Set up VPN on Cisco 871 Router?
I have a Cisco 871 Router at my home, running C870-advipservicesk9 11.T2.
I have never set up a VPN on it.
I have a static WAN address from my ISP.
My goal (and I don't know if this is even possible using this router) is to be able to connect to this router (which sits at my house) from my laptop running Windows XP, when I'm at coffee shops, using a VPN connection, such that my internet traffic goes from my laptop at the coffee shop, to the router (via VPN), and from my router out to the internet... the idea being to establish a secure connection at the coffee shop end, so that my traffic can't be sniffed by others in the coffee shop.
That is, my router at home would be a "middleman" between myself at the coffee shop and the internet.
Ideally, I'd like to do this without adding any software on the XP machine, using XP's built in VPN capability, though I don't know if that's compatible with any of the VPN setups that the Cisco offers. (It seems to have quite a few, and I'm not sure which if any of them are right for this scenario -- it seems to have things called "Site-to-Site VPN," "Easy VPN Remote," "Easy VPN Server," "Dynamic Multipoint VPN," "SSL VPN," etc.)
Can someone provide a step-by-step telling me how to set this up, both on the router and on the XP machine?
I have never set up a VPN on it.
I have a static WAN address from my ISP.
My goal (and I don't know if this is even possible using this router) is to be able to connect to this router (which sits at my house) from my laptop running Windows XP, when I'm at coffee shops, using a VPN connection, such that my internet traffic goes from my laptop at the coffee shop, to the router (via VPN), and from my router out to the internet... the idea being to establish a secure connection at the coffee shop end, so that my traffic can't be sniffed by others in the coffee shop.
That is, my router at home would be a "middleman" between myself at the coffee shop and the internet.
Ideally, I'd like to do this without adding any software on the XP machine, using XP's built in VPN capability, though I don't know if that's compatible with any of the VPN setups that the Cisco offers. (It seems to have quite a few, and I'm not sure which if any of them are right for this scenario -- it seems to have things called "Site-to-Site VPN," "Easy VPN Remote," "Easy VPN Server," "Dynamic Multipoint VPN," "SSL VPN," etc.)
Can someone provide a step-by-step telling me how to set this up, both on the router and on the XP machine?
ASKER
I don't see anything about SSL in the Cisco... just IPSEC and IKE... so I guess I'd have to install a client on XP...not ideal, but if that's what I have to do, then that's what I have to do.
The Shrew docs describe how to set up the client, but say nothing about setting up the router. What I need help with here is setting up the router, using Cisco Configuration Professional.
The Shrew docs describe how to set up the client, but say nothing about setting up the router. What I need help with here is setting up the router, using Cisco Configuration Professional.
ASKER
OH, wait, there is "SSL VPN," as mentioned earlier.
Still need step-by-step guidance to setting this up on the router.
Thanks!
Still need step-by-step guidance to setting this up on the router.
Thanks!
I'm going to assume you're using command line to set this up.
871's don't support SSL anyconnect vpn's; that begins on the ASA's.
871 can only terminate an IPSec connection, therefor a client will be used. I strongly recommend Cisco's client. This generally requires a Cisco support contract, but I'm confident you can find it on the internet.
The following is the configuration steps from the command line. Obviously my IP addressing will not be accurate since you didn't post yours, so you'll have to substitute as necessary.
Setup Local Authorization:
aaa authentication login default local
aaa authentication login remoteusers local
aaa authorization exec default local
aaa authorization network remotegroup local
Add Users/Usernames
username User1 privilege 15 secret blahblahblah
Define Phase1 (isakmp) Policy
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
Create an isakmp peer that ignores source address. Use whatever key you want
crypto isakmp key super$secretk3y address 0.0.0.0 0.0.0.0
Create pool to be used for client connections. You can change the network used, but you have to obviously make the same changes to match further on in the config
ip local pool vpnpool 192.168.55.5 192.168.55.25
Specify the address pool to use for your VPN connections
crypto isakmp client configuration address-pool local vpnpool
Create a group for authentication. Set the key to whatever.
crypto isakmp client configuration group vpngroup
key groupk3y
pool vpnpool
acl 100
save-password
include-local-lan
max-users 5
Configure phase2 (ipsec) negotiation
crypto ipsec transform-set myset esp-3des esp-sha-hmac
Create the crypto map
crypto dynamic-map dynmap 10
set transform-set myset
crypto map dynmap client authentication list remoteusers
crypto map dynmap isakmp authorization list remotegroup
crypto map dynmap client configuration address respond
Assign crypto map to interface (assuming outside is fa4)
int fa4
crypto map dynmap
Define interesting traffic. This is the traffic set to traverse the tunnel. Will contain your vpn network and your local inside network. Assuming a local network of 192.168.1.0
access-list 100 remark ***VPN Permits***
access-list 100 permit ip 192.168.1.0 0.0.0.255 192.168.55.0 0.0.0.255
That should be about it. Not the easiest task on the planet. Troubleshooting usually consists of turning on term mon, and then watching debug crypto ipsec and debug crypto isakmp. That should give you all the info you need. You may need to alter your NAT overload statement, or possibly add some tweaks if you have static NATs that you want to be able to access via VPN. If you have any questions regarding this configuration, let us know.
871's don't support SSL anyconnect vpn's; that begins on the ASA's.
871 can only terminate an IPSec connection, therefor a client will be used. I strongly recommend Cisco's client. This generally requires a Cisco support contract, but I'm confident you can find it on the internet.
The following is the configuration steps from the command line. Obviously my IP addressing will not be accurate since you didn't post yours, so you'll have to substitute as necessary.
Setup Local Authorization:
aaa authentication login default local
aaa authentication login remoteusers local
aaa authorization exec default local
aaa authorization network remotegroup local
Add Users/Usernames
username User1 privilege 15 secret blahblahblah
Define Phase1 (isakmp) Policy
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
Create an isakmp peer that ignores source address. Use whatever key you want
crypto isakmp key super$secretk3y address 0.0.0.0 0.0.0.0
Create pool to be used for client connections. You can change the network used, but you have to obviously make the same changes to match further on in the config
ip local pool vpnpool 192.168.55.5 192.168.55.25
Specify the address pool to use for your VPN connections
crypto isakmp client configuration address-pool local vpnpool
Create a group for authentication. Set the key to whatever.
crypto isakmp client configuration group vpngroup
key groupk3y
pool vpnpool
acl 100
save-password
include-local-lan
max-users 5
Configure phase2 (ipsec) negotiation
crypto ipsec transform-set myset esp-3des esp-sha-hmac
Create the crypto map
crypto dynamic-map dynmap 10
set transform-set myset
crypto map dynmap client authentication list remoteusers
crypto map dynmap isakmp authorization list remotegroup
crypto map dynmap client configuration address respond
Assign crypto map to interface (assuming outside is fa4)
int fa4
crypto map dynmap
Define interesting traffic. This is the traffic set to traverse the tunnel. Will contain your vpn network and your local inside network. Assuming a local network of 192.168.1.0
access-list 100 remark ***VPN Permits***
access-list 100 permit ip 192.168.1.0 0.0.0.255 192.168.55.0 0.0.0.255
That should be about it. Not the easiest task on the planet. Troubleshooting usually consists of turning on term mon, and then watching debug crypto ipsec and debug crypto isakmp. That should give you all the info you need. You may need to alter your NAT overload statement, or possibly add some tweaks if you have static NATs that you want to be able to access via VPN. If you have any questions regarding this configuration, let us know.
ASKER
Hi, thanks very much -
Please pardon my ignorance, but a few questions.... I'm reasonably smart, but TOTALLY unfamiliar with some of these commands...
Add Users/Usernames
username User1 privilege 15 secret blahblahblah
A login name for the VPN should be substituted for "User1", yes?
And would "blahblahblah" be a hash of the password that the User is going to use to access the VPN? Or something else?
Create an isakmp peer that ignores source address. Use whatever key you want
crypto isakmp key super$secretk3y address 0.0.0.0 0.0.0.0
I assume "super$secretk3y" is a placeholder for the "key"? What form does the key take? How would I generate one, or get one?
