Browse All Articles > SmartCard 2-factor domain authentication for free!
This article is about my concept of combining TPM Virtual SmartCards with standard USB sticks to achieve true 2-factor windows domain authentication at no additional cost. If you feel like trying it for yourself, you will need a domain certification authority as well as a computer with a TPM chip.
Introduction
Passwordless authentication is a common IT goal nowadays. However, getting there is not a straight forward process, and it comes with new challenges, costs and new administrative headaches.
I recently began to evaluate what benefits our administrative team might get out of SmartCards when used for windows domain logon. Despite being available for a long time, the option to use SmartCards seems to be largely overlooked and possibly underestimated, it seems. In short: the logon secret is stored encrypted on a SmartCard and will only be released after you enter a PIN on your keyboard or your SmartCard reading device. That SmartCard is said to be tamper-proof, you cannot copy the Card nor extract its secrets without the PIN. So you would be only allowed to log in if you have the SmartCard and know the PIN, which makes it a form of 2-factor authentication.
In a book about Multifactor authentication, a former Microsoft employee and security expert revealed Microsoft themselves are internally relying on SmartCards heavily. They will know what they are doing, right, so why not do the same?
How I started
After ordering test devices (a SmartCard- and SC-Reader Combo-device), and reading a simple how-to by the manufacturer, I was ready to go in just half an hour. No more relying on a complicated password alone, I could now log in to my domain using a SmartCard and a PIN, which looks like having more security and even more comfort at the same time. The costs were relatively small (50 US$ per device) and I wouldn't even need additional software, nothing in need of constant updating, no fees, no strings attached. Wow!
At that point, I was almost convinced that it could get no better. But during the next weeks of testing, some usage related research made me aware of the existence of TPM Virtual SmartCards. Until then, I had thought that virtual SmartCards were virtual devices meant to be used only with virtual machines but not with physical machines. I was wrong. Virtual SmartCards store your logon secrets on your computer in an encrypted form by the help of a TPM chip. The TPM chip will require a PIN right at the windows logon mask to release the stored secret that allows you to logon, just as a physical SmartCard reader would.
If you, too, are unaware of these, I will leave it up to you to read the documentation, but I suggest to read it later on since it will take you quite a while. Just that much: a virtual SmartCard (let's call it "VSC" from here) is almost as good as a real SmartCard but it comes at absolutely no cost!
There are two obvious differences to real hardware SmartCards:
So is 2-factor-authentication possible with these VSCs?
Microsoft writes in its TPM VSC documentation paper:
Aha... So the user's computer itself becomes the 2nd factor? You know, you have to guard both factors...Is the machine attended by the user at all time while it's running? You can surely note guarantee that, so Microsoft's statement is debatable, to say the least.
So this finally gets us rolling: this article will not only praise VSCs, but foremost, I will introduce you to a method that I created to achieve real 2-factor-authentication!
Imagine, you fear bad guys to do shoulder surfing or, using a hidden camera, even film your keyboard while you are entering your VSC PIN. Or maybe they even manage to mount a keylogger device at your keyboard that records your VSC PIN. What then? That means, they will only need to visit your machine while it's running but locked and enter that PIN they harvested and they may logon to your account! Of course, that is something normal SmartCards could prevent from happening since you would not let these crooks get their hands on your SmartCard as well, would you?
But the VSC is always inserted as soon as your computer has booted, and that's the problem!
If an adversary finds out your PIN, he will be in.
What can we do about that?
I speculated that this VSC will not be relying on the TPM alone but must have some file associated to it that gets read during authentication... and that proved to be right. There is a hidden folder in
C:\Windows\ServiceProfiles\LocalService\AppData\Local\Microsoft\Windows\SmartCard\Tpm
that is associated with my VSC.
So my idea was: if this folder wouldn't exist, the VSC should no longer be functional - and that proved to be true as well: I could rename that folder and was no longer able to use my VSC until I renamed it back. And that's the big idea: we intentionally rename that folder to disable the VSC while we are away from our machine so that only we may use it and no one else.
So my next idea was to tie this renaming process to the presence/absence of a USB stick.
If I insert my stick, the VSC should be functional.
If I remove my stick, the VSC should be dysfunctional.
Removing the stick is like unplugging and taking a real SmartCard with you.
Can windows do that? Sure. Windows has a task scheduler that allows you to trigger-start whatever script you like when a USB-Stick is inserted/removed, and that script would simply do that renaming for me, automatically.
So all I needed to do was to find the right event triggers to use for my tasks: Windows logs USB insertions and removals to the (by default disabled) event log section.
Microsoft-Windows-DriverFrameworks-UserMode/Operational
To enable and use that log, launch this line on an elevated command prompt
Now take a USB-Stick and insert it and see what gets logged.
You'll see an event with ID 2003
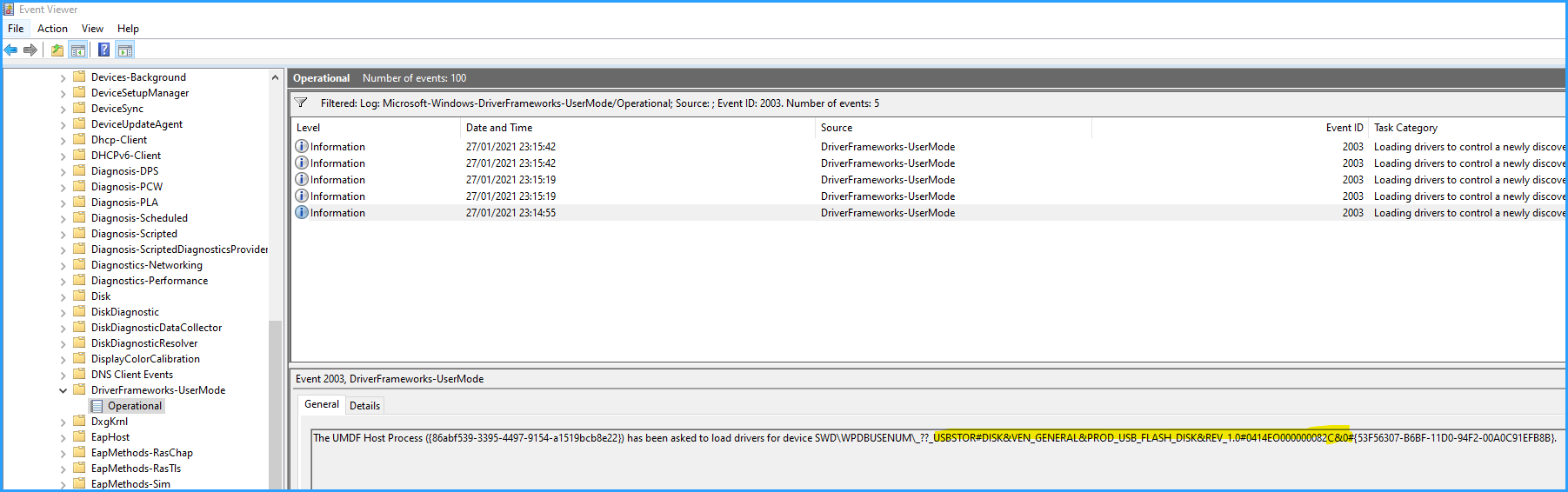
This USB device ID highlighted in yellow will be the essential part in my script to enable the VSC (you need to copy that ID from there).
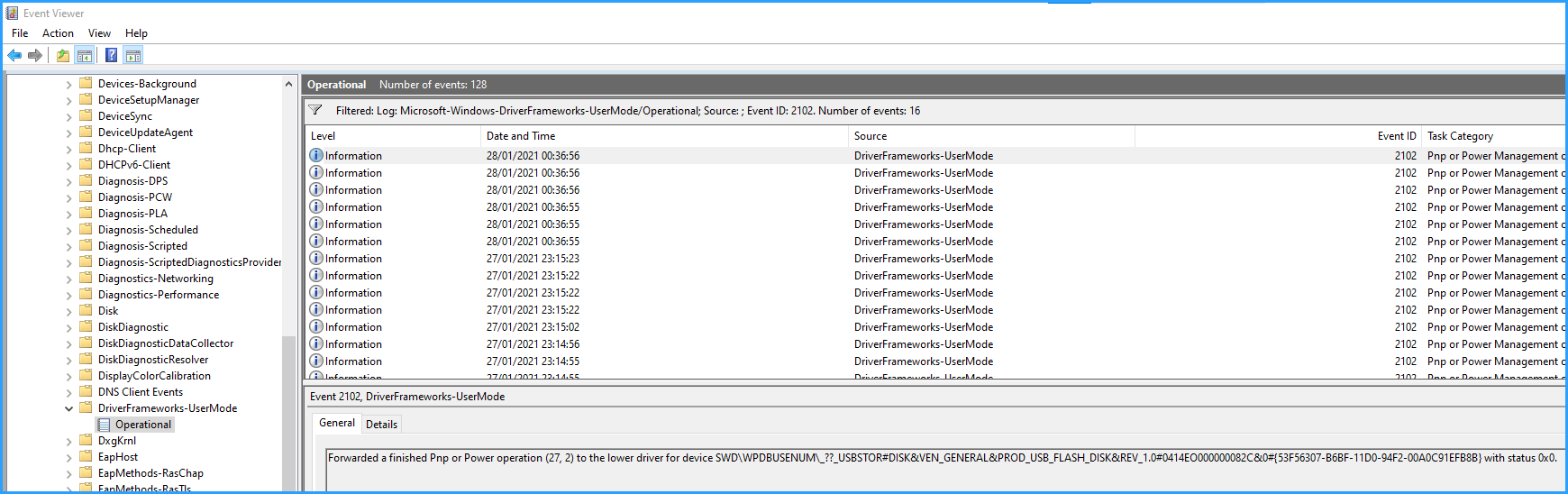
If you remove the stick, event ID 2102 will get logged:
Before we start with setting this up, let me show you how the logon mask looks like, while the VSC is enabled:
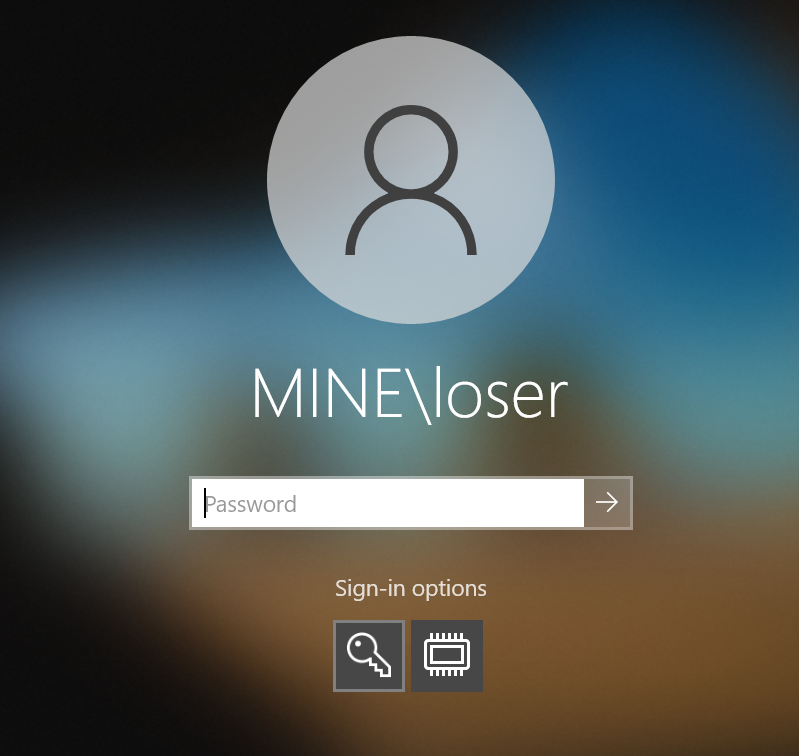 Under "Sign-in options", you'll see a chip-like icon which represents the VSC.
Under "Sign-in options", you'll see a chip-like icon which represents the VSC.
After clicking on it, we are no longer asked for a password but for our VSC PIN: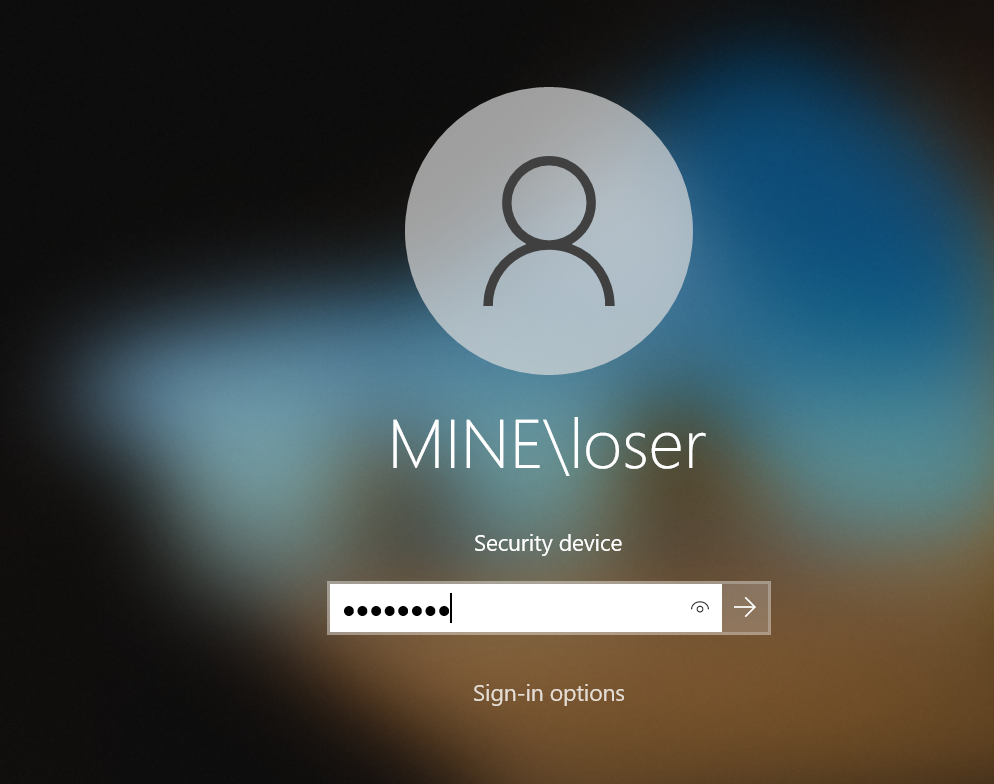
After entering the correct PIN, logon will proceed as usual.
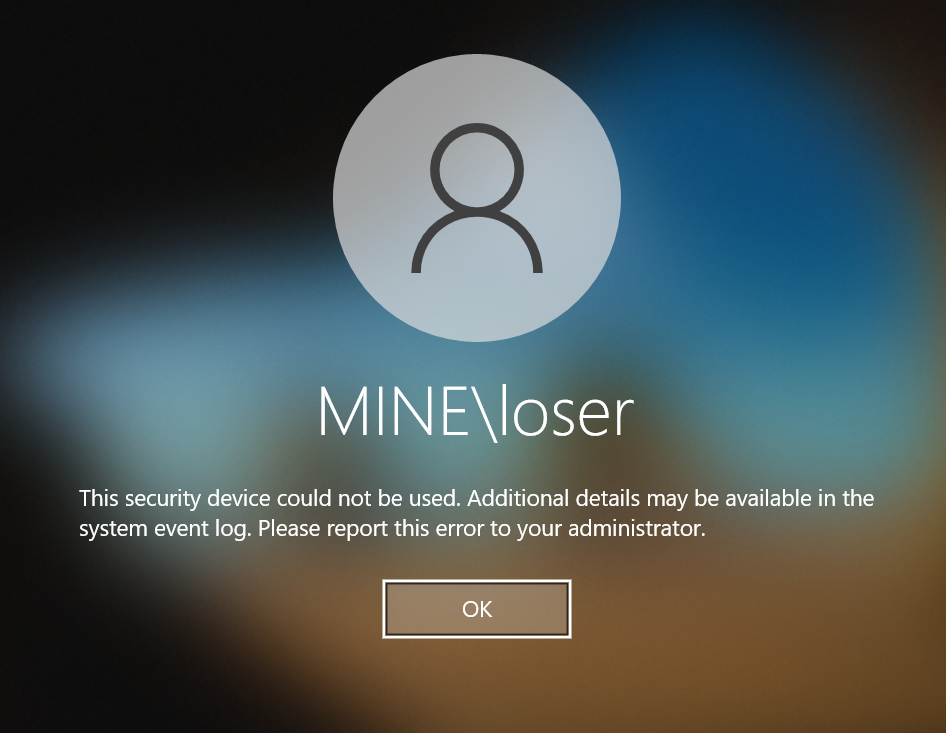
Now with a disabled VSC, the following would be what you (or the attacker, having your PIN) would see after trying to logon. As you can see, the VSC is dysfunctional; the attack is stopped.
Now let's set this up!
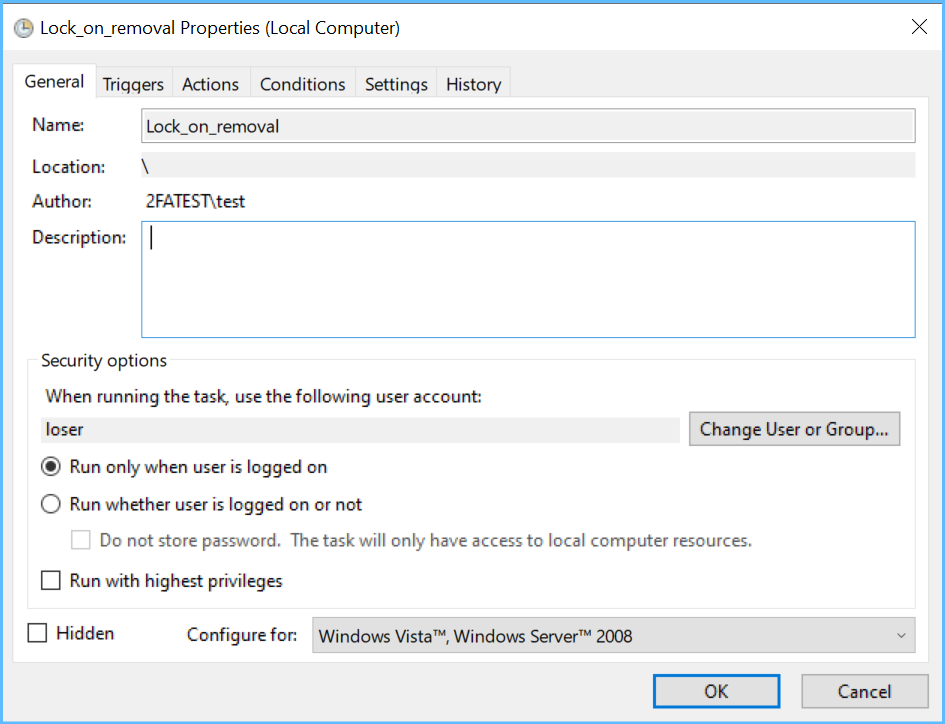
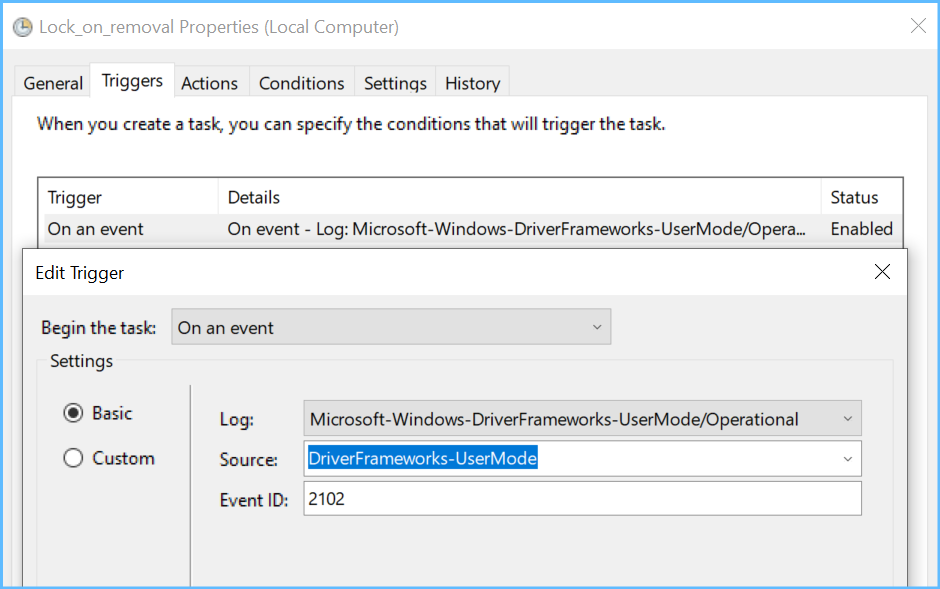
The first step is to create a task that launches when I remove my stick. It serves to lock the screen and at the same time trigger another task to disable the VSC:
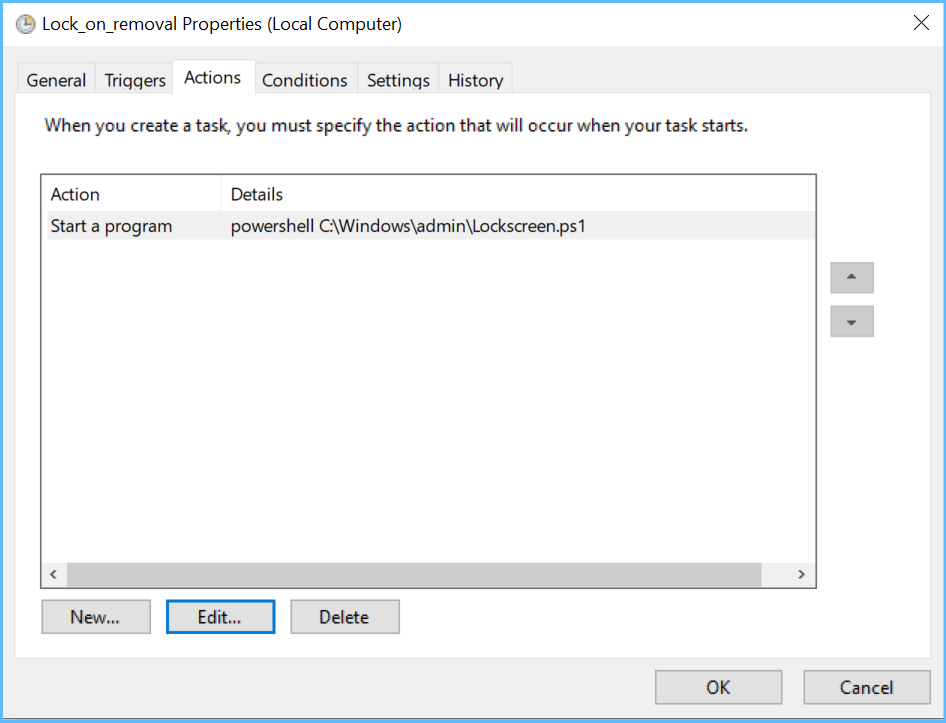
The PowerShell script it launches (c:\windows\admin\Lockscreen.ps1) goes:
Next is the task that disables the VSC:

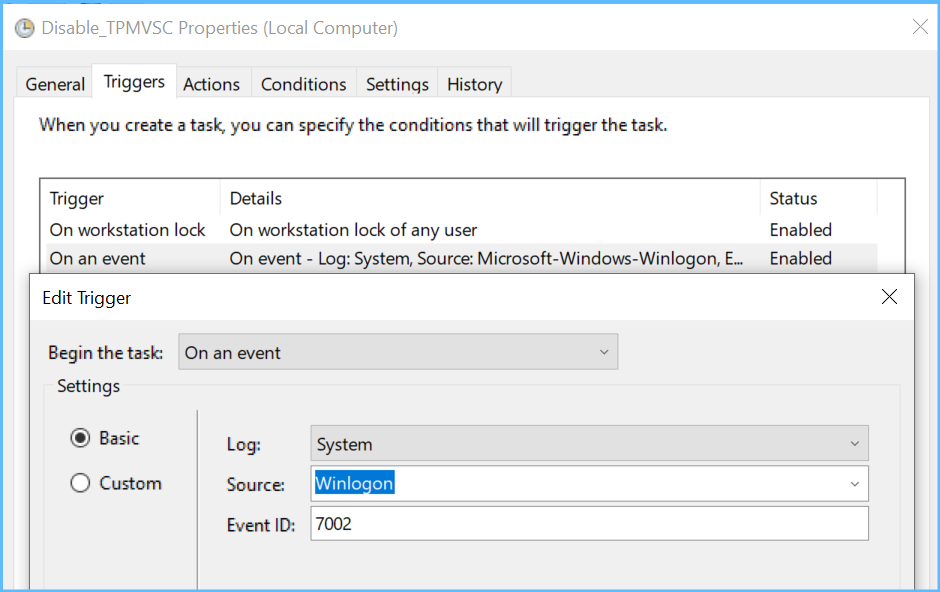 (this task will launch as well when I logoff, that's what the 2nd trigger is for)
(this task will launch as well when I logoff, that's what the 2nd trigger is for)
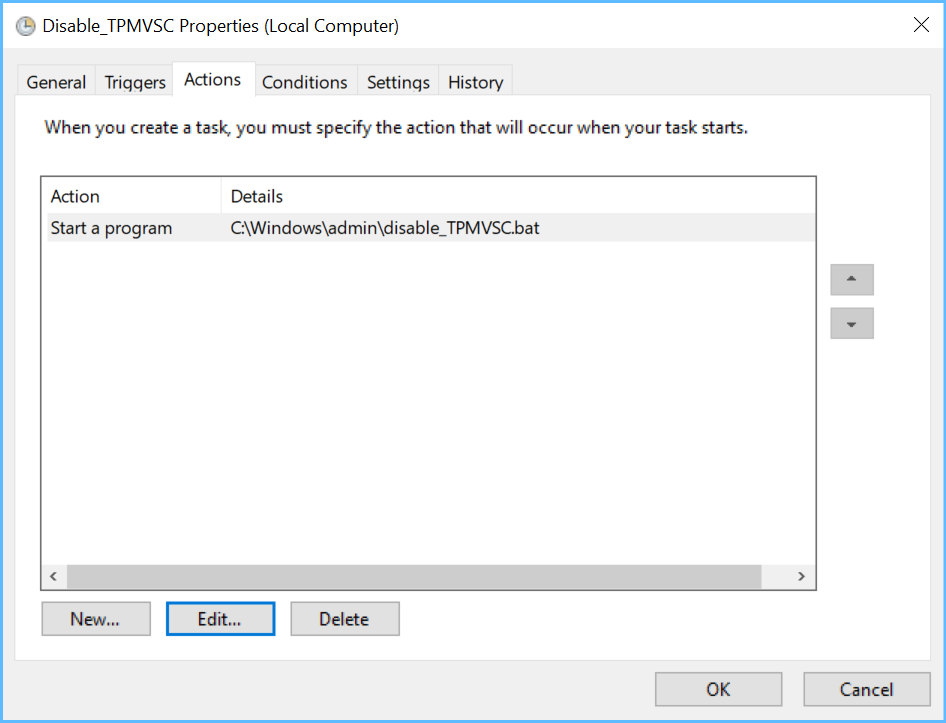
Ok, so what the Disable-task will do in my example is launch a one-liner batch (c:\windows\admin\disable_TPMVSC.bat) which goes
(please note that the folder name in this example needs to be adjusted by you)
And finally, another task, triggered by stick insertion, will rename that folder back to what it was and afterwards restart the VSC reader (the virtual device), so then it becomes available again immediately without a reboot.
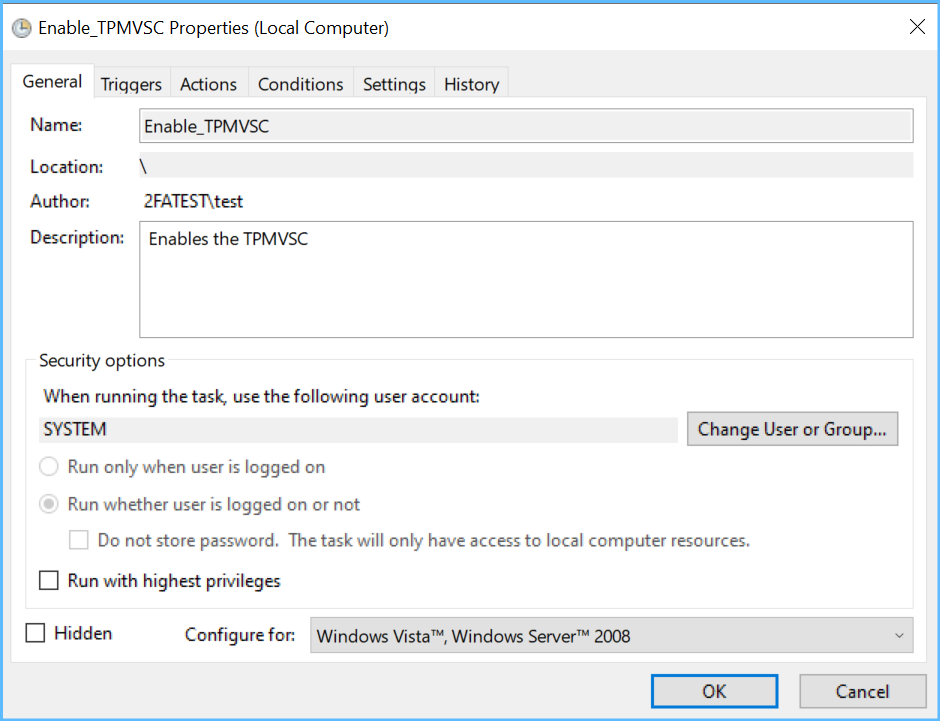
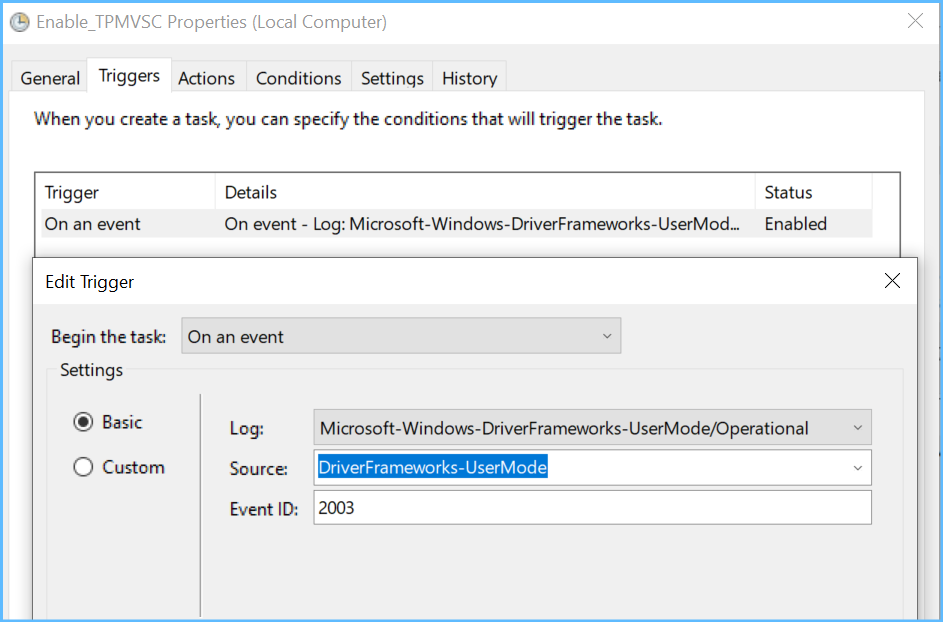

That batch c:\windows\admin\enableTPMVSC.bat goes
Two important notes:
Done! Please note that these scripts should be saved to a location that only admins may modify, so for example to c:\windows\admin\.
By now, you might be eager to try it for yourself. Some requirements are mandatory:
So after successfully trying, I hope you will agree that this is comparable to using a real SmartCard!
In the next section, I will look at the problems that I see with this usage scenario and compare them to those of real SmartCards. These problems are not all grave, but they clearly exist, so let me name them:
At this point, I would like to compare the risks that come with SmartCards to those that come with using ordinary passwords:
SmartCards have the advantage of allowing you to require 2 factors for authentication: something you have (the physical SmartCard or, with VSCs, the stick) and something you know (the PIN). Not having that 2nd factor is not something hackers will easily defeat.
Passwords will work on all machines that you may logon to - but that is not only convenient for you but also positive from a hacker's perspective. Passwords will also allow an attacker to potentially use them from the LAN, or even from the internet, while not having to be on premises.
VSCs will only work on one machine, so once a VSC is compromised, it's still only abusable on a single machine and only if the attacker is able to boot that machine and visit it physically - a VSC can not be used without sitting in front of the machine it is tied to!
Conclusion
VSCs are definitely worth looking into as an alternate way for securely logging on to your domain. The functional differences to real SmartCards are small by default, and my method even enhances them to allow true 2-factor-authentication like with a real SmartCard, but without having to buy anything, nor depend on any software but the OS alone!
But like with many other security technologies, they are not safe by design but instead only when used carefully. So it's up to you to judge and decide whether you or your users are ready for them.
That's all. I hope you have learned something new and I am looking forward to your questions or comments of any kind!
Passwordless authentication is a common IT goal nowadays. However, getting there is not a straight forward process, and it comes with new challenges, costs and new administrative headaches.
I recently began to evaluate what benefits our administrative team might get out of SmartCards when used for windows domain logon. Despite being available for a long time, the option to use SmartCards seems to be largely overlooked and possibly underestimated, it seems. In short: the logon secret is stored encrypted on a SmartCard and will only be released after you enter a PIN on your keyboard or your SmartCard reading device. That SmartCard is said to be tamper-proof, you cannot copy the Card nor extract its secrets without the PIN. So you would be only allowed to log in if you have the SmartCard and know the PIN, which makes it a form of 2-factor authentication.
In a book about Multifactor authentication, a former Microsoft employee and security expert revealed Microsoft themselves are internally relying on SmartCards heavily. They will know what they are doing, right, so why not do the same?
How I started
After ordering test devices (a SmartCard- and SC-Reader Combo-device), and reading a simple how-to by the manufacturer, I was ready to go in just half an hour. No more relying on a complicated password alone, I could now log in to my domain using a SmartCard and a PIN, which looks like having more security and even more comfort at the same time. The costs were relatively small (50 US$ per device) and I wouldn't even need additional software, nothing in need of constant updating, no fees, no strings attached. Wow!
At that point, I was almost convinced that it could get no better. But during the next weeks of testing, some usage related research made me aware of the existence of TPM Virtual SmartCards. Until then, I had thought that virtual SmartCards were virtual devices meant to be used only with virtual machines but not with physical machines. I was wrong. Virtual SmartCards store your logon secrets on your computer in an encrypted form by the help of a TPM chip. The TPM chip will require a PIN right at the windows logon mask to release the stored secret that allows you to logon, just as a physical SmartCard reader would.
If you, too, are unaware of these, I will leave it up to you to read the documentation, but I suggest to read it later on since it will take you quite a while. Just that much: a virtual SmartCard (let's call it "VSC" from here) is almost as good as a real SmartCard but it comes at absolutely no cost!
There are two obvious differences to real hardware SmartCards:
- VSCs are bound to a specific device: each VSC works only in combination with one single device's TPM module. You may, of course, have several VSCs, one for each machine that you use.
- VSCs are always in an "inserted state"; they don't support removal since they are not physically present.
So is 2-factor-authentication possible with these VSCs?
Microsoft writes in its TPM VSC documentation paper:
...two-factor auth is achieved: the user must both have a computer set up with the virtual smart card and know the PIN necessary to use the VSC.
Aha... So the user's computer itself becomes the 2nd factor? You know, you have to guard both factors...Is the machine attended by the user at all time while it's running? You can surely note guarantee that, so Microsoft's statement is debatable, to say the least.
So this finally gets us rolling: this article will not only praise VSCs, but foremost, I will introduce you to a method that I created to achieve real 2-factor-authentication!
Imagine, you fear bad guys to do shoulder surfing or, using a hidden camera, even film your keyboard while you are entering your VSC PIN. Or maybe they even manage to mount a keylogger device at your keyboard that records your VSC PIN. What then? That means, they will only need to visit your machine while it's running but locked and enter that PIN they harvested and they may logon to your account! Of course, that is something normal SmartCards could prevent from happening since you would not let these crooks get their hands on your SmartCard as well, would you?
But the VSC is always inserted as soon as your computer has booted, and that's the problem!
If an adversary finds out your PIN, he will be in.
What can we do about that?
I speculated that this VSC will not be relying on the TPM alone but must have some file associated to it that gets read during authentication... and that proved to be right. There is a hidden folder in
C:\Windows\ServiceProfiles\LocalService\AppData\Local\Microsoft\Windows\SmartCard\Tpm
that is associated with my VSC.
So my idea was: if this folder wouldn't exist, the VSC should no longer be functional - and that proved to be true as well: I could rename that folder and was no longer able to use my VSC until I renamed it back. And that's the big idea: we intentionally rename that folder to disable the VSC while we are away from our machine so that only we may use it and no one else.
So my next idea was to tie this renaming process to the presence/absence of a USB stick.
If I insert my stick, the VSC should be functional.
If I remove my stick, the VSC should be dysfunctional.
Removing the stick is like unplugging and taking a real SmartCard with you.
Can windows do that? Sure. Windows has a task scheduler that allows you to trigger-start whatever script you like when a USB-Stick is inserted/removed, and that script would simply do that renaming for me, automatically.
So all I needed to do was to find the right event triggers to use for my tasks: Windows logs USB insertions and removals to the (by default disabled) event log section.
Microsoft-Windows-DriverFrameworks-UserMode/Operational
To enable and use that log, launch this line on an elevated command prompt
wevtutil sl Microsoft-Windows-DriverFrameworks-UserMode/Operational /e:trueNow take a USB-Stick and insert it and see what gets logged.
You'll see an event with ID 2003

This USB device ID highlighted in yellow will be the essential part in my script to enable the VSC (you need to copy that ID from there).
If you remove the stick, event ID 2102 will get logged:

Before we start with setting this up, let me show you how the logon mask looks like, while the VSC is enabled:
 Under "Sign-in options", you'll see a chip-like icon which represents the VSC.
Under "Sign-in options", you'll see a chip-like icon which represents the VSC.
After clicking on it, we are no longer asked for a password but for our VSC PIN:

After entering the correct PIN, logon will proceed as usual.
Now with a disabled VSC, the following would be what you (or the attacker, having your PIN) would see after trying to logon. As you can see, the VSC is dysfunctional; the attack is stopped.

Now let's set this up!
The first step is to create a task that launches when I remove my stick. It serves to lock the screen and at the same time trigger another task to disable the VSC:



The PowerShell script it launches (c:\windows\admin\Lockscreen.ps1) goes:
$JustNow = (Get-Date).AddSeconds(-5)
$foundstick = Get-WinEvent -FilterHashtable @{LogName='Microsoft-Windows-DriverFrameworks-UserMode/Operational'; ID=2102; starttime=$JustNow}| where message -match 'USBSTOR#DISK&VEN_GENERAL&PROD_USB_FLASH_DISK&REV_1.0#0414EO000000082C&0'
if ($foundstick -ne $null) {rundll32.exe user32.dll,LockWorkStation}Next is the task that disables the VSC:

 (this task will launch as well when I logoff, that's what the 2nd trigger is for)
(this task will launch as well when I logoff, that's what the 2nd trigger is for)

Ok, so what the Disable-task will do in my example is launch a one-liner batch (c:\windows\admin\disable_TPMVSC.bat) which goes
ren C:\Windows\ServiceProfiles\LocalService\AppData\Local\Microsoft\Windows\SmartCard\Tpm\2h264d81-038e-4403-9e86-788ab3d70362 2h264d81-038e-4403-9e86-788ab3d70362bak(please note that the folder name in this example needs to be adjusted by you)
And finally, another task, triggered by stick insertion, will rename that folder back to what it was and afterwards restart the VSC reader (the virtual device), so then it becomes available again immediately without a reboot.



That batch c:\windows\admin\enableTPMVSC.bat goes
pnputil /enum-devices /instanceid "USBSTOR\DISK&VEN_&PROD_USB_FLASH_MEMORY&REV_PMAP\00187D0F569EEC10F0003F40&0" | findstr "USBSTOR\Disk&Ven_&Prod_USB_Flash_Memory&Rev_PMAP\00187D0F569EEC10F0003F40&0" && ren C:\Windows\ServiceProfiles\LocalService\AppData\Local\Microsoft\Windows\SmartCard\Tpm\17f7e054-3bae-46c4-8e35-ee3f9c6a0e40bak 17f7e054-3bae-46c4-8e35-ee3f9c6a0e40 && pnputil /restart-device "ROOT\SMARTCARDREADER\0000"Two important notes:
- if the device ID in the batch looks slightly different to the ID in the PowerShell script, it's intended. That's because PowerShell needs to have "#" where batch works with "\" :-)
- If your windows 10 version is lower than Windows 10 v2004, the built-in executable pnputil.exe supports less parameters and that line will not work, so in that case, you'll have to download devcon.exe from Microsoft (see instructions here), deploy it to c:\windows and change that script to c:\windows\admin\enable_TPMVSC.ps1 which should go
$JustNow = (Get-Date).AddSeconds(-5)
$foundstick = Get-WinEvent -FilterHashtable @{LogName='Microsoft-Windows-DriverFrameworks-UserMode/Operational'; starttime=$JustNow}| where message -match 'USBSTOR#DISK&VEN_GENERAL&PROD_USB_FLASH_DISK&REV_1.0#0414EO000000082C&0'
if ($foundstick -ne $null) {ren C:\Windows\ServiceProfiles\LocalService\AppData\Local\Microsoft\Windows\SmartCard\Tpm\17f7e054-3bae-46c4-8e35-ee3f9c6a0e40bak 17f7e054-3bae-46c4-8e35-ee3f9c6a0e40}
if ($foundstick -ne $null) {devcon restart @ROOT\SMARTCARDREADER\0000}Done! Please note that these scripts should be saved to a location that only admins may modify, so for example to c:\windows\admin\.
By now, you might be eager to try it for yourself. Some requirements are mandatory:
- a domain-based certification authority (CA) that you control
- a machine with a TPM module, domain-joined
- a test account (no, please don't start this test with any important account... :-) )
- the steps for setting up the TPM VSC that are found in section 3 of Understanding and Evaluating Virtual Smart Cards
- the 3 scripts from above together with the 3 tasks
- a simple USB stick (empty, any size, any make)
- [if you are hoping to try this on a virtual machine: yes you can, but you need a hypervisor that supports both vTPMs and also USB-passthrough. I recommend to use VMWare Workstation 16 Pro, since this will not work on Hyper-V, nor on Virtual Box]
So after successfully trying, I hope you will agree that this is comparable to using a real SmartCard!
In the next section, I will look at the problems that I see with this usage scenario and compare them to those of real SmartCards. These problems are not all grave, but they clearly exist, so let me name them:
- The logon using a TPM-VSC is 2 seconds slower than with my real SmartCard
Oh, that's too bad, there go another two seconds and here another two, ouch... Honestly, does this really matter? I don't think so, but I still wanted to share this observation with you.
- If you shutdown your computer with your USB stick still inserted (but you remove it afterwards), the VSC will not become disabled - now is that a problem, exclusive to VSC? Yes, if we think of an attacker able to film our keyboard and gather PINs, he may of course also be able to gather your disk encryption password which would allow him to start the machine, enter the PIN and be in! So you better have 2FA for disk encryption as well! To do that, you could use Bitlocker with TPM+PIN+USB stick and use the same USB stick, as this will also defeat this attack vector! Here's the command to do it
manage-bde -protectors -add C: -TPMandPINandStartupKey -tp 12345678 -tsk E:- You might forget to unplug the USB stick when you leave the room
Sadly, this could become a problem. If someone has shoulder-surfed your PIN before, leaving the stick plugged in is an invitation (but that same problem exists with ordinary SmartCards, too!). So train yourself to always lock the screen by removing the stick and not by pressing Windows-L, so removal will quickly become a habit. But even if you forget the stick, the attacker won't get anywhere without your PIN.
- To get the PIN, an attacker has more options than just shoulder surfing, hidden cameras/keyloggers
True. Namely, he may use malware placed on your device to steal your PIN from your machine's RAM. The infamous Mimikatz, for example, can do it when executed as administrator. But if he already got admin on your machine, then why bother? And by the way, this is, of course, applicable to normal SmartCards and passwords as well.
At this point, I would like to compare the risks that come with SmartCards to those that come with using ordinary passwords:
SmartCards have the advantage of allowing you to require 2 factors for authentication: something you have (the physical SmartCard or, with VSCs, the stick) and something you know (the PIN). Not having that 2nd factor is not something hackers will easily defeat.
Passwords will work on all machines that you may logon to - but that is not only convenient for you but also positive from a hacker's perspective. Passwords will also allow an attacker to potentially use them from the LAN, or even from the internet, while not having to be on premises.
VSCs will only work on one machine, so once a VSC is compromised, it's still only abusable on a single machine and only if the attacker is able to boot that machine and visit it physically - a VSC can not be used without sitting in front of the machine it is tied to!
Conclusion
VSCs are definitely worth looking into as an alternate way for securely logging on to your domain. The functional differences to real SmartCards are small by default, and my method even enhances them to allow true 2-factor-authentication like with a real SmartCard, but without having to buy anything, nor depend on any software but the OS alone!
But like with many other security technologies, they are not safe by design but instead only when used carefully. So it's up to you to judge and decide whether you or your users are ready for them.
That's all. I hope you have learned something new and I am looking forward to your questions or comments of any kind!
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (8)
Author
Commented:Commented:
1) Other security measures block the use of USB devices for most Users via a User GPO. With this process, the USB is used before the User is logged on.... so it seems like it might work even in this case?
2) Another security measure logs off the User after a time. So, a new logon is required. I guess this means that the machine is in the same pre-logon state as always.
3) Another security measure turns on a screen saver requiring a password. I wonder about that in this case.
I got a bit stuck on this:Did you mean WITH this approach or WITHOUT it? I'd hope the latter. With it, what is the alternative such as in the cases I've mentioned?
Author
Commented:2) yes
3) no problem
"4") I wrote "passwords". So I mean with passwords, not with my 2FA-approach, no.
Commented:
Well, our implementation of blocking is with a User GPO so *some* users are allowed USB storage devices and most aren't. And, some computers have this GPO Denied so we can run USB hard drives on them. So, I rather think it might work. We can try.
Thanks for the good ideas all worked out!
Commented:
View More