Browse All Articles > Using PowerShell to Delegate GPO permissions
Group Policy Delegation
Recently, I was tasked with delegating permissions for a specific group of administrators to a specific list of Group Policy Objects(GPO). A couple of things need to happen here for this to work.If you want the Administrators to be able to create new Group Policy Objects, you should add them to the Group Policy Creator Owners group as it is set up by default to be able to create new certificates as seen below:
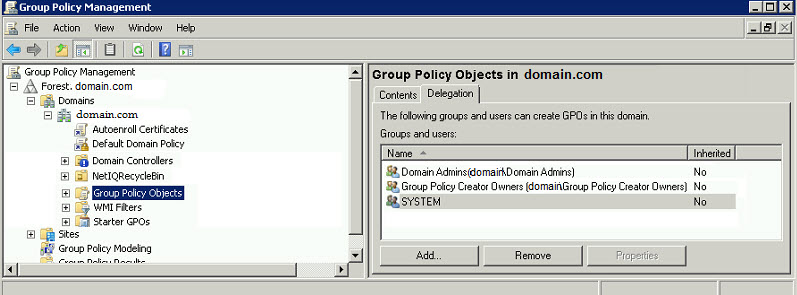 However, it may not have the necessary permissions to edit other Group Policy Objects.
However, it may not have the necessary permissions to edit other Group Policy Objects.
This is what a typical Group Policy Object looks like.
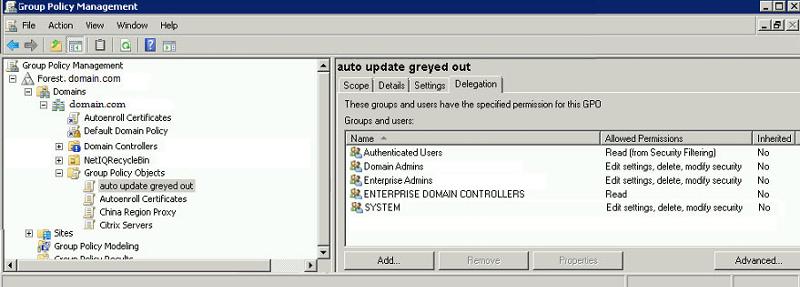 Authenticated Users have read access, Domain Admins, Enterprise Admins, and System all have Edit settings, delete, and modify security (basically full control) for the specific Group Policy Object. If the administrators you are working with are not a member of either the Domain Admins or the Enterprise Admins group, then it is most likely that they do not have permissions to edit any Group Policy Objects that they did not create.
Authenticated Users have read access, Domain Admins, Enterprise Admins, and System all have Edit settings, delete, and modify security (basically full control) for the specific Group Policy Object. If the administrators you are working with are not a member of either the Domain Admins or the Enterprise Admins group, then it is most likely that they do not have permissions to edit any Group Policy Objects that they did not create.
So, how do we fix this?
Well, you can go through each policy in the Group Policy Management console and add them manually, or, you can script it in PowerShell.
To script it in PowerShell, you will need to meet a couple of prerequisites:
1
You must use PowerShell from a Windows 2008 R2 server that is a domain controller or on a member server that has the Group Policy Management console installed, or you can run it from Windows 7 with the Remote Server Administration Tools installed.2
You have to import the Group Policy Module using the Import-Module cmdlet before you can use any of the Group Policy cmdlets.The cmdlet looks as follows:
Import-Module GroupPolicyNow the fun part.
If you are going to be granting rights to several administrators on the same Group Policy Objects, it is best if you create a security group, put all of the administrators in this group, and then assign the group the permissions. For the sake of this discussion, we will be using the following:
A security group called GPOAdministrators
We will be giving the highest level of access on the GPOs (edit, delete, modify security)
We will be applying the permissions on every GPO that start with "china"
I typically like to assign non-changing values to a variable first, just to make my code cleaner. We know the group name and the security level so lets set them to some variables that we can use in the code:
$grp = "GPOAdministrators"
$level = "GpoEditDeleteModifySecurity"$gpos = get-gpo -All | where {$_.DisplayName -like "china*"}foreach ($gpo in $gpos)
{
$gpname = $gpo.DisplayName
set-GPPermissions -Name $gpname -permissionlevel $level -TargetName $grp -targettype Group
}Import-Module GroupPolicy
$grp = "GPOAdministrators"
$level = "GpoEditDeleteModifySecurity"
$gpos = get-gpo -All | where {$_.DisplayName -like "china*"}
foreach ($gpo in $gpos)
{
$gpname = $gpo.DisplayName
set-GPPermissions -Name $gpname -permissionlevel $level -TargetName $grp -targettype Group
}That should take care of it for you. If you want to learn more about the other Group Policy cmdlets, you can simply do get-help in PowerShell. For instance, to see a detailed help about the set-GPPermissions, you would type the following:
get-help set-GPPermissions -fullHave a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (0)