Create a group for authentication. Set the key to whatever.
crypto isakmp client configuration group vpngroup
key groupk3y
pool vpnpool
acl 100
save-password
include-local-lan
max-users 5
Here, again, is "groupk3y" standing in for the key ? What form would it take, and how would I generate one, or get one?
Thanks!
Please pardon my ignorance, but a few questions.... I'm reasonably smart, but TOTALLY unfamiliar with some of these commands...
Add Users/Usernames
username User1 privilege 15 secret blahblahblah
A login name for the VPN should be substituted for "User1", yes?
And would "blahblahblah" be a hash of the password that the User is going to use to access the VPN? Or something else?
Create an isakmp peer that ignores source address. Use whatever key you want
crypto isakmp key super$secretk3y address 0.0.0.0 0.0.0.0
I assume "super$secretk3y" is a placeholder for the "key"? What form does the key take? How would I generate one, or get one?
Create a group for authentication. Set the key to whatever.
crypto isakmp client configuration group vpngroup
key groupk3y
pool vpnpool
acl 100
save-password
include-local-lan
max-users 5
Here, again, is "groupk3y" standing in for the key ? What form would it take, and how would I generate one, or get one?
Thanks!
Hi, thanks very much -
Please pardon my ignorance, but a few questions.... I'm reasonably smart, but TOTALLY unfamiliar with some of these commands...
Add Users/Usernames
username User1 privilege 15 secret blahblahblah
Yes, User1 is the username, and "blahlblahblah" is that users password. Both of these can be edited to whatever you wish.
Create an isakmp peer that ignores source address. Use whatever key you want
crypto isakmp key super$secretk3y address 0.0.0.0 0.0.0.0
I assume "super$secretk3y" is a placeholder for the "key"? What form does the key take? How would I generate one, or get one?
This setting actually isn't needed; I was blowing through this quickly and added it without thinking. If you're using group authentication, you don't need this statement.
Create a group for authentication. Set the key to whatever.
crypto isakmp client configuration group vpngroup
key groupk3y
pool vpnpool
acl 100
save-password
include-local-lan
max-users 5
Here, again, is "groupk3y" standing in for the key ? What form would it take, and how would I generate one, or get one?
This is the key for the group authentication. When you're setting up a connection from the Cisco client; you specify Group (vpngroup in this example) and then you specify the key for that group, which is what you're setting with this. As with the other, you can use any string you like.
ASKER
OK, am able to connect to the VPN, and am able to ping machines on the local network from the coffee shop...but, once connected, I can't surf the net. Unable to ping IP addresses on the internet either by numeric IP address or canonical IP addresses. Somehow, I'm confined to the LAN when connected from the outside world... what have I screwed up?
On your Cisco client, go to the transport tab of your vpn connection properties make sure you check the box that says allow local LAN access, and make sure you have that included on your router as displayed here:
crypto isakmp client configuration group vpngroup
key groupk3y
pool vpnpool
acl 100
save-password
include-local-lan
max-users 5
crypto isakmp client configuration group vpngroup
key groupk3y
pool vpnpool
acl 100
save-password
include-local-lan
max-users 5
ASKER
Thanks... time to give up for the moment, but I'll be back to this tomorrow... will keep you posted!
ASKER
Well, I tried and tried with your proposal, but it didn't work... So then, I tried using Cisco Configuration Professional, in which you utilize a "wizard," which then modifies the running configuration for you to reflect the choices you've made in the wizard. Using that, I feel I'm very very close: I can log in via the VPN, but still cannot surf to internet sites through the router. I feel like I must be missing Just One Thing. Here's a [redacted to remove private information] version of my config... can you tell what's missing or wrong?
-----
version 12.4
no service pad
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
service password-encryption
service sequence-numbers
!
hostname nohostbar
!
boot-start-marker
boot-end-marker
!
security authentication failure rate 3 log
security passwords min-length 6
logging buffered 51200
logging console critical
enable secret 5 [redacted]
!
aaa new-model
!
!
aaa authentication login local_authen local
aaa authentication login ciscocp_vpn_xauth_ml_1 local
aaa authorization exec local_author local
aaa authorization network ciscocp_vpn_group_ml_1 local
!
!
aaa session-id common
clock timezone PST -8
clock summer-time PDT recurring
no ip source-route
no ip gratuitous-arps
ip cef
!
