Intel's Bug, Spectre and MeltDown Updated 01/19/2018
EE Awarded 2018
IT articles https://medium.jortit.com/
Microsoft Certified Pro (server/Exchange)
Yesterday 01/03/2018 Intel's company says that their (Central Processing Unit 'CPU') chips have been discovered with a couple of serious security bugs, that allows a malicious hacker to get the information in real time about your computer (even passwords or your Credit card number, etc).
With Meltdown CVE-2017-5754 is a vulnerability of how the Operating System handles the memory, so to fix it would require a software patch in the OS, and with Spectre, CVE-2017-5715 the hacker is able to get control over processes and get information from your pc, even in real time.
So putting this into perspective, this is it how it looks like: https://youtu.be/RbHbFkh6eeE
Intel and other people are working on a solution of the patches right now. But right now the important things you need to know is if you are affected or not, so how do you know if you're affected?
How to find out if your computer is vulnerable "The Powershell Way"
Those who know me, do know that I really love PowerShell, and a couple of hours before there was released a PowerShell module, Using official Microsoft documentation. So running in a PowerShell console with administrative privileges:
Install-Module SpeculationControl
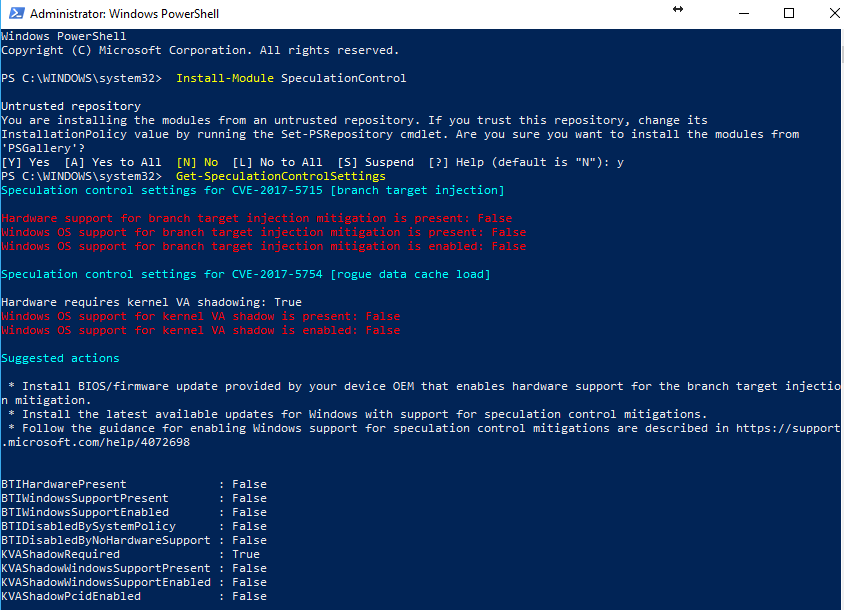
Get-SpeculationControlSettingsI ran this on my laptop (I5) and I got this:
It turns out that my laptop didn't have any kind of protection for CVE-2017-1515 (branch target injection)
So it should be patched with firmware from the hardware manufactures (Motherboard BIOS), that most of the manufacturers don't have still (01/10/2018), for example, ASUS, that send me a "We actually didn't have any updates we will publish as soon we got something", that was my answer in Spanish.
The only thing we can do right now is this:
And be aware of the BIOS updates.
