HOW TO: Fix Error code: ERR_CONNECTION_CLOSED when connecting to VMware vSphere Data Protection 5.x and 6.0.x using current versions of Internet Explorer, Chrome and Firefox
EE Fellow, MVE, Expert of the Year 2021,2017-11, Scribe 2016-2012, Author of the Year 2018-6,2013-2012 VMware vExpert Pro, vExpert 2022-2011
Published:
Browse All Articles > HOW TO: Fix Error code: ERR_CONNECTION_CLOSED when connecting to VMware vSphere Data Protection 5.x and 6.0.x using current ver…
Accessing the VMware vSphere Data Protection 5.x and 6.0.x appliance management or file level restore (FLR) portal using current versions of Internet Explorer, Chrome and Firefox will fail, with a This webpage is not available, Error code: ERR_CONNECTION_CLOSED or Secure Connection Failed.
This article will show you in 6 easy steps how to fix this issue.
The majority of VMware vSphere Data Protection functions are performed via the vSphere Web Client connected to VMware vSphere vCenter Server. However on occasions, there are requirements to access the VDP appliance directly, here are some examples
![firefox-Problem-loading-page.png]() This is the web page received with an un-patched VDP 5.8 or 6.0.x, using Firefox. Firefox, removed DSA ciphers from release 37. This improved certificate and TLS communication security by removing support for DSA.
This is the web page received with an un-patched VDP 5.8 or 6.0.x, using Firefox. Firefox, removed DSA ciphers from release 37. This improved certificate and TLS communication security by removing support for DSA.
Source: https://www.mozilla.org/en-US/firefox/37.0/releasenotes/
![vdp2_8543_vdp-configure-is-not-avail.png]() This is the web page received with an un-patched VDP 5.8 or 6.0.x, using Google Chrome. Chrome removed DSA ciphers from release 40.0.2215.115m: ef2116d Remove DSA-based cipher suites and client auth.
This is the web page received with an un-patched VDP 5.8 or 6.0.x, using Google Chrome. Chrome removed DSA ciphers from release 40.0.2215.115m: ef2116d Remove DSA-based cipher suites and client auth.
Source: https://code.google.com/p/chromium/issues/detail?id=396787
VMware vSphere Data Protection (VDP) 5.x and 6.0.x are both affected with this issue. VMware vSphere Data Protection 6.1 is not affected by this issue, and has been fixed. See the VMware vSphere Data Protection (VDP) 6.0.1 Release Notes.
You could opt for completing an upgrade from VMware vSphere Data Protection 5.x and 6.0.x to VMware vSphere Data Protection 6.1, but I think you'll agree, that the following 6 steps are much quicker.
1. Download the HotFix from VMware
Using the browser of your choice download the Hotfix - 2111900_VDPHotfix.SHA2.sh.zip from http://kb.vmware.com/selfservice/viewAttachment.do?attachID=2111900_VDPHotfix.SHA2.sh.zip&documentID=2111900
2. Copy the HotFix to the VDP appliance via WinSCP
![WinSCP-VDP.jpg]() Using WinSCP, copy the Hotfix from your workstation to the VDP appliance, to the /tmp directory.
Using WinSCP, copy the Hotfix from your workstation to the VDP appliance, to the /tmp directory.
3. Connect via SSH (PuTTY) to the VDP Appliance.
![ssh-vdp.jpg]() SSH using PuTTY to the VDP appliance. You may need to use the admin account, and not the root username.
SSH using PuTTY to the VDP appliance. You may need to use the admin account, and not the root username.
![ssh-vdp-tmp.jpg]() Change to the /tmp folder, by typing
Change to the /tmp folder, by typing
![image.gif]()
![image.gif]() 4. Assume the root role.
4. Assume the root role.
![ssh-vdp-tmp-sudo1.jpg]() If you have logged in remotely via SSH, you will need to "su" to root. Type
If you have logged in remotely via SSH, you will need to "su" to root. Type
![image.gif]()
![image.gif]()
![ssh-vdp-tmp-sudo2.jpg]()
followed by the password at the command prompt. You will notice the prompt changes from a > to a #, when you are "rooted."
