Browse All Articles > RADIUS authentication for Cisco switches using w2k8R2 NPS
When replacing some switches recently I started playing with the idea of having admins authenticate with their domain accounts instead of having local users on all switches all over the place.
Since I allready had an w2k8R2 NPS running for my access points I thought I'd use that. Though there are plenty of examples to find, none of them worked for my specific setup (I think it is the R2). So what better place there is to put one but here at EE.
Here we go.
First, if you haven't allready done so, install NPS on your server:
-Start server manager, right-click roles and choose 'add role'.
-In the Server Roles screen, tick 'Network Policy and Access Server'
![Select role]() (Here it's allready installed)
(Here it's allready installed)
-Now do the 'next', 'install', 'finish' part and presto! NPS is installed.
Now we need to configure the NPS so the switch(es) will be able to authenticate against it:
Radius client
-Start NPS: Start->Admin Tools->Network Policy Server
-On the left side, go to: RADIUS Clients and Servers->RADIUS Clients
-Right click on 'RADIUS Clients' and select 'new'
![New client]()
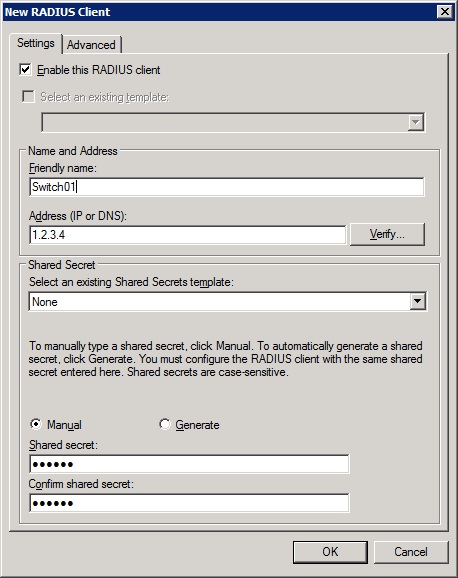
-Under the settings tab, choose a friendly name for the client so you can identify it.
-Enter the ip address of the switch.
-Enter or generate a shared secret.
![New client 2]()
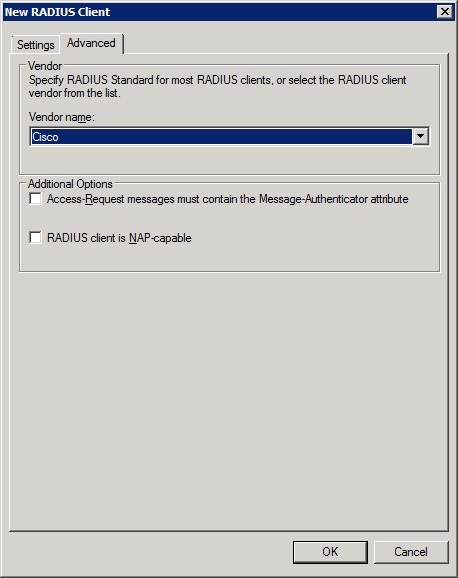
-Go to the Advanced tab and change the vendor name to 'Cisco'
![New client 3]()
-Click ok and the client is finished.
Connection Request Policy
-On the left side of NPS, go to: Policies->Connection Reuquest Policies
-Right click on 'Connection Reuquest Policies' and select 'new'
-Enter a name for the policy so you can identify it.
-Leave the type setting below to 'Unspecified'
![New policy]()
-Press next.
Now we need to add a condition. Because (I think) a connection request should always be possible, we'll just add a day and time restriction here and allow always.
-Press add and scroll down to 'day and time restrictions'. Click 'add' again.
![condition]()
-Now click on 'all' and tick 'Permitted'
![condition2]()
-Press 'ok', 'next', 'next', 'next', 'next'. The policy should look something like:
![policy finished]()
Network Policy
-On the left side of NPS, go to: Policies->Network Policies
-Right click on 'Network Policies' and select 'new'
-Enter a name for the policy so you can identify it.
-Leave the type setting below to 'Unspecified'
![Network policy]()
-Press 'next'
Now we're going to add a condition that specifies who is able to log on to the switches. In my case I chose the 'Domain Administrators' group. But you can always create a Cisco admins group or whatever you would like :)
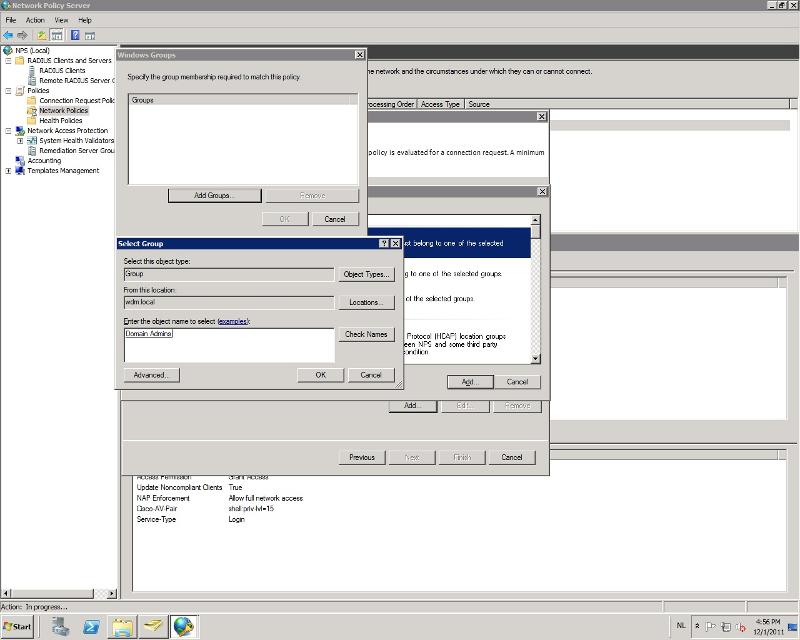
-Click 'add', select 'Windows Groups' and clieck 'add'
![NWP condition]()
-Click 'Add Groups' and select the group you want to use
![adding]()
-Click 'ok', 'ok', 'next'
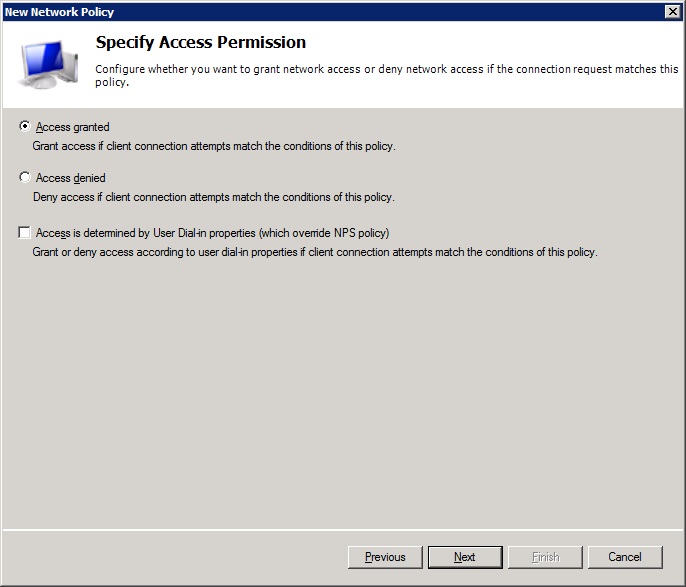
-The next screen (access permission) we leave as is because we want access
![access]()
-Press 'next'
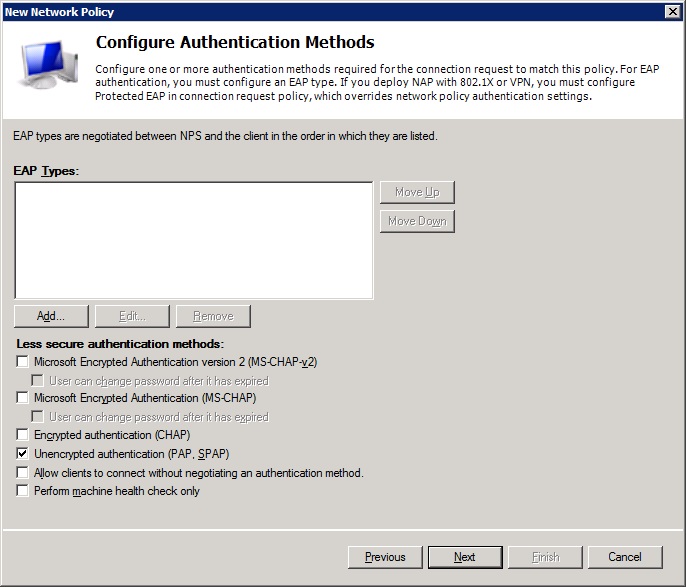
-In authentication methods, untick all methods except 'Unencrypted authentication (PAP, SPAP)'.
![authentication]()
I know, it's not secure and not ideal. But at the moment it's the only supported way.
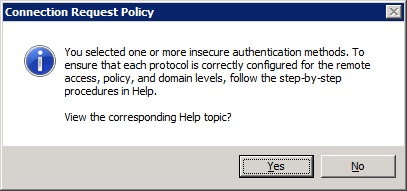
-So let's click 'next' and just say no to the question if you want to see any help topics
![help]()
-We don't need to configure any constraints, so press 'next'
![next]()
-Here at settings we need to make some changes. The attributes shown under: RADIUS attributes->Standard, need to be removed (that's the Framed-Protocol and Service-Type).
![remove]()
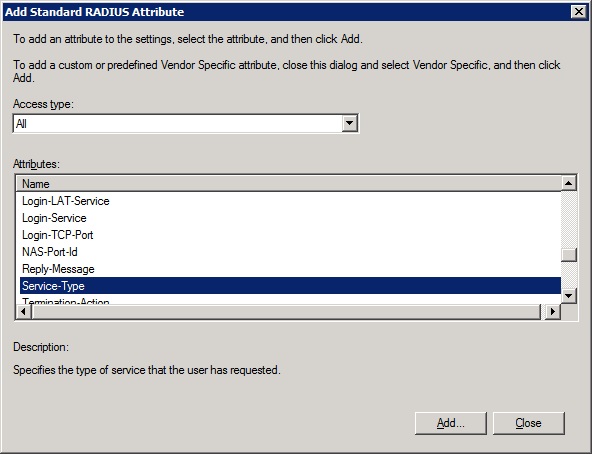
-Now we need to add an attribute: click add and find the attribute 'Service-Type'.
![service-type]()
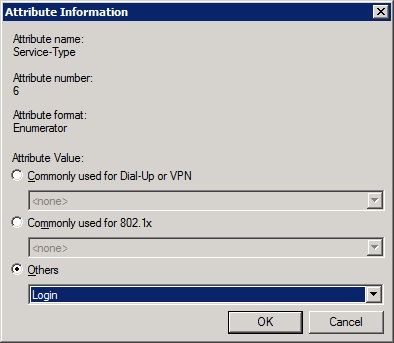
-Click 'add', tick 'others' and select 'Login'
![login]()
-Click 'ok' and 'close'
Now, because I'm lazy, I want to get to priviledged mode automatically when I log in. You don't need to do that but I'll show it anyway.
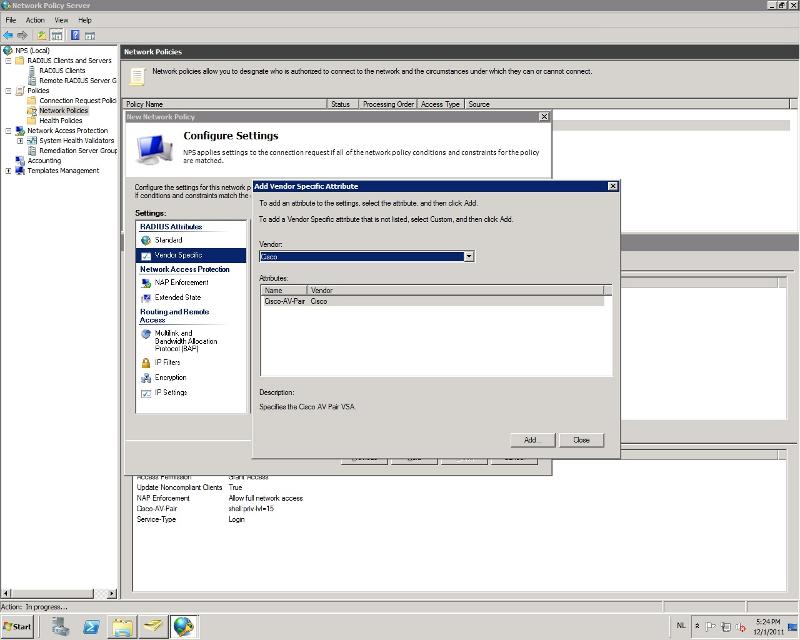
-Go to: RADIUS Attributes->Vendor Specific and press 'Add'
-Select Cisco as vendor, select Cisco-AV-Pair and click on 'add'
![vendor]()
-Click 'add' again and enter the following in the attribute information box: shell:priv-lvl=15
-Click 'ok', 'ok', 'close' and 'next'
-Now you can click 'finish' for the policy
![finish]()
That was the hard part ;) Now to set up the switch to use the RADIUS server for authentication with a fallback to the local user in case the server is unavailable.
Here we go:
conf t
aaa new-model
aaa authentication login default group radius local
aaa authorization exec default group radius if-authenticated
aaa authorization network default group radius if-authenticated
radius-server host 1.2.3.4 auth-port 1812 acct-port 1813 key ********
line vty 0 4
logging synchronous
login authentication default
After that you can use your domain account to log on (as long as you are in the correct group :)
That's all there is to it.
Since I allready had an w2k8R2 NPS running for my access points I thought I'd use that. Though there are plenty of examples to find, none of them worked for my specific setup (I think it is the R2). So what better place there is to put one but here at EE.
Here we go.
First, if you haven't allready done so, install NPS on your server:
-Start server manager, right-click roles and choose 'add role'.
-In the Server Roles screen, tick 'Network Policy and Access Server'
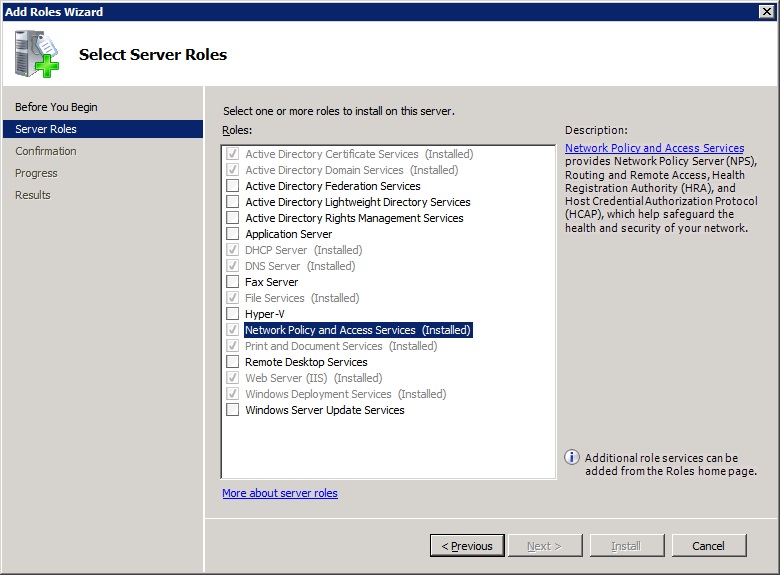 (Here it's allready installed)
(Here it's allready installed)
-Now do the 'next', 'install', 'finish' part and presto! NPS is installed.
Now we need to configure the NPS so the switch(es) will be able to authenticate against it:
Radius client
-Start NPS: Start->Admin Tools->Network Policy Server
-On the left side, go to: RADIUS Clients and Servers->RADIUS Clients
-Right click on 'RADIUS Clients' and select 'new'
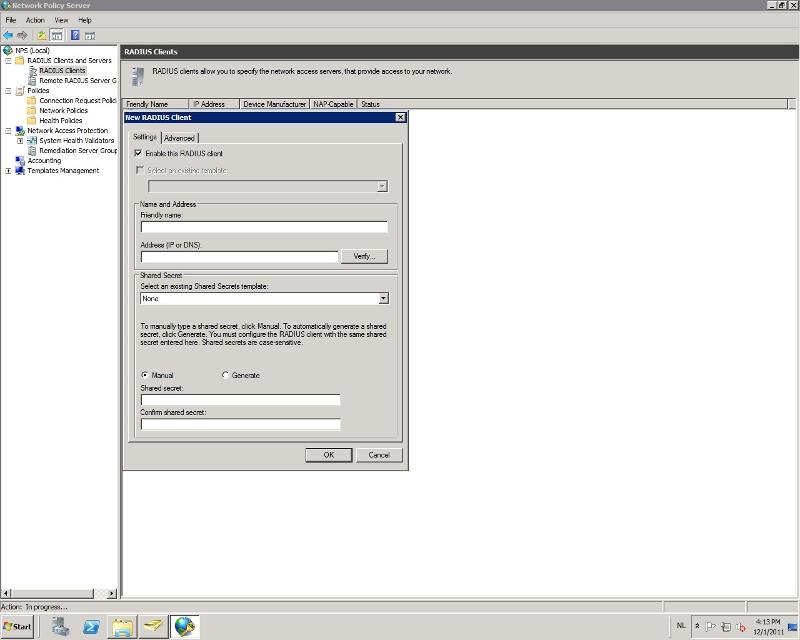
-Under the settings tab, choose a friendly name for the client so you can identify it.
-Enter the ip address of the switch.
-Enter or generate a shared secret.
-Go to the Advanced tab and change the vendor name to 'Cisco'
-Click ok and the client is finished.
Connection Request Policy
-On the left side of NPS, go to: Policies->Connection Reuquest Policies
-Right click on 'Connection Reuquest Policies' and select 'new'
-Enter a name for the policy so you can identify it.
-Leave the type setting below to 'Unspecified'
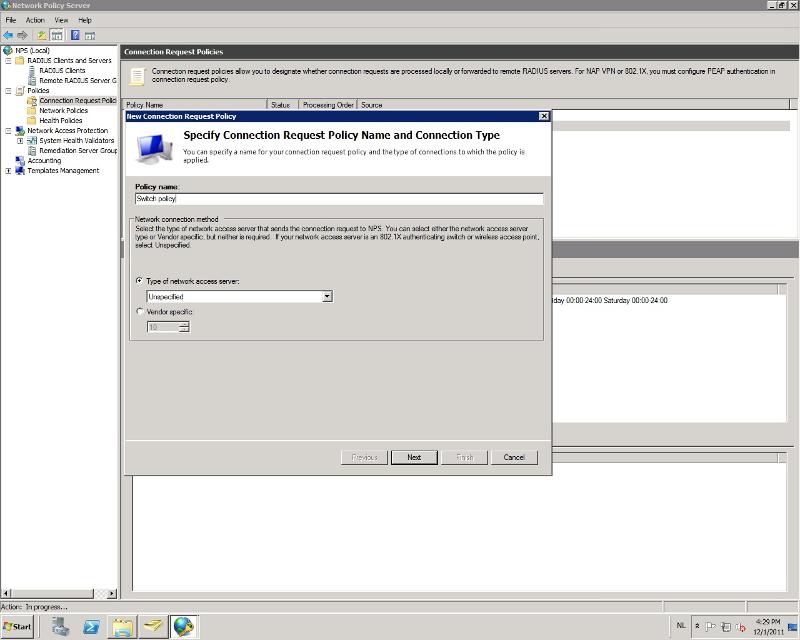
-Press next.
Now we need to add a condition. Because (I think) a connection request should always be possible, we'll just add a day and time restriction here and allow always.
-Press add and scroll down to 'day and time restrictions'. Click 'add' again.
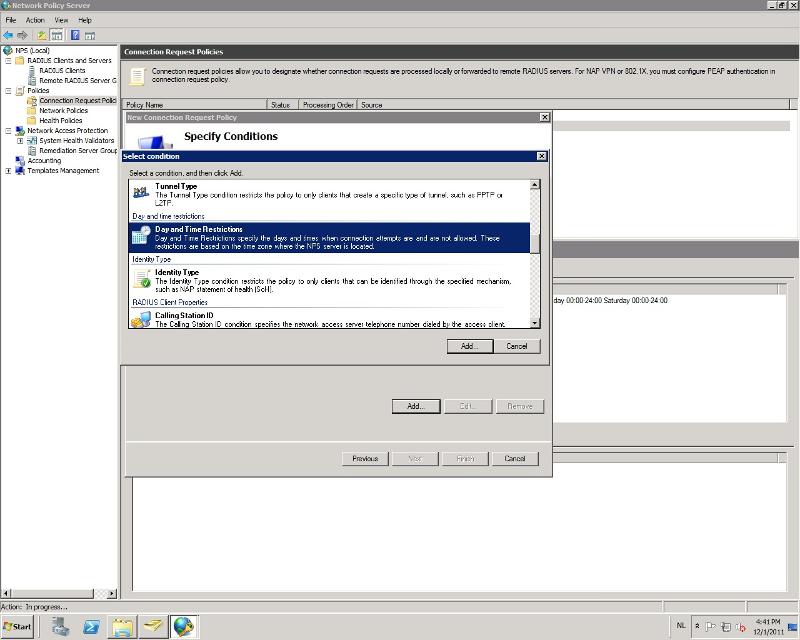
-Now click on 'all' and tick 'Permitted'

-Press 'ok', 'next', 'next', 'next', 'next'. The policy should look something like:

Network Policy
-On the left side of NPS, go to: Policies->Network Policies
-Right click on 'Network Policies' and select 'new'
-Enter a name for the policy so you can identify it.
-Leave the type setting below to 'Unspecified'
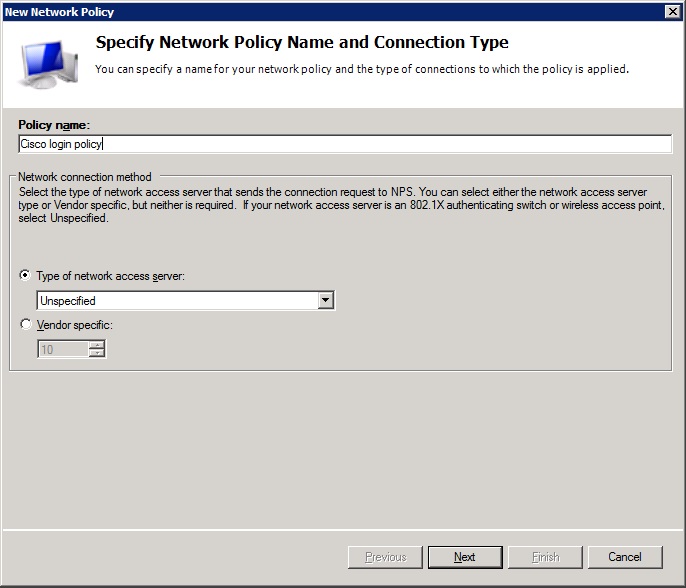
-Press 'next'
Now we're going to add a condition that specifies who is able to log on to the switches. In my case I chose the 'Domain Administrators' group. But you can always create a Cisco admins group or whatever you would like :)
-Click 'add', select 'Windows Groups' and clieck 'add'
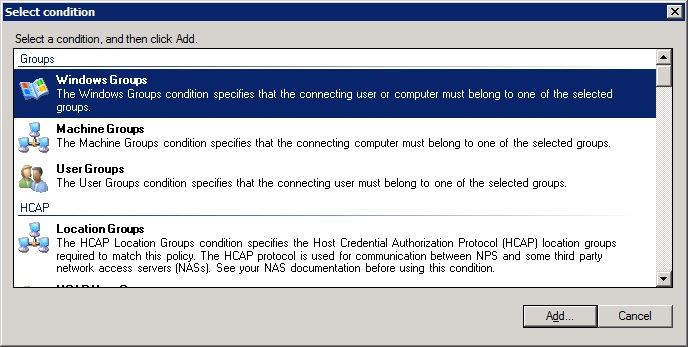
-Click 'Add Groups' and select the group you want to use
-Click 'ok', 'ok', 'next'
-The next screen (access permission) we leave as is because we want access
-Press 'next'
-In authentication methods, untick all methods except 'Unencrypted authentication (PAP, SPAP)'.
I know, it's not secure and not ideal. But at the moment it's the only supported way.
-So let's click 'next' and just say no to the question if you want to see any help topics
-We don't need to configure any constraints, so press 'next'
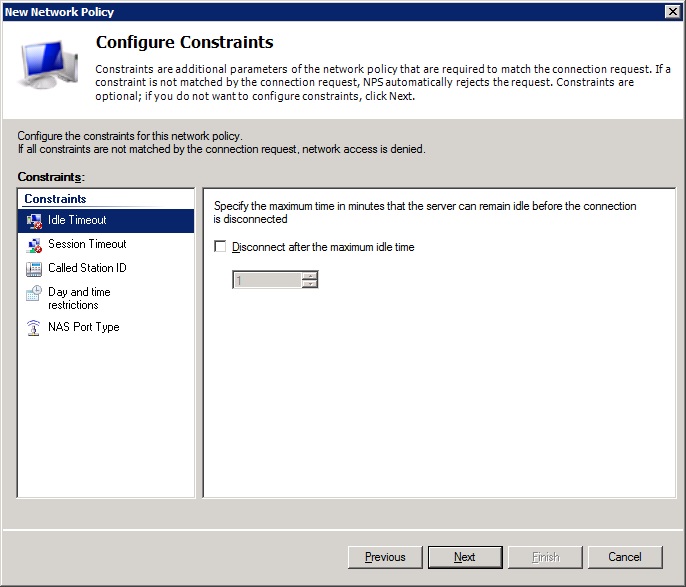
-Here at settings we need to make some changes. The attributes shown under: RADIUS attributes->Standard, need to be removed (that's the Framed-Protocol and Service-Type).
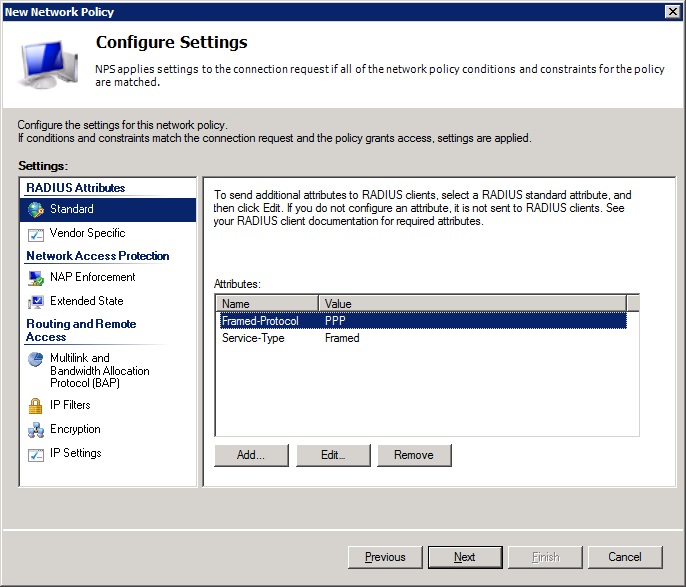
-Now we need to add an attribute: click add and find the attribute 'Service-Type'.
-Click 'add', tick 'others' and select 'Login'
-Click 'ok' and 'close'
Now, because I'm lazy, I want to get to priviledged mode automatically when I log in. You don't need to do that but I'll show it anyway.
-Go to: RADIUS Attributes->Vendor Specific and press 'Add'
-Select Cisco as vendor, select Cisco-AV-Pair and click on 'add'
-Click 'add' again and enter the following in the attribute information box: shell:priv-lvl=15
-Click 'ok', 'ok', 'close' and 'next'
-Now you can click 'finish' for the policy
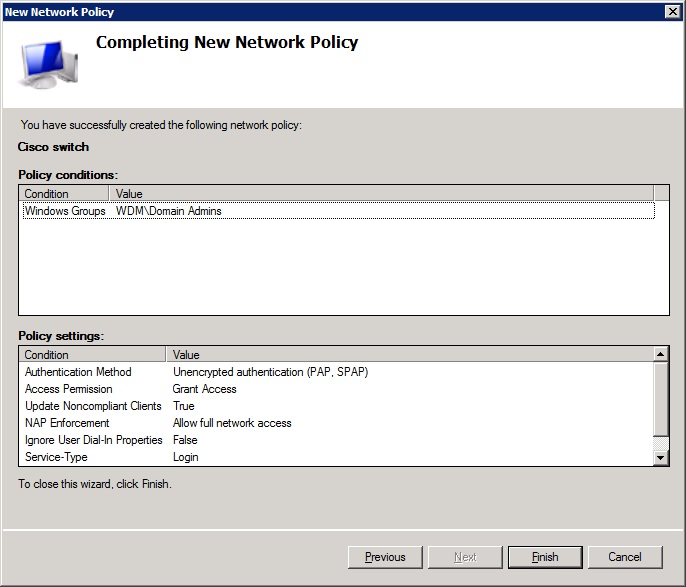
That was the hard part ;) Now to set up the switch to use the RADIUS server for authentication with a fallback to the local user in case the server is unavailable.
Here we go:
conf t
aaa new-model
aaa authentication login default group radius local
aaa authorization exec default group radius if-authenticated
aaa authorization network default group radius if-authenticated
radius-server host 1.2.3.4 auth-port 1812 acct-port 1813 key ********
line vty 0 4
logging synchronous
login authentication default
After that you can use your domain account to log on (as long as you are in the correct group :)
That's all there is to it.
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (12)
Commented:
Author
Commented:Thx mate :)
Commented:
Commented:
Commented:
View More