Cyberattacks Using AI/ML Technology Targeting Controlled Information
1. Summary
The possibilities of AI/ML Technology are vast, but it is essential to understand its potential security risks. This article will explore the most common methods criminal attackers use to take advantage of AI/ML Technology solutions. In conclusion, AI/ML Technology are powerful technologies that have the potential to revolutionize many industries. However, it is vital to understand their risks and how to mitigate them. By understanding the risks and taking the necessary steps to protect against them, organizations can minimize the chances of becoming victims of a criminal attack.
2. Terms and Definitions
Herewith are clarifications for terms needed to understand and clarify Artificial Intelligence AI/Machine Learning ML concept:
Figure: Schematic view of AI, machine learning, and big data analytics
Artificial Intelligence AI: Artificial Intelligence AI is the ability of computer software or a computer-controlled robot to perform tasks requiring the application of knowledge or reasoning, as well as the simulation or imitation of human intelligence. Today, Artificial Intelligence AI is a broad term meaning machines performing tasks without explicit direction from a programmer.
Machine Learning ML: Machine learning is a common implementation of Artificial Intelligence AI today. An Artificial Intelligence AI discipline in which a machine can gradually improve its predictive and/or decision-making capabilities without being given explicit instructions. Machine Learning is a subspecialty of the science of Artificial Intelligence AI by which a computer improves its own performance by continuously incorporating new data into its statistical model.
Training: In the field of machine learning, the process by which a model learns from input data.
Training Sample: A dataset of examples used to generate a Machine Learning ML model.
Model: One of the significant products of a Machine Learning ML project is the creation of a Machine Learning ML model, a mathematical representation of the process or system that you need to analyze or automate in some way. For example, you might create a Machine Learning ML model to represent a problem scenario in a different field and then apply the model to gain insights, provide guidance, or automate the process.
Algorithm: A set of rules that defines how a problem-solving operation is performed. In computer programming, algorithms are used to express a set of processes that the program must take to determine outcomes.
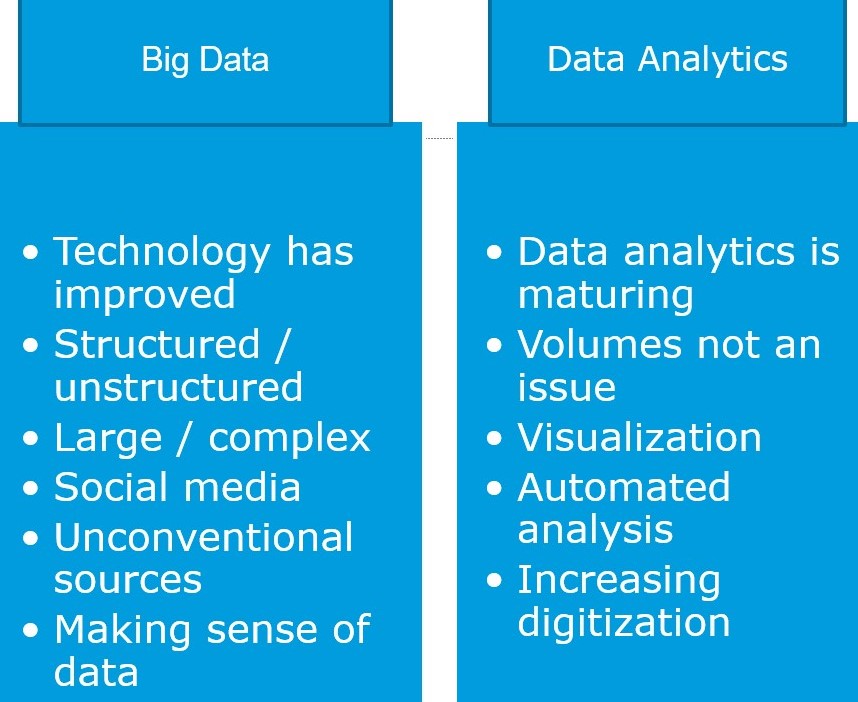
Big Data: This term is based on a collection of data that are so large and complex that they require advanced tools to process and analyze them.
Data Science: The discipline that involves accumulating data, analyzing the data, extracting value from the data, and presenting the value of the data in a meaningful way.
Data analytics: The science of inspecting raw data to draw inferences. It involves applying algorithmic over the raw data to derive insights. Various industries leverage data analytics to examine massive data sets to draw conclusions and ensure the attributes are correlated.
Deep Learning: A type of Machine Learning ML that makes complex decisions using multiple layers of information. Deep learning is a collection of algorithms used in machine learning to model high-level abstractions in data through model architectures. Deep learning is a collection of algorithms used in machine learning. It is used to model high-level abstractions in data using model architectures. It is part of a broad family of Machine Learning ML methods based on learning representations of different data types. Deep learning is a more complex machine learning model that combines other algorithms and outcomes to allow the program to learn further.
Supervised Learning: An algorithm that analyzes data and returns the desired output. This is done by analyzing input with expected and pre-defined input-output data and defining the expected outputs of that data pair. The algorithm then infers the best (most reasonable) course of action based on its training data.
Unsupervised Learning: This is an algorithm characterized by being able to self-organize unknown patterns in data pairs to model the probabilities and the outcomes based on the availability of the data. The model gets more precise with more data.
Reinforcement Learning: This algorithm focuses not on the input/output pairs but on the outcomes that bring the best reward. Think positive reinforcement without losing the "incorrect/not best" results.
Recurrent Neural Network RNN: An artificial neural network (ANN) in which information can flow to and from artificial neurons in a loop rather than just a single direction.
Deep Fake: This type of Artificial Intelligence AI technology generates videos and images of real people doing or saying things they never did or said, which poses a unique challenge to digital media authentication. Deep fake Artificial Intelligence AI can combine and realistically manipulate different elements, such as audio, video, and images, to create an entirely new, synthetic video or image. This technology has also created fake news stories and political propaganda.
Application Programming Interface API: These protocols define how one application interacts with another, usually to facilitate information exchange.
An API specifies: (a) A mechanism for connecting to the software or application; (b) The data and functionality that is made available for this software; (c) Rules and standards that need to be followed by other applications to interact with the application's data and functionality.
Natural Language Processing NLP: The discipline involves computers analyzing and applying human languages.
An Artificial Neural Network ANN: This term describes algorithms and programs that mimic biological neural networks and the term used to describe algorithms and programs that mimic how biological brains process information. The machine learns based on input and output as information flows through these networks. The information given to the system will use various Machine Learning ML models to conduct different solutions. Then the system will correlate the experiences to produce an outcome.
Chatbots: This term describes Artificial Intelligence AI programs designed to carry out conversations and interact with humans via text or voice. Furthermore, they are designed to simulate how a human would speak or type; some are simple (like you see on websites), and some can be as complex as attempting to pass the Turing test.
Privacy: The organization must ensure that data is protected for security (the company's confidential data, for example) and privacy (user data protected by laws and regulations).
Security Concept: Herewith are other essential security concepts that should be known for the reader, such as Confidentiality – Prevents disclosure of data; Integrity – Prevents modification of data; availability – Ensures reliable, timely access to data; Identification – Means by which the user claims Identity, Authentication – Establishes the user's Identity, Accountability – System's ability to determine the actions of users; Authorization – Rights, and permissions granted to an individual and Privacy – The level of confidentiality that a user is given.
Risk Management: This process is a systematic application of management policies, procedures, and practices to communicate, consult, establish the context, and identify, analyze, evaluate, treat, monitor, and review risk.
Fraud: Any action that depends on deception to generate profit is considered fraud.
Sentiment Analysis: A machine should be able to quickly "read" through each review and, based on its language usage, determine whether the user did or did not like a product. This sentiment analysis is a Natural Language Processing NLP task that can be dealt with by creating a Recurrent Neural Network RNN. So, you'll create a review classifier using an RNN.
Automation: The designing and implementing hardware or software capable of doing things automatically — without human intervention.
Business Process Automation BPA: Refers to using cutting-edge technology to complete business processes with the least amount of human involvement.
Figure: Big Data and Data Analytics
3. Artificial Intelligence AI
Artificial Intelligence AI is the technology behind machine learning. It enables machines to learn from data and make decisions without being explicitly programmed.
Artificial Intelligence AI can be used to automate processes, improve decision-making, and even predict outcomes. For example, Artificial Intelligence AI can be used to analyze large datasets and make predictions. It can also be used to identify patterns in data, uncover insights, and recommend actions.
In the world of criminal technology, Artificial Intelligence AI can automate tasks such as facial recognition and surveillance. Artificial Intelligence AI can analyze large amounts of data to identify patterns that could indicate criminal activity. Artificial Intelligence AI can also be used to detect anomalies in data and uncover potential fraud.
As with any technology, criminals can use its vulnerabilities to commit fraud and other illegal activities. Understanding the risks associated with Artificial Intelligence AI and how to mitigate them is vital.
4. Machine Learning ML
Machine Learning ML is the term used to describe the science of algorithms that programs and applications use to analyze data and create probabilities of outcomes to inform the program or application on how to perform a task. Most models rely on input-output pairs to direct the desired results.
Machine Learning ML is a branch of Artificial Intelligence AI that uses algorithms to process and interpret data. It is used to identify patterns in data and make predictions about future events. Machine Learning ML has become increasingly popular in recent years, as it has the potential to revolutionize many industries.
Data anomalies can be found using Machine Learning ML techniques, which can then be utilized to find possible criminal activities. Machine learning ML can be used to find patterns in data that can be utilized to identify potential criminals in the world of criminal technology. Fraud and other shady conduct can also be found with it.
However, using Machine Learning ML in criminal technology is not without risk. As with any technology, criminals can use its vulnerabilities to commit fraud and other illegal activities. Understanding the risks associated with ML and how to mitigate them is important.
5. Examples of AI/ML Use Cases
Many car manufacturers today are including their vehicles' ability to drive without human intervention. This is based on the vehicle being aware of its surroundings and deciding where to be on the road. Perhaps most commonly, many car manufacturers are introducing auto-park features where the vehicle can get itself into a parking spot on its own.
Home automation uses artificial intelligence to adjust your living environment based on the patterns it observes. This adjustment may include learning what temperature you like your living space to be at.
Many online companies relying on ad sales use complex algorithms to target end-users with ads specific to their interests. For example, Google has been using highly targeted ad sales for years based on observing your search history through Google's search engine.
Using Artificial Intelligence AI in healthcare has a tremendous impact via image recognition. Artificial Intelligence AI is being trained to identify cancers. This screening has the potential to make visual recognition of cancer cells a task that can be completely automated, at least from a pre-screening perspective. An Artificial Intelligence AI can get through far more images than a human can. More complex diagnoses may not be something an Artificial Intelligence AI can handle all the time, but it can make simple identification or even rule out non-cancerous cells.
Modern security systems use Artificial Intelligence AI to identify attacks that may not have been seen before. Endpoint detection systems with intrusion prevention capabilities may use Artificial Intelligence AI to perform their duties. Because Artificial Intelligence AI technology is expanding in the Information Security field, all professionals must understand the similarities and differences between these Artificial Intelligence AI variations.
Businesses are often interested in using AI/ML to automate essential business processes to reduce costs, streamline resources, and improve productivity. This process, referred to as Business Process Automation BPA, is geared toward implementing software applications to automate routine business tasks through initiation, execution, and completion while achieving enterprise-wide workflow efficiency.
The finance back office is an essential component of every organization, but when businesses engage in automation and cutting-edge technology like artificial intelligence and machine learning, they are frequently left behind. The most laborious of all back-office duties, accounts payable and accounts receivable, are among the processes that are now least likely to be automated. Artificial Intelligence AI-powered automation has the potential to alter the back office of the finance department and give senior management the tools they need to work more intelligently with their system. It can also support business continuity and resilience.
Figure: AI/ML use cases in finance
6. Understanding the Risk of AI/ML
AI/ML Technology today includes smart home devices, personal assistants, speech recognition, predictive health devices, exercise trackers, financial and stock predictors, chatbot customer support, travel assistance, smart maps, facial recognition, prescriptive advertising, shopping recommendations, and much more.
Artificial intelligence AI is the science and engineering of making intelligent machines. It should be able to make decisions and perform actions without explicit instructions.
Machine Learning ML is an Artificial Intelligence AI that enables computer systems to learn from data and make predictions. Machine Learning ML has become increasingly popular and is now used in various applications, from autonomous vehicle navigation to medical diagnosis.
AI/ML Technology Systems are vulnerable to malicious attacks, and attackers can use AI to their advantage. As AI/ML Technology evolves, so does the criminal element. With the increased use of AI/ML Technology, criminals have found new ways to exploit it for their own gain.
Attackers may also try to take advantage of the vulnerabilities in the system itself. For example, attackers may try to access the system by exploiting weak passwords or other security flaws. They may also try to modify the design to gain access to sensitive data or make it behave unexpectedly.
Another common attack on Machine Learning ML systems is known as a "model stealing attack." In this type of attack, the attacker attempts to steal the trained model from the system. This type of attack is particularly dangerous because the attacker can then use the stolen model to make predictions on different data sets and potentially gain access to sensitive information.
As the adoption and impact of AI/ML Technology increase, regulators need to be well-prepared to address emerging issues. It is essential to be conscious of business resiliency and consumer protection implications while either framing new regulations or tweaking the existing ones without hampering emerging innovations.
The ethics of privacy has become a big topic in AI/ML Technology as more companies are storing more and more information about us. Every company you interact with probably has some record of who you are and what you interacted with them for. Beyond that, various government agencies also have much information about you.
In conclusion, AI/ML Technology are powerful technologies that have the potential to revolutionize many industries. However, it is vital to understand their risks and how to mitigate them. By understanding the risks and taking the necessary steps to protect against them, organizations can minimize the chances of becoming victims of a criminal attack.
7. Cybersecurity
The security of AI/ML Technology is paramount, as Artificial Intelligence AI systems are increasingly used in critical applications such as healthcare, finance, and government. As Artificial Intelligence AI systems become more popular, they become more attractive targets for attackers.
Attacks on AI/ML Technology Systems often involve exploiting vulnerabilities in the system. Such vulnerabilities include poor authentication, weak passwords, and a lack of encryption. Attackers can also try to manipulate the data used by an Artificial Intelligence AI system to get it to make inaccurate predictions.
In addition to these vulnerabilities, attackers may also try to take advantage of the inherent weaknesses of machine learning algorithms. For example, machine learning algorithms are often trained on biased or incomplete datasets, which can lead to inaccurate predictions.
Several measures can be taken to ensure the security of AI/ML Technology. First, it is crucial to ensure that all data used in the system is adequately secured. This includes encrypting data and ensuring that only authorized personnel can access it. Second, it is essential to use secure algorithms and protocols to protect data. This includes using secure authentication, encryption, and firewalls. Finally, it is essential to regularly test and monitor the system to ensure that all security measures are working properly.
Figure: Artificial Intelligence AI for Cybersecurity
8. AI/ML Cyberattacks
Despite the security measures in place, criminals can still exploit Machine Learning ML and Artificial Intelligence AI systems. Attacks occur when an attacker attempts to manipulate a machine learning system to gain access to sensitive data or commit fraud. Attackers may use various methods, such as exploiting vulnerabilities in the system, manipulating data, or creating fake data.
Machine-learning algorithms can improve security solutions and support security teams. Or help criminal hackers to carry out more extensive and more complex attacks.
AI/ML Technology is becoming a core threat detection and response technology. The ability to automatically adapt to changing threat scenarios in real time can give security teams an advantage.
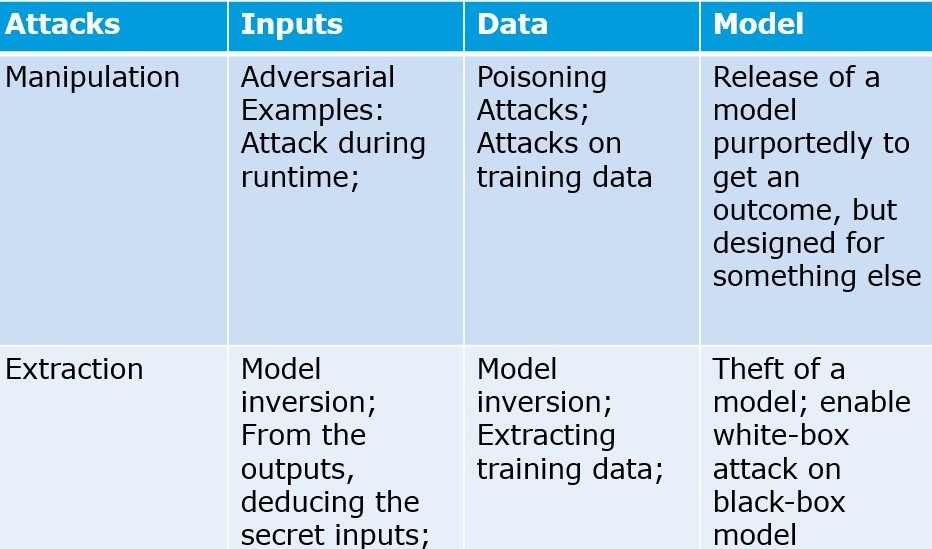
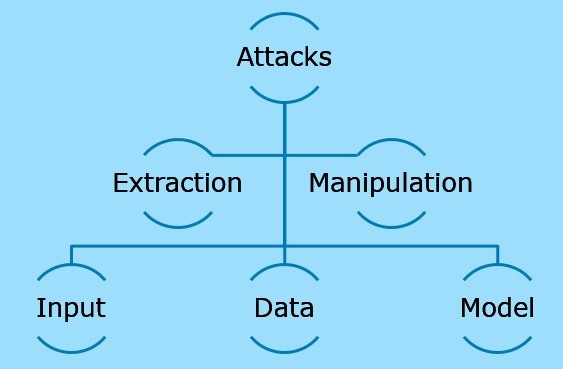
Figure: AI/ML Attacks
Figure: AI/ML Attacks Methods
Cybercriminals are also increasingly using Machine Learning ML and Artificial Intelligence AI to expand their attacks, bypass security controls, and find new vulnerabilities. The most common methods criminal attackers use to take advantage of machine-learning technology are in the field of:
Spam: Defenders have been using machine learning for a long time to detect spam; Spam prevention is the number one use case for machine learning. However, suppose the spam filter relies on predefined rules or creates a type of score. In that case, attackers can exploit this to increase the success of their attacks. You only have to try long enough, and you can reconstruct the underlying model and launch a tailored attack that bypasses this model. Not only are spam filters vulnerable: any security assessment or other output provided by a security provider can potentially be misused. Not everyone has this problem, but a helpful output can provide the basis for malicious activities if you're not careful.
Optimize phishing: Attackers use machine learning-based security tools to test if their messages can bypass spam filters and use machine learning to create these emails. They advertise in criminal forums with special machine learning-based services and use them to make better phishing emails and fake personas for fraud campaigns. These criminal Machine Learning ML services definitely work better. With the help of machine learning, attackers can creatively optimize phishing emails so that they are not recognized as spam and generate as much engagement as possible in the form of clicks. Cybercriminals do not limit themselves to email text; with the help of Artificial Intelligence AI, realistic-looking photos, social media profiles, and other materials can be created to make the communication appear as legitimate as possible.
Password Cracking: Cybercriminals also use Machine Learning ML to crack passwords. This is proven by numerous systems designed to guess passwords and is convincing in terms of frequency and success rate. Cybercriminals are now creating better dictionaries and becoming more clever at hacking stolen hashes. The criminals also use machine learning to identify security controls and to be able to "guess" passwords with fewer attempts. This increases the likelihood of success for cyber attacks.
Deep Fake: Today's deep fake tools create deceivingly realistic video or audio files that are sometimes difficult to detect as fraud. The ability to simulate the voice or face of a person is beneficial for attackers. Some high-profile cases have been reported in recent years where deep fakes have cost companies millions of dollars. To create realistic-looking photos, user profiles, and phishing emails and make their messages appear more credible, more criminal actors are now turning to Artificial Intelligence AI.
Neutralized Security Tools: Many current security tools use a form of artificial intelligence or machine learning. For example, antivirus solutions increasingly look beyond elemental signatures for suspicious behaviors. Attackers could use the tools to optimize their malware until it can evade detection. Artificial Intelligence AI models have many blind spots. All systems that are available online - especially open source - can be exploited by cybercriminals.
Educational Work: Cybercriminals can use machine learning to gather intelligence on traffic patterns, defense measures, and potential vulnerabilities. However, It takes certain skills to take advantage of Artificial Intelligence AI. If the technology eventually becomes commercialized and offered as a service in the cybercrime underworld, it could become accessible to a broader audience. This could also happen if a state-sponsored threat actor develops a specific toolkit that uses machine learning and makes it available to the criminal community. But the barriers to entry remain high: attackers who want to use these tools need to have machine learning expertise.
Autonomous Agents: Suppose a company realizes that it is under attack and blocks internet access to the affected systems. In that case, malware may not be able to connect to the command and control servers to receive instructions. Cybercriminals want to counteract this with intelligent machine-learning models that ensure the malware's functionality even if direct control is impossible. However, this is not relevant for 'conventional' criminal hackers.
AI Poisoning: One of the most common attacks on machine learning systems is known as a "data poisoning attack." In this attack, the attacker modifies the data used to train the machine learning algorithm to get it to make inaccurate predictions. This type of attack is especially dangerous because it can be difficult to detect, as the attacker can hide their modifications in the data.
Data poisoning, also known as Artificial Intelligence AI poisoning, is an attack where an attacker alters the data used to train a machine learning system. The attacker may change the data to make the system believe that a certain type of data is normal when it is not. This can lead to inaccurate results or even complete failure of the system. The datasets could, for example, be intentionally distorted. For example, attackers can trick Machine Learning ML models by feeding them new information - manipulating the training dataset. The same approach could be used to teach a system that a certain type of malware is safe or that certain bot behavior is entirely normal.
To protect against data poisoning attacks, it is important to ensure that all data used to train the system is accurate and up to date. Additionally, it is important to use data validation techniques such as cross-validation and outlier detection to identify any anomalies in the data.
AI Fuzzing: Artificial Intelligence AI fuzzing is an attack where an attacker manipulates the inputs to a machine learning system to cause inaccurate results. This can lead to inaccurate predictions or even complete failure of the system. Professional software developers and penetration testers use fuzzing solutions to generate random inputs and test systems or find vulnerabilities in this way. Machine learning is also often used, for example, to generate more specific and organized inputs.
This makes fuzzing tools useful for companies but also for cybercriminals. It is necessary to create multiple obstacles, not just one that the attackers can eventually use to their advantage. Therefore, basic cyber hygiene in the form of patches, anti-phishing training, and micro-segmentation is still of crucial importance.
To protect against Artificial Intelligence AI fuzzing, it is vital to use input validation techniques such as parameter checking and data type checking. Additionally, it is essential to use secure algorithms and protocols to protect the system from malicious inputs.
9. Conclusion
Security is of the utmost importance when it comes to using AI/ML Technology. As with any technology, criminals can exploit any vulnerabilities to gain access to sensitive data or commit fraud. AI/ML Technology investment requires a high level of expertise, which needs improvement. Additionally, there are typically more accessible and more straightforward ways for attackers. Generally, criminal hackers do not make use of them in most cases. However, this could change if companies further improve their defensive measures and criminals and nation-states continue to invest in cyber attacks.
The cyber threat landscape is evolving as unethical hackers shift to more-advanced attacks to gain access to data and control systems. For the cybersecurity professional, the strategies for defense are also shifting, and many considerations, including the use of Artificial Intelligence AI, are now commonplace discussions in the industry.
10. References and Resources
Keep yourself updated with the Latest Research from [https://arxiv.org/] [https://arxiv-sanity-lite.com/]; they have valuable resources. Automatically recommends new papers according to your interests.
https://www.telusinternational.com/insights/ai-data/article/50-beginner-ai-terms-you-should-know
https://www.expert.ai/glossary-of-ai-terms/
https://arxiv.org/pdf/2102.07969.pdf
https://arxiv.org/ftp/arxiv/papers/2209/2209.13454.pdf
https://www.experts-exchange.com/articles/37654/Guidelines-for-Adequate-Cyber-Hygiene.html
https://www.iso.org/standard/74438.html
https://www.experts-exchange.com/articles/33330/Threat-Modeling-Process-Basics-and-Purpose.html
https://www.cancer.gov/news-events/cancer-currents-blog/2022/artificial-intelligence-cancer-imaging
https://www.ibm.com/topics/artificial-intelligence-healthcare
https://www.auditoria.ai/wp-content/uploads/Auditoria_CFO-Dive-Playbook_web1.pdfhttps://hbr.org/2017/07/the-business-of-artificial-intelligence
https://www.experts-exchange.com/articles/34091/Big-Data-Concepts-Security-and-Use-Cases.html
https://www.experts-exchange.com/articles/36691/IT-Risk-Management.html
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.

Comments (6)
Commented:
Commented:
Commented:
Commented:
Commented:
View More