Internet of Things: Guidelines to prevent common IoT security risks
Introduction
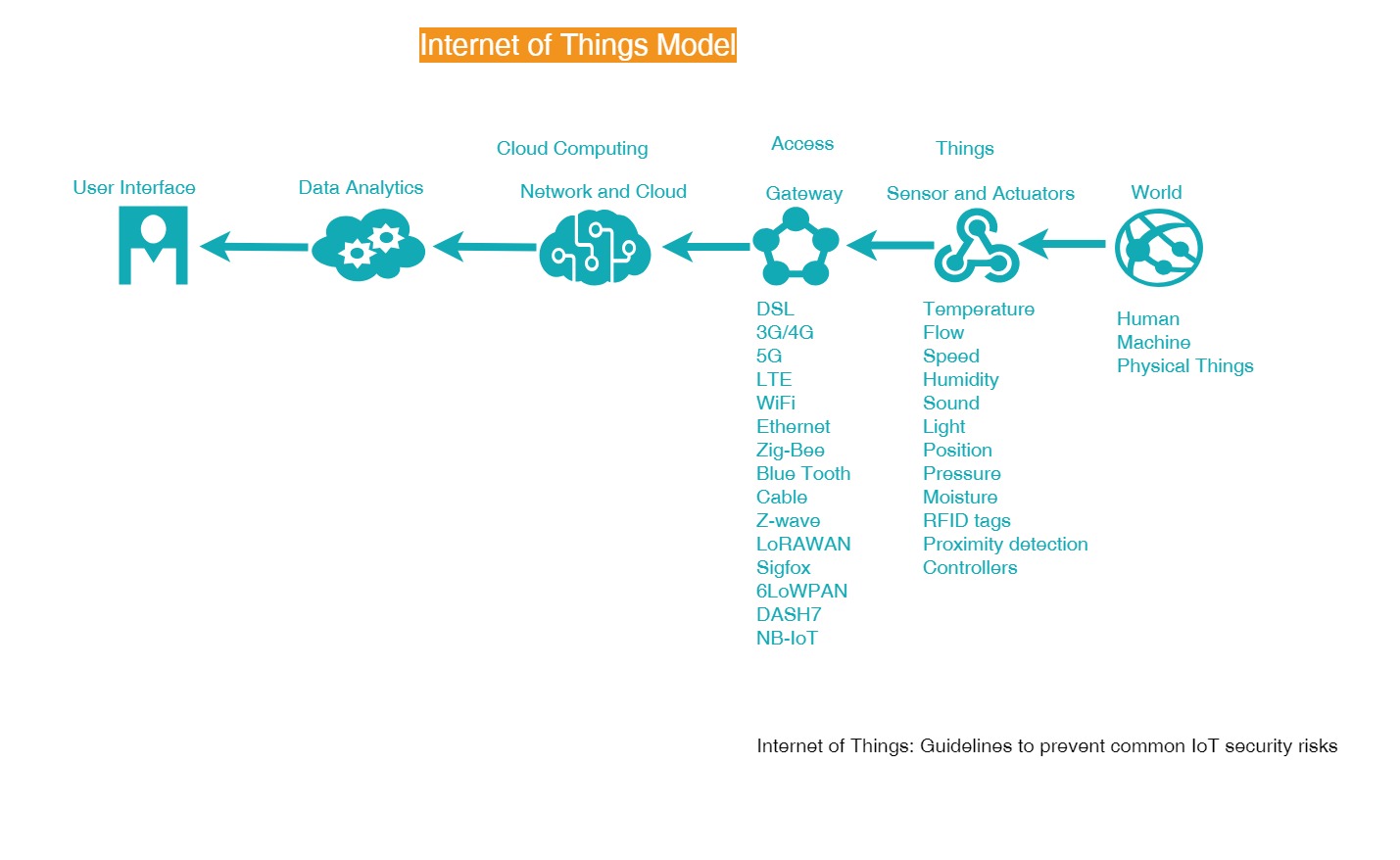
Figure 1
Oxford defines the Internet of Things (IoT) as [1]: “A proposed development of the Internet in which everyday objects have network connectivity, allowing them to send and receive data.” IoT includes everything connected to the Internet which refers to a broad range of devices from industrial meters, personal medical devices, home appliances, CCTV and automobiles etc.
