The well known Cerber ransomware continues to be active this summer. The size of the cryptolocker varies between 244 to 292 Kbytes, with the new builds spreading through spear phishing email campaigns targeting enterprises. The latest Cerber ransomware easily bypasses traditional defences. The analysed Cerber sample (MD5: cfd2d6f189b04d42618007fc9c540352) was only detected as a suspicious malicious object by nine out of 64 antiviruses on the first submission to Virustotal. The low detection rate can be explained by the fact that the cryptolocker is using a polymorphic encryptor and API call obfuscation to protect its copies from being detected by antiviruses.
Static analysis
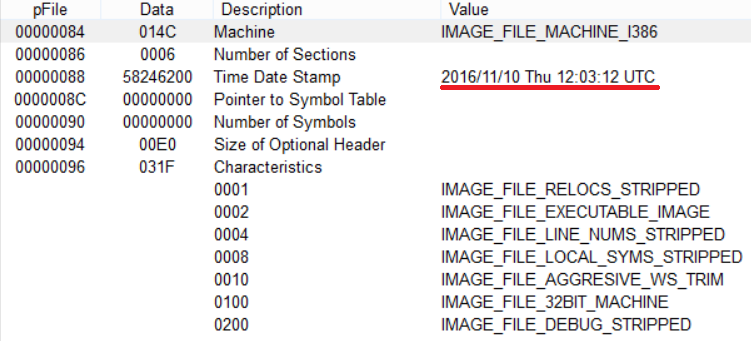
The PE EXE file has a fake timestamp, Import Address Table and even Export Address Table.
Export Address Table
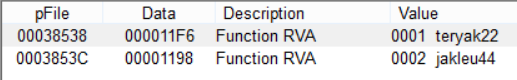
Hiding the payload
The latest builds of the Cerber’s code are even more protected with API call obfuscation. To hide the actual imports, Cerber loads them in runtime:
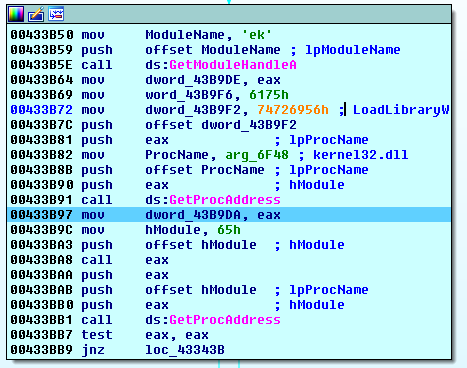
The actual Import Address Table looks like this:
Decrypting the configuration data
The configuration JSON data is encrypted and stored as RCDATA in the resource section:
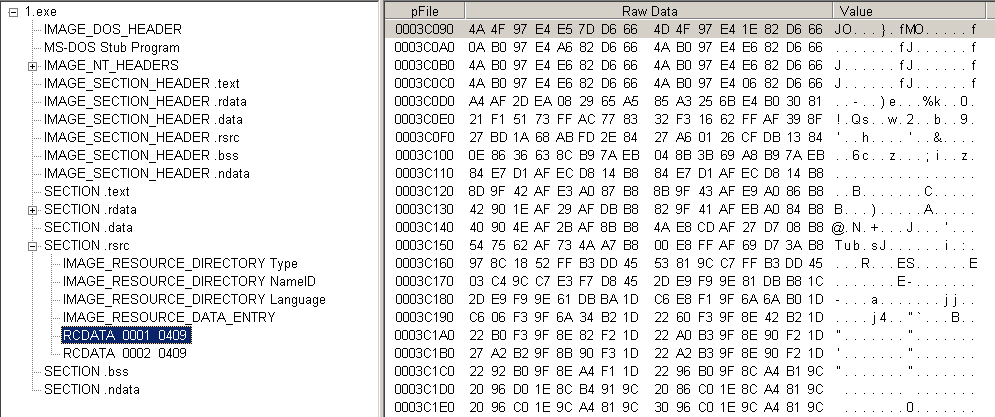
To decrypt the configuration data, Cerber goes through the following steps:
1. Imports the hard coded RC4 128-bit key from the BLOB data which is 28 bytes in size.
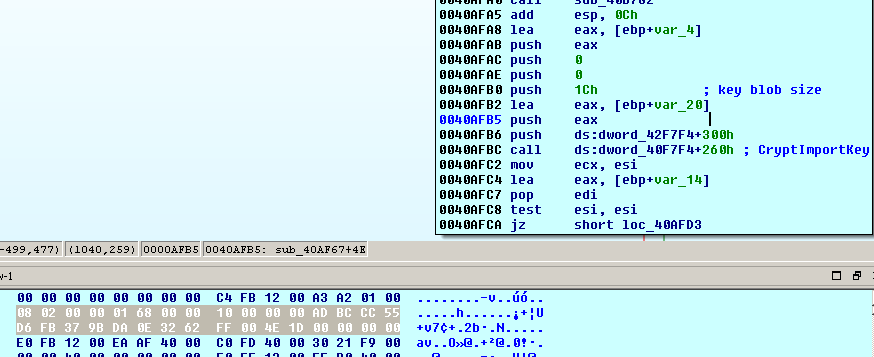
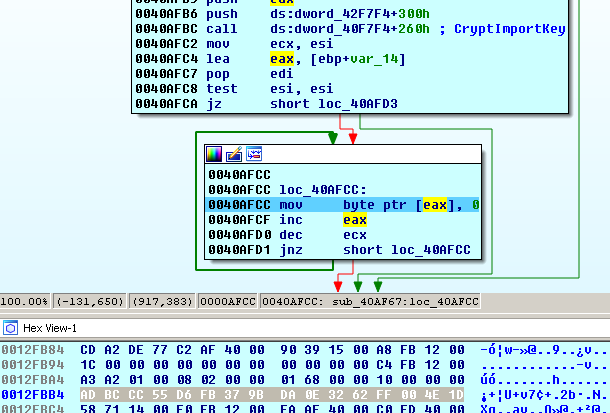
1st byte: BLOB type = PLAINTEXTKEYBLOB (0x08) 2nd byte: version = CUR_BLOB_VERSION (0x02) 5-8 bytes: algorithm id = CALG_RC4 (0x00006801) 9-12 bytes: key size in bytes = 16 (0x00000010) 13-28 bytes: key data ‘ ADBCCC55D6FB379BDA0E3262FF004E1D’2. Wipes the 128-bit encryption key from the memory with zeros after decryption:
3. Calls the CryptEncrypt() function to decrypt the JSON config which is 107 171 bytes in size:
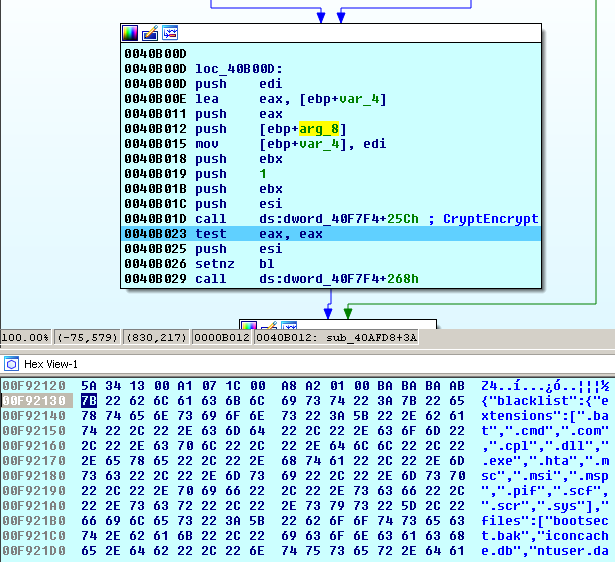
Configuration parameters
The Cerber configuration contains the following information:
- Blacklist
- File extensions for the files not to be encrypted: bat, cmd, com, cpl, dll, exe, hta, msc, msi, msp, pif, scf, scr, sys
- Files:
- Bootsect.bak
- Iconcache.db
- Ntuser.dat
- thumbs.db
- Folders that the cryptolocker should avoid when encrypting files:
- ":\\$getcurrent\\",
- ":\\$recycle.bin\\",
- ":\\$windows.~bt\\",
- ":\\$windows.~ws\\",
- ":\\boot\\",
- ":\\documents and settings\\all users\\",
- ":\\documents and settings\\default user\\",
- ":\\documents and settings\\localservice\\",
- ":\\documents and settings\\networkservice\\",
- ":\\intel\\",
- ":\\msocache\\",
- ":\\perflogs\\",
- ":\\program files (x86)\\",
- ":\\program files\\",
- ":\\programdata\\",
- ":\\recovery\\",
- ":\\recycled\\",
- ":\\recycler\\",
- ":\\system volume information\\",
- ":\\temp\\",
- ":\\windows.old\\",
- ":\\windows10upgrade\\",
- ":\\windows\\",
- ":\\winnt\\",
- "\\appdata\\local\\",
- "\\appdata\\locallow\\",
- "\\appdata\\roaming\\",
- "\\local settings\\",
- "\\public\\music\\sample music\\",
- "\\public\\pictures\\sample pictures\\",
- "\\public\\videos\\sample videos\\",
- "\\tor browser\\"
- Languages that make OS protected from the cryptolocker:
- 1049: Russian,
- 1058: Ukrainian
- 1059: Belarusian,
- 1064: Tajik,
- 1067: Armenian,
- 1068: Azeri (Latin),
- 1079: Georgian,
- 1087: Kazakh,
- 1088: Kyrgyz (Cyrillic),
- 1090: Turkmen,
- 1091: Uzbek (Latin),
- 1092 : Tatar (Russia),
- 2072: Romanian (Moldova),
- 2073: Russian (Moldova),
- 2092: Azeri (Cyrillic),
- 2115: Uzbek (Cyrillic).
- Whitelist
- Folders that should be encrypted:
- "\\bitcoin\\",
- "\\excel\\",
- "\\microsoft sql server\\",
- "\\microsoft\\excel\\",
- "\\microsoft\\microsoft sql server\\",
- "\\microsoft\\office\\",
- "\\microsoft\\onenote\\",
- "\\microsoft\\outlook\\",
- "\\microsoft\\powerpoint\\",
- "\\microsoft\\word\\",
- "\\office\\",
- "\\onenote\\",
- "\\outlook\\",
- "\\powerpoint\\",
- "\\steam\\",
- "\\the bat!\\",
- "\\thunderbird\\",
- "\\word\\"
- Folders that should be encrypted:
Global RSA 2048-bit public key:
-----BEGIN PUBLIC KEY----- MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvkty5qhqEydR9076Fevp 0uMP7IZNms1AA7GPQUThMWbYiEYIhBKcT0/nwYrBq0Ogv79K1tta04EHTrXgcAp/ OJgBhz9N58aewd4yZBm2coeaDGvcGRAc9e72ObFQ/TME/Io7LZ5qXDWzDafI8LA8 JQmSz0L+/G+LPTWg7kPOpJT7WSkRb9T8w5QgZRJuvvhErHM83kO3ELTH+SoEI53p 4ENVwfNNEpOpnpOOSKQobtIw56CsQFrhac0sQlOjek/muVluxjiEmc0fszk2WLSn qryiMyzaI5DWBDjYKXA1tp2h/ygbkYdFYRbAEqwtLxT2wMfWPQI5OkhTa9tZqD0H nQIDAQAB -----END PUBLIC KEY-----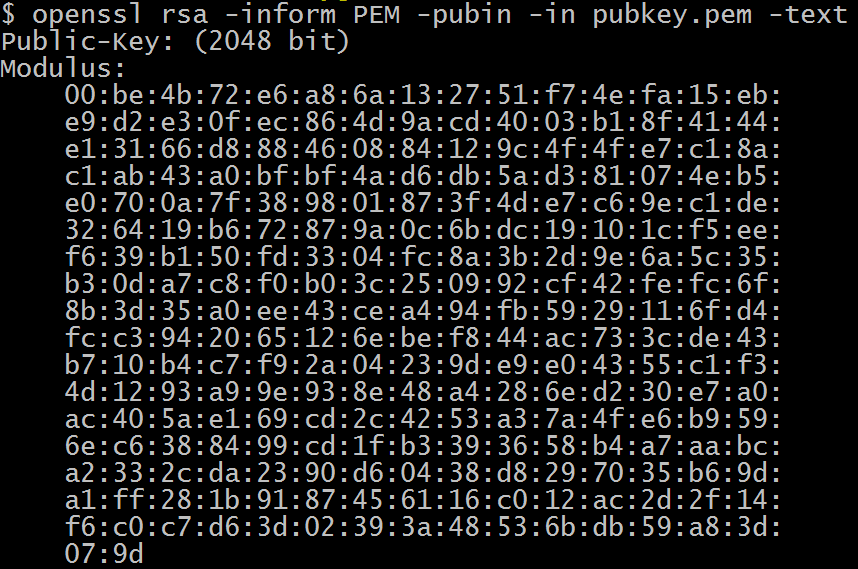
Traces on the hard disk
Once being unpacked, Cerber stores its temporary data and encryption keys in a subfolder named using the first part of the Machine GUID, inside the Temp folder. For example:
%Temp%\c36ab9c2
Encryption
Cerber uses RC4 and RSA algorithms for encryption. Every file is encrypted using the RC4 algorithm with a unique 128-bit key.
The file’s RC4 key is encrypted using a RSA-880 public session key generated on the victim’s machine. The prime numbers (p and q) used to calculate the RSA-880 session public key are encrypted using the RSA-2048 master public key delivered in the configuration data embedded in the cryptolocker’s file.
The prime numbers can be decrypted with the RSA-2048 master key by the attacker to restore the RSA-880 session private key through calculating a private key exponent (d) using the extended Euclidean algorithm.
The new file contains the encrypted RC4 key used to encrypt this file as well as the encrypted original file’s data, original filename, and checksum stored in a specific order. Cerber also adds a 60-byte block of randomly generated data into the middle of the file to complicate the encrypted file structure even more.
Key encryption
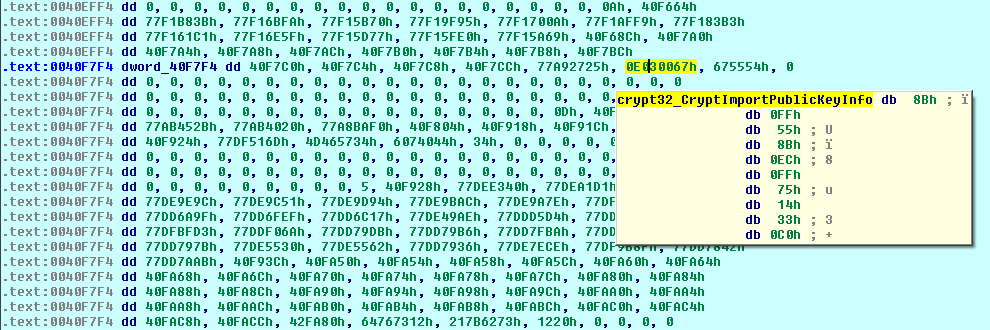
First, the RSA-2048 public key from the configuration file is decoded from Base64 to PEM format and then to PUBLICKEYBLOB:
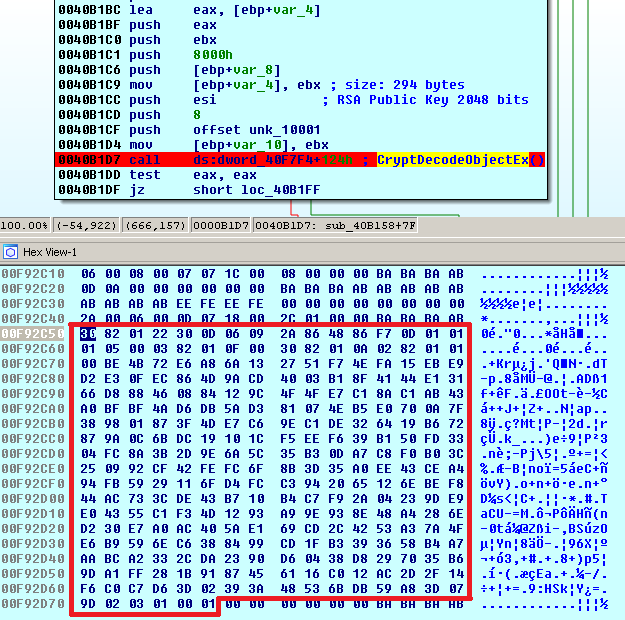
Once decoded, the CERT_PUBLIC_KEY_INFO structure contains a public key and its algorithm (OID_RSA_RSA "1.2.840.113549.1.1.1" - RSA is used to both encrypt and sign the content):