!
no ip dhcp use vrf connected
ip dhcp excluded-address 192.168.1.1 192.168.1.99
ip dhcp excluded-address 192.168.1.135 192.168.1.254
!
ip dhcp pool sdm-pool1
import all
network 192.168.1.0 255.255.255.0
dns-server 68.87.76.182 68.87.78.134
default-router 192.168.1.253
!
ip dhcp pool WINKY
host 192.168.1.106 255.255.255.0
client-identifier 0100.1903.0030.c4
!
ip dhcp pool ChairmanWIRED
host 192.168.1.107 255.255.255.0
client-identifier 0100.0f1f.1812.d2
!
ip dhcp pool SARA
host 192.168.1.110 255.255.255.0
client-identifier 0100.123f.aeed.3b
!
ip dhcp pool AVLP2
host 192.168.1.111 255.255.255.0
client-identifier 0100.a0b0.6556.90
!
ip dhcp pool MEDIABOY
host 192.168.1.109 255.255.255.0
client-identifier 0100.1320.48cd.9d
!
ip dhcp pool DLINKALI
host 192.168.1.103 255.255.255.0
client-identifier 0100.1195.b726.d2
!
ip dhcp pool DLINKMPT
host 192.168.1.100 255.255.255.0
client-identifier 0100.1195.ca38.e0
!
ip dhcp pool DLINKFR
host 192.168.1.102 255.255.255.0
client-identifier 0100.1195.eb66.15
!
ip dhcp pool ChairmanWIRELESS
host 192.168.1.108 255.255.255.0
client-identifier 0100.0b6b.358d.42
!
ip dhcp pool ALFA
host 192.168.1.114 255.255.255.0
client-identifier 0100.c0ca.26c7.55
!
ip dhcp pool SARALAPWL
host 192.168.1.116 255.255.255.0
client-identifier 0100.166f.be13.8e
!
ip dhcp pool SARALAP
host 192.168.1.117 255.255.255.0
client-identifier 0100.16d3.2f61.49
!
ip dhcp pool PHILBIN
host 192.168.1.104 255.255.255.0
client-identifier 0100.1c23.1f08.61
!
ip dhcp pool PHILBINWL
host 192.168.1.105 255.255.255.0
client-identifier 0100.1644.bc35.47
!
ip dhcp pool IPHONE3G
host 192.168.1.119 255.255.255.0
client-identifier 0100.21e9.4ff0.8b
!
ip dhcp pool SARAMACETH
host 192.168.1.120 255.255.255.0
client-identifier 0158.b035.f73a.6f
!
ip dhcp pool SARAMACWLESS
host 192.168.1.121 255.255.255.0
client-identifier 0158.b035.7d8b.1e
!
ip dhcp pool LauraTouch
host 192.168.1.122 255.255.255.0
client-identifier 0100.1ec2.532e.9d
!
ip dhcp pool APPLETV
host 192.168.1.123 255.255.255.0
client-identifier 0100.1f5b.a96f.ee
!
ip dhcp pool VLPPHONE
host 192.168.1.124 255.255.255.0
hardware-address 0004.f2a5.8985
!
ip dhcp pool DISHTVFR
host 192.168.1.112 255.255.255.0
client-identifier 0100.0889.8e20.ed
!
ip dhcp pool DISHTVBR
host 192.168.1.113 255.255.255.0
client-identifier 0100.0889.502d.af
!
ip dhcp pool IPHONE3GS
host 192.168.1.115 255.255.255.0
client-identifier 01c4.2c03.67a7.37
!
ip dhcp pool SaraIphone
host 192.168.1.101 255.255.255.0
client-identifier 01f8.1edf.4e85.db
!
ip dhcp pool PORTAROUTER
host 192.168.1.125 255.255.255.0
client-identifier 0100.2401.3d11.e4
!
ip dhcp pool NIKKI
host 192.168.1.126 255.255.255.0
client-identifier 0100.1b63.c0be.36
!
ip dhcp pool BLURAY
host 192.168.1.118 255.255.255.0
client-identifier 0100.16fb.0099.03
!
