Ransomware: One Year after WannaCry - are we any better off?
When I first started writing articles about Ransomware for Experts Exchange and even up to last year, Ransomware was still a problem, but one we are learning to deal with. The recent attack on Boeing was purportedly a WannaCry virus and Boeing said they contained it fairly quickly. This would not have been the case a year ago.
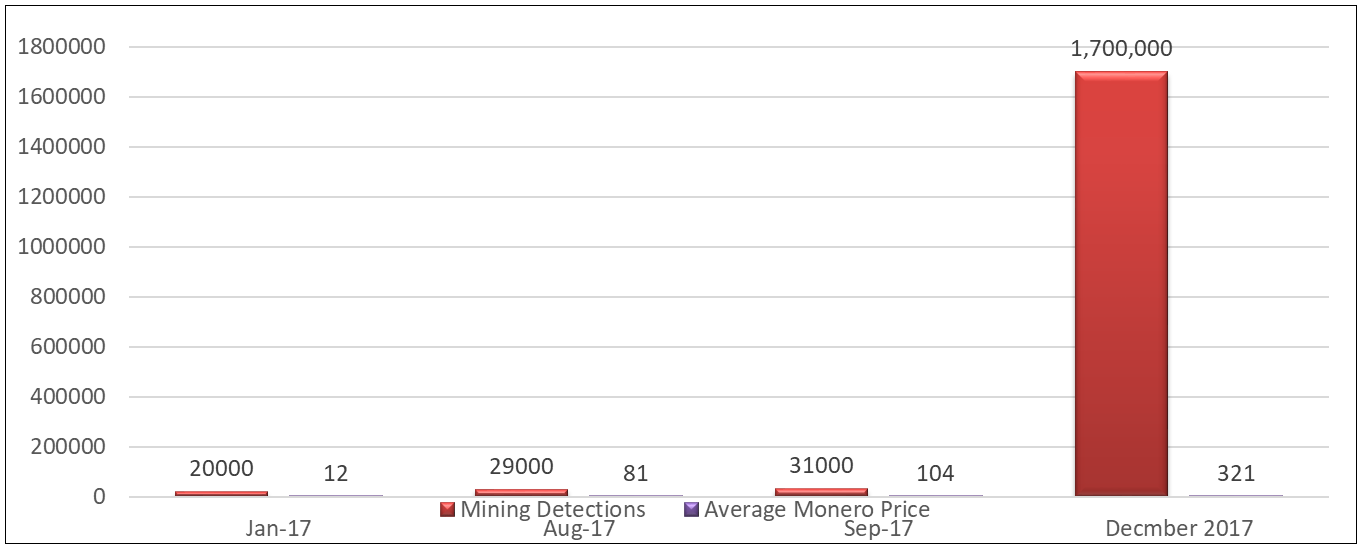
Fortunately or unfortunately, ransomware has become more of a distraction. Targets are infected with ransomware to distract the end user, while some coin-mining software is deposited and run on the endpoint, unbeknownst to the user. Symantec reports that coin-mining attacks rose 34,000% in the last quarter of 2017 (Symantec ISTR 2018).
(source: Symantec ISTR #23, 2018)
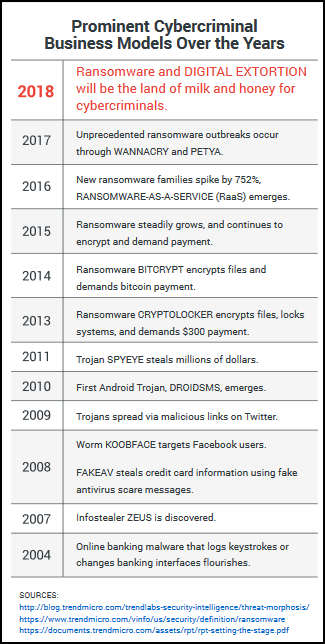
Ransomware development/timeline
One can get a very specific timeline, or a generalized timeline, like this one:
But I believe it is more important to look at the basic evolution of ransomware. This helps us not only to understand how to defend against it but also how to defend against the next step it may take.
The most innocuous ransomware is scareware. Scareware attempts to scare the end user into paying without actually doing anything. The vanilla lockers attempt to extort money by locking one's device and promising to unlock it when the ransom is paid. Many of the early variants had the unlock keys embedded into the dropped malware.
Then there is general ransomware/crypto-ransomware followed by Doxware (ransomware which mines personal documents before encrypting them and then threatens to make these documents public if a ransom is not paid (encryption beforehand works well with this type of attack).
Some later versions of ransomware are mostly destructive in that they now encrypt devices and files but have no way to decrypt them, even if a ransom is paid. The latest variants seem to have targeted IoT devices and have been entirely too successful.