The RSA-2048 public key is to be imported as PUBLICKEYBLOB.
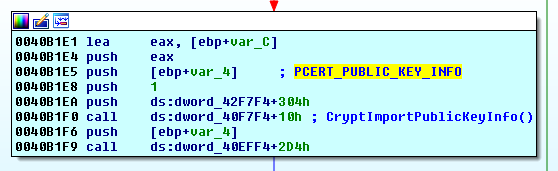

1st byte: BLOB type = PUBLICKEYBLOB (0x06) 2nd byte: version = CUR_BLOB_VERSION (0x02) 5-8 bytes: algorithm id = CALG_RSA_KEYX (0x0000A400) 9-20 bytes: RSAPUBKEY {magic = ‘RSA1’, key length = 2048 bits, public exponent = 65537} 21-276 bytes: key data 256 bytesThen, Cerber creates another RSA public key but with an 880-bit modulus length and saves it to the temporary file:
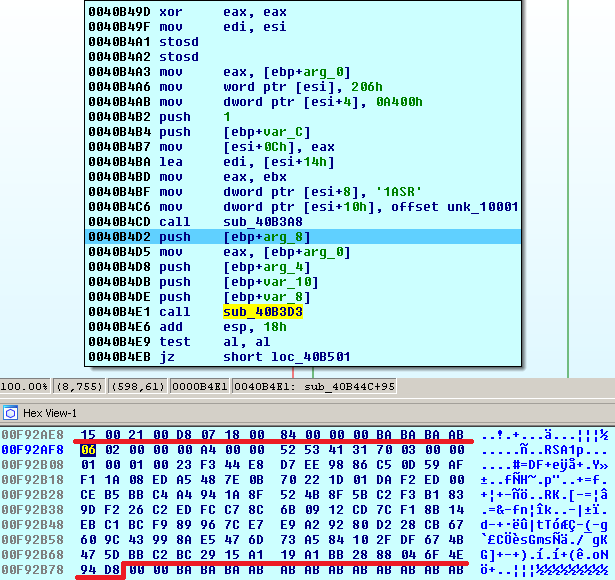
The RSA-2048 public key is used to encrypt an 114-byte block of data that consist of two prime numbers, each 55 bytes, generated for a RSA-880 public key that is used to encrypt the RC4 key and the 4-byte header that specifies the size of each block ‘37003700’:
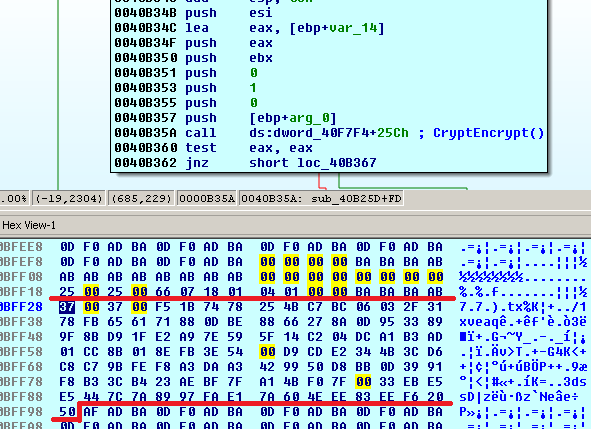
The encrypted block is stored in a tmp file in the %TEMP% folder and added to the end of every encrypted file:

File encryption
Cerber encrypts a file using the RC4 algorithm with a 128-bit key generated for every file that will be encrypted.
After encryption, the file will contain the following data blocks:
| Offset | Data |
| 0 1800 |
Original file data (‘skip_bytes’ = 1800) |
| 1800 1860 |
Randomly generated data (60 bytes) |
| 1860 ... |
Encrypted data from offset 1860 (‘skip_bytes’ + 60) to the end of the original file |
| The encrypted data containing the original filename, checksum, and RC4 key (48 bytes) | |
| Encrypted 99 bytes that includes header (39 bytes) and 60 bytes of the original file located after ‘skip_bytes’ (offset 1800) that were replaced with the randomly generated data (110 bytes). The header (39 bytes) includes: magic = FrbR, size of data, 16-byte RC4 key |
|
| RSA-880 prime numbers p and q encrypted by RSA-2048 (256 bytes) |
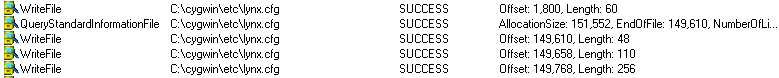
The file with the encrypted data is renamed as:
<Random characters>.<4th part of the Machine GUID>Ransom notes
The ransom notes are stored in the folders together witht the encrypted files and are named in the following format:
_R_E_A_D___T_H_I_S___<RAND>_.hta _R_E_A_D___T_H_I_S___<RAND>_.txt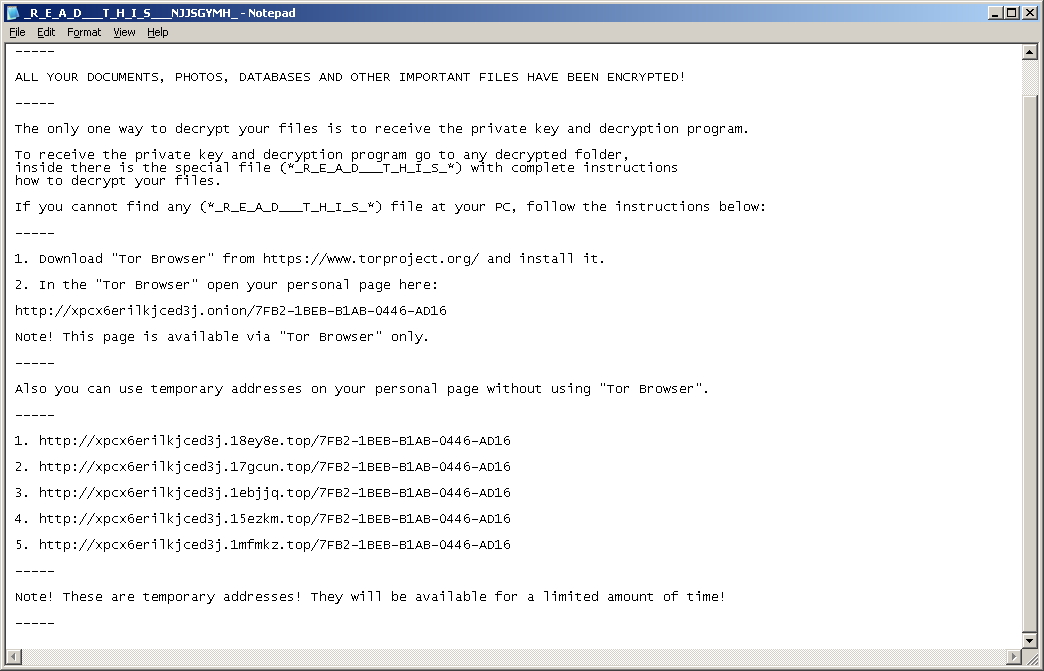
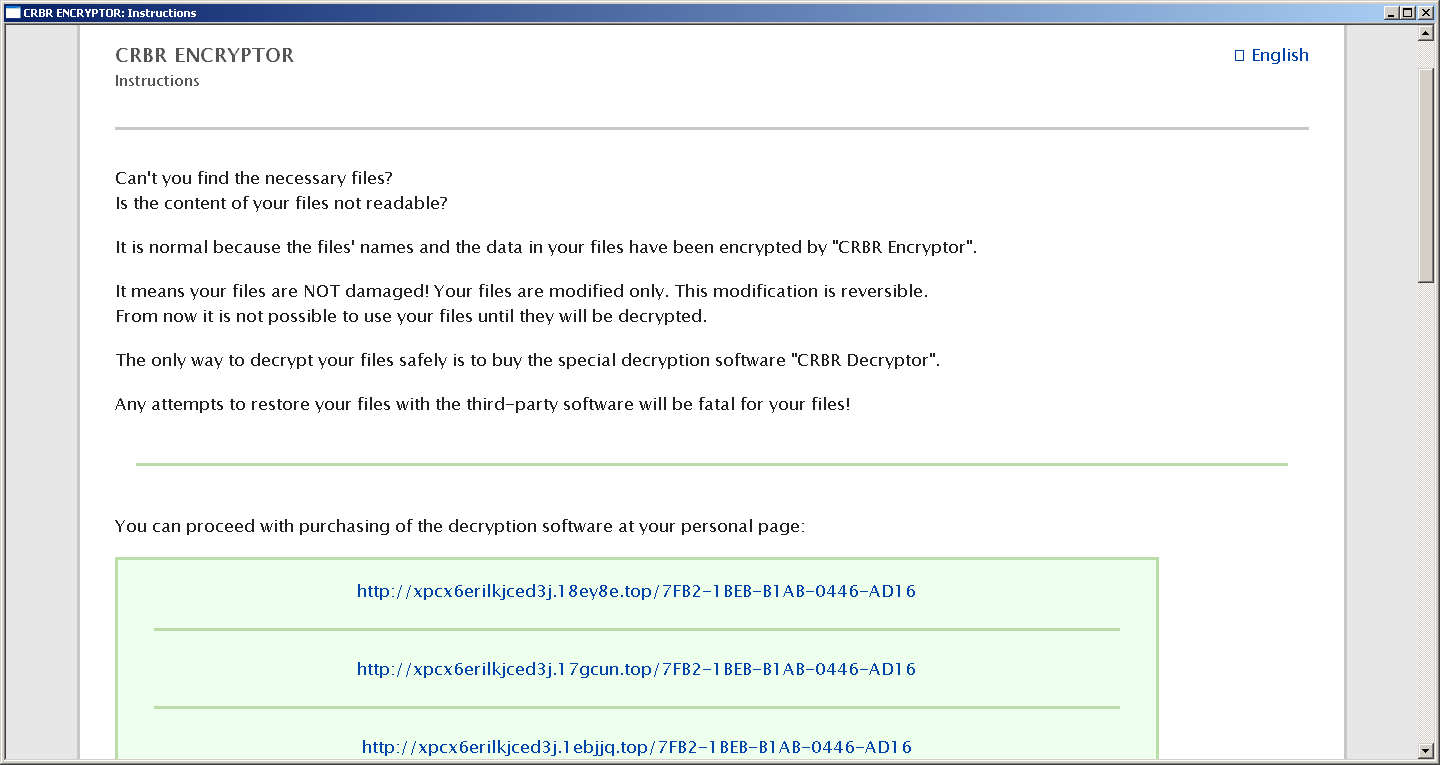
At the end of the encryption, the cryptolocker sets the familiar Cerber-style wallpaper:
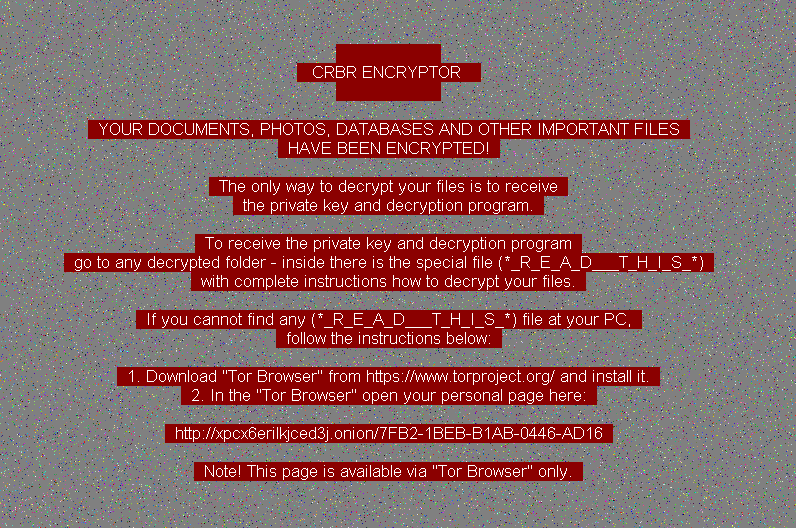
The wallpaper bitmap is generated based on the parameters mentioned in the configuration data:
"wallpaper": {
"change_wallpaper": 1,
"background": 139,
