Introduction
Ransomware is a malicious software that encrypts victims data and makes it unusable until the victim pays the attacker in Bitcoin. Unfortunately, decryption of data is never guaranteed and one should never forget that they are dealing with criminals, who most time, don't really care about restoring your encrypted files. What they are mainly interested in is extracting as much money out of you as they can.
About Ransomware and Cryptography Payments
Ransomware uses cryptography technology. Attackers decrypt files only if the victims pays a specified bitcoin amount within a certain period of time, but as already mentioned, there is never any guarantee that your files will be restored, even if you pay the ransom!
Usually, decryption keys are removed from the victims' system. If a victim is unable to pay the ransom amount demanded within a specified period, then the decryption key is claimed to be deleted from the attacker's server which makes the victim's system unusable unless a decryption rescue package is developed by reputable Anti-Malware companies around the world.
Types of Ransomware
There are different variants of Ransomware found such as wannacry, notpetya, samsam etc,. In the year 2017 the world had a major hit of ransomware all over the globe by the "wannacry" ransomware. It had a huge impact on NHS hospitals which lead to major interruptions and functionality got stopped until the data was recovered. Still nobody can assure that an attacker will send you the decryption key once they are paid. It’s just because “nobody trusts these "criminals and thieves”.
How does ransomware work?
Step 1: Ransomware comes in the form of an email with a malware attachment or website link. Once the user clicks the link, the file gets downloaded from the control server and inspects the victim's system for flaws in the operating system such as missing patches, software vulnerabilities etc.
Step 2: Once the user executes the malicious file, the software talks with the Command and Control center and downloads the encryption code. From this point of time, the script will be executed, which starts the encryption process including some system files. All the files will be renamed to some different extensions. According to the variant of ransomware. For example, for wannacry, it will be file.wannacry. For locky ransomware it is filename.locky
Thus the process continues. There are literally dozens of examples and variants.
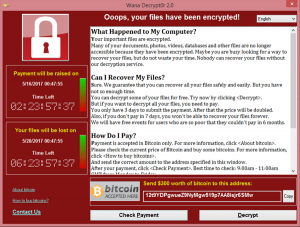
Step 3: Once the encryption process completes, the attacker will place his warning banner with a bitcoin address and amount for payment. And he will start the timer as well. Below shows the sample warning banner of the wannacry ransomware. The attacker waits for the payment until the timer stops. Later the timer stops and the decryption key is removed from the attacker's server's database list. Each user has their own unique ID to be used at the time of payment.
After the encryption attacker will remove decryption key and the traces of attack originated and how it came inside.
Conclusion
None of us can assure you that your data will be safe or recoverable even after you pay the requested amount to the attacker. In fact, the best policy is NOT to pay, learn from such an unfortunate experience and increase your system's defenses.
Employ the use of a reputable anti-virus and keep your Operating System security up to date with patches. Also, employ the use of an offline (cloud) backup system that is updated with incremental backups at least once a day. Don't just rely on backing up to a local NAS drive either, because if hit with ransomware, all of your backup files will likely be encrypted as well because nearly all Ransomware strains are network aware.
Finally, avoid paying to recover your files unless they all mission critical to you or your business and you have no other choice! Remember that at the end of the day, you are rewarding the criminal who did this to you in the first place and encouraging him to keep doing it to you as well as to others. If no one ever paid the criminals to recover files after a ransomware attack, then these attacks would stop!
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (1)
Commented:
Ransomware attacks are becoming problematic for both individuals and businesses of all sizes.
The best and the most important mitigation techniques is to maintain secure backups and educate your employees.
Ways to Address Ransomware Attacks in Today’s Security Landscape:
https://www.lepide.com/blog/nine-ways-to-address-ransomware-attacks-in-todays-security-landscape/
Simple things you can do to protect against ransomware attacks:
http://expert-advice.org/security/ways-to-protect-yourself-from-ransomware-attack/