Securing Active Directory Domain Controllers
I have over 30 years in the IT industry. During this time I have worked with a variety of products in a variety of industries.
Published:
Browse All Articles > Securing Active Directory Domain Controllers
It is more important than ever to ensure that your domain controllers are as secured as possible. This article walks you through a number of settings and procedures to harden your domain controllers.
Active Directory is the core to any Microsoft network environment. Even with the adoption of cloud services, many organizations continue to run on premise domain controllers. These systems provide management, access and control of the majority of the environment. Therefore, if a threat actor can compromise one or more of these systems, they have essentially stolen the “keys to the kingdom”. There are several things that can be done to help protect these from compromise. Some are well known and done may domain administrators, others are less known and have the potential to cause issues depending on the age of other operating systems and technologies in the environment.
Simple, Common Best Practices
Change the administrator account – it is common knowledge that the default administrator name is “Administrator”. Therefore, while not a major hurdle, changing this to something other than administrator will take a small step in making it harder to compromise the system.
Use a long, complex password – make the password at lease 12 characters that consist of upper- and lower-case letters, special characters and numbers. The longer the better, but currently it is estimated that it would take 34,000 years to crack a 12-character password (Buchholz, 2021)
Do not commonly long in with administrator account – do not log into the domain as administrator unless performing a function that requires it. This is typically functions like adding or removing domain controllers or other similar functions. For normal day to day responsibilities, use a dedicated domain administrator account.
Use a separate account and computer – when logging into a domain controller, it is recommended to have a dedicated user account that you do not use for your normal day-to-day activities. In addition, it is recommended to use a dedicated computer that is only used to log into the domain controllers or Active Directory. This system should never be used to go to the Internet, receive emails, etc.
Hardening the Server Operating System
These changes can be implemented as Group Policies that will automatically apply to all existing and new domain controllers. You should not alter the default domain controller policy. You could make a copy if it, provide a detailed name such as "Secured Domain Controller Policy" and attach it to the Domain Controller OU along with the default policy. The recommendation would be to only add two to three at a time. This way if something breaks, you have some idea which policy maybe causing the issues. In order to implement some of these GPO’s, you need to download the Microsoft Security and Compliance Toolkit located here for your specific operating system version: https://www.microsoft.com/en-us/download/details.aspx?id=55319 then extract the zip file and place the ADMX and ADML packages in the Policy Definition folder on the domain controller(s). Always ensure that you BACKUP YOUR REGISTRY before implementing changes!
Block browsers from running – this policy will prevent IE, Chrome, Firefox
Right-click on the GPO and select "Edit", then Computer Configuration > Policies > Windows Settings > Security Settings > Application Control Policies > AppLocker > Executable Rules
Make LDAP Authentication over SSL/TLS More Secure – this setting helps enforce encryption and helps protect against “man-in-the-middle” attacks. However, before implementing, you need to make sure this update is installed or you could have compatibility issues: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2017-8563
To implement, make the following GPO changes:
Disable Insecure Guest Logons to SMB – by default, the system will allow insecure SMB guest access. By setting this to “Disabled”, these connections are denied
Hardened UNC Paths– this policy secures the UNC path. On a domain controller, the Netlogon and Sysvol are shared. This policy will harden access to them.
Prevent the System Storage of Hashed Passwords– by default, Windows stores a hash of each user’s password when they login. This hash table can be stolen, and a threat actor can crack the hashes allowing them to obtain the login password. This setting prevents the storage of password hashes. This one is good to apply not to just domain controllers, but all domain systems. Now, this does not delete the current hash values, so this should be used in conjunction with password changes.
Enforce LAN Manager Server Authentication to NTLMv2 – WARNING – this setting can impact some older client operating systems. This GPO will force the server to only allow NTLMv2 sessions and refuse LM and NTLM.
Enforce Client-Side LAN Manager – this is the second part to the above server-side setting
Disable SMBv1 – SMBv1 should disabled unless it truly needed for older operating systems that are no longer supported (this is a entirely different discussion if these are still in the environment). More modern servers like Windows Server 2016 and 2019 have it disabled by default.
Disable SMB/NETBIOS NULL Sessions – while disable on newer operating systems, this could still be an issue. It is best to set this GPO setting to ensure it NULL session do not occur.
Disable NULL Session Fallback– this policy affects the way the authentication process works when communicating with older operating systems. This determines if a local service can fallback to NULL session. It is recommended to disable this function.
Disable Autoplay– this is a feature where when a CD\ISO is inserted, the system auto launches the device and may initiate the installation of an application. This is seen as a security risk and should be disabled.
Harden Remote Desktop – while in many environments Remote Desktop is a necessity for remote management, there are a number of steps that can be taken to harden it an reduce the attack footprint like preventing passwords from being saved and setting specific encryption levels.
NEVER EXPOSE RDP TO THE INTERNET!!!
Vulnerability Remediation
Below is a list of various vulnerabilities that may or may not have been implemented in your environment. While most security vulnerabilities are addressed via updates, there are others that need to be addressed via registry settings, or a combination of updates and registry settings. These are highly recommended to secure your domain controllers
Spectre Meltdown – is a speculative side-channel execution issue covered under ADV18002 and CVE’s 2017-5753, 2017-5715, and 2017-5754. Reporting on this seems to vary slightly depending on the vulnerability scanning tool. Depending on your operating system, you may need KB4056897, KB4056890, KB4056892, or KB4056898 in conjunction with these registry settings. The listed commands can be applied via an elevated PowerShell session and addresses all three CVE’s:
Disable TLS 1 and 1.1 – TLS version 1 and 1.1 have been depreciated and found to be insecure. It is highly recommended to disable these if they have not already been disabled. These can be placed in a note pad and saved as a .reg file. Then applied by double-clicking the file.
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client]"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server]"Enabled"=dword:00000000
Disable Depreciated Ciphers – there are a few encryption ciphers that have been found to be vulnerable. These are RC4 128 and Triple DES 168. These can be disabled with the following registry entries:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128]"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168]"Enabled"=dword:00000000
SMB Signing Disabled or Not Required Vulnerability – this helps prevent “man-in-the-middle” attacks by enabling this for both the server and the client, SMB sessions are authenticated. This is address in the following Microsoft article: Overview of Server Message Block Signing
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters] "requiresecuritysignature"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanWorkstation\Parameters] "RequireSecuritySignature"=dword:00000001
Disable Null Sessions – These settings should be used in conjunction with the above GPO setting Disable SMB/NETBIOS NULL Sessions. NOTE: Even with this setting some vulnerability scanners will show it as not resolved. However, this has been validated with Microsoft support and they feel that some vulnerability scanners are improperly checking as described here: SMB and Null Sessions: Why Your Pen Test is Probably Wrong
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA] RestrictAnonymous = 1
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA] RestrictAnonymousSAM = 1
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA] EveryoneIncludesAnonymous = 0
Other Recommendations
One last item to note on securing your Active Directory and domain controllers is to move to some form of elevated account password rotation. This is a utility where any administrative level account has the password rotated on a regular basis and the required password needs to be “checked out” to login in with that account. It also enhances security by consistently changing the password, so that even if it is compromised, the password is not valid for very long. Microsoft has its LAPS (Local Administrator Password Solution) that will rotate and change the local administrator password on a regular basis. There are also third-party solutions that can rotate various domain login accounts like CyberArk, BeyondTrust, and One Identity just to name a few. Doing this will enhance the security of your system making it more complicated to compromise the system as well as keeping a log of who checks out the password and logs into the system.
Conclusion
While no solution or setting offers a 100% guarantee that your network will not be compromised. It is important to take as many steps as necessary to protect and secure the environment. It is best to continually monitor and look for security updates and recommendations. Particularly, when it comes to securing you domain controllers. If you are running older, unsupported operating systems, please check out other related below about moving to a more current version of Microsoft operating systems for your domain controllers and moving to a higher functional level of your domain.
Introducing a Windows 2012 Domain Controller into a 2008 Active Directory Environment
https://www.experts-exchange.com/videos/483/Introducing-a-Windows-2012-Domain-Controller-into-a-2008-Active-Directory-Environment.html
Simple, Common Best Practices
Change the administrator account – it is common knowledge that the default administrator name is “Administrator”. Therefore, while not a major hurdle, changing this to something other than administrator will take a small step in making it harder to compromise the system.
Use a long, complex password – make the password at lease 12 characters that consist of upper- and lower-case letters, special characters and numbers. The longer the better, but currently it is estimated that it would take 34,000 years to crack a 12-character password (Buchholz, 2021)
Do not commonly long in with administrator account – do not log into the domain as administrator unless performing a function that requires it. This is typically functions like adding or removing domain controllers or other similar functions. For normal day to day responsibilities, use a dedicated domain administrator account.
Use a separate account and computer – when logging into a domain controller, it is recommended to have a dedicated user account that you do not use for your normal day-to-day activities. In addition, it is recommended to use a dedicated computer that is only used to log into the domain controllers or Active Directory. This system should never be used to go to the Internet, receive emails, etc.
Hardening the Server Operating System
These changes can be implemented as Group Policies that will automatically apply to all existing and new domain controllers. You should not alter the default domain controller policy. You could make a copy if it, provide a detailed name such as "Secured Domain Controller Policy" and attach it to the Domain Controller OU along with the default policy. The recommendation would be to only add two to three at a time. This way if something breaks, you have some idea which policy maybe causing the issues. In order to implement some of these GPO’s, you need to download the Microsoft Security and Compliance Toolkit located here for your specific operating system version: https://www.microsoft.com/en-us/download/details.aspx?id=55319 then extract the zip file and place the ADMX and ADML packages in the Policy Definition folder on the domain controller(s). Always ensure that you BACKUP YOUR REGISTRY before implementing changes!
Block browsers from running – this policy will prevent IE, Chrome, Firefox
Right-click on the GPO and select "Edit", then Computer Configuration > Policies > Windows Settings > Security Settings > Application Control Policies > AppLocker > Executable Rules
- Right-click and select “Create New Rule” and then "Next"
- Select “Deny” and keep the default of “Everyone”
- Ensure “Publisher” is selected
- Browse to the executable for the browser, select it and click "Open". This will give you a screen similar to the one below.
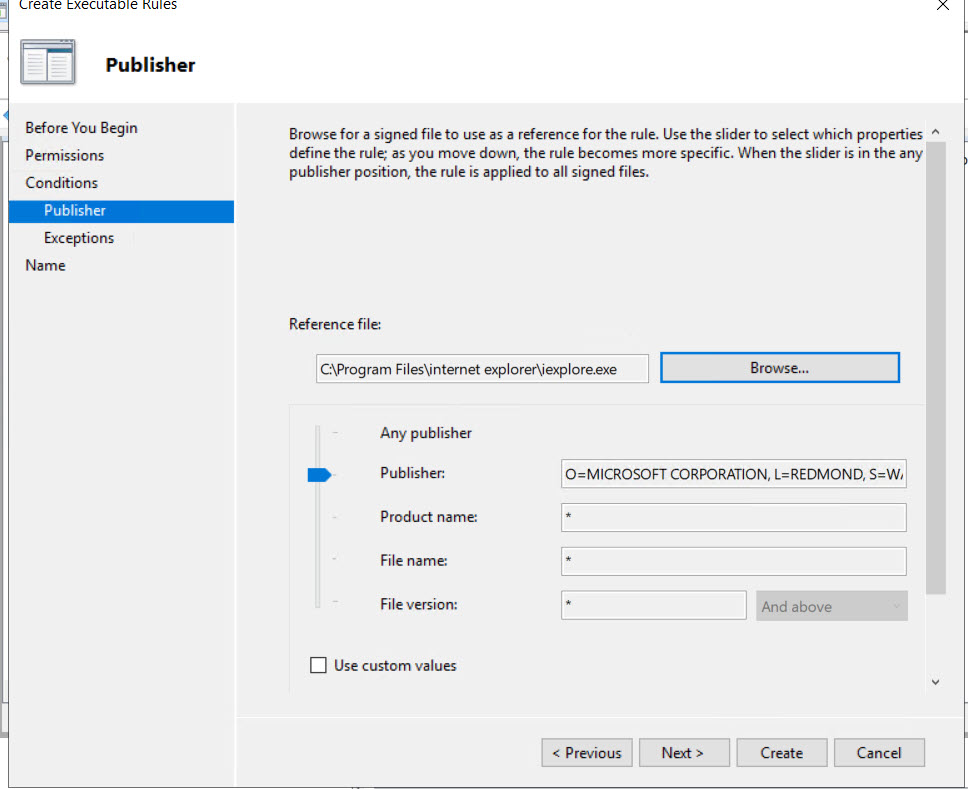
- Then click on "Create". Answer "OK" if asked about creating default rules.
- Repeat for all other browsers.
Make LDAP Authentication over SSL/TLS More Secure – this setting helps enforce encryption and helps protect against “man-in-the-middle” attacks. However, before implementing, you need to make sure this update is installed or you could have compatibility issues: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2017-8563
To implement, make the following GPO changes:
- Computer Configuration > Preferences > Windows Settings > Registry
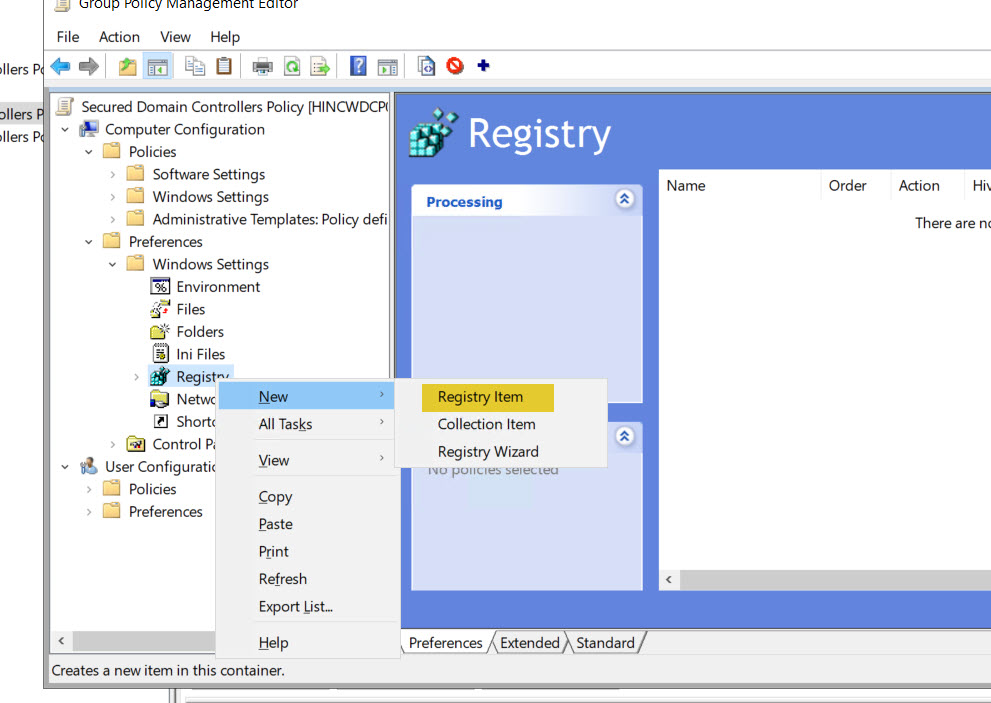
- Change Action to Create and make sure the Hive is set for "HKEY_LOCAL_MACHINE"
- Click on the ellipsis (box with three dots in it) and browse to HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\NTDS\Parameters
- In the Value Name put: LdapEnforceChannelBinding
- For Value Type, select REG_DWORD from the drop down
- Enter "1" for the value and then click "Apply"
Disable Insecure Guest Logons to SMB – by default, the system will allow insecure SMB guest access. By setting this to “Disabled”, these connections are denied
- Computer Configuration > Policies > Administrative Template > Network > Lanman Workstation
- Change “Enable insecure guest logons” to “Disabled”
Hardened UNC Paths– this policy secures the UNC path. On a domain controller, the Netlogon and Sysvol are shared. This policy will harden access to them.
- Computer Configuration > Policies > Administrative Template > Network > Network Provider
- Double-click on “Hardened UNC Paths”
- Select “Enabled
- Scroll down and double-click on “Show” and enter the two paths as follows:
- \\*\NETLOGON Value = RequireMutualAuthentication=1,RequireIntegrity=1
- \\*\SYSVOL Value = RequireMutualAuthentication=1,RequireIntegrity=1
- These setting force mutual authentication and integrity between the clients and servers
Prevent the System Storage of Hashed Passwords– by default, Windows stores a hash of each user’s password when they login. This hash table can be stolen, and a threat actor can crack the hashes allowing them to obtain the login password. This setting prevents the storage of password hashes. This one is good to apply not to just domain controllers, but all domain systems. Now, this does not delete the current hash values, so this should be used in conjunction with password changes.
- Computer Configuration > Policies > Windows Settings > Local Policies > Security Options
- Scroll down until you find “Network Security: Do not store LAN Manager has value on next password change
- Enabled
Enforce LAN Manager Server Authentication to NTLMv2 – WARNING – this setting can impact some older client operating systems. This GPO will force the server to only allow NTLMv2 sessions and refuse LM and NTLM.
- Computer Configuration > Policies > Windows Settings > Local Policies > Security Options
- Scroll down until you find “Network Security: LAN Manager authentication level
- Check the box to define this policy setting
- From the drop down, select “Send NTLMv2 response only. Refuse LM & NTLM”
- Click on “Apply”
- Scroll down two more to “Network Security: Minimum session security for NTLM SSP based (including secure RPC) servers”
- Check the box next to “Define these policy settings”
- Ensure the both of the following are checked:
- Require NTLMv2 session security
- Require 128-bit Encryption
- Click “Apply”
Enforce Client-Side LAN Manager – this is the second part to the above server-side setting
- Computer Configuration > Policies > Windows Settings > Local Policies > Security Options
- Scroll down two more to “Network Security: Minimum session security for NTLM SSP based (including secure RPC) clients”
- Check the box next to “Define these policy settings”
- Ensure the both of the following are checked:
- Require NTLMv2 session security
- Require 128-bit Encryption
- Click “Apply”
Disable SMBv1 – SMBv1 should disabled unless it truly needed for older operating systems that are no longer supported (this is a entirely different discussion if these are still in the environment). More modern servers like Windows Server 2016 and 2019 have it disabled by default.
Disable SMB/NETBIOS NULL Sessions – while disable on newer operating systems, this could still be an issue. It is best to set this GPO setting to ensure it NULL session do not occur.
- Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options
- Network access: Restrict Anonymous access to Named Pipes and Shares
- Enabled
- Network access: Do not allow anonymous enumeration of SAM accounts
- Enabled
- Network access: Do not allow anonymous enumeration of SAM accounts and shares
- Enabled
- Network access: Shares that can be accessed anonymously
- Enabled
- Network access: Let Everyone permissions apply to anonymous users
- Disabled
- Network access: Allow anonymous SID/Name translation
- Disabled
Disable NULL Session Fallback– this policy affects the way the authentication process works when communicating with older operating systems. This determines if a local service can fallback to NULL session. It is recommended to disable this function.
- Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options
- Network security: Allow LocalSystem NULL Session fallback
- Disabled
Disable Autoplay– this is a feature where when a CD\ISO is inserted, the system auto launches the device and may initiate the installation of an application. This is seen as a security risk and should be disabled.
- Computer Configuration > Policies > Administrative Templates > Windows Components > AutoPlay Policies
- Turn off Autoplay
- Enabled
- Disallow Autoplay for non-volume devices
- Enabled
- Set the default behavior for AutoRun
- Enabled
Harden Remote Desktop – while in many environments Remote Desktop is a necessity for remote management, there are a number of steps that can be taken to harden it an reduce the attack footprint like preventing passwords from being saved and setting specific encryption levels.
NEVER EXPOSE RDP TO THE INTERNET!!!
- This should go without saying. However, attack after attack has shown that people still do this with their servers. Set up a VPN and only perform RDP access over a VPN login to the network
- Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Connection Client
- Do not allow passwords to be saved
- Enabled
- Do not allow passwords to be saved
- Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop > Remote Desktop Session Host > Security
- Encryption Level
- High Level
- Encryption Level
- Computer Configuration > Policies > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop > Remote Desktop Session Host > Device and Resource Redirection
- Do not allow driver redirection
- Enabled
- Do not allow driver redirection
Vulnerability Remediation
Below is a list of various vulnerabilities that may or may not have been implemented in your environment. While most security vulnerabilities are addressed via updates, there are others that need to be addressed via registry settings, or a combination of updates and registry settings. These are highly recommended to secure your domain controllers
Spectre Meltdown – is a speculative side-channel execution issue covered under ADV18002 and CVE’s 2017-5753, 2017-5715, and 2017-5754. Reporting on this seems to vary slightly depending on the vulnerability scanning tool. Depending on your operating system, you may need KB4056897, KB4056890, KB4056892, or KB4056898 in conjunction with these registry settings. The listed commands can be applied via an elevated PowerShell session and addresses all three CVE’s:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 72 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Disable TLS 1 and 1.1 – TLS version 1 and 1.1 have been depreciated and found to be insecure. It is highly recommended to disable these if they have not already been disabled. These can be placed in a note pad and saved as a .reg file. Then applied by double-clicking the file.
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client]"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server]"Enabled"=dword:00000000
Disable Depreciated Ciphers – there are a few encryption ciphers that have been found to be vulnerable. These are RC4 128 and Triple DES 168. These can be disabled with the following registry entries:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128]"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168]"Enabled"=dword:00000000
SMB Signing Disabled or Not Required Vulnerability – this helps prevent “man-in-the-middle” attacks by enabling this for both the server and the client, SMB sessions are authenticated. This is address in the following Microsoft article: Overview of Server Message Block Signing
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters] "requiresecuritysignature"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanWorkstation\Parameters] "RequireSecuritySignature"=dword:00000001
Disable Null Sessions – These settings should be used in conjunction with the above GPO setting Disable SMB/NETBIOS NULL Sessions. NOTE: Even with this setting some vulnerability scanners will show it as not resolved. However, this has been validated with Microsoft support and they feel that some vulnerability scanners are improperly checking as described here: SMB and Null Sessions: Why Your Pen Test is Probably Wrong
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA] RestrictAnonymous = 1
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA] RestrictAnonymousSAM = 1
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA] EveryoneIncludesAnonymous = 0
Other Recommendations
One last item to note on securing your Active Directory and domain controllers is to move to some form of elevated account password rotation. This is a utility where any administrative level account has the password rotated on a regular basis and the required password needs to be “checked out” to login in with that account. It also enhances security by consistently changing the password, so that even if it is compromised, the password is not valid for very long. Microsoft has its LAPS (Local Administrator Password Solution) that will rotate and change the local administrator password on a regular basis. There are also third-party solutions that can rotate various domain login accounts like CyberArk, BeyondTrust, and One Identity just to name a few. Doing this will enhance the security of your system making it more complicated to compromise the system as well as keeping a log of who checks out the password and logs into the system.
Conclusion
While no solution or setting offers a 100% guarantee that your network will not be compromised. It is important to take as many steps as necessary to protect and secure the environment. It is best to continually monitor and look for security updates and recommendations. Particularly, when it comes to securing you domain controllers. If you are running older, unsupported operating systems, please check out other related below about moving to a more current version of Microsoft operating systems for your domain controllers and moving to a higher functional level of your domain.
Introducing a Windows 2012 Domain Controller into a 2008 Active Directory Environment
https://www.experts-exchange.com/videos/483/Introducing-a-Windows-2012-Domain-Controller-into-a-2008-Active-Directory-Environment.html
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (0)