Internet of Ransomware Things
Maybe one of the more troubling implementations of ransomware is those variants that target IoT devices. Many of these devices have no way to change default passwords and the default security is fairly low or non-existent. This was evidenced by the massive Mirai and Persirai DDoS attacks. And more recently Reaper, the IoT botnet, compromised many devices from a variety of different manufacturers. Even patching devices could be dangerous as the KRACK attack showed that a wireless connection to the internet could be easily exploited.
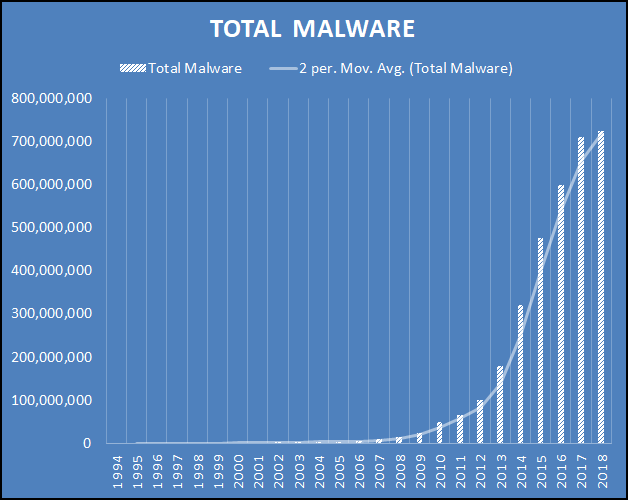
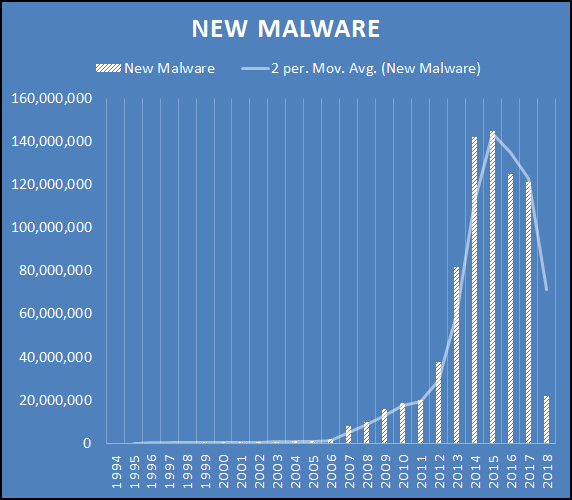
Growth
Although we are still seeing Total Malware grow each year, new malware has plummeted.
(data from AV-TEST)
Not only are we facing the same or similar ransomware, those like WannaCry can most likely no longer be decrypted by the ransomware authors. They have become mainly a destructive tool.
So how can you protect yourself?
One of the most often touted ways is with frequent, tested backups. This works well as does the idea I promoted in my course of keeping an up to date clone of your boot drive, so you will be down for the amount of time it takes to turn off your system, remove the old drive, and put the new one in. Probably 15 minutes. I haven't timed it, but have done it several times and it works like a charm.
Another great way was delineated in this article. Use something like Horizon Datasys' Reboot Restore RX freeware to keep an up to date image of your hard drive that only needs a reboot to bring you back to life. I have been using this method for over a month now, and am very satisfied with it (one needs to understand the way it interacts with the SSD trim function though).
These 2 ways are the fastest ways to protect yourself. If you have a little more technical savvy I recommend running in a virtual machine.
In a corporate environment, the easiest way for a corporation to protect its' assets, which include the network, is to implement a Privilege Access Management solution. There are many off the shelf packages that just need a bit of configuration. Some of the more popular ones are from CyberArk, Microsoft (MIM), Centrify, BeyondTrust, Ivanti, CA technologies, Core Security, Lieberman, ManageEngine, OneIdentity, Thycotic, and XTON technologies.
These products implement the principle of least privilege (PoLP), along with application whitelisting. The result is that at the endpoint most local administrative features are removed while making exceptions for known executables. A practice that is known as greylisting. This has been shown to be 100% effective in preventing malware attacks.
Conclusion
What does this mean to you? It seems that ransomware is not going away any time soon. If you have not already done so, you should implement a backup plan and test it. I highly recommend using one of the other software items I mentioned here as well. For files you feel you cannot lose, you should have at least two backups, meaning 2 other than the original, in 2 different places. One of these places should be in a cloud storage server.
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (6)
Commented:
I also think that top notch spam control is essential because a lot of these attacks come from "Look at this" links
Author
Commented:in looking a solutions, the hardest is user education. It also seems to be the least effective. A PAM solution actually addresses that in that the user is no longer able to make the changes necessary to get their computer encrypted. The home user can use the Reboot Restore for Home and MakeMeAdmin (makemeadmin.com) for those times when they need administrative access. Since I was asked to write this as a where are we now compared to a year ago article, I didn't get too much into that.
Commented:
Author
Commented:Thanks for pointing that out. The page editor and i both missed it.
Author
Commented:View More