"color": 16777215,
"size": 13,
"text": " \n CRBR ENCRYPTOR ... }Communication
Cerber Connects to 6893 port on the IPs specified by CIDR in the config:
77.12.57.0/27 19.48.17.0/27 87.98.176.0/22The communication packet starts with a hash consisting of the Machine GUID: {MD5_KEY} and ending with {PARTNER_ID}{OS}{IS_X64}{IS_ADMIN}{COUNT_FILES}{STOP_REASON}{STATUS}.
For example, Cerber tries to initiate a connection to the remote server from the range specified in the configuration data by sending a victim’s machine ID:
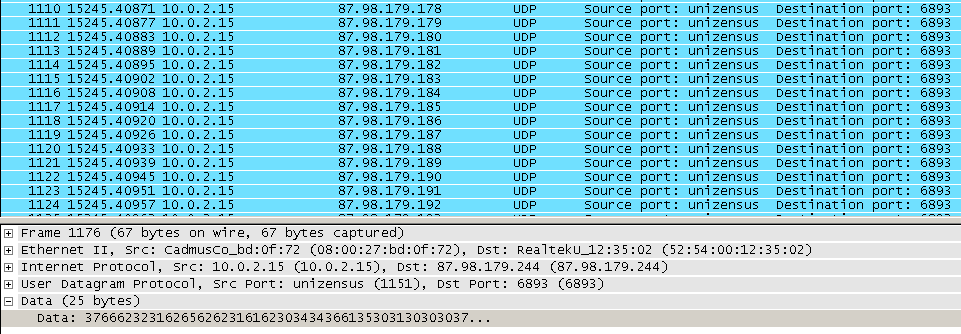
Decryptor
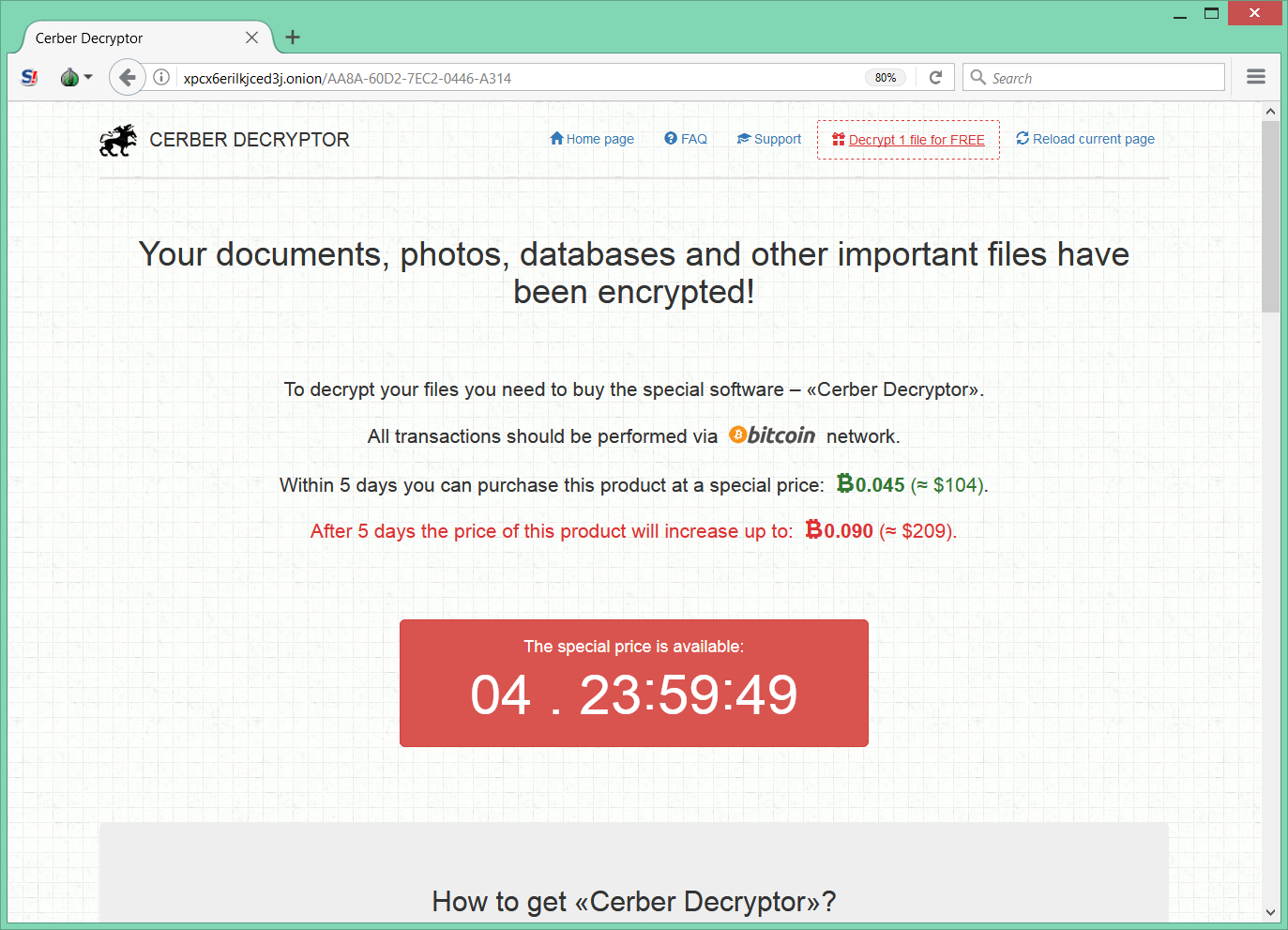
The Decryption Service is available through Tor at http://xpcx6erilkjced3j.onion/<MACHINE_ID>. For example: http://xpcx6erilkjced3j.onion/AA8A-60D2-7EC2-0446-A314
It requires solving the CAPTCHA
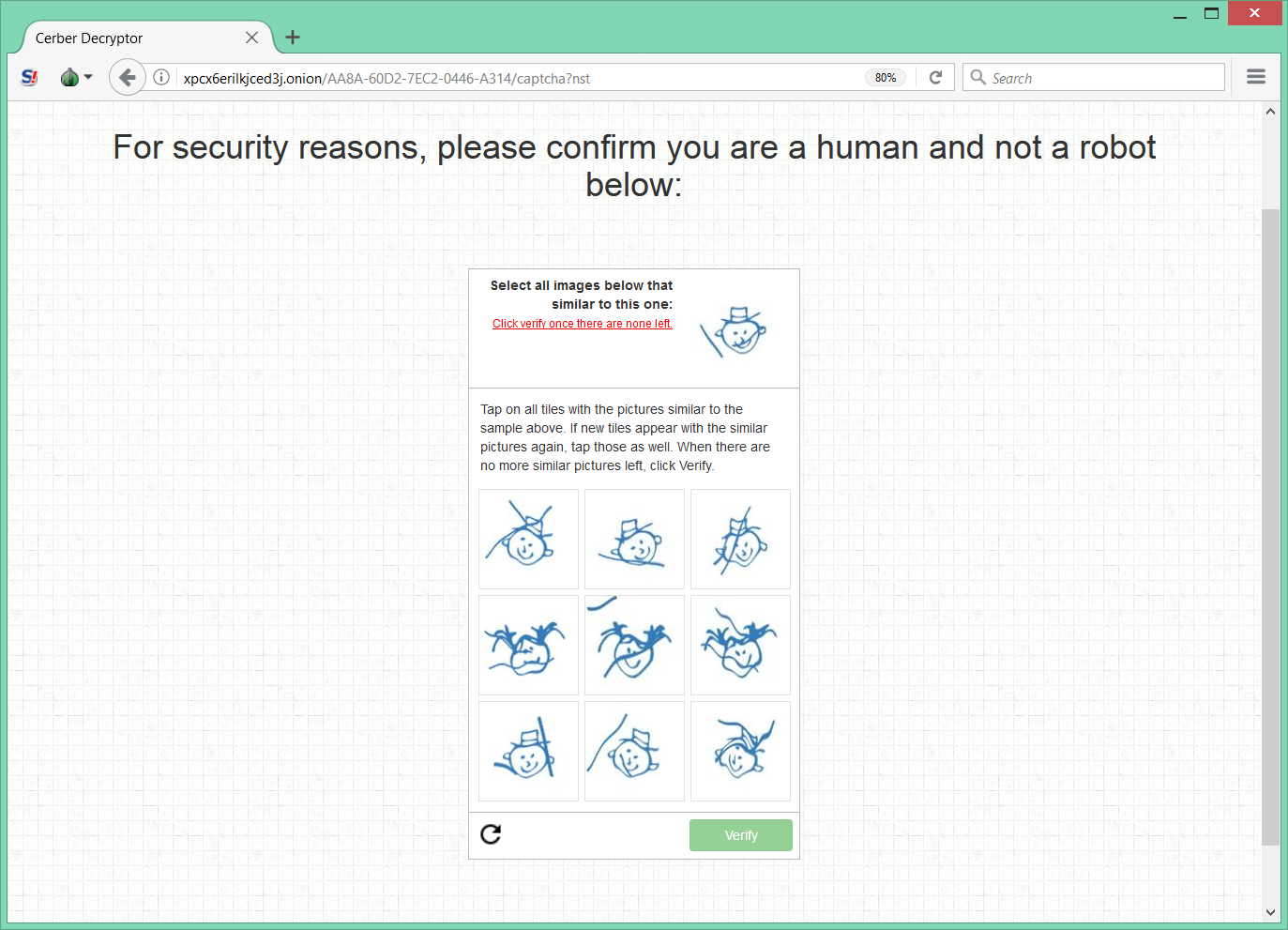
It requires a payment of 0.045 Bitcoins in five days, otherwise the price will be doubled.
Payment
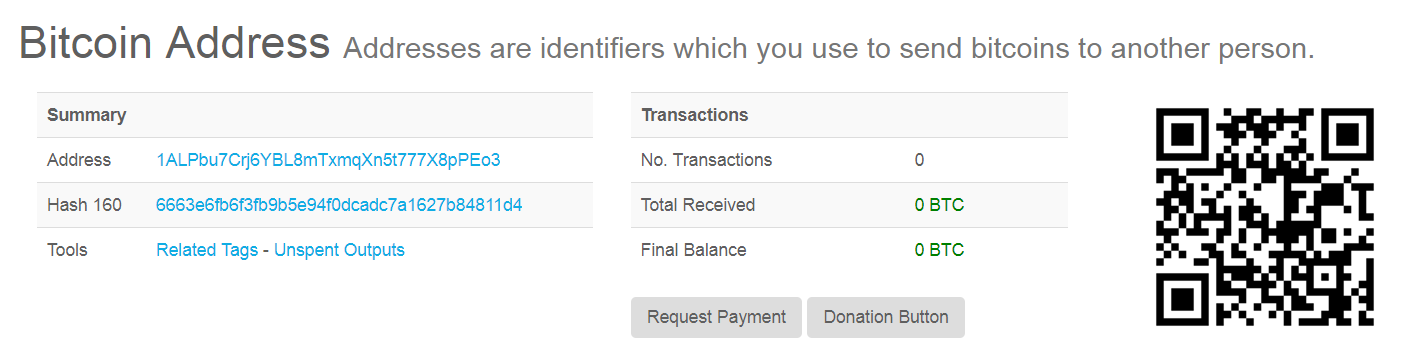
The Bitcoin address used in the attack has not received any transaction yet.
Conclusion
- Cerber is spread through spear phishing email campaigns targeting enterprises.
- Cerber uses polymorphic encryption and API calls obfuscation to bypass antivirus protection.
- As in previous versions, it uses encrypted configuration data stored in a JSON format.
- It uses the encryption scheme of master RSA-2048 key -> session RSA-880 -> RC4-128.
- It is not possible to decrypt files without knowing the master private RSA-2048 key.
