What is MD5 Hashing?
MD5 (Message Digest Algorithm) is the one method which produces a “fingerprint”. This is useful because you can compare and store these small hashes very easily rather than the entire original sequences.
MD5 is one of many hashing algorithms, it was developed by Ronald Rivest in 1991. It is an updated version of MD5.
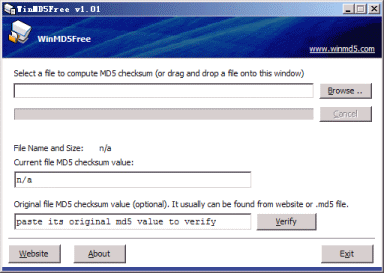
WinMD5Free is a small (Freeware) utility view the MD5 hash value for the files, MD5 has been used in a wide variety of security applications like blocking hash values in Antivirus solutions or in Application Control solutions etc.
MD5 has been used to detect malware for a long time, this is been an old method but still, this utility is useful and used to view the hash value of the application as nowadays various network-based appliances are available which have this functionality to protect the has values.
This utility supports almost all Windows platforms including Microsoft Windows XP, 2003, Vista and Windows 7, 10.
You can download this utility from here
Hope you found this useful.
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (1)
Commented:
Further reading:
https://www.zdnet.com/article/ssl-broken-hackers-create-rogue-ca-certificate-using-md5-collisions/
https://blog.avira.com/md5-the-broken-algorithm/