Information Technology Audit in Nutshell
Introduction:
Organizations are totally dependent on their technology for their business to function and achieve their strategic objectives. Organizations cannot perform their critical operations without their IT systems. The level of technological complexity of Organizations is increasing.
This article Information Technology Audit (IT Audit) in Nutshell, gives the reader an awareness of the vital concepts and principles required to understand audit function and IT Audit based on the Information Systems Audit and Control Association (ISACA), International Organization for Standardization (ISO) [iso.org], IT Assurance Framework (ITAF), Control Objectives for Information and Related Technologies (COBIT) [isaca.org], the Institute of Internal Auditors [theiia.org], and the National Institute of Standards and Technology (NIST) [nist.gov].
ISACA is a global organization focusing on IT Governance that provides IT professionals with Risk-Based Audit, governance, privacy, and security knowledge. ITAF requires that the information technology audit and assurance function use an appropriate risk assessment approach and supporting methodology to develop the overall IT Infrastructure audit plan and determine priorities for the effective allocation of IT Infrastructure audit resources. The COBIT aims to build an IT Governance framework to effectively control the organization's IT activities. The COBIT framework provides a standard language for IT professionals, business executives, and compliance auditors to communicate with each other about IT control objectives and outcomes.
Every organization shall define an audit policy. Within this policy, the auditing requirements and frequency represent the types of audits performed, who perform those audits, and how frequently they are performed. It delineates the authority for remediating audit issues found in the process. The audit policy should also define the auditing requirements for business partners and subcontractors, which should be included in all contracts with third parties who could impact the organization's overall security. Auditing policies typically include event trigger provisions based on organization risk assessments.
To ensure that Audit Teams/Auditors can perform the audit work, they should:
- Have a complete understanding of the standards, guidelines, and framework that will be applied.
- Know about the auditee's products and services.
- Have studied the regulations that govern the auditee's activities.
- Have the technical qualifications needed to carry out a proper audit.
- Have the professional qualifications required to carry out an audit.
- Understand the new technologies being adopted by the organization.
- Know about new Technology – risks and benefits.
- Learn about new technologies that potentially introduce a set of additional information security vulnerabilities, both known and unknown.
- Understand the concept of operational resilience.
In addition to ensuring Auditor competency, Audit Managers/Lead Auditors should:
- Develop and enforce a code of ethics to govern the audit process.
- Monitor and evaluate the performance of the audit teams.
- Guarantee consistency that all Auditors make the same observations and draw the same conclusions when confronted with the same evidence.
- Plan and schedule audit activities.
- Perform the Audit Reporting process.
- Control the audit follow-up process.
- Protect the confidentiality of audit information.
- Ensure that Auditors have the resources they need.
Terms and Definitions:
Before we start, herewith are some clarifications that are needed to observe the Audit and IT Audit concept:
- IT System – is defined in the National Institute of Standards and Technology NIST (800-30) [nist.gov] as any collection of processes and/or devices that accomplish an objective. The Auditor needs to understand IT systems design and testing comprehensively.
- IT Infrastructure – includes, i.e., Investment Programs, IT services, IT Projects, IT Assets, Applications, Databases, Websites, Operating Systems (OS), Virtual Machines, Cloud Services, Third-Party Suppliers, Subsidiaries, Divisions of the organization, or other technical resources.
- Audit – formal evidence-based examination of a process or product for the purpose of control. An audit is a systematic assessment of the security controls of information systems. Also, an audit involves the evaluation of the information systems-related controls implemented by the management to ensure the achievement of control objectives.
- Auditee – the organization being audited can be from internal or external sources.
- Auditor – the organization is performing the audit work. Auditors must understand materiality and the relative importance of findings based on business impact due to noncompliance to controls.
- Audit Customer – the organization requests the audit work to ensure compliance.
- Audit Framework – the specific standard used to conduct the audit. The primary mandate for any organization implementing an effective audit framework is to follow the standards and guidelines.
- Audit Program – is a set of audit instructions and procedures that should be performed to complete an audit. It is a list of the audit evidence-gathering activities that are performed during the execution in the fieldwork.
- Audit Procedures – these are the activities/steps taken to acquire audit evidence that is sufficient, appropriate, and satisfies the audit objectives.
- Audit Methodology – this is the strategy used to conduct the audit.
- Audit Evidence – lifecycle 4 phases are collection, analysis, preservation, and destruction. It should include information regarding the original source and date of creation. Also, security measures should be taken to preserve its integrity.