- Cerber tries to connect to C&C using the IPs specified in the configuration data in order to send the encryption statistics.
Acronis True Image 2018 Beta Blocks Cerber
The new version of Acronis Active Protection, which is part of Acronis True Image 2018 Beta, detects Cerber ransomware and instantly restores the affected files.
Acronis Active Protection constantly observes patterns in how data files are being changed on a system. One set of behaviors may be typical and expected. Another set of behaviors may signal a suspect process taking hostile action against files. The Acronis approach looks at these actions and compares them to with malicious behavior patterns. This approach is exceptionally powerful in identifying ransomware attacks, even from ransomware variants that are as-yet unreported.The well known Cerber ransomware continues to be active this summer. The size of the cryptolocker varies between 244 to 292 Kbytes, with the new builds spreading through spear phishing email campaigns targeting enterprises. The latest Cerber ransomware easily bypasses traditional defences. The analysed Cerber sample (MD5: cfd2d6f189b04d42618007fc9c540352) was only detected as a suspicious malicious object by nine out of 64 antiviruses on the first submission to Virustotal. The low detection rate can be explained by the fact that the cryptolocker is using a polymorphic encryptor and API call obfuscation to protect its copies from being detected by antiviruses.
Static analysis
The PE EXE file has a fake timestamp, Import Address Table and even Export Address Table.

Export Address Table

Hiding the payload
The latest builds of the Cerber’s code are even more protected with API call obfuscation. To hide the actual imports, Cerber loads them in runtime:

The actual Import Address Table looks like this:

Decrypting the configuration data
The configuration JSON data is encrypted and stored as RCDATA in the resource section:

To decrypt the configuration data, Cerber goes through the following steps:
1. Imports the hard coded RC4 128-bit key from the BLOB data which is 28 bytes in size.

1st byte: BLOB type = PLAINTEXTKEYBLOB (0x08)
2nd byte: version = CUR_BLOB_VERSION (0x02)
5-8 bytes: algorithm id = CALG_RC4 (0x00006801)
9-12 bytes: key size in bytes = 16 (0x00000010)
13-28 bytes: key data ‘ ADBCCC55D6FB379BDA0E3262FF004E1D’2. Wipes the 128-bit encryption key from the memory with zeros after decryption:

3. Calls the CryptEncrypt() function to decrypt the JSON config which is 107 171 bytes in size:

Configuration parameters
The Cerber configuration contains the following information:
- Blacklist
- File extensions for the files not to be encrypted: bat, cmd, com, cpl, dll, exe, hta, msc, msi, msp, pif, scf, scr, sys
- Files:
- Bootsect.bak
- Iconcache.db
- Ntuser.dat
- thumbs.db
- Folders that the cryptolocker should avoid when encrypting files:
- ":\\$getcurrent\\",
- ":\\$recycle.bin\\",
- ":\\$windows.~bt\\",
- ":\\$windows.~ws\\",
- ":\\boot\\",
- ":\\documents and settings\\all users\\",
- ":\\documents and settings\\default user\\",
- ":\\documents and settings\\localservice\\",
- ":\\documents and settings\\networkservice\\",
- ":\\intel\\",
- ":\\msocache\\",
- ":\\perflogs\\",
- ":\\program files (x86)\\",
- ":\\program files\\",
- ":\\programdata\\",
- ":\\recovery\\",
- ":\\recycled\\",
- ":\\recycler\\",
- ":\\system volume information\\",
- ":\\temp\\",
- ":\\windows.old\\",
- ":\\windows10upgrade\\",
- ":\\windows\\",
- ":\\winnt\\",
- "\\appdata\\local\\",
- "\\appdata\\locallow\\",
- "\\appdata\\roaming\\",
- "\\local settings\\",
- "\\public\\music\\sample music\\",
- "\\public\\pictures\\sample pictures\\",
- "\\public\\videos\\sample videos\\",
- "\\tor browser\\"
- Languages that make OS protected from the cryptolocker:
- 1049: Russian,
- 1058: Ukrainian
- 1059: Belarusian,
- 1064: Tajik,
- 1067: Armenian,
- 1068: Azeri (Latin),
- 1079: Georgian,
- 1087: Kazakh,
- 1088: Kyrgyz (Cyrillic),
- 1090: Turkmen,
- 1091: Uzbek (Latin),
- 1092 : Tatar (Russia),
- 2072: Romanian (Moldova),
- 2073: Russian (Moldova),
- 2092: Azeri (Cyrillic),
- 2115: Uzbek (Cyrillic).
- Whitelist
- Folders that should be encrypted:
- "\\bitcoin\\",
- "\\excel\\",
- "\\microsoft sql server\\",
- "\\microsoft\\excel\\",
- "\\microsoft\\microsoft sql server\\",
- "\\microsoft\\office\\",
- "\\microsoft\\onenote\\",
- "\\microsoft\\outlook\\",
- "\\microsoft\\powerpoint\\",
- "\\microsoft\\word\\",
- "\\office\\",
- "\\onenote\\",
- "\\outlook\\",
- "\\powerpoint\\",
- "\\steam\\",
- "\\the bat!\\",
- "\\thunderbird\\",
- "\\word\\"
- Folders that should be encrypted:
Global RSA 2048-bit public key:
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvkty5qhqEydR9076Fevp
0uMP7IZNms1AA7GPQUThMWbYiEYIhBKcT0/nwYrBq0Ogv79K1tta04EHTrXgcAp/
OJgBhz9N58aewd4yZBm2coeaDGvcGRAc9e72ObFQ/TME/Io7LZ5qXDWzDafI8LA8
JQmSz0L+/G+LPTWg7kPOpJT7WSkRb9T8w5QgZRJuvvhErHM83kO3ELTH+SoEI53p
4ENVwfNNEpOpnpOOSKQobtIw56CsQFrhac0sQlOjek/muVluxjiEmc0fszk2WLSn
qryiMyzaI5DWBDjYKXA1tp2h/ygbkYdFYRbAEqwtLxT2wMfWPQI5OkhTa9tZqD0H
nQIDAQAB
-----END PUBLIC KEY-----
Traces on the hard disk
Once being unpacked, Cerber stores its temporary data and encryption keys in a subfolder named using the first part of the Machine GUID, inside the Temp folder. For example:
%Temp%\c36ab9c2
Encryption
Cerber uses RC4 and RSA algorithms for encryption. Every file is encrypted using the RC4 algorithm with a unique 128-bit key.
The file’s RC4 key is encrypted using a RSA-880 public session key generated on the victim’s machine. The prime numbers (p and q) used to calculate the RSA-880 session public key are encrypted using the RSA-2048 master public key delivered in the configuration data embedded in the cryptolocker’s file.
The prime numbers can be decrypted with the RSA-2048 master key by the attacker to restore the RSA-880 session private key through calculating a private key exponent (d) using the extended Euclidean algorithm.
The new file contains the encrypted RC4 key used to encrypt this file as well as the encrypted original file’s data, original filename, and checksum stored in a specific order. Cerber also adds a 60-byte block of randomly generated data into the middle of the file to complicate the encrypted file structure even more.
Key encryption
First, the RSA-2048 public key from the configuration file is decoded from Base64 to PEM format and then to PUBLICKEYBLOB:

Once decoded, the CERT_PUBLIC_KEY_INFO structure contains a public key and its algorithm (OID_RSA_RSA "1.2.840.113549.1.1.1" - RSA is used to both encrypt and sign the content):

The RSA-2048 public key is to be imported as PUBLICKEYBLOB.


1st byte: BLOB type = PUBLICKEYBLOB (0x06)
2nd byte: version = CUR_BLOB_VERSION (0x02)
5-8 bytes: algorithm id = CALG_RSA_KEYX (0x0000A400)
9-20 bytes: RSAPUBKEY {magic = ‘RSA1’, key length = 2048 bits, public exponent = 65537}
21-276 bytes: key data 256 bytesThen, Cerber creates another RSA public key but with an 880-bit modulus length and saves it to the temporary file:

The RSA-2048 public key is used to encrypt an 114-byte block of data that consist of two prime numbers, each 55 bytes, generated for a RSA-880 public key that is used to encrypt the RC4 key and the 4-byte header that specifies the size of each block ‘37003700’:

The encrypted block is stored in a tmp file in the %TEMP% folder and added to the end of every encrypted file:

File encryption
Cerber encrypts a file using the RC4 algorithm with a 128-bit key generated for every file that will be encrypted.
After encryption, the file will contain the following data blocks:
| Offset | Data |
|
0 |
Original file data (‘skip_bytes’ = 1800) |
|
1800 |
Randomly generated data (60 bytes) |
|
1860 |
Encrypted data from offset 1860 (‘skip_bytes’ + 60) to the end of the original file |
| The encrypted data containing the original filename, checksum, and RC4 key (48 bytes) | |
|
Encrypted 99 bytes that includes header (39 bytes) and 60 bytes of the original file located after ‘skip_bytes’ (offset 1800) that were replaced with the randomly generated data (110 bytes). The header (39 bytes) includes: magic = FrbR, size of data, 16-byte RC4 key |
|
| RSA-880 prime numbers p and q encrypted by RSA-2048 (256 bytes) |

The file with the encrypted data is renamed as:
<Random characters>.<4th part of the Machine GUID>Ransom notes
The ransom notes are stored in the folders together with the encrypted files and are named in the following format:
_R_E_A_D___T_H_I_S___<RAND>_.hta
_R_E_A_D___T_H_I_S___<RAND>_.txt

At the end of the encryption, the cryptolocker sets the familiar Cerber-style wallpaper:

The wallpaper bitmap is generated based on the parameters mentioned in the configuration data:
"wallpaper": {
"change_wallpaper": 1,
"background": 139,
"color": 16777215,
"size": 13,
"text": " \n CRBR ENCRYPTOR ... }Communication
Cerber Connects to 6893 port on the IPs specified by CIDR in the config:
77.12.57.0/27
19.48.17.0/27
87.98.176.0/22The communication packet starts with a hash consisting of the Machine GUID: {MD5_KEY} and ending with {PARTNER_ID}{OS}{IS_X64}{IS_ADMIN}{COUNT_FILES}{STOP_REASON}{STATUS}.
For example, Cerber tries to initiate a connection to the remote server from the range specified in the configuration data by sending a victim’s machine ID:

Decryptor
The Decryption Service is available through Tor at http://xpcx6erilkjced3j.onion/<MACHINE_ID>. For example: http://xpcx6erilkjced3j.onion/AA8A-60D2-7EC2-0446-A314

It requires solving the CAPTCHA

It requires a payment of 0.045 Bitcoins in five days, otherwise the price will be doubled.

Payment
The Bitcoin address used in the attack has not received any transaction yet.

Conclusion
- Cerber is spread through spear phishing email campaigns targeting enterprises.
- Cerber uses polymorphic encryption and API calls obfuscation to bypass antivirus protection.
- As in previous versions, it uses encrypted configuration data stored in a JSON format.
- It uses the encryption scheme of master RSA-2048 key -> session RSA-880 -> RC4-128.
- It is not possible to decrypt files without knowing the master private RSA-2048 key.
- Cerber tries to connect to C&C using the IPs specified in the configuration data in order to send the encryption statistics.
Acronis True Image 2018 Beta Blocks Cerber
The new version of Acronis Active Protection, which is part of Acronis True Image 2018 Beta, detects Cerber ransomware and instantly restores the affected files.
Acronis Active Protection constantly observes patterns in how data files are being changed on a system. One set of behaviors may be typical and expected. Another set of behaviors may signal a suspect process taking hostile action against files. The Acronis approach looks at these actions and compares them to with malicious behavior patterns. This approach is exceptionally powerful in identifying ransomware attacks, even from ransomware variants that are as-yet unreported.
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.

Comments (0)