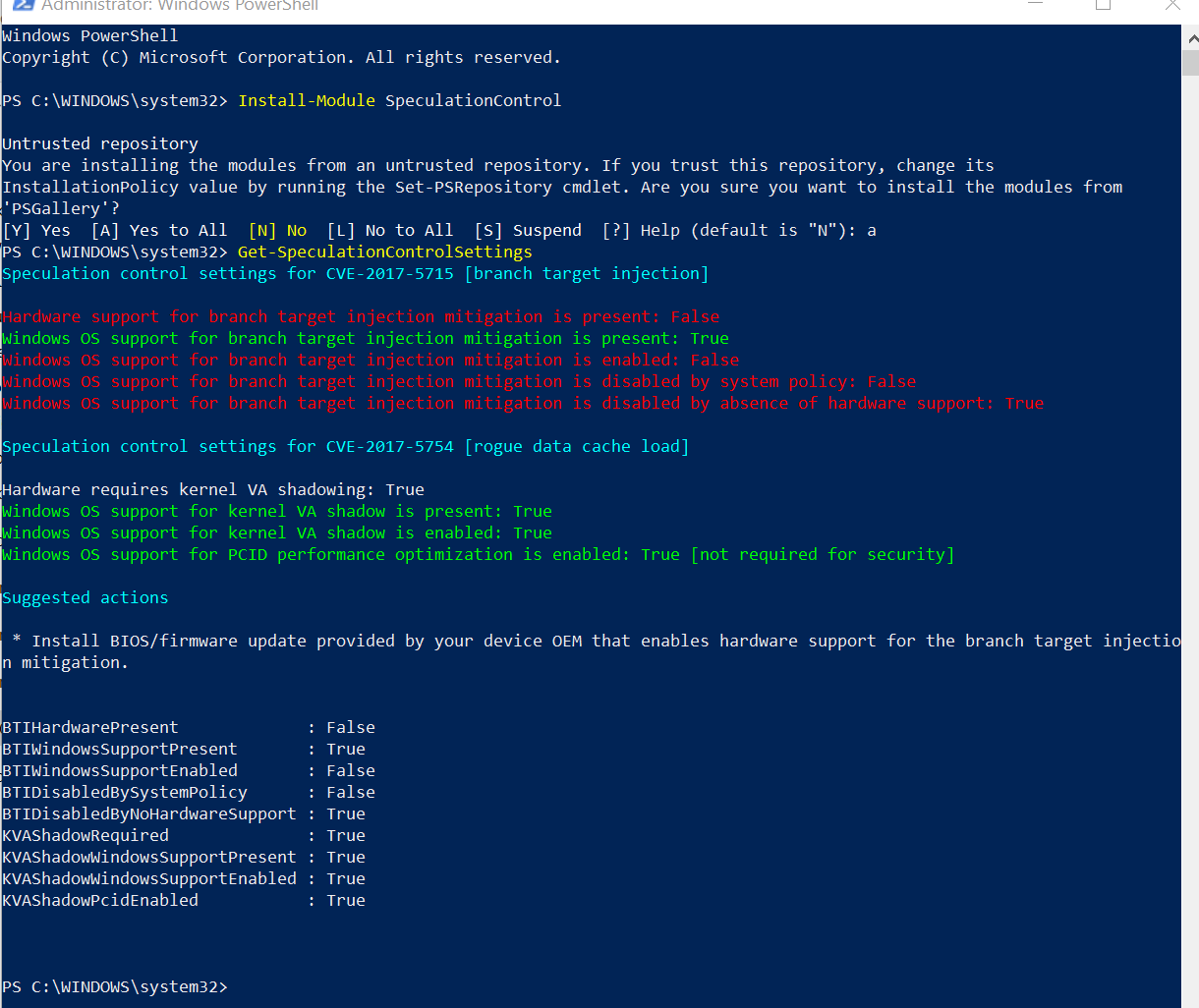
Here's another computer (Desktop computer):
Which the only solution is to request for BIOS/Firmware updates of your manufacturers.
