Account lockout policy not applied
I know this has been asked many times but heres my go :)
Im getting this in the server performace report evey night, sometimes more attemps.
 Here is the GP result
Here is the GP result
I have been testing by deliberately logging with wrong passwords and after 11 wrong passwords I can still log in with the correct one?
A lot info I know but it seems to be required from other threads i've read.
Thanks all :)
Im getting this in the server performace report evey night, sometimes more attemps.
Security
529
01/06/2010 17:09
1,124 *
Logon Failure:
Reason:
Unknown user name or bad password
User Name:
administrator
Domain:
MYDOMAIN
Logon Type:
10
Logon Process:
User32
Authentication Package:
Negotiate
Workstation Name:
MYDOMAIN-SERVER
Caller User Name:
MYDOMAIN-SERVER$
Caller Domain:
MYDOMAIN
Caller Logon ID:
(0x0,0x3E7)
Caller Process ID:
8116
Transited Services:
-
Source Network Address:
24.101.10.276
Source Port:
30880 Here is the GP result
Here is the GP result Value: 1, 0, 0, 0
State: Enabled
GPO: Default Domain Policy
KeyName: Software\Policies\Microsoft\Windows\WindowsUpdate\A
U\NoAutoUpdate
Value: 0, 0, 0, 0
State: Enabled
GPO: Default Domain Policy
KeyName: Software\Policies\Microsoft\Windows\WindowsUpdate\A
U\ScheduledInstallTime
Value: 2, 0, 0, 0
State: Enabled
GPO: Default Domain Policy
KeyName: Software\Policies\Microsoft\Windows\WindowsUpdate\A
U\RescheduleWaitTime
Value: 1, 0, 0, 0
State: Enabled
GPO: Small Business Server Remote Assistance Policy
KeyName: software\policies\microsoft\windows NT\Terminal Ser
vices\fAllowUnsolicited
Value: 1, 0, 0, 0
State: Enabled
GPO: Small Business Server Remote Assistance Policy
KeyName: software\policies\microsoft\windows NT\Terminal Ser
vices\fAllowUnsolicitedFullControl
Value: 1, 0, 0, 0
State: Enabled
GPO: Default Domain Policy
KeyName: Software\Policies\Microsoft\Windows\WindowsUpdate\E
levateNonAdmins
Value: 1, 0, 0, 0
State: Enabled
GPO: Default Domain Policy
KeyName: Software\Policies\Microsoft\Windows\WindowsUpdate\T
argetGroup
Value: 87, 0, 69, 0, 83, 0, 84, 0, 79, 0, 78, 0, 69, 0, 85
, 0, 75, 0, 0, 0
State: Enabled
GPO: Small Business Server Remote Assistance Policy
KeyName: software\policies\microsoft\windows NT\Terminal Ser
vices\RAUnsolicit\MYDOMAIN\Domain Admins
Value: 87, 0, 69, 0, 83, 0, 84, 0, 79, 0, 78, 0, 69, 0, 92
, 0, 68, 0, 111, 0, 109, 0, 97, 0, 105, 0, 110, 0, 32, 0, 65, 0, 100, 0, 109, 0,
105, 0, 110, 0, 115, 0, 0, 0
State: Enabled
GPO: Default Domain Policy
KeyName: Software\Policies\Microsoft\Windows\WindowsUpdate\A
U\NoAutoRebootWithLoggedOnUsers
Value: 1, 0, 0, 0
State: Enabled
GPO: Default Domain Policy
KeyName: Software\Policies\Microsoft\Windows\WindowsUpdate\A
U\RescheduleWaitTimeEnabled
Value: 1, 0, 0, 0
State: Enabled
GPO: Default Domain Policy
KeyName: Software\Policies\Microsoft\Windows\WindowsUpdate\T
argetGroupEnabled
Value: 1, 0, 0, 0
State: Enabled
GPO: Small Business Server Client Computer
KeyName: software\policies\microsoft\windows\network connect
ions\NC_ShowSharedAccessUI
Value: 0, 0, 0, 0
State: Enabled
GPO: Default Domain Policy
KeyName: Software\Policies\Microsoft\Windows\WindowsUpdate\A
U\DetectionFrequency
Value: 22, 0, 0, 0
State: Enabled
GPO: Default Domain Policy
KeyName: Software\Policies\Microsoft\Windows\WindowsUpdate\A
U\RebootRelaunchTimeoutEnabled
Value: 1, 0, 0, 0
State: Enabled
GPO: Default Domain Policy
KeyName: Software\Policies\Microsoft\Windows\WindowsUpdate\W
UServer
Value: 104, 0, 116, 0, 116, 0, 112, 0, 58, 0, 47, 0, 47, 0
, 119, 0, 101, 0, 115, 0, 116, 0, 111, 0, 110, 0, 101, 0, 45, 0, 115, 0, 101, 0,
114, 0, 118, 0, 101, 0, 114, 0, 58, 0, 56, 0, 53, 0, 51, 0, 48, 0, 0, 0
State: Enabled
GPO: Default Domain Policy
KeyName: Software\Policies\Microsoft\Windows\WindowsUpdate\A
U\ScheduledInstallDay
Value: 0, 0, 0, 0
State: Enabled
GPO: Small Business Server Client Computer
KeyName: software\policies\microsoft\windows\network connect
ions\NC_AllowNetBridge_NLA
Value: 0, 0, 0, 0
State: Enabled
GPO: Default Domain Policy
KeyName: Software\Policies\Microsoft\Windows\WindowsUpdate\A
U\UseWUServer
Value: 1, 0, 0, 0
State: Enabled
USER SETTINGS
--------------
CN=Administrator,CN=Users,DC=MYDOMAIN,DC=local
Last time Group Policy was applied: 06/06/2010 at 12:06:00
Group Policy was applied from: MYDOMAIN-SERVER.MYDOMAIN.local