IoT is helping human beings in all the fields like healthcare, tracking system, retail market, parenting, weather and environment, alert system and notifications, etc. It is also changing the lifestyle of human beings, but it comes with all of the security issues which are handled from time to time with change technology.
IoT brings a tremendous amount of complexity since there is so much involved with IoT; you have mobile devices, wireless, embedded, web, network, cloud and data analytics (figure 1). There are tons and tons of data that can be used through all these IoT devices. For example, a smart electric power meter basically does what power meters have always done, it tracks the customer's use of electricity, the base capability is enhanced with sensors that collect data about the environment and how users interact with it.
The risk is real with IoT, and it is growing! According to a recent Symantec Internet Security Threat Report, there will be around 200 billion connected devices by 2020 [2], however, there is a downside that is hard to ignore. Some IoT vendors have implemented poor security measures, such as weak encryption protocols, which open the door for attackers to compromise these connected devices.
OWASP
OWASP (Open Web Application Security Project) has specialized resources, including in-depth documentation on various attack types and security techniques for Web applications, Mobile app and Internet of Things (IoT).
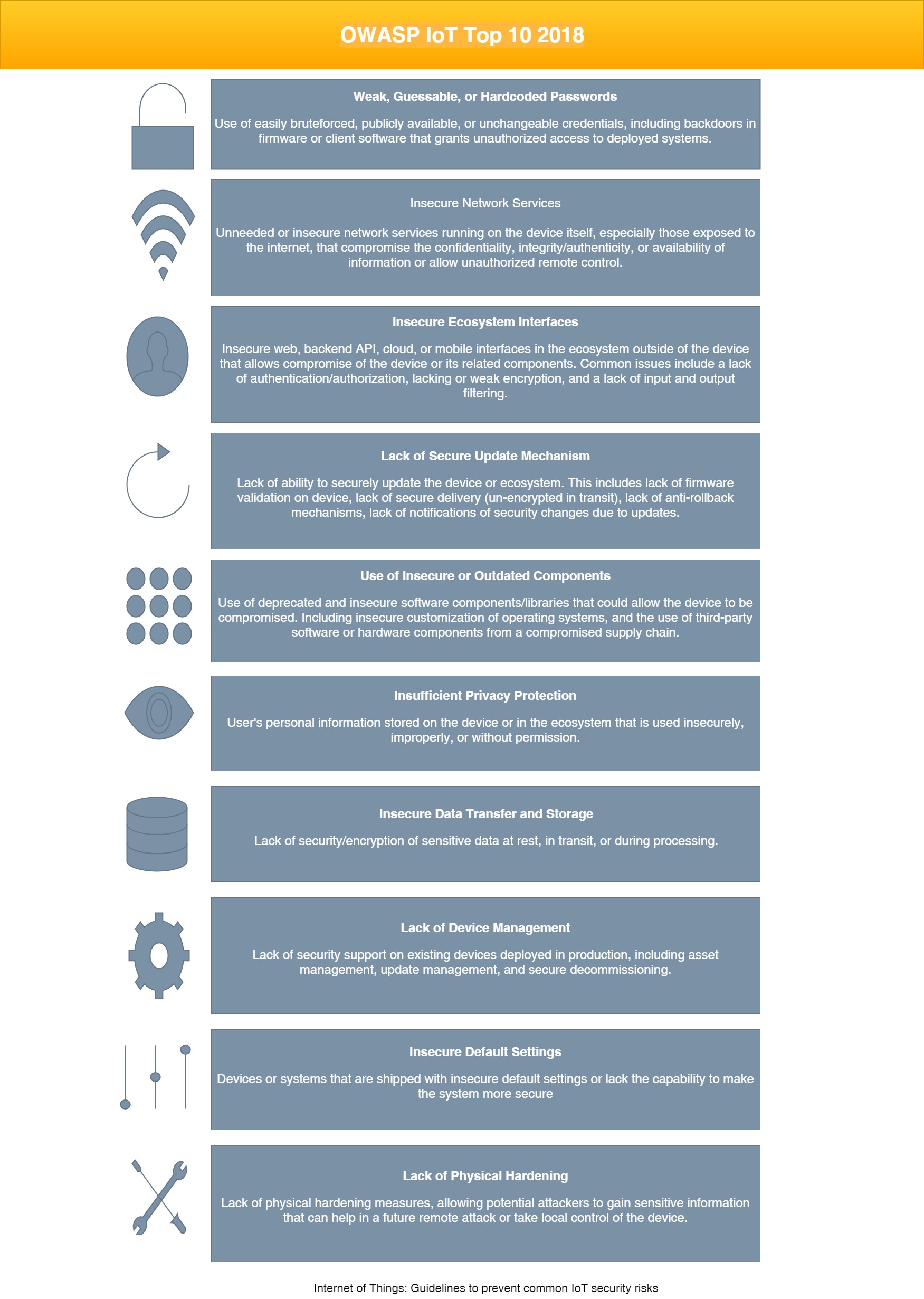
The OWASP IoT Project is currently reviewing the Top Ten list for 2018 (figure 2). The official launch date is December 2018. The new IoT Top Ten 2018 is a collection of experienced IoT practitioners, review of the previous list, parsing of tons of related projects, internal team discussion, and feedback from the community [3].
