Adding Computers to AD groups through an SCCM Task Sequence
IT is my life...SCCM my passion! I work full time with SCCM, Exchange, and Windows Server. I have a beautiful family and love Star Trek!
Published:
Browse All Articles > Adding Computers to AD groups through an SCCM Task Sequence
Adding Computers to AD groups through an SCCM Task Sequence
SCCM Add to GRP TS
One of the many highly useful windows features that I have loved since the Windows 7 days is DirectAccess for anyone not familiar with DirectAccess, I encourage you to at least investigate the possibility of enabling this in your environment if you have the infrastructure to support it.
[u]https://technet.microsoft.com/en-us/library/jj134204(v=ws.11).aspx[/u]
In a nutshell: Any windows based laptop or device enabled with DirectAccess has the ability to automatically connect via secure VPN connection upon logging into said device. From an end user perspective this connection is relatively seamless and as such is a huge perk to the Windows environment
We use DirectAccess in our organization heavily for our staff issued windows laptops. These consist of a mix of Dell Latitude 3350 laptops and Microsoft Surface Pro 3 and 4 devices. My colleague had setup DirectAccess in such a way that the service was only applied to devices that were members of specific AD security Groups. Upon deploying the device through our UDI Task Sequence, techs would typically have to manually add the deployed devices to the necessary security groups after deploying the machine. This was then followed by a gpupdate /force, followed by a restart…I’m sure you get the idea, its a time consuming task that shouldn’t be necessary.
I began looking at a way to have this portion of the deployment automated through the task sequence. The first task was finding a way to add the machine to AD programmatically. I found the following script on the web (I unfortunately forget where I found it so if you are the author of this script please let me know so I can credit you in this piece)
The same could likely be accomplished via a PowerShell script…I simply have not taken the time to convert it.
The next step is to add the script to a package that can be distributed to your distribution points. I use a package titled SCRIPTS. I add all custom scripts that I use in my task sequences to this package. The package source simply points to the root folder containing any script referenced by the task sequence. I then add a Group called Provision DirectAccess.
![image]()
![image]()
On the options tab of the group I add a WMI Query that essentially scans for the memory type of the machine the TS is being run against, a value of 12 indicates a SODIMM:
[u]https://msdn.microsoft.com/en-us/library/aa394347(v=vs.85).aspx[/u]
If the result is ‘TRUE’ then the child items in the TS group will process. The purpose of this is to ensure the Group is only run against machines with SODIMMS which should only be mobile devices
I then add a Run Command Line step under the previously created group. The step in the example is called Teacher Laptops:![image]()
![image]()
Check the Package box and browse to the SCRIPTS package. ensure that the command is set to run with an account that has permissions. We then run the command line cscript.exe adgroup.vbs “AD Group Name” where adgroup.vbs is the name of the script from above and AD Group Name is the name of the AD group that you wish to add the machine to.
![image]()
We then add a WMI query to each of the Run Command Line steps under the TS group that looks for the ComputerName Prefix of TCH%. Our techs enter computer names based on a computer naming scheme and the TS adds those computers to the correct Security groups that provision the DirectAccess connections.
The above technique can be used to add workstations to an AD security group for any purpose. We happen to use it for provisioning DirectAccess. I hope you find this technique as beneficial as I have with your task sequences. Feel free to post any questions or comments below.
[u]https://technet.microso
In a nutshell: Any windows based laptop or device enabled with DirectAccess has the ability to automatically connect via secure VPN connection upon logging into said device. From an end user perspective this connection is relatively seamless and as such is a huge perk to the Windows environment
We use DirectAccess in our organization heavily for our staff issued windows laptops. These consist of a mix of Dell Latitude 3350 laptops and Microsoft Surface Pro 3 and 4 devices. My colleague had setup DirectAccess in such a way that the service was only applied to devices that were members of specific AD security Groups. Upon deploying the device through our UDI Task Sequence, techs would typically have to manually add the deployed devices to the necessary security groups after deploying the machine. This was then followed by a gpupdate /force, followed by a restart…I’m sure you get the idea, its a time consuming task that shouldn’t be necessary.
I began looking at a way to have this portion of the deployment automated through the task sequence. The first task was finding a way to add the machine to AD programmatically. I found the following script on the web (I unfortunately forget where I found it so if you are the author of this script please let me know so I can credit you in this piece)
Const ADS_PROPERTY_APPEND = 3
Set WshShell = WScript.CreateObject("WScript.Shell")
'----Get Computer DN------
Set objADSysInfo = CreateObject("ADSystemInfo")
ComputerDN = objADSysInfo.ComputerName
strcomputerdn = "LDAP://" & computerDN
Set objADSysInfo = Nothing
'----Connect AD-----
Set oRoot = GetObject("LDAP://rootDSE")
strDomainPath = oRoot.Get("defaultNamingContext")
Set oConnection = CreateObject("ADODB.Connection")
oConnection.Provider = "ADsDSOObject"
oConnection.Open "Active Directory Provider"
'-----Read commandline---
Set args = WScript.Arguments
For i = 0 To Args.Count - 1
addgroup Args.Item( i )
next
Function Addgroup(groupname)
'----Get Group DN------
Set oRs = oConnection.Execute("SELECT adspath FROM 'LDAP://" & strDomainPath & "'" & "WHERE objectCategory='group' AND " & "Name='" & GroupName & "'")
If Not oRs.EOF Then
strAdsPath = oRs("adspath")
End If
Set objGroup = GetObject (stradspath)
Set objComputer = GetObject (strComputerDN)
If (objGroup.IsMember(objComputer.AdsPath) = False) Then
objGroup.PutEx ADS_PROPERTY_APPEND, "member", Array(computerdn)
objGroup.SetInfo
End If
End FunctionThe same could likely be accomplished via a PowerShell script…I simply have not taken the time to convert it.
The next step is to add the script to a package that can be distributed to your distribution points. I use a package titled SCRIPTS. I add all custom scripts that I use in my task sequences to this package. The package source simply points to the root folder containing any script referenced by the task sequence. I then add a Group called Provision DirectAccess.
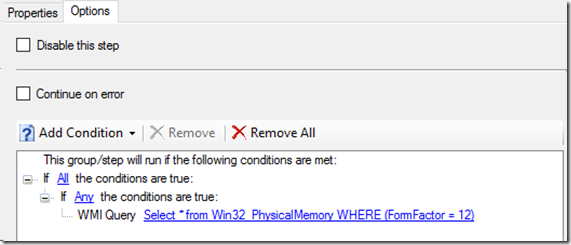
On the options tab of the group I add a WMI Query that essentially scans for the memory type of the machine the TS is being run against, a value of 12 indicates a SODIMM:
[u]https://msdn.microsoft.
If the result is ‘TRUE’ then the child items in the TS group will process. The purpose of this is to ensure the Group is only run against machines with SODIMMS which should only be mobile devices
I then add a Run Command Line step under the previously created group. The step in the example is called Teacher Laptops:
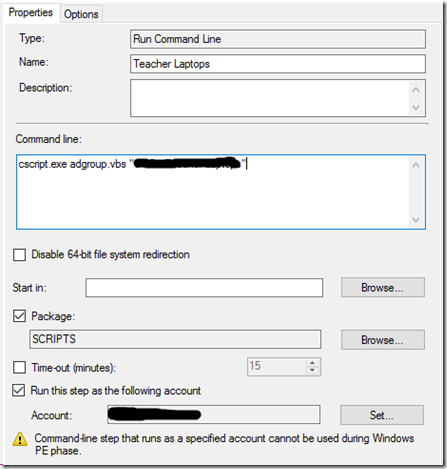
Check the Package box and browse to the SCRIPTS package. ensure that the command is set to run with an account that has permissions. We then run the command line cscript.exe adgroup.vbs “AD Group Name” where adgroup.vbs is the name of the script from above and AD Group Name is the name of the AD group that you wish to add the machine to.
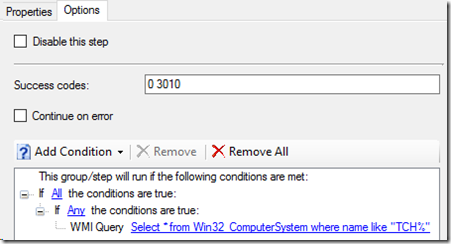
We then add a WMI query to each of the Run Command Line steps under the TS group that looks for the ComputerName Prefix of TCH%. Our techs enter computer names based on a computer naming scheme and the TS adds those computers to the correct Security groups that provision the DirectAccess connections.
The above technique can be used to add workstations to an AD security group for any purpose. We happen to use it for provisioning DirectAccess. I hope you find this technique as beneficial as I have with your task sequences. Feel free to post any questions or comments below.
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (0)