5. Unzip the HotFix
![ssh-vdp-tmp-dir.jpg]() Check the hotfix file is present using
Check the hotfix file is present using
![image.gif]()
![image.gif]()
![ssh-vdp-tmp-unzip.jpg]() The zip file needs extracting using the unzip command, type
The zip file needs extracting using the unzip command, type
![image.gif]()
![image.gif]()
![ssh-vdp-tmp-folder1.jpg]() Then change directory to the folder 2111900_VDPHotfix.SHA2.sh,
Then change directory to the folder 2111900_VDPHotfix.SHA2.sh, by typing
![image.gif]()
![image.gif]() 6. Change permissions and execute the HotFix script
6. Change permissions and execute the HotFix script
![ssh-vdp-chmod.jpg]() Type
Type
![image.gif]()
![image.gif]() to change permissions on the Hotfix script, so it can be executed and run to patch the server.
to change permissions on the Hotfix script, so it can be executed and run to patch the server.
![ssh-vdp-patch.jpg]() Type
Type
![image.gif]()
![image.gif]() to execute and patch the server. select y(es) to continue and patch the server. The VDP appliance will be patched and fixed.
to execute and patch the server. select y(es) to continue and patch the server. The VDP appliance will be patched and fixed.
![ssh-vdp-tmp-patch.png]() The Hotfix has been applied successfully. Check by going to the VDP URL:
The Hotfix has been applied successfully. Check by going to the VDP URL:
![vdp-configure_.png]() Congratulations; you have successfully patched and fixed your VMware vSphere Data Protection 5.x and 6.0.x appliance for use with current versions of Internet Explorer, Chrome and Firefox.
Congratulations; you have successfully patched and fixed your VMware vSphere Data Protection 5.x and 6.0.x appliance for use with current versions of Internet Explorer, Chrome and Firefox.
The majority of VMware vSphere Data Protection functions are performed via the vSphere Web Client connected to VMware vSphere vCenter Server. However on occasions, there are requirements to access the VDP appliance directly, here are some examples
- VDP troubleshooting - e.g. checking VDP logs and creating checkpoints.
- File level restore (FLR) - e.g. restoring files from individual virtual machine backups.
- Emergency Restore e.g. if vCenter Server should fail, you need to access VDP directly to restore virtual machines.
 This is the web page received with an un-patched VDP 5.8 or 6.0.x, using Firefox. Firefox, removed DSA ciphers from release 37. This improved certificate and TLS communication security by removing support for DSA.
This is the web page received with an un-patched VDP 5.8 or 6.0.x, using Firefox. Firefox, removed DSA ciphers from release 37. This improved certificate and TLS communication security by removing support for DSA.
Source: https://www.mozilla.org/en
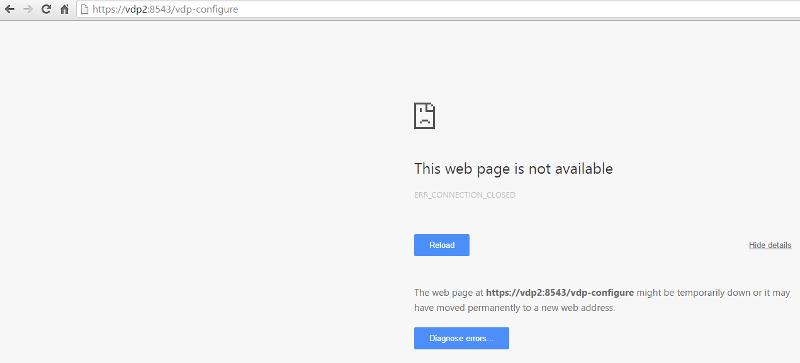 This is the web page received with an un-patched VDP 5.8 or 6.0.x, using Google Chrome. Chrome removed DSA ciphers from release 40.0.2215.115m: ef2116d Remove DSA-based cipher suites and client auth.
This is the web page received with an un-patched VDP 5.8 or 6.0.x, using Google Chrome. Chrome removed DSA ciphers from release 40.0.2215.115m: ef2116d Remove DSA-based cipher suites and client auth.
