please review the previous EE article Nmap: Performing a Basic Scan.
Listing Targets to be Scanned (List Scan)
Before conducting a host discovery scan or sweep, an Nmap user may wish to examine the hosts that would be queried by the scan itself prior to conducting the scan. For example, a security professional conducting a penetration test may use this option to first check his work before performing a scan. This technique is referred to as a List Scan and is performed with the -sL option.
When a List Scan is performed, Nmap will attempt to perform a reverse DNS lookup to identify the FQDN of the host(s) to be scanned. Resolved names will be included as part of the scan results.
NOTE: If you have multiple DNS servers configured on the system conducting an Nmap scan, Nmap will use each of the DNS servers at the same time to help increase response time.
In the following example, Nmap is used to conduct a List Scan of the 192.168.2.0/24 (255.255.255.0) subnet.
C:\>Nmap -sL 192.168.2.0/24
Starting Nmap 5.00 ( http://nmap.org ) at 2009-11-09 19:57 Eastern Standard Time
Host 192.168.2.0 not scanned
Host 192.168.2.1 not scanned
Host ad1.company.net (192.168.2.2) not scanned
Host ad2.company.net (192.168.2.3) not scanned
Host exchange.company.net (192.168.2.4) not scanned
Host payroll.company.net (192.168.2.5) not scanned
Host 192.168.2.6 not scanned
Host 192.168.2.7 not scanned
... [Additional hosts removed for space consideration]
Nmap done: 256 IP addresses (0 hosts up) scanned in 0.69 seconds As you can see, the List Scan does not perform a scan of the remote system(s) as each port is listed as 'not scanned', but is used to perform a reverse DNS lookup against each host. In the above example, you can see that there are four hosts that had their system names resolved. For example, 192.168.2.5 is reported as being named payroll.company.net
Performing a Ping Scan/Sweep
One method used traditionally by administrators to find online hosts is to perform a ping sweep of their networks. Using their system to send out an ICMP Echo Request packet to each possible host, the admin would then wait for any system to reply back with an ICMP Echo Reply packet. So, ideally, if a host was online, it would respond - if the ICMP Echo Request/Reply traffic wasn't blocked by some mechanism.
An Nmap Ping Scan not only attempts an ICMP Echo Request discovery, but also attempts several other methods for discovery hosts in case ICMP traffic is being blocked - typically by a router or firewall (either host- or network-based).
After Nmap uses ICMP Echo Requests to discover systems that are online and responding to the request, Nmap will then attempt to enumerate additional online systems by using a SYN scan on TCP port 443 and TCP port 80 for hosts not responding to the initial ICMP Echo Request. If a remote host responds to the SYN request, then Nmap will list the host as available on the network - even if it was blocking the ICMP request/reply traffic.
Finally, Nmap will attempt to use an ICMP Timestamp Request packet against remaining IP addresses that have not been detected as online. If an ICMP Timestamp Reply is received by Nmap, the responding system is then 'marked' as being online.
C:\>nmap -sP 192.168.2.0/24
Starting Nmap 5.00 ( http://nmap.org ) at 2009-11-09 19:00 Eastern Standard Time
Host ad1.company.net (192.168.2.2) is up (0.00s latency).
MAC Address: 00:23:AE:55:55:55 (Dell)
Host ad2.company.net (192.168.2.3) is up (0.00s latency).
MAC Address: 00:23:AE:55:55:55 (Dell)
Host exchange.company.net (192.168.2.4) is up (0.00s latency).
MAC Address: 00:23:AE:55:55:55 (Dell)
Host payroll.company.net (192.168.2.5) is up (0.00s latency).
MAC Address: 00:1A:A0:55:55:55 (Dell)
&[u]Additional Options[/u]
Along with the List Scan and other scan types covered above, Nmap has additional options that are available for controlling which DNS servers are used by Nmap (--dns-servers), to disable name resolution (-r) complete and add the ability for Nmap to perform a traceroute to its targets (--traceroute).
Specifying DNS Servers
If you want to specify which DNS servers Nmap uses for name resolution, you can use the ' --dns-servers' switch.
C:\>Nmap -sL 192.168.2.0/24 --dns-servers 192.168.1.1,192.168.1.2,192.168.1.3Disable DNS Resolution
To not have Nmap perform name resolution for your scanned hosts, you can use the -n option to disable this functionality.
C:\>Nmap -n 192.168.2.0/24
Starting Nmap 5.00 ( http://nmap.org ) at 2009-11-09 19:36 Eastern Standard Time
Host 192.168.2.1 is up (0.00s latency).
MAC Address: 00:23:AE:55:55:55 (Dell)
Host 192.168.2.2 is up (0.00s latency).
MAC Address: 00:23:AE:55:55:55 (Dell)
Host 192.168.2.3 is up (0.00s latency).
MAC Address: 00:23:AE:55:55:55 (Dell)
Host 192.168.2.4 is up (0.00s latency).
MAC Address: 00:23:AE:A55:55:55 (Dell)
&Performing a Traceroute
If you wish to identify the various "hops" or routers that your Nmap scan passes through to reach its target(s), you can use the -traceroute switch to provide this information. As you can see by the scan results below, this traceroute is completed using TCP 80 packets rather than traditional ICMP or UDP traffic.
C:\>Nmap 192.168.1.1 --traceroute
Starting Nmap 5.00 ( http://nmap.org ) at 2009-11-09 19:15 Eastern Standard Time
Interesting ports on gateway.company.net (192.168.1.1):
Not shown: 998 filtered ports
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 0.00 192.168.2.1
2 0.00 192.168.3.254
3 0.00 gateway.company.net (192.168.1.1)
Nmap done: 1 IP address (1 host up) scanned in 6.51 secondsIn this article, we covered Nmap's basic host discovery options that are available to administrators for finding live network hosts.
For more information on Nmap as well as instructions on how to conduct a basic port scan with Nmap, please review my previous EE article Nmap: Performing a Basic Scan.
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (0)