ip dhcp pool SamDS
host 192.168.1.127 255.255.255.0
client-identifier 0100.25a0.f1ac.7a
!
ip dhcp pool SaraTouch
host 192.168.1.128 255.255.255.0
client-identifier 0100.2332.5891.f2
!
ip dhcp pool AriIphone4
host 192.168.1.129 255.255.255.0
client-identifier 017c.c537.3bd2.f5
!
ip dhcp pool GRACIELLA
host 192.168.1.130 255.255.255.0
client-identifier 01e0.cb4e.b124.b8
!
ip dhcp pool CELTOWER
host 192.168.1.131 255.255.255.0
client-identifier 0144.5829.3ef3.ba
!
ip dhcp pool blackwii
host 192.168.1.132 255.255.255.0
client-identifier 018c.56c5.38c9.f3
!
ip dhcp pool LAURALAPWL
host 192.168.1.133 255.255.255.0
client-identifier 0100.24d7.5644.28
!
ip dhcp pool LAURALAPWIRED
host 192.168.1.134 255.255.255.0
client-identifier 015c.260a.151b.93
!
!
ip tcp synwait-time 10
no ip bootp server
ip name-server 208.67.220.220
ip name-server 208.67.222.222
ip ssh time-out 60
ip ssh authentication-retries 2
ip inspect max-incomplete high 20000000
ip inspect max-incomplete low 20000000
ip inspect one-minute high 100000000
ip inspect one-minute low 100000000
ip inspect tcp max-incomplete host 100000 block-time 0
ip inspect name SDM_LOW cuseeme
ip inspect name SDM_LOW dns
ip inspect name SDM_LOW ftp
ip inspect name SDM_LOW h323
ip inspect name SDM_LOW https
ip inspect name SDM_LOW icmp
ip inspect name SDM_LOW netshow
ip inspect name SDM_LOW rcmd
ip inspect name SDM_LOW realaudio
ip inspect name SDM_LOW rtsp
ip inspect name SDM_LOW sqlnet
ip inspect name SDM_LOW streamworks
ip inspect name SDM_LOW tftp
ip inspect name SDM_LOW tcp
ip inspect name SDM_LOW udp
ip inspect name SDM_LOW vdolive
!
multilink bundle-name authenticated
!
crypto pki trustpoint TP-self-signed-404758651
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certifi
revocation-check none
rsakeypair TP-self-signed-404758651
!
!
crypto pki certificate chain TP-self-signed-404758651
certificate self-signed 01
3082023F 308201A8 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
30312E30 2C060355 04031325 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 34303437 35383635 31301E17 0D313030 36313631 33313332
305A170D 32303031 30313030 30303030 5A303031 2E302C06 03550403 1325494F
532D5365 6C662D53 69676E65 642D4365 72746966 69636174 652D3430 34373538
36353130 819F300D 06092A86 4886F70D 01010105 0003818D 00308189 02818100
CA33ACAA A539309F 93478CB8 6710746D C0137632 AE9BC625 12A4E324 CEAC8FC1
B22A96B9 AA6B32CB 5A486AEC BE2BB54E 02A03228 83365EE9 72BEE864 A0739C5B
49C839FB 271F0B05 BD3A4DE0 B382B646 18CB5781 839337D2 42B3B024 FBD575D1
FDF7AD72 10429EDF 5974761A 836BE80B C12840EE D7B96156 61382343 AB066991
02030100 01A36930 67300F06 03551D13 0101FF04 05300301 01FF3014 0603551D
11040D30 0B82096E 6F686F73 74626172 301F0603 551D2304 18301680 147C1814
601ABAAD 1933D0ED CBE030DD 3D4F2B36 BD301D06 03551D0E 04160414 7C181460
1ABAAD19 33D0EDCB E030DD3D 4F2B36BD 300D0609 2A864886 F70D0101 04050003
8181006C D6D7527A 82EBE362 452EE6EC 594BA7D8 CFD0E0FD 22058F21 47AA7437
C181D428 938E008F 3E2CDA95 FDD284AE F80E6DB4 35082372 F97A84ED 5358883B
BD07DE1B A35EDCEB C466E19B E4396107 AC6A52A2 717704A9 8A14B3BF 012C5BD7
4F840B2B ECEA9F35 42B1A37F 7FC87538 B7011EE4 66B8D679 E17D3134 7D0DFC0A B7C36A
quit
crypto ctcp port 10000
!
!
username admin privilege 15 secret 5 [redacted]
username akahan privilege 15 secret 5 [redacted]
!
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
!
crypto isakmp client configuration group vpnusers
key [redacted]
pool SDM_POOL_1
include-local-lan
max-users 10
netmask 255.255.255.0
crypto isakmp profile ciscocp-ike-profile-1
match identity group vpnusers
client authentication list ciscocp_vpn_xauth_ml_1
isakmp authorization list ciscocp_vpn_group_ml_1
client configuration address respond
virtual-template 1
!
!
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
!
crypto ipsec profile CiscoCP_Profile1
set transform-set ESP-3DES-SHA
set isakmp-profile ciscocp-ike-profile-1
!
!
!
!
!
interface Null0
no ip unreachables
!
interface FastEthernet0
!
interface FastEthernet1
!
interface FastEthernet2
!
interface FastEthernet3
!
interface FastEthernet4
description $ES_WAN$$ETH-WAN$$FW_OUTSI
ip address 208.74.[redacted] 255.255.255.224
ip access-group 101 in
ip verify unicast reverse-path
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat outside
ip inspect SDM_LOW out
ip virtual-reassembly
ip route-cache flow
duplex auto
speed auto
!
interface Virtual-Template1 type tunnel
ip unnumbered FastEthernet4
tunnel mode ipsec ipv4
tunnel protection ipsec profile CiscoCP_Profile1
!
interface Vlan1
description $ETH-SW-LAUNCH$$INTF-INFO-
ip address 192.168.1.1 255.255.255.0
ip access-group 2051 in
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat inside
ip virtual-reassembly
ip route-cache flow
ip tcp adjust-mss 1452
!
ip local pool SDM_POOL_1 192.168.55.1 192.168.55.20
ip route 0.0.0.0 0.0.0.0 208.74.177.97 10
ip route 0.0.0.0 0.0.0.0 192.168.1.253 20
!
!
ip http server
ip http access-class 1
ip http authentication local
ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
ip nat inside source list 1 interface FastEthernet4 overload
ip nat inside source static udp 192.168.1.124 5060 interface FastEthernet4 5060
ip nat inside source static udp 192.168.1.124 5199 interface FastEthernet4 5199
ip nat inside source static udp 192.168.1.124 3479 interface FastEthernet4 3479
ip nat inside source static udp 192.168.1.124 15044 interface FastEthernet4 15044
ip nat inside source static tcp 192.168.1.199 6999 interface FastEthernet4 6999
ip nat inside source static tcp 192.168.1.199 6998 interface FastEthernet4 6998
ip nat inside source static tcp 192.168.1.199 6997 interface FastEthernet4 6997
ip nat inside source static tcp 192.168.1.199 6996 interface FastEthernet4 6996
ip nat inside source static tcp 192.168.1.199 6995 interface FastEthernet4 6995
ip nat inside source static tcp 192.168.1.199 6994 interface FastEthernet4 6994
ip nat inside source static tcp 192.168.1.199 6993 interface FastEthernet4 6993
ip nat inside source static tcp 192.168.1.199 6992 interface FastEthernet4 6992
ip nat inside source static tcp 192.168.1.199 6991 interface FastEthernet4 6991
ip nat inside source static tcp 192.168.1.199 6990 interface FastEthernet4 6990
ip nat inside source static tcp 192.168.1.199 6989 interface FastEthernet4 6989
ip nat inside source static tcp 192.168.1.199 6988 interface FastEthernet4 6988
ip nat inside source static tcp 192.168.1.199 6987 interface FastEthernet4 6987
ip nat inside source static tcp 192.168.1.199 6986 interface FastEthernet4 6986
ip nat inside source static tcp 192.168.1.199 6985 interface FastEthernet4 6985
ip nat inside source static tcp 192.168.1.199 6984 interface FastEthernet4 6984
ip nat inside source static tcp 192.168.1.199 6983 interface FastEthernet4 6983
ip nat inside source static tcp 192.168.1.199 6982 interface FastEthernet4 6982