Source: https://code.google.com/p/
VMware vSphere Data Protection (VDP) 5.x and 6.0.x are both affected with this issue. VMware vSphere Data Protection 6.1 is not affected by this issue, and has been fixed. See the VMware vSphere Data Protection (VDP) 6.0.1 Release Notes.
You could opt for completing an upgrade from VMware vSphere Data Protection 5.x and 6.0.x to VMware vSphere Data Protection 6.1, but I think you'll agree, that the following 6 steps are much quicker.
1. Download the HotFix from VMware
Using the browser of your choice download the Hotfix - 2111900_VDPHotfix.SHA2.sh.
2. Copy the HotFix to the VDP appliance via WinSCP
 Using WinSCP, copy the Hotfix from your workstation to the VDP appliance, to the /tmp directory.
Using WinSCP, copy the Hotfix from your workstation to the VDP appliance, to the /tmp directory.
3. Connect via SSH (PuTTY) to the VDP Appliance.
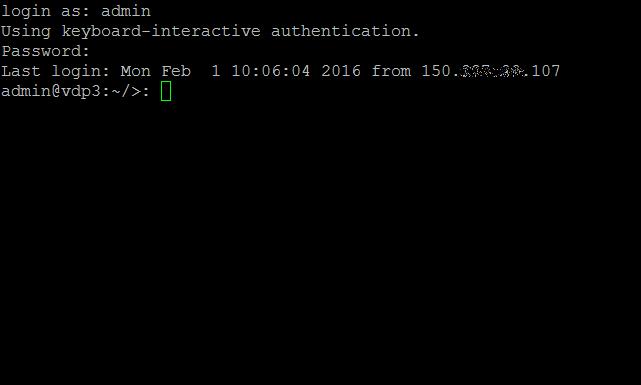 SSH using PuTTY to the VDP appliance. You may need to use the admin account, and not the root username.
SSH using PuTTY to the VDP appliance. You may need to use the admin account, and not the root username.
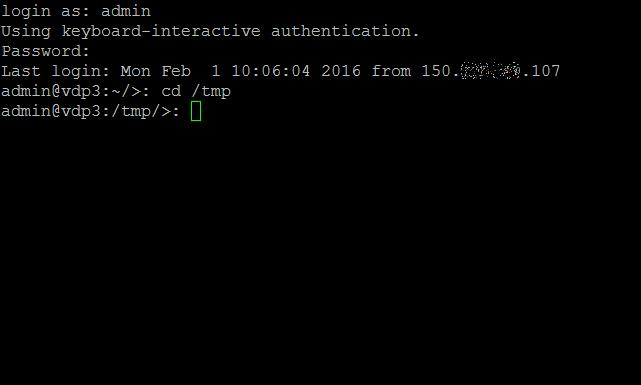 Change to the /tmp folder, by typing
Change to the /tmp folder, by typing
cd /tmp
 4. Assume the root role.
4. Assume the root role.
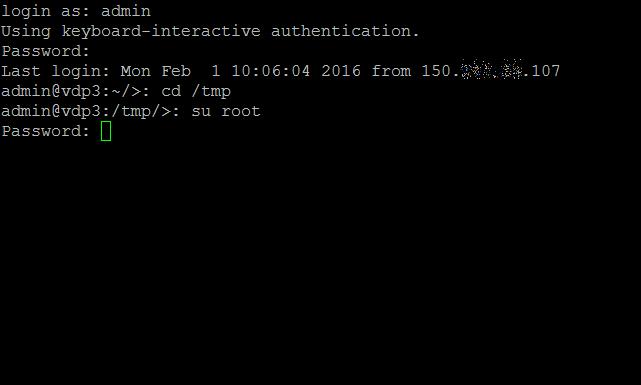 If you have logged in remotely via SSH, you will need to "su" to root. Type
If you have logged in remotely via SSH, you will need to "su" to root. Type
su root

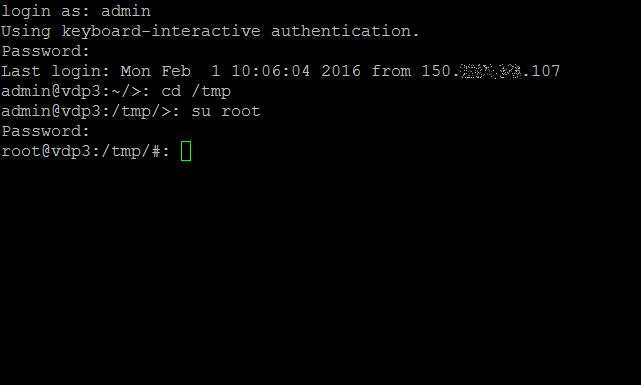
followed by the password at the command prompt. You will notice the prompt changes from a > to a #, when you are "rooted."
5. Unzip the HotFix
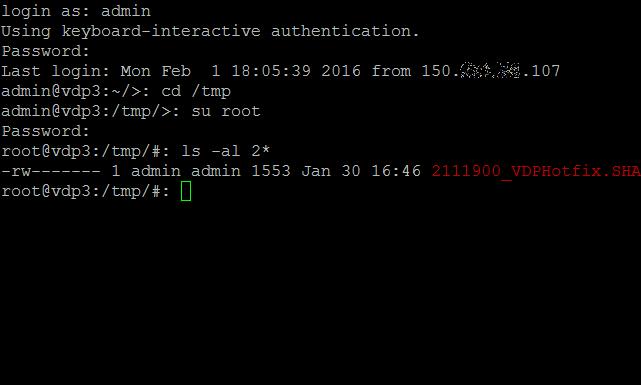 Check the hotfix file is present using
Check the hotfix file is present using
-ls -al 2111900_VDPHotfix.SHA2.sh.zip

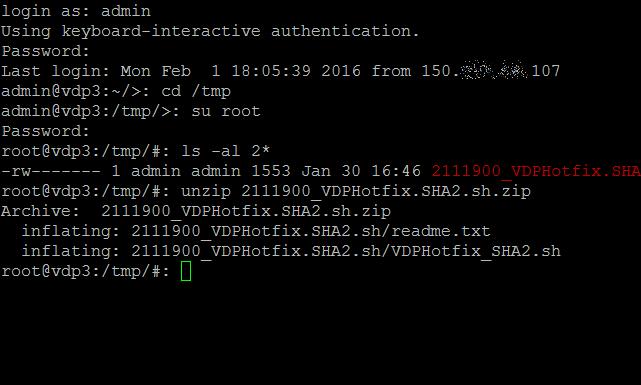 The zip file needs extracting using the unzip command, type
The zip file needs extracting using the unzip command, type
-ls -al 2111900_VDPHotfix.SHA2.sh.zip

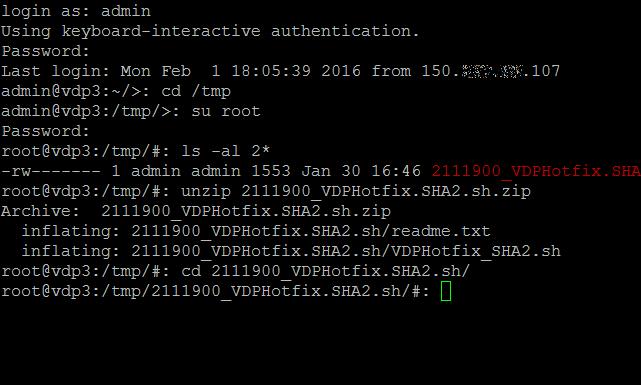 Then change directory to the folder 2111900_VDPHotfix.SHA2.sh,
Then change directory to the folder 2111900_VDPHotfix.SHA2.sh,-cd 2111900_VDPHotfix.SHA2.s
 6. Change permissions and execute the HotFix script
6. Change permissions and execute the HotFix script
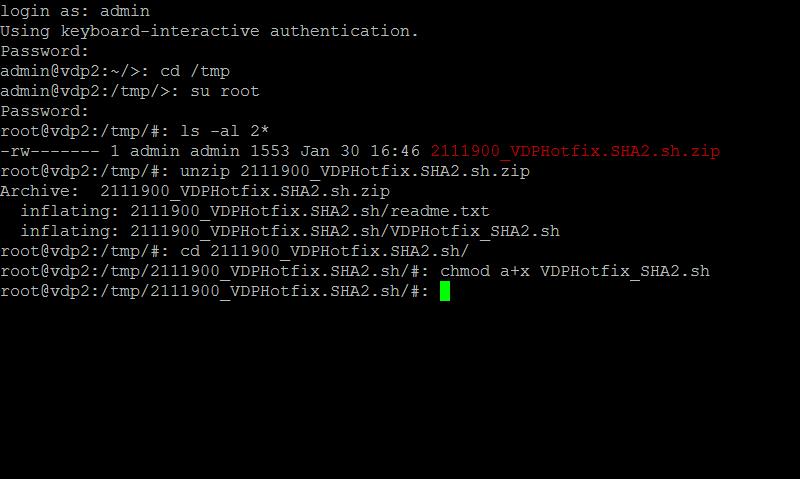 Type
Type
chmod a+x VDPHotfix_SHA2.sh
 to change permissions on the Hotfix script, so it can be executed and run to patch the server.
to change permissions on the Hotfix script, so it can be executed and run to patch the server.
 Type
Type
./VDPHotfix_SHA2.sh
 to execute and patch the server. select y(es) to continue and patch the server. The VDP appliance will be patched and fixed.
to execute and patch the server. select y(es) to continue and patch the server. The VDP appliance will be patched and fixed.
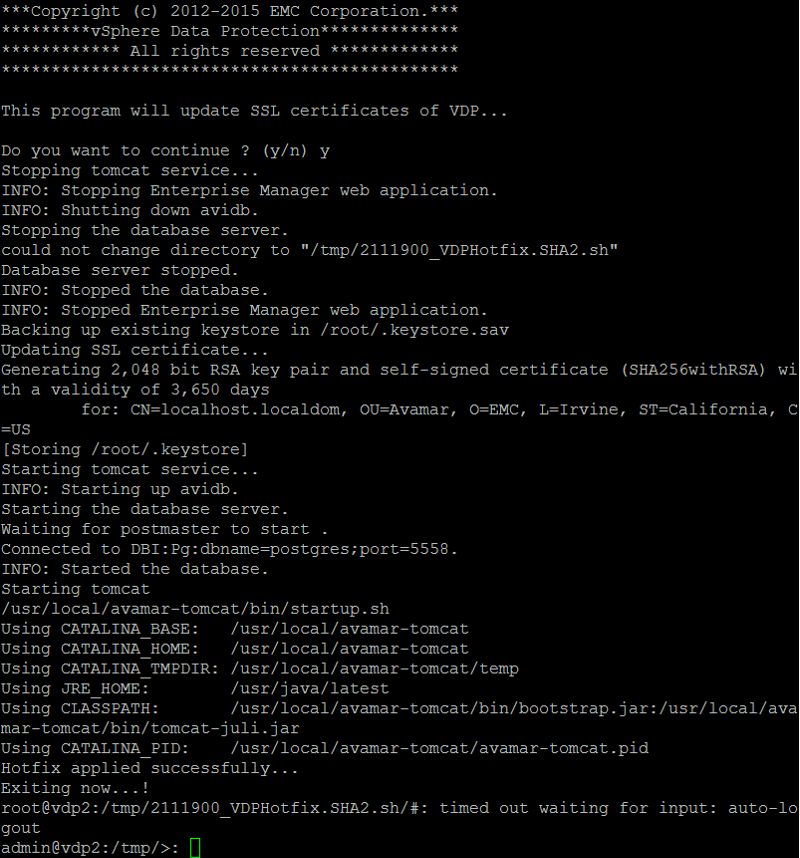 The Hotfix has been applied successfully. Check by going to the VDP URL:
The Hotfix has been applied successfully. Check by going to the VDP URL:
https://:8543/vdp-configure Congratulations; you have successfully patched and fixed your VMware vSphere Data Protection 5.x and 6.0.x appliance for use with current versions of Internet Explorer, Chrome and Firefox.
Congratulations; you have successfully patched and fixed your VMware vSphere Data Protection 5.x and 6.0.x appliance for use with current versions of Internet Explorer, Chrome and Firefox.
Have a question about something in this article? You can receive help directly from the article author. Sign up for a free trial to get started.


Comments (0)