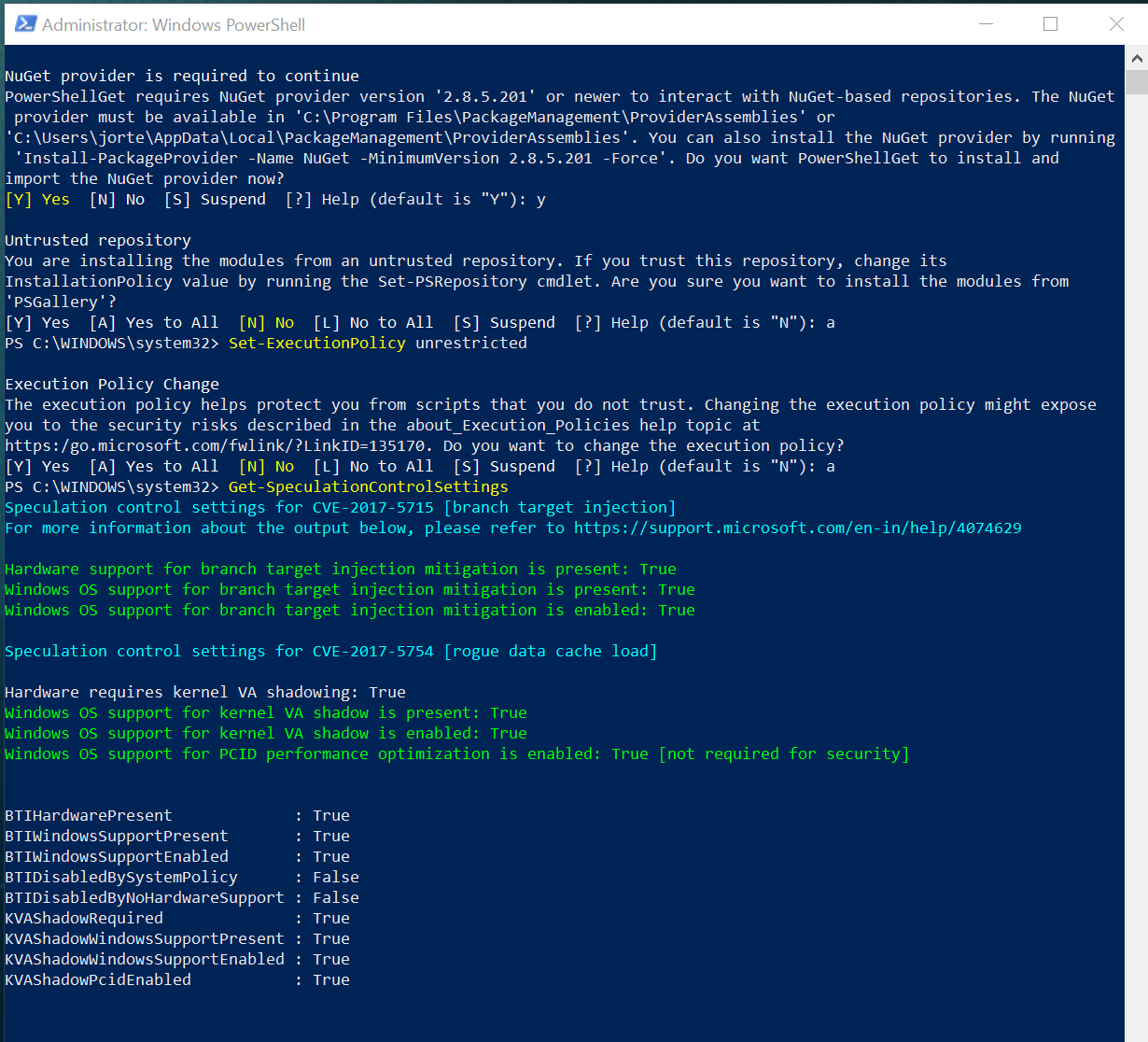
UPDATE 03/01/2018 - I went beyond and test it on another computer ?
I did the test on a brand new computer, I7 8770k with motherboard Aorus x370 Gaming 7 with the latest BIOS.
Initially, I started PowerShell with elevated privileges (as administrator) and run:
Set-ExecutionPolicy Unrestricted
The reason is because the cmdlet uses scripts and if you don't do this, you won't be able to run the command: Get-SpeculationControlSettings cmdlet once the module is installed.
Then, I run the "install-module SpeculationControl" it asked to install the NuGet package version 2.87.5.201 to install the required, I accept and then also accepted the installation for all the required software.
This is how it should look a computer without this issues discovered on early 2018:
What CPUs are being Affected?
In the official Intel's page: The CPUs affected are virtually almost everything from the last 10 years...
