More than Basic Security on your Windows Computer
Recently Andrew Leniart reposted an article on LinkedIn about basic Windows security. Although the article really only covers very basic security, it got me thinking. Security on Windows computers can be a fairly complicated endeavor. I myself have several (yes several) different layers of security on my work computer.
Although everyone likes a slightly different setup, I thought I would share mine in case anyone finds it beneficial (YMMV). Note that using this setup has kept me from being infected with anything up until this point (knock on fake wood).
Note that I use multi-layered security on all my computers. I discuss the reasoning for this in my article on Multilayered security (Note: in the "How can I protect myself?" section of the article I delineate my own install process. I suggest everyone should have such a process.). Suffice it to say that software that purports to do everything tends to be a jack of all trades and a master of none. So on top of the institution's Network Protection (using internal addressing - NATted IP addresses - and a firewall device), I use a number of applications to address the local security prevention, mitigation, detection and guard aspects of layered security.
Endpoint security solutions generally address the mitigation and detection aspects of security, Prevention is another problem. Although endpoint solutions should prevent anything from affecting your computer, most rely on detecting some activity first, which may be too late. So preventative software is a good idea. Additional software to guard against unwanted changes to your system or installed applications is also necessary, since these can slip by many endpoint solutions.
Your first layer of protection should be a good endpoint solution. This will catch most of the malware traffic that tries to infect your computer.
Symantec Endpoint Protection
Our institution requires that we run Symantec Endpoint Protection on all endpoints. Since SEP has to be on the device, let's talk about that first. Symantec Endpoint Protection has evolved over the years from a very resource hungry application up to and including version 11, to a slightly less resource hungry application since then. SEP does a fairly good job of mitigating known malware and using heuristics to determine what activity might be malware. Their Insight and SONAR also "analyze the reputation and characteristics of suspicious files to determine if they pose a danger." SEP purports to do much more. Although, IMHO, not the best piece of anti malware software out there, it is pretty good. I have spoken a number of times to the engineers at Symantec. The gentlemen I spoke to were CISSPs and had a deep understanding of computer security/cyber security. I believe this company is going in the right direction. The screen below is what shows up when you ask the SEP agent to open up.
Now that you have installed an endpoint solution, which should be your first step after booting up any system, you will want to protect yourself from malware changing things like your homepage, registry or your hosts file. A good program to do this is WinPatrol Plus. It is important that you take this step as well since it will help with the guard layer of your security. You may also wish to install an alternate hosts file, which you can download from this website. Once you have installed an alternate hosts file, I recommend installing Winpatrol Plus to prevent any changes to your registry, hosts file, homepage, etc that you don't initiate.
WinPatrol +
I purchased WinPatrol Plus some time ago when it was on sale for $0.99 and have never looked back. I have renewed by subscription to a lifetime one, because I like the software so much. You tell it which directories or files to monitor for changes/adverse activity, lock out changes, change boot order of programs using delayed boot (now built into windows) among other things. Like some of the best products, WinPatrol Plus is not only a set it and forget it type program, it also learns.
Another Program that will help protect/guard your computer against malware is an anti-ransomware application. This is specific to detecting ransomware activity, generally these programs look for indicators of compromise (IOCs). I use WAR, which I settled on after testing many different anti-ransomware programs. With this application you can set which programs/directories are okay, or just let it learn while you are using it.
WinPatrol AntiRansomware (WAR)
This piece of software came out a couple of years ago, I initially saw it when I was doing a review of various anti-ransomware software. WAR runs in the background with a system tray icon. WAR is fairly good at detecting suspicious activity. Both WAR and Winpatrol Plus learn when you install new software (in some cases you may need to start an installer twice in order to allow it to run). For ransomware solutions, please refer to my article on ransomware prevention.
For mitigating, guarding and preventing virtually everything else, I use HitmanPro.Alert. This is an excellent program that not only learns how you use your computer, but protects each program from malware with individual profiles. It can encrypt your keystrokes to prevent keyloggers and monitor you processes for malware. Sophos's InterceptX incorporates HMP.A functionality.
HitmanPro.Alert (from Sophos)
This is probably the best piece of software I have tried. It learns and protects you while browsing the web (no matter what browser you use). I have only encountered a false positive once and support was very responsive. HMP.A is very comprehensive and neither intrusive nor resource hungry. It has many ways in which it keeps malware off your computer, including, but not limited to , input encryption, USB vaccination, crypto-guard, credential theft mitigation, process protection, webcam notifier (protects webcam from being turned on silently), exploit mitigation, and browsing protection.
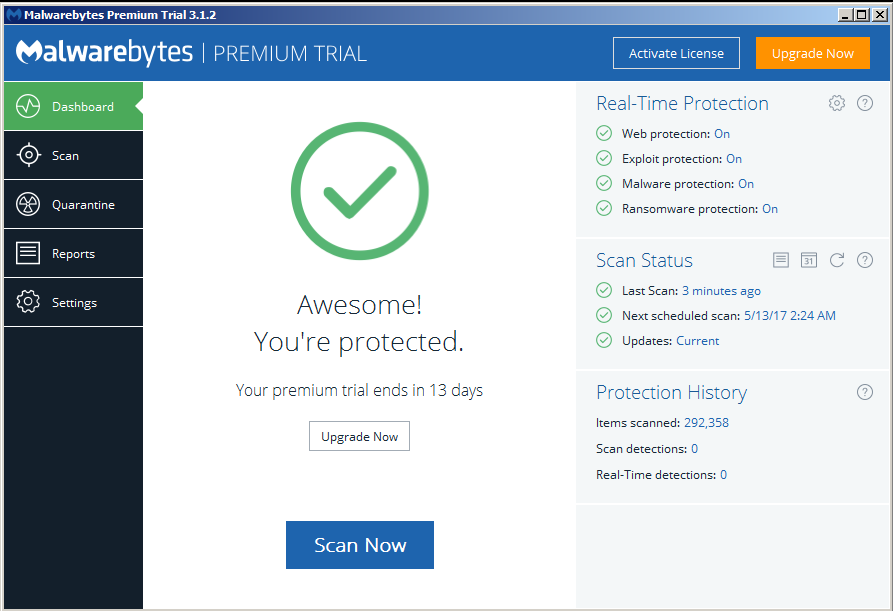
When there is a chance that there may be an infection, I use Roguekiller to "kill" all known malware processes and then, without rebooting, run a scan with MalwareBytes Antimalware (MBAM) - removing anything it detects. The combination of all of these makes a machine very secure.
Malwarebytes Antimalware
If you run this on a windows box alongside any other product, make sure that this is the only one doing on-access scanning, otherwise there will be a conflict - again see the article on Multilayered security for further detail. Note that the last time I ran MBAM, I had to turn on Root kit protection because the default was off. MBAM Pro along with Roguekiller (MBAM Pro gets removed by GPO) are two of the most frequently used programs that don't continually run on my computer.
This program locks a computer using an external device such as a USB stick. Always a good idea to prevent the average user from accessing your computer (if a person knowledgeable about windows and security has physical access to a computer, they can defeat any security). Register any USB stick with the predator preferences and the program will check every 30 seconds to see if it is plugged in. If Predator does not detect a USB with the proper file on it, the program will lock the computer (with 20 seconds to put in a password to bypass the lockdown). Any number of USB sticks can be registered with the program so that any one of them will effectively prevent the computer from locking.
The biggest drawback is that the program will keep popping up this dialog with a warning tone when you enter the password instead of registering a USB stick.
Not on any particular schedule, I run Belarc Security Advisor, which scans my computer and finds if there are security problems (up until windows 7 it gave a security score), including a basic audit of your computer, virus protection scanning, missing updates, mapped drives, users, printers, displays, etc. This tool gives you an excellent overview of your computer. It generates a report in your default browser like the one below.
It is a good idea to run this every so often to see where you stand.
Why go to all this trouble?
You could just install an endpoint solution and be done with it, but that would not completely protect you. No matter what you install you will never be "completely" protected, but these pieces of software will get you close. Don't forget to provide additional protection by creating, using and testing a backup routine that creates two different types of backups in two different locations.
I still have trouble trusting that everything will go perfectly, so I also use a piece of software that restores my system to a predefined image every time I reboot. The software is called Reboot Restore RX (see this article on EE).
Conclusion
One should use several pieces of software to properly protect your computer. Which ones you use are up to you. I have settled on the ones mentioned here after trying various different applications. Beware of programs that use a lot of resources (EMET is an excellent program, but unless properly configured, it will slow down your computer considerably). You can get the applications listed above at the following links:
- Symantec Endpoint Protection
- WinPatrol Plus
- WinPatrol AntiRansom (WAR)
- HitmanPro.Alert 3
- MalwareBytes AntiMalware
- RogueKiller
- Predator
- Alternate Hosts File
- Belarc Security Advisor
- Reboot Restore RX
Thank you for reading my article, please leave valuable feedback. If you liked this article and would like to see more, please click the thumbs up icon below.
I look forward to hearing from you. - Tom - twitter @cyberdad
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.



Comments (0)