Top 10 Ways to Secure Your File Servers
As an IT manager; you need to be doing everything you can to ensure the integrity of your data. If you’re wondering how best to do this, I’d suggest you start right here. Listed below are some of our security top tips to preventing data leakage.
1. Centralized Management of Permissions
If a company has a decentralized way of storing confidential files and folders including the encrypted ones, IT managers will have to scan the entire network to locate required files and modify permissions. Instead of having data spread on different computers, IT teams must consolidate and keep all their files & folders in one place. Centralized management of permissions ensures that you can quickly lock down overexposed data and control file and folder permissions in a quicker and easier way.
2. Limiting Expansive Privileges to Users
The wider an employee’s portfolio of network access, the greater the risk of unusual file server access events! Having an overly long list of privileged users can put your domain security at risk. The best solution to this is to limit the number of privileged users on your file servers.
3. Reinstating Micro View on File Servers
Whether it’s changing user access permissions, spotting unusual user activity or tracking last read/modified files or folders, these actions correspond to micro events in a file server. Having the ability to drill down into the intricate details enables IT teams to quickly unravel complex file server activity and get to the cause of the problem.
4. Applying the Rule of Thumb
Assigning effective share-level, NTFS and overall permissions can lead to unfettered access or even Access Denied messages for users that require share access. In other words, identifying and determining effective permissions ensures that no one has excessive access rights that would put your data at risk.
5. Administering Control with Secure Change Management
A secure change management practice delivers complete visibility into excessive access rights, overexposed/stale data, anomalous access attempts and everything across your file servers. Introduce secure change management to help prevent malicious insiders from abusing their administrator privileges.
6. Giving Your Files & Folders Succinct and Intuitive Names
Long names are harder to read and even harder to skim through when you are scanning lists of files and folders. Remember to also pick a phrase that means something when you are naming one of your files. That said, name your files and folders with simple and short titles.
7. Monitoring Your Employees
Regular monitoring of your employees’ systems enables you to keep track of their day-to-day actions. Protect your vital files by monitoring to-and-fro data exchange within the organization. Moreover, your dedicated file server tracks each users’ activities and protects your network from potential insider attacks.
8. Protecting Against Unauthorized Users
Users with unauthorized access to the internal network may attempt to enter, trespass within, interfere with or otherwise intercept and try to change the system. It is advisable to steer clear of administrative privileges when possible, especially when the user holds unauthorized access to the file server.
9. Control File Access
Restricting file and folder access to specific groups or individual users limits control from the many to the few. When it is about preventing file server access exploitation, your IT team must run a regular examination of share and security permissions to keep intruders away.
10. Use the Auditing Function
When it comes to file change auditing, it’s better to be proactive. Auditing your file server is an easy way to keep track of all the changes taking place to your sensitive files and folders. Additionally, you get a single log for a single change displaying who, what, where and when the changes are made in your files and folders.
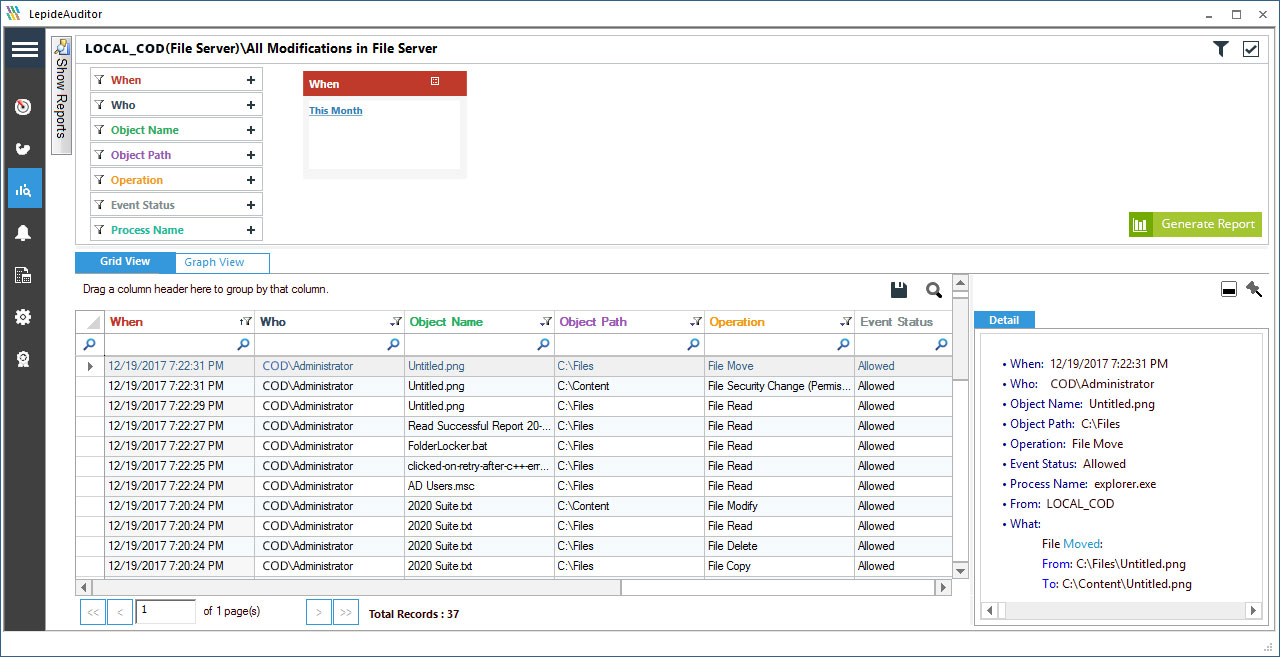 Figure 1: All Modifications in a File Server Report
Figure 1: All Modifications in a File Server Report
So, if you want to beef up the security around the critical files and folders (even if they are encrypted using native method of Windows) in your file server, LepideAuditor for File Server could be the solution for you. This file server auditing solution helps you to report on attempts of file or folder creation, modification, deletion or permission changes. Don’t sit idle, be proactive and protect your File Server today!
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.

Comments (0)