- Intel® Core™ i3 processor (45nm and 32nm)
- Intel® Core™ i5 processor (45nm and 32nm)
- Intel® Core™ i7 processor (45nm and 32nm)
- Intel® Core™ M processor family (45nm and 32nm)
- 2nd generation Intel® Core™ processors
- 3rd generation Intel® Core™ processors
- 4th generation Intel® Core™ processors
- 5th generation Intel® Core™ processors
- 6th generation Intel® Core™ processors
- 7th generation Intel® Core™ processors
- 8th generation Intel® Core™ processors
- Intel® Core™ X-series Processor Family for Intel® X99 platforms
- Intel® Core™ X-series Processor Family for Intel® X299 platforms
- Intel® Xeon® processor 3400 series
- Intel® Xeon® processor 3600 series
- Intel® Xeon® processor 5500 series
- Intel® Xeon® processor 5600 series
- Intel® Xeon® processor 6500 series
- Intel® Xeon® processor 7500 series
- Intel® Xeon® Processor E3 Family
- Intel® Xeon® Processor E3 v2 Family
- Intel® Xeon® Processor E3 v3 Family
- Intel® Xeon® Processor E3 v4 Family
- Intel® Xeon® Processor E3 v5 Family
- Intel® Xeon® Processor E3 v6 Family
- Intel® Xeon® Processor E5 Family
- Intel® Xeon® Processor E5 v2 Family
- Intel® Xeon® Processor E5 v3 Family
- Intel® Xeon® Processor E5 v4 Family
- Intel® Xeon® Processor E7 Family
- Intel® Xeon® Processor E7 v2 Family
- Intel® Xeon® Processor E7 v3 Family
- Intel® Xeon® Processor E7 v4 Family
- Intel® Xeon® Processor Scalable Family
- Intel® Xeon Phi™ Processor 3200, 5200, 7200 Series
- Intel® Atom™ Processor C Series
- Intel® Atom™ Processor E Series
- Intel® Atom™ Processor A Series
- Intel® Atom™ Processor x3 Series
- Intel® Atom™ Processor Z Series
- Intel® Celeron® Processor J Series
- Intel® Celeron® Processor N Series
- Intel® Pentium® Processor J Series
- Intel® Pentium® Processor N Series
The solution?
The solution is to request loudly a firmware update to your MotherBoard Manufacturer and install it As soon as possible.
My MB's manufacturer is ASUS (Formula VII) with still no updates (01/09/2018) and I don't think they are going to even bother in doing it.
My motherboard is simply not listed https://www.asus.com/mx/Motherboards/MAXIMUS_VII_FORMULA/HelpDesk_BIOS/
What I did was to request via email an update for all that have brought that MB
Depending of your Operating System, you can use the KB listed on microsoft official site:
Be aware of windows updates:
It's pretty important that updates (windows updates) that will be applied and released next week or so, to be installed "don't click, not now" as Snowden says:
It needs to be installed it on every server, on every client including those that are in windows azure.
For those that use Windows Azure
The solution is to change the network cards in your VMs so possibly you would need to remove them (without deleting and re-create the virtual switches using the EnabledAceleratedNetwork Option, as documented in https://azure.microsoft.com/en-us/blog/securing-azure-customers-from-cpu-vulnerability/ and https://docs.microsoft.com/en-us/azure/virtual-network/create-vm-accelerated-networking-powershell
So it's important that every single computer that you manage and especially those for clients like banks or really dedicated clients with their data and computers receive these updates as soon as possible, there are people just finishing given the "happy new year" in their computers to their families for working on this, this article is a way to compile all the information I got in my mind and put it in a single point and also a way to thank all of them.
Thank you, Michael for all that I haven't heard of.
For those that are really concerned about how this can be exploited, use the original articles as the scientists do: Spectre and Meltdown
And to read even more about it, I'd recommend this one :
Update 01/19/2018
Here's a bunch of resources to help mitigate this vulnerability, please kindly go to the Resources section of this link:
In there, you will find the guidance for AMD windows OS security update, surface guidance, Azure KB, even NVIDIA security advisory. Also, you will find additional resources by OEM manufactures with the links of each to give the support about this vulnerability.
As added value, I'd like to add the direct download link for most Recent windows and windows server's product software https://www.catalog.update.microsoft.com/Search.aspx?q=KB4056892
The latest BIOS for the Motherboard Gigabyte z370 AORUS GAmming 7, can be found here:
https://www.gigabyte.com/Motherboard/Z370-AORUS-Gaming-7-rev-10#support-dl
You just need to uncompress the downloaded file into a flash drive formatted as fat32 and plug it into the orange USB port.
Thank you for reading
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (2)
Commented:
This is the Meltdown and Spectre problem which is a new flaw.
Author
Commented: