Cloud Security Threats, Risks, and Concerns
1- Cloud Computing
The NIST Definition of Cloud Computing: “Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.”
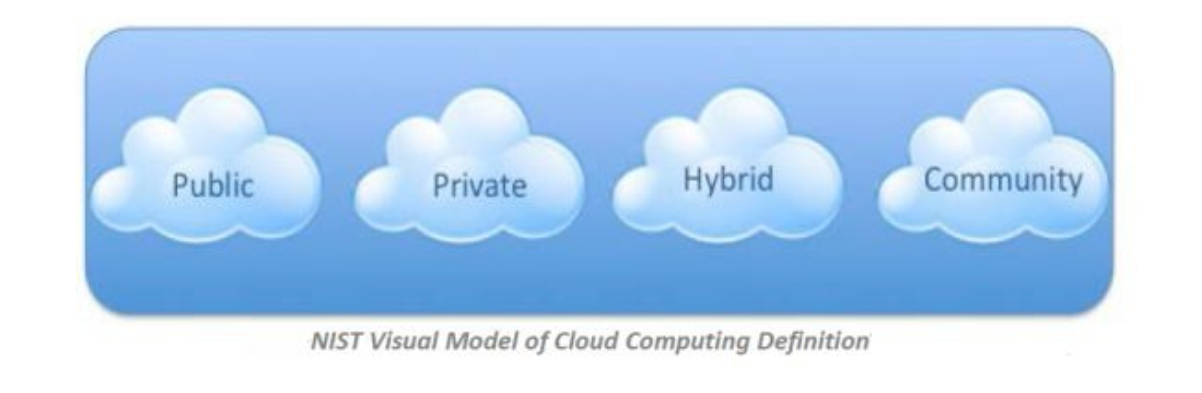
2- There are Four Cloud Types
The first is a Private Cloud. Private clouds are privately owned and managed cloud services where access is limited to the enterprise employees only. Large enterprises tend to use private cloud rather than public, because it is completely managed by them and is, therefore, more secure, aside from providing the services that meet their exact needs with lower cost. There is also a virtual private cloud. This is purchased from another vendor where you still have hardware that is only used by your enterprise, but it’s managed by the vendor. There are also different levels of separation for tenants in a virtual private cloud.
The second type is a Public Cloud. This has the same concept as private cloud, but it’s accessible to anyone with a credit card. Resources are shared across many tenants without interfering with each other. Public cloud users can manage their virtual machines, or whichever service they are subscribed to, via a self-service portal.
The third type is a Hybrid Cloud. This is a mix between private and public cloud with orchestration between the two. An example of hybrid cloud is Windows Azure.
The fourth and last type of cloud is a Community Cloud. A community cloud is a multitenant infrastructure shared between several organizations that have common concerns such as security, audit, compliance, etc.
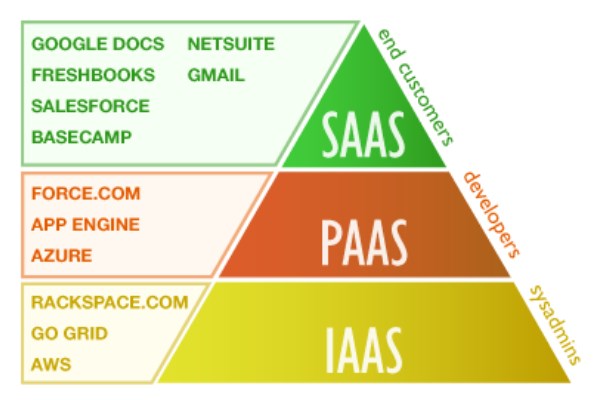
3- IaaS, PaaS and SaaS – Cloud Service Models
Infrastructure as a Service (IaaS) is a form of cloud computing that provides virtualized computing resources over the Internet. IaaS is a highly scalable resource that can be adjusted based on the customer needs payable on a peruse basis, such as hourly, weekly, or monthly. IaaS is provided by a third party that hosts hardware, software, servers, storage, etc. It also provides applications, backup plans, maintenance, and disaster recovery planning. Examples of IaaS include Amazon Web Services (AWS), Microsoft Azure, Google Compute Engine, Rackspace Open Cloud.
Platform as a Service (PaaS) is a model where the cloud provider hosts hardware and software tools needed for application development and makes it available for users as a service. As a result, users do not need to install any OS or application, as they are already installed. This does not necessarily mean it will replace the business infrastructure; but rather, it is a cooperation. Examples of PaaS include Amazon Web Services (AWS), Elastic Beanstalk, Google App Engine and Heroku.
Software as a Service (SaaS) is an application distributed over the internet where the cloud provider hosts the hardware and the application software is installed and ready to use. Office 365 and Google Docs are both examples of SaaS. The cloud provider makes sure that the systems are backed up and proper protection controls are in place; Be aware this does not eliminate threats and vulnerabilities.
4- Moving to Cloud
Why are so many businesses moving up to the cloud? Simply put, it has many benefits! Here are a few of them:
- Scalability: Cloud services are ideal for growing businesses. It is easy to scale up if your needs increase. Likewise, you can scale down if needed.
- Disaster recovery: Any business from medium size and up needs a proper disaster recovery plan, such as leaving small businesses without a contingency plan due to lack of cash flow. Having your services hosted on cloud helps you achieve proper backup and recovery solutions.
- Automated software updates: No pare patch server on premises! No more bad updates that crash your servers. All updates are managed by the cloud service provider.
- Lower capital expenditure: Cloud computing saves the users by eliminating the needs the high cost of hardware. You simply pay for your usage.
- Flexibility and increased collaboration: Your team can access, share, and edit documents from anywhere. Cloud workflow and sharing applications ensure that updates are done in real time.
- Work from anywhere: With cloud computing, you can set up your office at home or at the beach. All you need is an internet connection.
- Document control: Documents are shared in a central location and accessed only by authorized users. This provides some security as well as better visibility. Users always see the latest version of a file, when it was last edited, and whoever was the last person to edit. This greatly improves collaboration.
- Security: Lost laptops or stolen data from physical systems cost billions of dollars each year. When you make sure that users do not store any data on their personal computers or the company-provided laptops when working from home or out of the office, you decrease the risk of stolen or lost company secrets and valuable information.
- Competitiveness: You never thought you would be able to use those expensive technologies from the market? Now almost all technologies are available for anyone. That is, if you have a credit card.The pay as you go service offers small and organizations with a limited cash flow to use competitive applications in their daily operations.
- Environmentally friendly: With cloud computing, you show your love for nature. Huge savings on the power bill always mean better environment!
5- Cloud Computing depends on Virtualization
From an investment point of view as well as productivity, it would be ineffective and inefficient if the provider is allocating a physical server for each client. Besides, on a physical server, there is no way to scale up or down based on your application needs. This would result in either low performance or a waste of resources. This issue is solved with virtualization where you can allocate resources based exactly on your needs.
Virtualization technology provides a technique where you can virtualize all your resources such as CPU, memory, NIC, and storage, thus allocating a certain amount of these resources to a given number of virtual machines. The number of virtual machines that can be created on a server is limited to either your resource pool or your virtualization technology license.
6- The following are more benefits offered by Virtualization
- Snapshots: allow you to take an image of a VM at a specific point in time and you can revert to that snapshot when needed. The number of snapshots you can take is limited to only your storage space.
- Patch compatibility: With any virtualization vendor, updates do need to be accounted for before implementation. Usually, patch releases are dependent on the preceding update and compatibility for patches is assumed to have the same compatibility of older update releases.
- Host availability and elasticity: Availability is usually addressed in the SLA (service level agreement) with the vendor you contract with. Most vendors provide five 9s of uptime, which is 99.999 percent of the time. This is the industry standard. According to the National Institute of Standards and Technology, or NIST, an essential element is to provide rapid elasticity. This means resources can be automatically allocated or release based on the customer usage.
- Security control testing: This is a subset of penetration testing where systems are reviewed and examined for weaknesses; such as Sand-boxing: which means running an application in restricted memory areas. In this case, it limits the possibility of a malicious code to access another app or data associated with it. This attack is called server hopping.
7- Cloud Computing Threats
Even though a cloud provider has more capital to implement enterprise security controls, this does not mean it is a 100% secure environment; but risks will always exist. Securing cloud services depends on the provider and client as well. Below are identified some serious security threats in cloud computing.
• Data loss
• Account hijacking
• Insecure API
• DoS
• Extra billing for unused resources
• Inside threats
• Poor security form SP
• Multi-tenancy related breaches
Cloud environments become an attractive target for attacks due to the vast amount of data stored on them. Damage can sometimes be severe, depending on the data exposed. Financial information may be the leader here, but what is more devastating is trade secrets, health information, and intellectual property.
When a data breach occurs, companies may face lawsuits, fines, and sometimes, even criminal charges. Breaches may have their effects for many years, such as loss of business and reputation damage.
Organizations are responsible to secure their data. Cloud providers deploy security controls to protect the environment; But, ultimately, data security is the responsibility of the client. That’s why it is recommended to use multi-factor authentication and encryption.
One of the main causes of data breaches is poor authentication – weak passwords and poor certificate management. Often organizations allocate unnecessary privileges to users or they forget to remove permissions when the user role changes. The problem with password authentication is that it can be easily stolen. Therefore, multifactor authentication such as onetime password or smartcards is a better approach to secure your login information.
Sometimes developers include cryptographic keys and credentials in their source code. Guess where they publish it? GitHub. Cryptographic keys need to be rotated on a regular basis. This will make it harder for an attacker to log in using a key that has been obtained without authorization.
Another big threat in the credentials world: identity federation. Centralizing identity in a single repository poses a huge threat, especially when you are federating with a cloud provider. Clients need to understand how the cloud provider is managing and securing this repository.
Every cloud provider offers application program interfaces, APIs. They use these APIs to interact and manage the cloud services. The security of a cloud depends heavily on the security of APIs, this is because they are exposed to the open internet. The risk increases when third parties develop new services relying on these APIs. In this case, you are exposing more services and credentials to the unsecure internet. A weak development will certainly result in a data breach.
Threat modeling applications and systems, including data flow and architecture/design, become important parts of the development lifecycle. Add to this security focused code reviews and rigorous penetration testing.
Vulnerabilities and exploits are not new subjects. As a result, cloud computing shares resources such as memory and storage across many tenants. This has created a new attack surface. Vulnerabilities in the cloud are treated the same as on premises, so periodic vulnerability scanning is recommended, followed by patch management. The cost of patching bugs and vulnerabilities is relatively small compared to the damage cost in case of a breach.
Cloud services add a new dimension to the known attacks such as hijacking. Since all transactions are through the internet, hackers do not need to breach your internal network, but they can eavesdrop on you and your cloud provider. Potential risks are transaction manipulation and/or data modification.
Common defense in-depth protection strategies can contain the damage incurred by a breach. Organizations should prohibit the sharing of account credentials between users and services as well as enable multifactor authentication schemes where available. Accounts, even service accounts, should be monitored so that every transaction can be traced to a human owner. The key is to protect account credentials from being stolen.
Current or former employees, receptionists or system administrators – any employee – can pose a threat, resulting in a penetration through the whole security system. The same goes for the cloud! If a disgruntled employee at your cloud provider decided to manipulate data, you will be at risk if you are not using your own encryption mechanism. The key here is to not depend on the cloud provider security controls but implement your own security layers.
Advanced Package Tools, APTs, infiltrate systems to establish a foothold. Then they stealthily extract data and intellectual property over an extended period of time. APTs typically move laterally through the network and blend in with normal traffic, so they're difficult to detect. The major cloud providers apply advanced techniques to prevent APTs from infiltrating their infrastructure, but customers need to be as diligent in detecting APT compromises in cloud accounts as they would in on-premises systems. Common points of entry include spear phishing; direct attacks, USB drives preloaded with malware and compromised third-party networks.
Regularly reinforced awareness programs keep users alert and less likely to be tricked into letting an APT into the network, and IT departments need to stay informed of the latest advanced attacks. Advanced security controls, process management, incident response plans, and IT staff training all lead to increased security budgets.
Although it rarely happens, loss of data still poses a serious risk. Data can be deleted from the cloud due to provider error or malicious hacker breaching into the data-center. Natural disasters are also a threat here, as cloud data-center are affected by them in the same way like any other facility. Cloud providers now distribute data across many locations and perform data backup as a precaution to save their clients' data in case of a disaster.
Organizations that embrace the cloud without fully understanding the environment and its associated risks may encounter a “myriad of commercial, financial, technical, legal, and compliance risks”. Due diligence applies whether the organization is trying to migrate to the cloud or merging (or working) with another company in the cloud. For example, organizations that fail to scrutinize a contract may not be aware of the provider’s liability in case of data loss or breach.
Operational and architectural issues arise if a company's development team lacks familiarity with cloud technologies as apps are deployed to a particular cloud. Organizations must perform extensive due diligence to understand the risks they assume when they subscribe to each cloud service.
Cloud computing can be used to initiate attacks just the same as having a server on your premises. It can be used to break an encryption key or launch distributed denial of service (DDoS) attack. A cloud provider must scrutinize the traffic by looking for suspicious traffic and offer tools for customers to monitor their cloud environment health.
Denial of service (DoS), attacks have been around a long time, but recently, they became more effective thanks to cloud computing. Cloud systems may slow down or time out. When a DoS attack targets a specific customer, the customer ends up paying the bill for high processing usage and bandwidth. Unfortunately, nothing much can be done. DoS also can target the cloud provider, but this requires a huge bandwidth attacking the data-center, which is known as DDoS.
Cloud providers tend to be better poised to handle DoS attacks than their customers. The key is to have a plan to mitigate the attack before it occurs, so administrators have access to those resources when they need them.
Vulnerabilities in shared technology pose a significant threat to cloud computing. Cloud service providers share infrastructure, platforms, and applications; and, if a vulnerability arises in any of these layers, it affects everyone. “A single vulnerability or misconfiguration can lead to a compromise across an entire provider’s cloud.”
It is recommended to have a defense in-depth strategy, including multifactor authentication on all hosts, host-based and network based intrusion detection systems. It is also recommended that you apply the concept of least privilege, network segmentation, and patching shared resources.
References:
searchcloudcomputing.techtarget
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (1)
Commented: