Browse All Articles > OVAL: Open Vulnerabiity Assessment Language
This white paper is a quick-view into the Open Vulnerability Assessment Language (OVAL) and where it fits into the context of security assessment and compliance. This white paper should help those who have not yet had an introduction to OVAL and its many applications. This content should give the reader a foundation in OVAL concepts and use, and provide the necessary links to resources for further investigation.
Cybercrime and the increasing number of attacks has reached such levels that a solid and standard security framework must be implemented for organizations responsible for maintaining private data (P.). In the past, determining compliance of the network and system were largely a manual and prose-based endeavor. If proprietary tools existed, there had been little-to-no interoperability between them. Consequently, the security posture of an organization had been more prone to gaps and error. OVAL, as only one of the several interoperable standards of the Security Content Automation Protocol (SCAP), can help close security gaps through the ease of automation, and provide measurable security results to organizations who adopt vendor tools that implement OVAL and other SCAP components. Implementing OVAL produces cost and time savings for organizations (Martin).
Many of the books and study materials for base-line security exams like Security+ may mention OVAL in isolation and as a proverbial footnote, not presenting it within the larger framework of collaborative standards. OVAL can be implemented independently (Quin). Yet , OVAL is only a piece of the Information Security assessment and compliance puzzle. To understand OVAL standards, and their application, OVAL must be discussed in context to the broader Security Content Automation Protocol (SCAP). OVAL is considered one of the SCAP components. Although a discussion of SCAP is out of this paper's scope, I will present OVAL as a piece within this broader puzzle.
![Independent, Yet Interoperable SCAP Standards]()
OVAL is a community developed standard for automating assessment and reporting within many areas of enterprise security including System Inventory, configuration Management, Patch Management, Security Advisory Distribution, Malware and Threat Indicator Sharing, and Vulnerability Assessment. OVAL, a significant addition to security automation, is an international standard that NIST's Security Content Automation Protocol (SCAP) uses under its umbrella along with other “components” like CVE, CCE, CPE, CVSS, and XCCDF. According to MITRE's Benchmark Development site, OVAL answers the question: “How do I make sure my systems conform to policy?”.
![a SCAP validated vendor tool]() An OVAL Definition is the foundation for implementation and provides the input for the automated assessment. You can obtain preexisting OVAL Definitions to implement in a vendor tool or your own application. They are available from public repositories. You may also enhance OVAL Definitions or develop new ones of your own.
An OVAL Definition is the foundation for implementation and provides the input for the automated assessment. You can obtain preexisting OVAL Definitions to implement in a vendor tool or your own application. They are available from public repositories. You may also enhance OVAL Definitions or develop new ones of your own.
Anyone can download and use MITRE's open source software – OVAL Interpreter - by downloading and running the installation package via SourceForge. The OVAL Interpreter provides a sample of how the OVAL standard can be implemented in a product.
The OVAL standard can be segmented into Language and Content (Hansbury). OVAL creates a process standard for security testing and assessment. The assessment process categories are:
![MITRE's Internet Site]()
To do a basic inventory check of my Windows 7 system, after I installed OVAL Interpreter, I downloaded the Windows 7 definition file from the OVAL Repositories on MITRE's site. There are 5 different class categories for OVAL Definition content (compliance, inventory, miscellaneous, path and vulnerability). I saved the definitions file in the same directory as the OVAL Interpreter application. Then, I ran the following command:
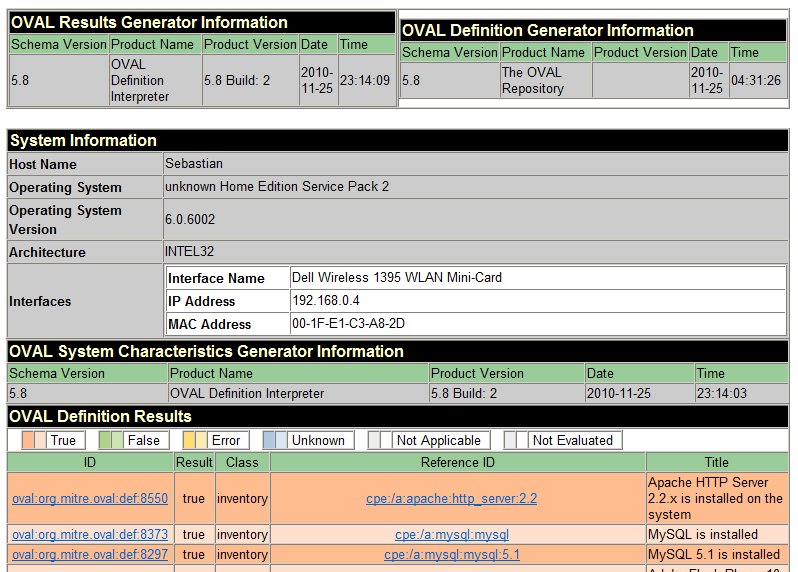
For a more meaningful understanding of the result, the OVAL Interpreter outputs a results.html. Within this instance of the final report output from my Windows 7 OVAL check, one of the items returned was a positive check that my system was installed with the Apache HTTP server 2.2. This check was performed using the OVAL inventory class.
column back to MITRE's site for each inventory item.
![OVAL's Output from Windows Inventory Class]() The ID link for the Apache HTTP 2.2 server opened an internet page containing a list of extending
The ID link for the Apache HTTP 2.2 server opened an internet page containing a list of extending
definitions related to Apache vulnerabilities. I then downloaded the extended definitions and ran those, to
find the below vulnerabilities on my system.
![OVAL's Output from Apache Vulnerability Class]()
assessments. The standardized XML base for OVAL means that the same definitions and data can be
shared and used across platforms, technologies and tools. MITRE's OVAL Interpreter helps us understand
the implementation of OVAL standards and how new tools can be developed to use the standard.
However, OVAL is only a piece of the SCAP puzzle. Vendor tools that can implement many SCAP
components will be able to offer more robust products that can operate on a larger scope of organizational
security.
whitepaper-ovalsecurity-HabbasCo.pdf
The Problem: Conforming to Security Guidance and Policy
Cybercrime and the increasing number of attacks has reached such levels that a solid and standard security framework must be implemented for organizations responsible for maintaining private data (P.). In the past, determining compliance of the network and system were largely a manual and prose-based endeavor. If proprietary tools existed, there had been little-to-no interoperability between them. Consequently, the security posture of an organization had been more prone to gaps and error. OVAL, as only one of the several interoperable standards of the Security Content Automation Protocol (SCAP), can help close security gaps through the ease of automation, and provide measurable security results to organizations who adopt vendor tools that implement OVAL and other SCAP components. Implementing OVAL produces cost and time savings for organizations (Martin).
What is OVAL?
Many of the books and study materials for base-line security exams like Security+ may mention OVAL in isolation and as a proverbial footnote, not presenting it within the larger framework of collaborative standards. OVAL can be implemented independently (Quin). Yet , OVAL is only a piece of the Information Security assessment and compliance puzzle. To understand OVAL standards, and their application, OVAL must be discussed in context to the broader Security Content Automation Protocol (SCAP). OVAL is considered one of the SCAP components. Although a discussion of SCAP is out of this paper's scope, I will present OVAL as a piece within this broader puzzle.
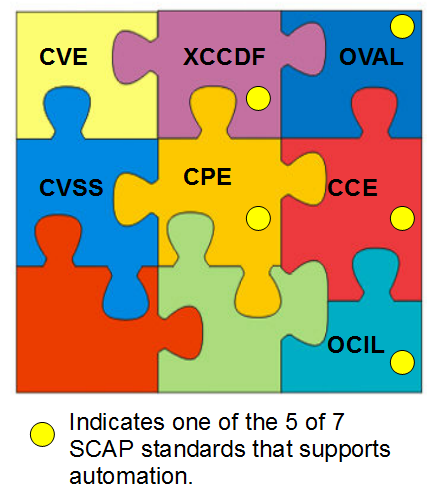
OVAL: Where does it fit into the Security Context?
OVAL is a community developed standard for automating assessment and reporting within many areas of enterprise security including System Inventory, configuration Management, Patch Management, Security Advisory Distribution, Malware and Threat Indicator Sharing, and Vulnerability Assessment. OVAL, a significant addition to security automation, is an international standard that NIST's Security Content Automation Protocol (SCAP) uses under its umbrella along with other “components” like CVE, CCE, CPE, CVSS, and XCCDF. According to MITRE's Benchmark Development site, OVAL answers the question: “How do I make sure my systems conform to policy?”.
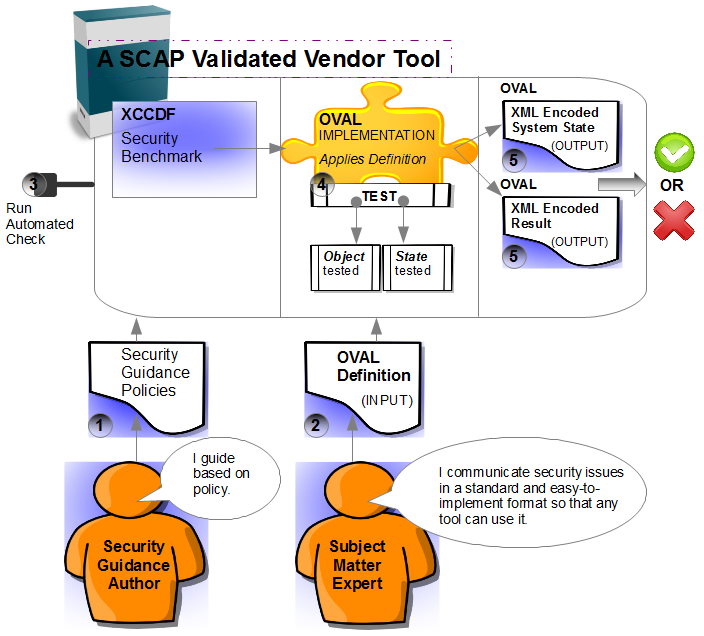 An OVAL Definition is the foundation for implementation and provides the input for the automated assessment. You can obtain preexisting OVAL Definitions to implement in a vendor tool or your own application. They are available from public repositories. You may also enhance OVAL Definitions or develop new ones of your own.
An OVAL Definition is the foundation for implementation and provides the input for the automated assessment. You can obtain preexisting OVAL Definitions to implement in a vendor tool or your own application. They are available from public repositories. You may also enhance OVAL Definitions or develop new ones of your own.
OVAL in Action
Anyone can download and use MITRE's open source software – OVAL Interpreter - by downloading and running the installation package via SourceForge. The OVAL Interpreter provides a sample of how the OVAL standard can be implemented in a product.
The OVAL standard can be segmented into Language and Content (Hansbury). OVAL creates a process standard for security testing and assessment. The assessment process categories are:
1. Retrieving system configuration information
2. Analyzing and testing the system
3. Reporting the assessment result
XML Schemas have been developed to directly map to the above processes.
2. Analyzing and testing the system
3. Reporting the assessment result
1. OVAL System Characteristics Schema: Representative of the machine configuration state.
2. OVAL Definition Schema: Representative of a machine state (vulnerable or compliant, etc.)
3. OVAL Results Schema: Representative of the reported results of the assessment.
In a simple inventory check on a Windows system, Oval Interpreter uses a windows definition file, as well as a system characteristics file in order to run tests to see what software is installed on a system. The System Characteristics file is an encoded XML document that represents the state of the current machine. The definition file contains the tests, test-objects and test- states that the OVAL Interpreter will use in its analysis. The final results are encoded in a results schema, and from it, the program creates an web document output for easy viewing.
2. OVAL Definition Schema: Representative of a machine state (vulnerable or compliant, etc.)
3. OVAL Results Schema: Representative of the reported results of the assessment.
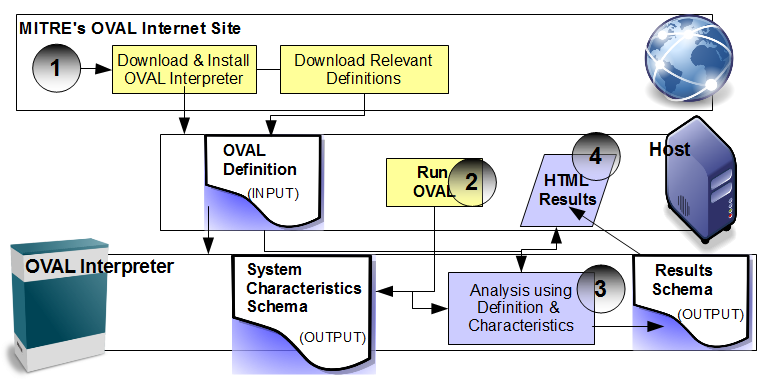
To do a basic inventory check of my Windows 7 system, after I installed OVAL Interpreter, I downloaded the Windows 7 definition file from the OVAL Repositories on MITRE's site. There are 5 different class categories for OVAL Definition content (compliance, inventory, miscellaneous, path and vulnerability). I saved the definitions file in the same directory as the OVAL Interpreter application. Then, I ran the following command:
ovaldi microsoft.windows.7.xml -mC:\Program Files\OVAL\ovaldi-5.8.2>ovaldi.exe -o xml/microsoft.windows.7.xml -m
----------------------------------------------------
OVAL Definition Interpreter
Version: 5.8 Build: 2
Build date: Oct 13 2010 20:30:22
Copyright (c) 2002-2010 - The MITRE Corporation
----------------------------------------------------
Start Time: Thu Nov 25 23:14:02 2010
** parsing xml/microsoft.windows.7.xml file.
- validating xml schema.
** creating a new OVAL System Characteristics file.
** gathering data for the OVAL definitions.
Collecting object: FINISHED
** saving data model to system-characteristics.xml.
** running the OVAL Definition analysis.
Analyzing definition: FINISHED
** applying directives to OVAL results.
** OVAL definition results.
OVAL Id Result
-------------------------------------------------------
oval:org.mitre.oval:def:8550 true
oval:org.mitre.oval:def:8373 true
oval:org.mitre.oval:def:6700 true
oval:org.mitre.oval:def:1282 true
oval:org.mitre.oval:def:6589 true
oval:org.mitre.oval:def:6390 true
oval:org.mitre.oval:def:6210 true
oval:org.mitre.oval:def:8507 false
oval:org.mitre.oval:def:8419 false
oval:org.mitre.oval:def:8282 false
oval:org.mitre.oval:def:7631 false
oval:org.mitre.oval:def:6165 false
----------------------------------------------------
** finished evaluating OVAL definitions.
** saving OVAL results to results.xml.
** running OVAL Results xsl: xml\results_to_html.xsl.
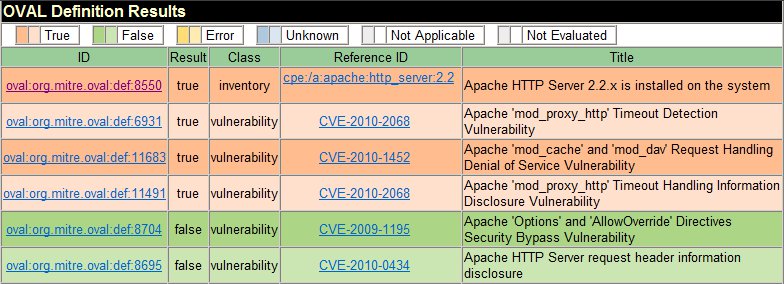
----------------------------------------------------For a more meaningful understanding of the result, the OVAL Interpreter outputs a results.html. Within this instance of the final report output from my Windows 7 OVAL check, one of the items returned was a positive check that my system was installed with the Apache HTTP server 2.2. This check was performed using the OVAL inventory class.
OVAL Interpreter Output: First Run Using Windows Inventory Class
Under the OVAL Definition Results category of the web-based results report, there is a link under the IDcolumn back to MITRE's site for each inventory item.
 The ID link for the Apache HTTP 2.2 server opened an internet page containing a list of extending
The ID link for the Apache HTTP 2.2 server opened an internet page containing a list of extending
definitions related to Apache vulnerabilities. I then downloaded the extended definitions and ran those, to
find the below vulnerabilities on my system.
OVAL Interpreter Output: Second Run Using Apache Vulnerability Class
Conclusion
OVAL is a welcomed standard that makes it more widely plausible to provide automated securityassessments. The standardized XML base for OVAL means that the same definitions and data can be
shared and used across platforms, technologies and tools. MITRE's OVAL Interpreter helps us understand
the implementation of OVAL standards and how new tools can be developed to use the standard.
However, OVAL is only a piece of the SCAP puzzle. Vendor tools that can implement many SCAP
components will be able to offer more robust products that can operate on a larger scope of organizational
security.
Appendices
Public OVAL Repositories
The OVAL Repositories are public. The information security community develops and and
contributes definitions to the OVAL repositories. OVAL has been funded by the U.S. Department of
Homeland Security and US-CERT. The Oval “content” repositories are a collection of XML
formatted system and application tests that have been written using the OVAL language.
The MITRE Corporation hosts the largest archive of OVAL definitions. Other participants hosting
OVAL content at the time of this writing are debian, IT Security Database, NIST, Novell, and
RedHat. Links to some of the repositories are:
contributes definitions to the OVAL repositories. OVAL has been funded by the U.S. Department of
Homeland Security and US-CERT. The Oval “content” repositories are a collection of XML
formatted system and application tests that have been written using the OVAL language.
The MITRE Corporation hosts the largest archive of OVAL definitions. Other participants hosting
OVAL content at the time of this writing are debian, IT Security Database, NIST, Novell, and
RedHat. Links to some of the repositories are:
- MITRE: http://oval.mitre.org/repository
- debian: http://www.debian.org/security/oval
- IT Security Database: http://www.itsecdb.com
- NIST: http://scap.nist.gov/content
- RedHat: http://www.redhat.com/oval
- debian: http://www.debian.org/security/oval
- IT Security Database: http://www.itsecdb.com
- NIST: http://scap.nist.gov/content
- RedHat: http://www.redhat.com/oval
References
Hansbury, Mathew. “Open Vulnerability and Assessment Language”. HS SEDI. Retrieved November 2010
from http://oval.mitre.org/oval/about/2010_ITSAC-OVAL_Tutorial.pdf
Martin, Robert A., “Security Patches Got You Running in Circles”. MITRE. Retrieved November 2010 from
http://oval.mitre.org/oval/documents/docs-04/security_patches_got_you_running_in_circles.html
Open Vulnerability and Assessment Language. http://oval.mitre.org . 2010.
P., Robert. “Closing the Circle of Compliance: SCAP, XCCDF, OVAL and ACR2 “.
https://www.acr2solutions.com. 2007.
Quin, Stephen. “Automated Security Measurement/FISMA Technical Control Automation”. Retrieved
November 2010 from http://oval.mitre.org/oval/documents/docs-08/oval_developer_day_slides.zip
MITRE. http://benchmarkdevelopment.mitre.org
Wikipedia. “Security Content Automation Protocol”. Retrieved November 2010 from
http://en.wikipedia.org/wiki/Security_Content_Automation_Protocol
from http://oval.mitre.org/oval/about/2010_ITSAC-OVAL_Tutorial.pdf
Martin, Robert A., “Security Patches Got You Running in Circles”. MITRE. Retrieved November 2010 from
http://oval.mitre.org/oval/documents/docs-04/security_patches_got_you_running_in_circles.html
Open Vulnerability and Assessment Language. http://oval.mitre.org . 2010.
P., Robert. “Closing the Circle of Compliance: SCAP, XCCDF, OVAL and ACR2 “.
https://www.acr2solutions.com. 2007.
Quin, Stephen. “Automated Security Measurement/FISMA Technical Control Automation”. Retrieved
November 2010 from http://oval.mitre.org/oval/documents/docs-08/oval_developer_day_slides.zip
MITRE. http://benchmarkdevelopment.mitre.org
Wikipedia. “Security Content Automation Protocol”. Retrieved November 2010 from
http://en.wikipedia.org/wiki/Security_Content_Automation_Protocol
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (0)