- Audit Findings – must be supported by objective evidence.
- Audit Management – standard activities planned and implemented to achieve audit goals.
- Audit Rules – the events that the Compliance Auditor must retrieve for viewing and permission are specified in the audit rules.
- Compliance – a state of agreement or alignment with formally expressed criteria.
- Governance – planned organization-wide control over all activities meant to achieve goals.
- IT Governance – the role is to know an asset's precise status at all times. It also focused on IT and its performance and risk management.
- Cyber Governance – refers to the organization of the arrangements put in place to establish, implement and review its approach to managing cyber risks. Effective cyber governance should start with a clear and comprehensive cyber resilience framework guided by a cyber resilience strategy.
- Information Security Governance – when properly implemented, should provide four basic outcomes: strategic alignment, value delivery, risk management, and performance measurement.
- Risk – any event that may negatively affect the accomplishment of business objectives.
- Risk Assessment – provides essential information required to determine the appropriate risk response. To assess IT risk, threats and vulnerabilities must be evaluated using qualitative or quantitative risk assessment approaches.
- Risk Profile – identifies the IT-related risk to which the organization is exposed and indicates which risk factors exceed the risk appetite.
- Risk Appetite – an overall level of risk that an organization is ready to take to fulfill its mission.
- Inherent Risk – is the risk that an event will pose if no controls are implemented to mitigate it. Identifying the inherit risk of an organization's asset or activity will aid you in assessing which controls to put in place to minimize the risk.
- Residual Risk – is the risk that remains even after controls are put into place. Identifying the residual risk of an organization's asset or activity will aid you in assessing the effectiveness of the controls you put in place to mitigate the risk.
- Risk-Based Audit – by following this approach, all of these business risks can be evaluated for severity so that decisions can be made about how to proceed. The Risk-Based Audit by following the below steps. Step 1: Identifying a Risk, Step 2: Factors for Estimating Likelihood, Step 3: Factors for Estimating Impact, Step 4: Determining Severity of the Risk.
- Risk Register – a risk management tool used to collect potential risk events, organize them by risk categories, and assign team members to address them. It also serves as a place to include additional information about each risk, like the nature of the risk and how it will be handled.
- Controls – are implemented top-down in a hierarchy. Furthermore, process and business owners evaluate and enforce controls based on the organization's risk appetite.
- BCP/DRP – Recovering critical and important systems and processes after unexpected harmful events within acceptable time and cost. The organization should have business continuity plans in place and conduct business continuity exercises under a range of severe but plausible scenarios to test its ability to deliver critical operations through disruption.
- Strategic Alignment – provides input for security requirements driven by organization requirements.
- Policies – are high-level documents that represent the corporate philosophy of an organization. Internal standards, procedures, and practices are subordinate to policy.
- Information Security Policies – must be aligned with an organization’s business and security objectives; this is the primary focus of the IT auditor when reviewing the development of information security policies.
Standards vs. Frameworks:
Most used standards and frameworks:
- ISO 27001
- NIST Cybersecurity Framework
- COBIT
- FFIEC Cybersecurity Assessment Tool (CAT)
Standards are:
- Enforceable
- Formalized requirements
- Basis for certification
- Recommended
- Less formal
- Basis for assessment
Audit Accountability and Continuous Auditing:
Every organization needs to understand the status of its own IT Infrastructure and decide the level of protection and control it should provide. The question is, how do we manage risks and secure the information and IT asset? Since both goals are tied directly to best practices, the aim is to utilize a common standard generally accepted to define the complete controls for effective IT Governance. That standard would give them a generally applicable and accepted basis for judging good IT Security and control practices. Furthermore, it would also support determining and monitoring the appropriate IT Security and Control level for a given organization.
While auditing any organization's IT Infrastructure, the following frameworks, including COBIT and ISO 27000, can help the organization apply the best practices. The COBIT aims to build a governance framework to control the organization's activities effectively. ISO 27001 is the best-known standard for information security and the only internationally accepted management system requirement. COBIT and ISO27000 are primarily oriented toward conventional business IT in their practical use.
Auditing is accountable to:
- Identify significant system elements and controls.
- Document control design.
- Evaluate control design.
- Evaluate operational effectiveness.
- Identify and remediate deficiencies.
- Document process and results build sustainability.
Continuous Auditing, per the journal of accountancy, includes:
- Establish priority areas.
- Identify audit rules.
- Determine process frequency.
- Configure parameters and execute.
- Manage results and follow up.
- Report results.
- Assess emerging risks and add them to the risk register.
Auditing and Management Perspective:
An audit process aims to help assure management that its formal controls are sufficient or advise management where processes need improvement. From the management perspective, the obvious question is: "Am I doing all right? If not, how can I make it right or fix it?" The auditing helps to answer these questions. Proper audit procedures suggest that comprehensive risk assessment be conducted to determine which control objectives must be specifically focused on and which may be ignored. The audit objective is to determine whether or not controls are adequate to ensure the reliable processing of the data information. The audit establishes and enforces organizational accountability and control, which requires the explicit description and regular assessment of an identified resource.
Audit Objectives:
The primary objectives of an audit include the following:
- Aim to produce objective reports based on evidence.
- Assure the business is operating smoothly.
- Address both process effectiveness and control efficiency.
- Assess compliance with stated criteria, usually framework based.
- Focus on the most critical element of the function under review.
- Assure that the control objectives are adequately and appropriately addressed.
Compliance Audit promotes Good Governance:
Any organization needs to establish measures to ensure the control and security of its IT Infrastructure. From a management point of view, controls are defined as determining what is being accomplished. Controls are useless if ineffective, so organization management needs to ensure that any control is effective and may be justified in cost terms. This is one of the essential parts of an audit.
Controls are necessary to assess whether the organization is meeting its goals. For the control process to work, the responsibility for the business or IT process must be straightforward, and that accountability must be unambiguous. If not, control information will not flow, and corrective action will not be acted upon. Controls can be standalone for a given purpose or integrated with other controls to achieve general accountability.
The control process formulation must be both direct and action-oriented and generic enough to give the necessary direction to get the organization's information and related processes under control and monitor the achievement of organizational goals.
The objectives of control system auditing are to provide management with reasonable assurance the control objectives are being met, and then where there are significant control weaknesses, to substantiate the resulting risks and advise management on corrective actions. Therefore, the auditing process is built around evaluating the appropriateness of stated controls and obtaining an explicit understanding of the relevant business requirements and their related risks and the control measures that have been deployed to address those risks and requirements. The generally accepted structure of the auditing process is to identify and document explicit control behaviors, evaluate their effectiveness, assess their compliance with their intended purpose, and substantively test for correctness and effectiveness. Compliance is evaluated by testing whether the stated controls work as prescribed, consistently, and continuously. The risk of not meeting control objectives is substantiated by using analytical techniques and/or consulting alternative sources.
IT Governance accomplishes its aims by building a comprehensive structure of rational procedures and relationships, which can be employed to direct and control information assets. As a result, IT Governance establishes a tangible link between the organization's IT resources and its information and business strategy. Ideally, it does this in such a way that it adds value to the organization's purposes.
Organizational Governance aims to build a tangible control and accounting structure to maintain accountability for specific organizational functions. In comparison, Information Governance is enabled by the specification of policies, organizational structures, practices, and procedures required to achieve particular ends. That includes the definition of explicit control elements for any given requirement. This is comprehensive and coherent for the aspect being controlled. It is based on explicit control objectives, the outcome of which is observable. Properly stated, this ensures that due professional care is exercised in the management, use, design, development, maintenance, or operation of Information Systems and Information Assets.
IT Governance involves several related processes to create and enforce ongoing organizational accountability within a control framework. For IT, in particular, this represents a different orientation from the usual assessments done for process development. Information governance aims to explicitly account for and manage an identified resource on a systematic and ongoing basis, for example, money parts. Assessment is exploratory and often one-shot. It is done to find out something specific about an organizational function.
Audit Findings and Risk Treatment:
The Auditors prepare their working documents from the meeting, including all necessary checklists and forms. The lists are used to evaluate IT systems elements, while the records are used to document observations and evidence. Then, the Auditors collect the evidence using these documentation tools. Audit evidence is collected by:
- Interviewing personnel.
- Reading documents.
- Reviewing manuals and working procedures.
- Studying records.
- Analyzing data and information.
- Observing activities.
- Examining conditions.
- Performing the audit.
Risk treatment aims to manage the significance of the risks by addressing either the likelihood or impact or both. Where Auditor's audit findings results are below acceptable thresholds, the organization should assess the residual risk and determine if mitigation, transfer, or acceptance is the correct approach. In some cases, it is impossible to reduce risk further; for example, using legacy systems is required as part of an established business function. Changing the business process or outsourcing the function may be necessary in such cases to avoid the risk. Likewise, it may be required to rethink about IT Infrastructure.
Audit Plan:
An Auditor must understand the overall environment under review when planning an audit. This should include a general understanding of the various business practices and functions relating to the audit subject and the types of information systems and technology supporting the activity. For example, interview appropriate management and staff to understand the following:
- Business requirements and associated risks
- Organization structure.
- Roles and responsibilities.
- Policies, procedures, laws, and regulations.
- Control measures in place.
- Management reporting (status, performance, action items).
The audit plan will enumerate the audit process, including the engagement scope and objectives, identify audit criteria, audit program, reviews and evaluation of evidence, and how to communicate audit conclusions and opinions. The audit plan of the organization should be based on the business risks related to the use of IT.
The audit plan process should be reviewed periodically, typically at least annually, to evaluate new control requirements based on changes in the risk environment, technologies, and business processes and enhanced audit evaluation techniques.
IT Audit process includes:
- Determine the goals.
- Involve the right business unit leaders.
- Determine the scope.
- Choose the audit team.
- Plan the audit: To understand any risk introduced to the business processes, Make sure we meet each of the audit goals, Ensure that the audit process is repeatable (reproduce the results), and ensure documentation starts and continues through to the results.
- Conduct the audit.
- Document the results.
- Communicate the results.
Sample IT Audit Scope:
Auditor review of the IT systems infrastructure should be concluded by a specific time period. The IT Auditor's mission is to examine and evaluate the adequacy and effectiveness of the ISO 27001 Standards to achieve stated goals and objectives for the comprehensive Information Security Management System (ISMS) Project.
IT Auditor review can be performed per auditee risk and control evaluation conducted on the IT processes and sub-processes. IT Audit Scope includes, for example:
- IT Governance
- Review of IT Steering Committee Composition and Functions.
- Review of IT Strategy Planning.
- Review and assessment of the organizational structure of the IT Department with emphasis on segregation of duties.
- Review and evaluate IT Policies, Information Security Policies, and Procedures (Operational and Security).
- Review of IT Budget Process and its compliance.
- Review the compliance process of IT Service Level Agreements (SLAs).
- Review of Information Security Program/Framework.
- Review of Management process of Business Continuity and IT Disaster Recovery Planning.
- Change and/or Patch Management
- Controls related to change authorization, testing, approval, and deployment of changes.
- Segregation of duties over change management process.
- Change monitoring process over applications, operating systems, databases, and networks.
- User Access Management
- Privilege ID Access Management.
- Access Grant and Modification.
- Access Rights Review.
- Access Revocation.
- Password Controls on applications, operating systems, and databases.
- Security settings of corresponding databases of applications.
- Security settings of hosting operating systems of applications.
- Review of antivirus management.
- Physical and Environmental Controls in Data Center
- Data Backup and Recovery Management
- BCP Business Continuity Planning and DRP Disaster Recovery Planning
- Problem and Incident Management
- Review of Network Security Controls:
- Local Area Network and Wide Area Network.
- Configuration/Patch Management for systems and networks.
- Remote access procedure and related controls.
- Email security policy and associated controls.
- User Account Management for network and related infrastructure.
- External Penetration Testing:
- Perform vulnerability scans targeting the public-hosted IPs, web services, and internal IPs.
- Identify the external and internal vulnerabilities.
- Identify the external and internal threats.
- Assess the likelihood of a security failure.
- Analyzing the Vulnerabilities.
- Classification of threats as low, medium, and high.
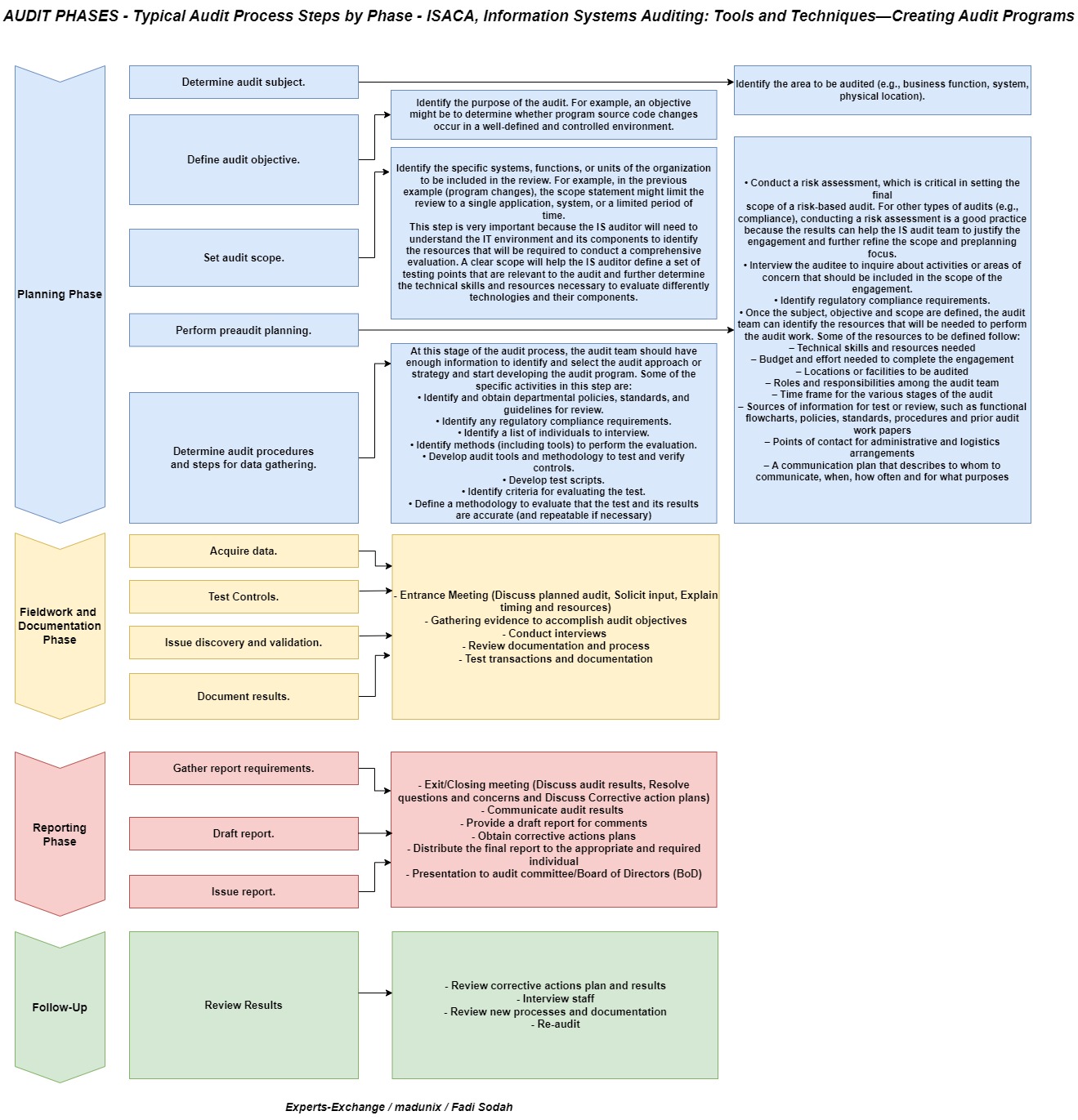
Audit Phases:
The basic steps in the performance of an audit usually include the following:
- Determine audit subject.
- Determine audit object.
- Definition of audit scope.
- Gaining an understanding of the flow of transactions through reviewing the approved policies and procedures.
- Reviewing the adequacy of the designed controls.
- Estimate resources.
- Identifying essential controls and assessing whether or not they are operating as designed.
- Validating audit findings with management.
- Obtaining management responses.
- Audit Report preparation.
- Drafting Audit Report.
- Propose feedback.
- Finalizing the final Audit Report.
- Presentation to Audit Committee and Board of Directors.
- Follow up, Assess Risk continuously.
Auditors will document the process-related IT resources affected by the process under review to obtain the requisite information. Auditors must confirm the understanding of the process under review, key indicators of the process's adequate performance, and the control implications. The effectiveness and appropriateness of control measures for the process under review, or the degree to which the control objective is achieved, can be evaluated using the following criteria:
- Documented processes exist.
- Appropriate deliverables exist.
- Responsibility and accountability are clear and effective.
- Compensating controls exist where necessary.
- The degree to which the control objective is met.
A different set of audit steps are necessary to ensure that the control measures established are working as prescribed; these require the Auditor to obtain direct or indirect evidence to ensure that the audit procedures themselves have adequately complied for the period under review. Therefore, using both direct and indirect evidence, the Auditor will perform a limited review of the adequacy of the process deliverables. In addition, the Auditor will determine the level of substantive testing and additional work needed to ensure that the IT process is adequate.
Finally, audit steps need to be performed to substantiate the risk of the control objective not being met. These steps aim to support the Audit Report and drive the management into action where necessary. Auditors have to be creative in finding and presenting this often sensitive and confidential information:
- Document the control weaknesses, the resulting threats, and vulnerabilities.
- Identify and document the actual and potential impact; for example, through root-cause analysis.
- Provide comparative information, for example, through benchmarks.
When assessing control mechanisms, reviewers should be aware that controls operate at different levels in operation and the lifecycle and that they have indicated relationships. The control framework that is selected will provide some indication as to different control processes, classes, and interrelationships, but actual implementation or assessment of control systems needs to take this added complex dimension into account.
Audit Steps:
The audit begins with a review of all aspects of the audit target. That includes all of the current system documentation. If the preliminary assessment indicates that the system is inadequately controlled, the audit process should go no further. This early exit point is essential because every audit is expensive and time-consuming.
However, if there is reason to assume that the system's controls are in a condition to be audited, an audit plan should be prepared. This is typically executed by the Lead Auditor and approved by the client before the audit begins. The audit is initiated through an opening meeting with the auditee's senior management.
Following the collection phase, any evidence that is obtained through interviews must be authenticated from other sources. In essence, interview evidence should, whenever possible, be confirmed more objectively since it is subjective in nature. Any clues from this evidence that point to possible control system nonconformities must be thoroughly investigated. Then, the system Auditors document their observations using all evidence gathered.
Following the analysis and documentation work, the audit team members make a list of key nonconformities. This list is based on the evidence obtained, and it is appropriately prioritized. The Auditors conclude how well the control system complies with requisite policies and how effectively it achieves its stated objectives. Finally, the Auditors discuss their evidence, observations, conclusions, and non-conformities with the auditee's senior managers before they prepare a final Audit Report.
The Auditor must understand the organization's environment, external and internal factors affecting it, its selection and implementation of policies and procedures, its objectives and strategies, and its performance measurement to identify its key risks effectively. The Auditor should be aware of the six-sigma stages process: Plan Do Check Act [sixsigma.com]. The standard elements of the conventional audit process are:
- Planning.
- Approval of the audit plan by the initiator.
- Conduct an opening meeting.
- Preparation for audit by Auditors.
- The examination and evidence collection.
- Closing meetings and reporting.
- Preliminary conclusions.
- Problems experienced.
- Recommendations.
Business risk is the most crucial driver of the audit program. An audit program is a set of audit instructions and procedures that should be performed to complete an audit. Essentially the audit program includes the following:
- Determine audit subject — What are you auditing?
- Define audit objective — Why are you auditing it?
- Set audit scope — What are the limits to your audit?
- Perform pre-audit planning — What are the risk factors?
- Specify audit procedures and steps for gathering data — How will you test the controls for these risks?
The audit process steps should be the first step to determine the correct scope of the audit. This requires investigation, analysis, and definition of the business processes concerned. The IT roles and responsibilities that might be investigated include in- or outsourced organizational objects and functions and the associated business risks and strategic choices. Platforms and information systems support the business process and are audit targets and connections with other systems.
The next step is identifying the information requirements of particular relevance concerning the business processes. Along with that comes the need to identify the inherent IT risks and the overall level of control that can be associated with the business process. To carry this out properly, there is a need to identify the following:
- Recent changes in the business environment are having an IT impact.
- Recent changes to the IT environment, new developments, and so on.
- Recent incidents are relevant to the controls and business environment.
- IT monitoring controls applied by management.
- Recent Audit Reports.
- Recent results of self-assessments.
IT Audit Report:
IT Audit Reports can include suggestions for improving accounting procedures, internal controls, and other aspects of the (auditee) organization's business arising from the audit. An Auditor is limited to the scope of the audit. In some cases, the Auditor would need to perform a more extensive study if the organization (auditee) wants him to review for weaknesses in existing systems and present detailed recommendations to improve them.
Identifying and remedying control deficiencies are essential to the practical control process. Where a material control deficiency is identified, the Auditor must report its status to the audit customer. The items of noncompliance are normally reported in Auditor's final report.
Every audit will produce some form of recommendations for corrective action. Those recommendations normally follow their own process independent of the audit's conclusion. The audit follow-up process should be officially planned and organized as part of audit planning. It is composed of formal steps to ensure that rework has been performed and to submit the final report close-out report detailing the particular audit's purpose and scope and the results for the audited organization.
The Lead Auditor is responsible for preparing the report. The Lead Auditor sends the Audit Report to the client, and the client sends it to the auditee. The audited is expected to take necessary actions to correct or prevent control system nonconformities. Follow-up audits might be scheduled to verify that corrective and preventive actions were taken.
Summary:
Before an auditee consults an IT Auditor, the organization should know the best IT systems infrastructure implementation practices based on standards. By seeking out industry-accepted and vetted sources for IT, including significant standards like ISO, NIST, IIA, ISACA, ITAF, and COBIT.
The implementation of these standards/frameworks/guidelines should be done in accordance with the principle of proportionality and strategic alignment, taking into account the scale and complexity of operations, the nature of the activity engaged in, the types of services provided, and the corresponding IT Infrastructure and security risks related to the organization’s processes and services.
The IT Auditing should be closely aligned with the business strategy and direction by adopting a Risk-Based Auditing approach along with the standards/frameworks/guidelines mentioned above. The audit process shall be performed following the best-of-practice standards/frameworks. Keeping in mind that IT only exists to assist and advance the organization's objectives and poses a risk to the organization if its failure makes it impossible to achieve the business purpose from an appropriate point of view.
Generally, IT Auditor review is primarily based on inquiry, interviewing, observation, and analytical review procedures supplemented by limited testing of processes, reports, and reconciliations. The resulting issues and recommendations are discussed with management during the audit and before the finalization of the Audit Report.
References:
- https://www.isaca.org/training-and-events/training-topics/browse-all-training ISACA - CISA Review Manual, 27th Edition
- https://www.isaca.org/credentialing/cism ISACA - CISM Review Manual, 16th Edition
- https://www.isaca.org/why-isaca/about-us/newsroom/press-releases/2020/isaca-updates-it-audit-framework-itaf
- https://www.isaca.org/itaf
- https://www.isaca.org/cobit
- https://www.isaca.org/resources/isaca-journal/issues/2019/volume-3/developing-the-it-audit-plan-using-cobit-2019
- https://www.isaca.org/resources/isaca-journal/issues/2020/volume-1/is-audit-basics-the-components-of-the-it-audit-report
- https://www.isaca.org/resources/isaca-journal/issues/2019/volume-2/is-audit-basics-auditing-cybersecurity
- https://www.isaca.org/-/media/files/isacadp/project/isaca/resources/glossary/glossary.pdf
- https://audit.utexas.edu/audit-process
- https://www.theiia.org
- https://www.theiia.org/en/standards/mission-of-internal-audit
- https://www.iso.org/isoiec-27001-information-security.html ISO/IEC 27001 and related standards Information security management
- https://www.iso.org/standard/73906.html ISO/IEC 27000:2018
- https://www.iso.org/standard/75106.html ISO 22301:2019
- https://www.iso.org/standard/82875.html ISO/IEC 27001:2022 Information security management systems — Requirements
- https://www.nist.gov/cyberframework/assessment-auditing-resources
- https://csrc.nist.gov/glossary/term/compliance_audit
- https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-55r1.pdf
- https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-12r1.pdf
- https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-30r1.pdf
- https://www.nist.gov/cyberframework
- https://www.mass.gov/service-details/review-the-ffiec-cybersecurity-assessment-tool-cat
- https://www.experts-exchange.com/articles/37671/Audit-Plays-a-Vital-Role-in-Risk-Assessment.html
- https://www.experts-exchange.com/articles/35333/RISK-ASSESSMENT-METHODOLOGY.html
- https://www.experts-exchange.com/articles/31793/Vulnerability-Assessments-versus-Penetration-Tests.html
- https://www.experts-exchange.com/articles/36691/IT-Risk-Management.html
- https://www.experts-exchange.com/articles/33330/Threat-Modeling-Process-Basics-and-Purpose.html
- https://www.experts-exchange.com/articles/36772/Best-Practice-Principles-for-Business-Impact-Analysis.html
- https://monday.com/blog/project-management/risk-register
- https://www.journalofaccountancy.com/issues/2017/mar/continuous-auditing.html
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.

Comments (0)