Group Policy slow link threshold: 500 kbps
Domain Name: MYDOMAIN
Domain Type: Windows 2000
Applied Group Policy Objects
-----------------------------
Default Domain Policy
Local Group Policy
The following GPOs were not applied because they were filtered out
-------------------------------------------------------------------
Small Business Server - Windows Vista policy
Filtering: Denied (WMI Filter)
WMI Filter: Vista
Small Business Server Client Computer
Filtering: Not Applied (Empty)
Small Business Server Remote Assistance Policy
Filtering: Disabled (GPO)
Small Business Server Domain Password Policy
Filtering: Not Applied (Empty)
Small Business Server Internet Connection Firewall
Filtering: Denied (WMI Filter)
WMI Filter: PreSP2
Small Business Server Lockout Policy
Filtering: Disabled (GPO)
Small Business Server Windows Firewall
Filtering: Denied (WMI Filter)
WMI Filter: PostSP2
The user is a part of the following security groups
---------------------------------------------------
Domain Users
Everyone
BUILTIN\Administrators
BUILTIN\Users
REMOTE INTERACTIVE LOGON
NT AUTHORITY\INTERACTIVE
NT AUTHORITY\Authenticated Users
This Organization
LOCAL
Domain Admins
Group Policy Creator Owners
SMSMSE Admins
Schema Admins
SBS Mobile Users
SBS Report Users
Enterprise Admins
Offer Remote Assistance Helpers
The user has the following security privileges
----------------------------------------------
Bypass traverse checking
Manage auditing and security log
Back up files and directories
Restore files and directories
Change the system time
Shut down the system
Force shutdown from a remote system
Take ownership of files or other objects
Debug programs
Modify firmware environment values
Profile system performance
Profile single process
Increase scheduling priority
Load and unload device drivers
Create a pagefile
Adjust memory quotas for a process
Remove computer from docking station
Perform volume maintenance tasks
Impersonate a client after authentication
Create global objects
Enable computer and user accounts to be trusted for delegation
Add workstations to domain
Resultant Set Of Policies for User
-----------------------------------
Software Installations
----------------------
N/A
Logon Scripts
-------------
N/A
Logoff Scripts
--------------
N/A
Public Key Policies
-------------------
N/A
Administrative Templates
------------------------
GPO: Local Group Policy
KeyName: Software\Microsoft\Windows\CurrentVersion\Policies\
Explorer\NoAddPrinter
State: disabled
GPO: Local Group Policy
KeyName: Software\Policies\Microsoft\Windows NT\Printers\Poi
ntAndPrint\TrustedServers
Value: 0, 0, 0, 0
State: Enabled
GPO: Local Group Policy
KeyName: Software\Policies\Microsoft\Windows NT\Printers\Poi
ntAndPrint\InForest
Value: 0, 0, 0, 0
State: Enabled
GPO: Local Group Policy
KeyName: Software\Policies\Microsoft\Windows NT\Printers\Poi
ntAndPrint\ServerList
State: disabled
GPO: Local Group Policy
KeyName: Software\Policies\Microsoft\Windows NT\Printers\Poi
ntAndPrint\Restricted
Value: 0, 0, 0, 0
State: Enabled
Folder Redirection
------------------
N/A
Internet Explorer Browser User Interface
----------------------------------------
GPO: Default Domain Policy
Large Animated Bitmap Name: N/A
Large Custom Logo Bitmap Name: N/A
Title BarText: West One UK Ltd
UserAgent Text: N/A
Delete existing toolbar buttons: No
Internet Explorer Connection
----------------------------
HTTP Proxy Server: N/A
Secure Proxy Server: N/A
FTP Proxy Server: N/A
Gopher Proxy Server: N/A
Socks Proxy Server: N/A
Auto Config Enable: No
Enable Proxy: No
Use same Proxy: No
Internet Explorer URLs
----------------------
GPO: Default Domain Policy
Home page URL: http://www.google.co.uk
Search page URL: N/A
Online support page URL: N/A
Internet Explorer Security
--------------------------
Always Viewable Sites: N/A
Password Override Enabled: False
GPO: Default Domain Policy
Import the current Content Ratings Settings: No
Import the current Security Zones Settings: No
Import current Authenticode Security Information: No
Enable trusted publisher lockdown: No
Internet Explorer Programs
--------------------------
GPO: Default Domain Policy
Import the current Program Settings: No
C:\Documents and Settings\Administrator>I have been testing by deliberately logging with wrong passwords and after 11 wrong passwords I can still log in with the correct one?
