Pre Server 2016 Group Membership Expiration Tool
But what if you want this functionality but you haven't upgraded yet?
Since I have many clients that cannot yet leverage this new feature, I have developed a custom tool.
Introduction
Group membership expiration gives the ability to add a user to a group with the notion of a membership expiration.
This means you can add a user to a group and the user will automatically be removed from the group when the configure timespan has passed.
Unfortunately, some environments do not yet run at an Active Directory 2016 functional level.
For those, I developed the GroupMembershipExpiration tool.
Setup
1) Download the GroupMembershipExpiration tool and extract its contents to a folder on a computer that you are planning to install this tool on.
(I recommend extracting to C:\Program Files\GroupMembershipExpiration)
2) Run Configurator.exe (Configurator Editor).
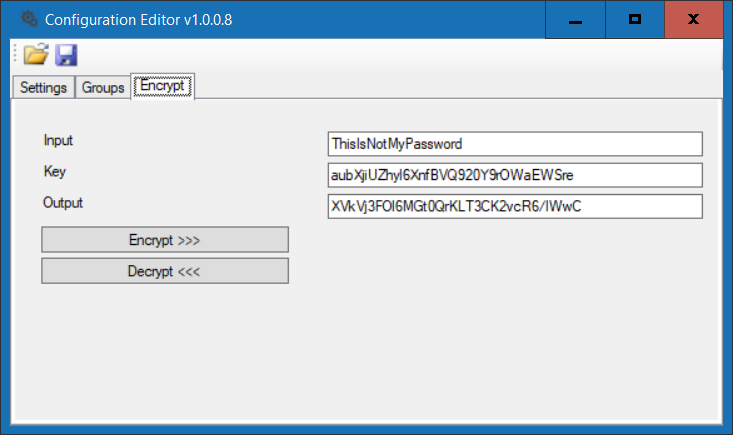
a) On the Encrypt tab, enter the password for the account that will be performing the cleanup task. Encrypt it with key aubXjiUZhyl6XnfBVQ920Y9rOWaEWSre and record the encrypted password.
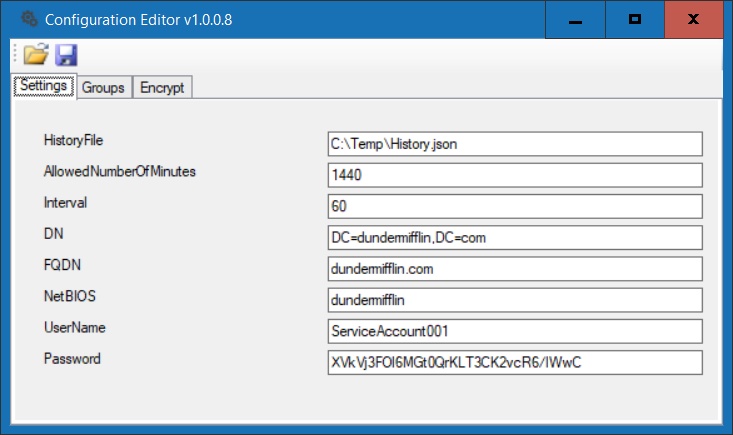
b) On the Settings tab, enter the distinguished name, fully qualified domain name, NetBIOS, and username and the encrypted password recorded in step 2a.
Specify a location where the tool can save a history file, the interval in seconds the task should be performed and the allowed number of minutes a member may be part of a group.
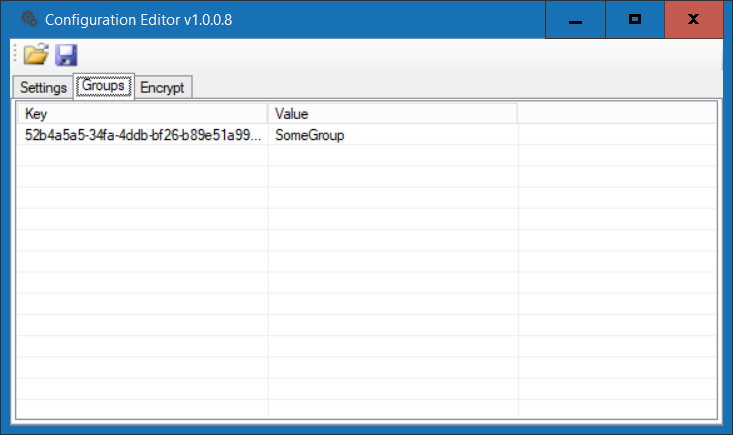
c) On the Groups tab, specify the group name that tool should manage the members for (+ or INS to add, - or DEL to delete, Enter or double-click to edit)
d) Although you can just run the tool by executing GroupMembershipExpiration.WindowsService.exe, I recommend you install it as a service by running GroupMembershipExpiration.WindowsService.exe INSTALL from an elevated command prompt. You may need to start the service manually the first time
The Code
private void ProcessGroup(string groupName)
{
List historicalyGroupMembers = new List();
// Read previous history file if it exists
if (File.Exists(_historyFile))
{
historicalyGroupMembers = Newtonsoft.Json.JsonConvert.DeserializeObject>(File.ReadAllText(_historyFile));
}
// Get current members of group
List genericGroupMembers = new List();
genericGroupMembers = ActiveDirectory.GenericGetGroupMembers(_domainInfo, groupName);
List groupMembers = new List();
// Compare histrory file with current members
foreach (var genericGroupMember in genericGroupMembers)
{
Models.GroupMember historicalyGroupMember = historicalyGroupMembers.Where(g => g.DistinguishedName == genericGroupMember.DistinguishedName).FirstOrDefault();
// If group member not in history, add it with current date and time as FirstDateObserved
if (historicalyGroupMember == null)
{
// Add to history
groupMembers.Add(new Models.GroupMember() { GroupName = genericGroupMember.GroupName, DistinguishedName = genericGroupMember.DistinguishedName, sAMAccountName = genericGroupMember.sAMAccountName, FirstDateObserved = DateTime.Now });
}
else
{
// If group member in history and it is pass the maximum allowed timespan, remove it
if ((DateTime.Now - historicalyGroupMember.FirstDateObserved).TotalMinutes > _allowedNumberOfMinutes)
{
// Remove Group from AD group and group history
groupMembers.Remove(historicalyGroupMember);
ActiveDirectory.GenericRemoveGroupMember(_domainInfo, groupName, genericGroupMember.DistinguishedName);
}
// If group member in history and it is not passed the maximum allowed timespan, ignore it
else
{
// Ignored
groupMembers.Add(historicalyGroupMember);
}
}
}
// Save current members to new history file
File.WriteAllText(_historyFile, Newtonsoft.Json.JsonConvert.SerializeObject(groupMembers));
}Conclusion
There you have it. Essentially everytime the timer triggers in the Windows Service, the process will reference the history file and use it to determine if a member's membership has expired.
I hope you found this tutorial useful. You are encouraged to ask questions, report any bugs or make any other comments about it below.
Note: If you need further "Support" about this topic, please consider using the Ask a Question feature of Experts Exchange. I monitor questions asked and would be pleased to provide any additional support required in questions asked in this manner, along with other EE experts...
Please do not forget to press the "Thumb's Up" button if you think this article was helpful and valuable for EE members.
It also provides me with positive feedback. Thank you!
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (4)
Commented:
I wonder if this takes into account that you, as a group member, get a kerberos ticket that will have a life time of some hours, so that when you are removed from the group, you will still, for some hours, be able to act as group member until the ticket expires. AD 2016 does that automatically (=shortens ticket lifetime accordingly already at the moment of ticket-granting).
Author
Commented:Good point though
Commented:
We would like to use less than 6 minutes, sometimes, for example when we activate a software license, we give the machine internet access for the shortest time possible (working close to the military, here, no direct internet access allowed). And to do so, we use AD groups, that the SQUID proxy works with. We would like to use, say, 1 minute, but we can't do less than 6... :-)
Author
Commented: