https://www.ru.nl/publish/pages/909282/advisory.pdf
Sweet, isn't it? Now go check your drives... all of them.
Solid State Disks (SSDs) often implement hardware full-disk encryption in a way known as Self-Encrypting Drives
(SEDs). Several implementations of SEDs have been analysed by reverse engineering their firmware. Many have security vulnerabilities that allow for full recovery of the data without knowledge of any secret when you have physical access to the drive.
BitLocker, bundled with Microsoft Windows, relies exclusively on hardware full-disk encryption if the drive indicates support for it. Thus, for these drives, data protected by BitLocker is also compromised.
Sweet, isn't it? Now go check your drives... all of them.
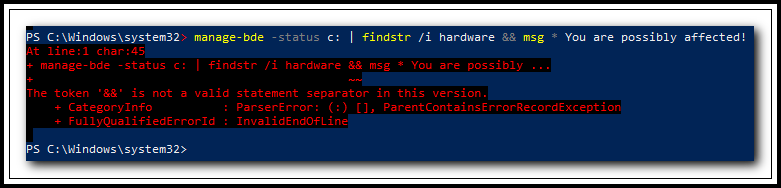
manage-bde -status c: | findstr /i hardware && msg * You are possibly affected!
Hi McKnife,
I assume that's a powershell command? Can you explain what it does and can I run it on my two SSD's without any fear of it doing something un-toward? I tend to shy away from powershell commands unless I'm assured that they won't harm anything. What does that one do exactly?
Sweet, isn't it? Now go check your drives... all of them.
manage-bde -status c: | findstr /i hardware && msg * You are possibly affected!
I assume that's a powershell command? Can you explain what it does and can I run it on my two SSD's without any fear of it doing something un-toward? I tend to shy away from powershell commands unless I'm assured that they won't harm anything. What does that one do exactly?
Hi.
It's batch code and it does no harm. The command has a look at the status of the encryption and if the status indicates that hardware encryption is in use, it throws a popup that tells you "you are possibly affected!". "Possibly", because not all hardware models are compromised, in fact, the researchers are only beginning to analyze how many models are affected. Some Samsung drives (the wide-spread models 840 and 850 EVO, for example) are confirmed to be affected as well as some drives made by Crucial.
However, although the researchers write that bitlocker would choose hw encryption whenever the drive offers it, please note that many drives need to be worked on with a manufacturer tool (for example samsung magician) to reveal those hw encryption capabilities to the OS. If you omit this, software encryption will be used, instead.
In other words: not many people will have done that because not many people know and those that don't know, are lucky in this case ;-)
It's batch code and it does no harm. The command has a look at the status of the encryption and if the status indicates that hardware encryption is in use, it throws a popup that tells you "you are possibly affected!". "Possibly", because not all hardware models are compromised, in fact, the researchers are only beginning to analyze how many models are affected. Some Samsung drives (the wide-spread models 840 and 850 EVO, for example) are confirmed to be affected as well as some drives made by Crucial.
However, although the researchers write that bitlocker would choose hw encryption whenever the drive offers it, please note that many drives need to be worked on with a manufacturer tool (for example samsung magician) to reveal those hw encryption capabilities to the OS. If you omit this, software encryption will be used, instead.
In other words: not many people will have done that because not many people know and those that don't know, are lucky in this case ;-)
Thanks, McKnife. I ran the command in an elevated Powershell on my C: drive which is an SSD and got the following result?
![PS-Command-Fail.png]()
Any ideas why it didn't work for me?
- Windows 10 Pro x64 (Version 1803)
- Version 10.0.17134 OS Build 17134.376
- PowerShell Version 5.1.17134.1
- Motherboard Intel Corporation DH67CL (LGA1155)
- 476GB Samsung SSD 850 PRO 512GB (SATA (SSD))
Any ideas why it didn't work for me?
Andrew, it's batch code, not powershell code. Run it on an elevated command prompt. If you get a popup, verify your drive model. If the output is empty, you are safe to go.
[batch code can usually be run on the powershell, too, but not all batch code and the operator "&&" ("continue if last result is success") is unknown to powershell - that's why you see an error]
[batch code can usually be run on the powershell, too, but not all batch code and the operator "&&" ("continue if last result is success") is unknown to powershell - that's why you see an error]
Andrew, it's batch code, not powershell code.Doh! <blush>
Run it on an elevated command prompt. If you get a popup, verify your drive model. If the output is empty, you are safe to go.Cool! I ran it on both my SSD drives and no output, so I guess I'm safe :-)
Many thanks for your help McKnife. Very much appreciated.
Andrew
Recommended Posts
Exchange Server Roadmap Update.
MS have moved the release date for the next version of Exchange Server to the second half of 2025.
It requires Server and CAL licenses and will be accessible only to customers with Software Assurance,
https://techcommunity.microsoft.com/t5/exchange-team-blog/exchange-server-roadmap-update/ba-p/3421389
MS have moved the release date for the next version of Exchange Server to the second half of 2025.
It requires Server and CAL licenses and will be accessible only to customers with Software Assurance,
https://techcommunity.microsoft.com/t5/exchange-team-blog/exchange-server-roadmap-update/ba-p/3421389
This is almost two years old and so far, no updates... am I missing something?
The detailed schedule for the virtual Access DevCon on April 18+19 is now available on the conference website.
https://www.donkarl.com/devcon
https://www.donkarl.com/devcon
Latest edition of Access News is available: https://www.youtube.com/watch?v=Taz6xjbgYDM
Keep in touch with Experts Exchange
Tech news and trends delivered to your inbox every month
Experts Exchange
The Original Tech Community
© 1996-2024 Experts Exchange, LLC. All rights reserved. Covered by US Patent.
© 1996-2024 Experts Exchange, LLC. All rights reserved. Covered by US Patent.