A lot info I know but it seems to be required from other threads i've read.
Thanks all :)
Hi,
I think that you haven't defined in your domain controller how many tries a user has untill he locks his account. You can check that following this steps:
-open administrative tools in your domain controller and click on Domain security policy
-Under security settings choose Account lock out policy
-On your right you will see: Account lockout threshold.. right clik on it and choose how many tries you want untill the account will lock. Hope it helps you
I think that you haven't defined in your domain controller how many tries a user has untill he locks his account. You can check that following this steps:
-open administrative tools in your domain controller and click on Domain security policy
-Under security settings choose Account lock out policy
-On your right you will see: Account lockout threshold.. right clik on it and choose how many tries you want untill the account will lock. Hope it helps you
you have account lockout duration of 10 minutes.. that means after account will be unlocked automatically
that is why you are able to log in
change this value to 0 that requires administrator to unlock account once locked.. alos i will set the invalid attempts to 5 or 3 just to be more secure...
and reset account lock out counter to some 30 minutes.
that is why you are able to log in
change this value to 0 that requires administrator to unlock account once locked.. alos i will set the invalid attempts to 5 or 3 just to be more secure...
and reset account lock out counter to some 30 minutes.
ASKER
But I am able to log in straight away, I thought the 10 minute duration would mean that I should not be able to log in until 10 minutes has passed.
ASKER
But I am able to log in straight away, I thought the 10 minute duration would mean that I should not be able to log in until 10 minutes has passed.
ASKER
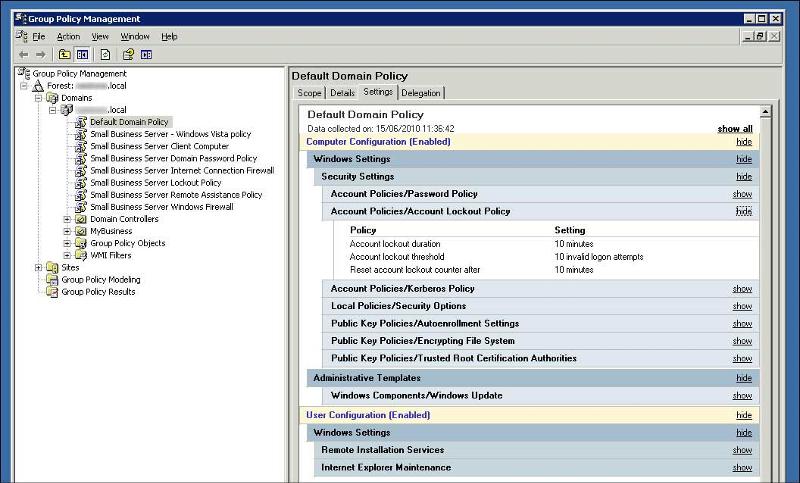
I have adjusted the settings as below, correct ?
GPO-Account-lockout.jpg
GPO-Account-lockout.jpg
ASKER
Still no joy, the account is never locked no matter how many incorrect logins.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Already answered by younghv, account lockout policies do not affect the built-in Administrator account. Test with a user account.
Hello
If you think that administrator account is target of atack you can rename it as user lambda, then create an administrator as copy of guest. Put a strong password on it. That account will be locked by GPO.
Dan
If you think that administrator account is target of atack you can rename it as user lambda, then create an administrator as copy of guest. Put a strong password on it. That account will be locked by GPO.
Dan
hello
I need some ugent help.I have an administrator account that needs to be excluded from my existing lock out policy.This is a special administrator account created maily to run services for a certain deployment application.I run windows server 2008 R2 AD.How do i set a policy or exclude this account from locking out , just like my enterprise administrator account?
I need some ugent help.I have an administrator account that needs to be excluded from my existing lock out policy.This is a special administrator account created maily to run services for a certain deployment application.I run windows server 2008 R2 AD.How do i set a policy or exclude this account from locking out , just like my enterprise administrator account?
Hello
FIrst is not ok to put a question in a closed one.
Seccond: no account can be excluded from this GPO, but the administrator account can't be looked. So:
even you run your apps using Domain Admin account, even you configure to run as a service.
Dan
FIrst is not ok to put a question in a closed one.
Seccond: no account can be excluded from this GPO, but the administrator account can't be looked. So:
even you run your apps using Domain Admin account, even you configure to run as a service.
Dan
ooh sorry, im a new user here , i was not aware i was asking on a comment but i asked again.my apologies.
ASKER