Risks
Figure 3
OWASP defines that most common data security vulnerabilities in IoT are mainly due to (figure 3):
• Poorly secured web applications (security concerns with their user interfaces).
• Weak user and device authentication.
• Unsecured communication channels (use of un-encrypted network services).
• Uncertain per-configurations.
• Vulnerabilities in the hardware and software.
The fact that there are so many devices each with the processing and network capability makes them a great potential platform for a box net that can be used to launch other attacks; in fact this has already happened in 2016 when IoT devices were used to take down Twitter Reddit Netflix and many other services [4,5,6].
Due to a security flaw IoT (figure 3), attackers were able to do:
- Stuxnet
- Mirai botnet
- Cold in Finland
- Brickerbot
- The botnet barrage
- Reaper
Such hacking attempts and IoT security issues across global IoT facilities have resulted in privacy violation, security breaches, loss of business, crippling of infrastructure and in some cases even health and medical emergencies. Unfortunately, IoT vendors and developers are not thinking properly enough about the security of the systems that they are building. Also, consumers usually pay little attention to the IT security of IoT devices.
Besides standards and know-how are lacking, which can be explained among other things by the fact that the security topic in the IoT is still relatively new despite the above-mentioned attacks. IoT manufacturer must perform controls to detect these threats and data protection weaknesses, disable IoT devices once an attack spreads and commit to communicating on the risks.
Guidelines
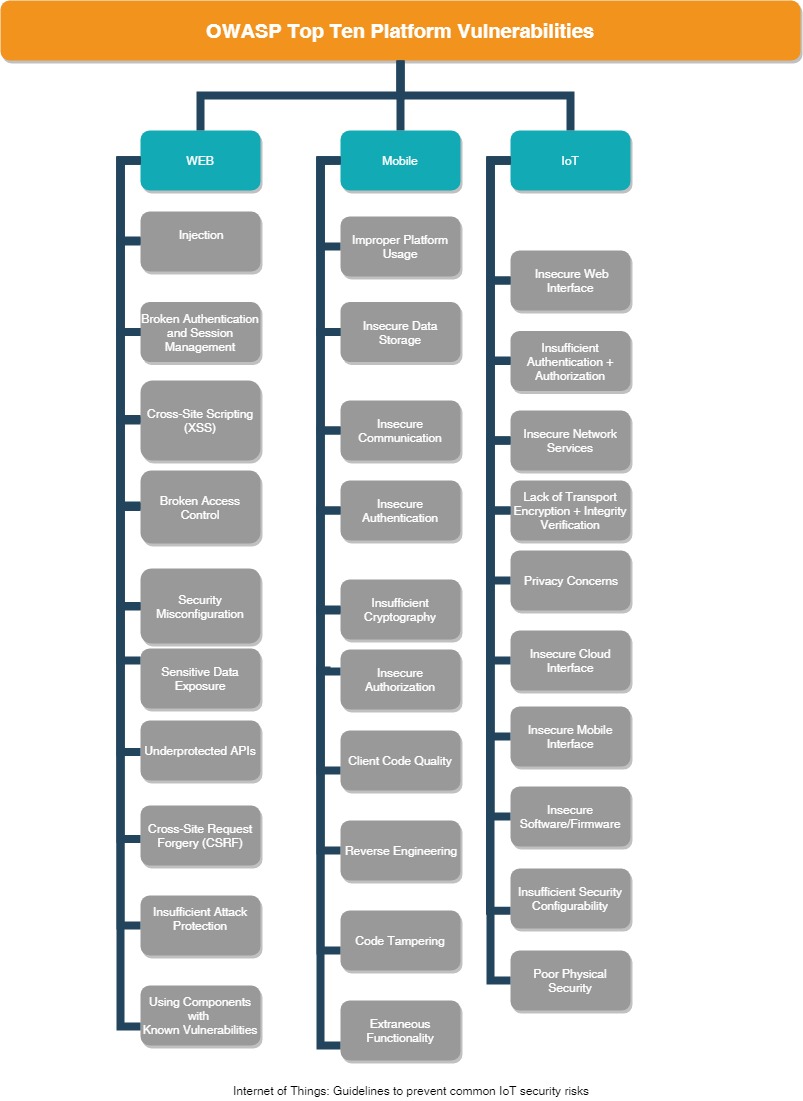
Figure 4
Vendors should focus on how the IoT is structured to identify specific locations where the IoT design is vulnerable or flawed, thus, in need of protection or improvement, in order to provide three aspects of security:
• Confidentiality—Keep information and communications private and protect them from unauthorized access.
• Integrity—Keep information accurate, without error, and without unauthorized modification.
• Availability—Ensure that systems operate continuously and that authorized users can access the data that they need.
Therefore, every manufacturer of IoT systems is challenged, all phases of the development process up to operate the equipment with appropriate safety measures to complete. Vendors should follow the above guidelines (figure 4) to prevent common IoT security risks identified by OWASP [7,8,9].
Few steps should be taken in consideration from manufacturer and consumer side to secure IoT:
- Since IoT devices are essentially web host, there are the typical protections you would provide to any web application or client. Make sure any web interfaces are secured through good authentication.
- Make sure you protect web interfaces problem vulnerabilities like cross-site scripting request forgeries and so forth provide strong authentication and authorization controls and secure your network devices and services.
- The IoT systems often provide cloud connectors, ensure that any cloud-based web interface requires strong passwords; web interfaces should have an account lockout mechanism and multi-factor authentication.
- The devices themselves need to be secure, as much as possible the devices should be physically secured minimizing physical connections protecting the firmware from tampering and so forth.
- Communication to and from the device should require authentication and authorization and should be encrypted.
- It is important to plan for security before IoT implementation, so design IoT systems to be agile.
- It should be possible to update the firmware through secure authorized channels so vulnerabilities can be patched in the future.
Conclusion
No doubt that IoT will improve customer experience, where connected objects think on our behalf, automate boring activities, make our lives better, more comfortable and healthier which means access to more and more information and control devices remotely.
However; the data is the most important part, without sufficient data security and data protection, the IoT will not be successful in the long run, only if both are guaranteed by enforcing privacy policies, using secure communication and encrypted data storage should consumers be willing to entrust their data to the network and openly accompany the advancing digitization.
References
[1] https://en.oxforddictionaries.com/definition/internet_of_things
[3] https://danielmiessler.com/blog/preparing-to-release-the-owasp-iot-top-10-2018/
[4] https://www.iotforall.com/5-worst-iot-hacking-vulnerabilities/
[5] https://www.zdnet.com/article/5-nightmarish-attacks-that-show-the-risks-of-iot-security/
[6] https://www.embitel.com/blog/embedded-blog/security-challenges-faced-by-iot-based-industries
[7] https://www.owasp.org/index.php/Category:OWASP_Top_Ten_Project
[8] https://www.owasp.org/index.php/Mobile_Top_10_2016-Top_10
[9] https://www.owasp.org/images/7/71/Internet_of_Things_Top_Ten_2014-OWASP.pdf
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (0)