mark_06
asked on
Symantec Endpoint Protection Error
Hi,
I have Symantec EndPoint Protection version 11.0.6005.562.
Every time I boot the computer, after about 10 minutes it comes up with about 30 trojans that are temp files. They are in the form of DWHxxxx.tmp.
They aren't trojans, they are some file that Symantec creates and it keeps thinking it's a trojan.
I have attached a screen shot.
Does anyone know how to fix this from happening?
Thanks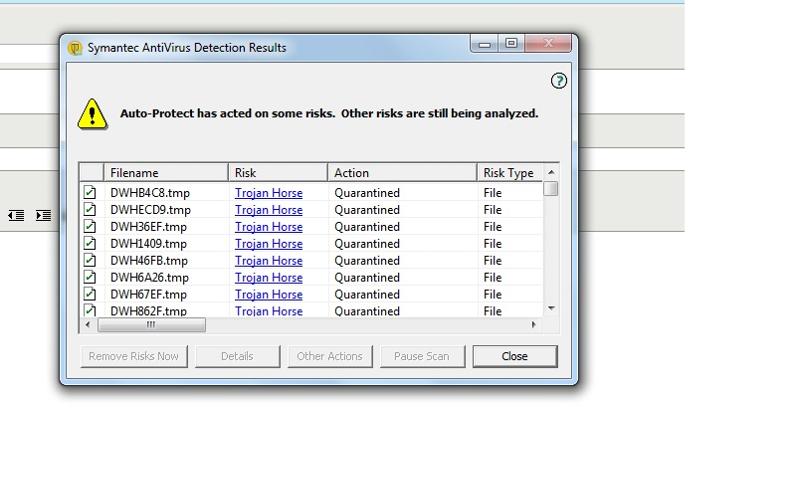
I have Symantec EndPoint Protection version 11.0.6005.562.
Every time I boot the computer, after about 10 minutes it comes up with about 30 trojans that are temp files. They are in the form of DWHxxxx.tmp.
They aren't trojans, they are some file that Symantec creates and it keeps thinking it's a trojan.
I have attached a screen shot.
Does anyone know how to fix this from happening?
Thanks

Boot your system into safe mode and delete all temp files and then reboot your system.
I would say:
- Disable system restore
- Reboot into safe mode
- delete all temp files
- make a full system scan
- Disable system restore
- Reboot into safe mode
- delete all temp files
- make a full system scan
Check also this post:
http://www.symantec.com/connect/forums/dwh-trojan-symantec-cant-remove-it
Read comment by Melchiah
http://www.symantec.com/connect/forums/dwh-trojan-symantec-cant-remove-it
Read comment by Melchiah
You could use CCleaner to clean the system of any temporary files and junk files
http://www.piriform.com/ccleaner/download
then you should also try HitManPro just to make sure anything left is cleaned
32bit
http://dl.surfright.nl/HitmanPro35.exe
http://download.cnet.com/Hitman-Pro-3/3000-2239_4-10895604.html
64bit
http://dl.surfright.nl/HitmanPro35_x64.exe
I hope that would help
Sudeep
http://www.piriform.com/ccleaner/download
then you should also try HitManPro just to make sure anything left is cleaned
32bit
http://dl.surfright.nl/HitmanPro35.exe
http://download.cnet.com/Hitman-Pro-3/3000-2239_4-10895604.html
64bit
http://dl.surfright.nl/HitmanPro35_x64.exe
I hope that would help
Sudeep
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.