ip nat inside source static tcp 192.168.1.199 6981 interface FastEthernet4 6981
ip nat inside source static tcp 192.168.1.199 6980 interface FastEthernet4 6980
ip nat inside source static tcp 192.168.1.199 6979 interface FastEthernet4 6979
ip nat inside source static tcp 192.168.1.199 6978 interface FastEthernet4 6978
ip nat inside source static tcp 192.168.1.199 6977 interface FastEthernet4 6977
ip nat inside source static tcp 192.168.1.199 6976 interface FastEthernet4 6976
ip nat inside source static tcp 192.168.1.199 6975 interface FastEthernet4 6975
ip nat inside source static tcp 192.168.1.199 6974 interface FastEthernet4 6974
ip nat inside source static tcp 192.168.1.199 6973 interface FastEthernet4 6973
ip nat inside source static tcp 192.168.1.199 6972 interface FastEthernet4 6972
ip nat inside source static tcp 192.168.1.199 6971 interface FastEthernet4 6971
ip nat inside source static tcp 192.168.1.199 6970 interface FastEthernet4 6970
ip nat inside source static tcp 192.168.1.199 6969 interface FastEthernet4 6969
ip nat inside source static tcp 192.168.1.199 6968 interface FastEthernet4 6968
ip nat inside source static tcp 192.168.1.199 6967 interface FastEthernet4 6967
ip nat inside source static tcp 192.168.1.199 6966 interface FastEthernet4 6966
ip nat inside source static tcp 192.168.1.199 6965 interface FastEthernet4 6965
ip nat inside source static tcp 192.168.1.199 6964 interface FastEthernet4 6964
ip nat inside source static tcp 192.168.1.199 6963 interface FastEthernet4 6963
ip nat inside source static tcp 192.168.1.199 6962 interface FastEthernet4 6962
ip nat inside source static tcp 192.168.1.199 6961 interface FastEthernet4 6961
ip nat inside source static tcp 192.168.1.199 6960 interface FastEthernet4 6960
ip nat inside source static tcp 192.168.1.199 6959 interface FastEthernet4 6959
ip nat inside source static tcp 192.168.1.199 6958 interface FastEthernet4 6958
ip nat inside source static tcp 192.168.1.199 6957 interface FastEthernet4 6957
ip nat inside source static tcp 192.168.1.199 6956 interface FastEthernet4 6956
ip nat inside source static tcp 192.168.1.199 6955 interface FastEthernet4 6955
ip nat inside source static tcp 192.168.1.199 6954 interface FastEthernet4 6954
ip nat inside source static tcp 192.168.1.199 6953 interface FastEthernet4 6953
ip nat inside source static tcp 192.168.1.199 6952 interface FastEthernet4 6952
ip nat inside source static tcp 192.168.1.199 6951 interface FastEthernet4 6951
ip nat inside source static tcp 192.168.1.199 6950 interface FastEthernet4 6950
ip nat inside source static tcp 192.168.1.199 6949 interface FastEthernet4 6949
ip nat inside source static tcp 192.168.1.199 6948 interface FastEthernet4 6948
ip nat inside source static tcp 192.168.1.199 6947 interface FastEthernet4 6947
ip nat inside source static tcp 192.168.1.199 6946 interface FastEthernet4 6946
ip nat inside source static tcp 192.168.1.199 6945 interface FastEthernet4 6945
ip nat inside source static tcp 192.168.1.199 6944 interface FastEthernet4 6944
ip nat inside source static tcp 192.168.1.199 6943 interface FastEthernet4 6943
ip nat inside source static tcp 192.168.1.199 6942 interface FastEthernet4 6942
ip nat inside source static tcp 192.168.1.199 6941 interface FastEthernet4 6941
ip nat inside source static tcp 192.168.1.199 6940 interface FastEthernet4 6940
ip nat inside source static tcp 192.168.1.199 6939 interface FastEthernet4 6939
ip nat inside source static tcp 192.168.1.199 6938 interface FastEthernet4 6938
ip nat inside source static tcp 192.168.1.199 6937 interface FastEthernet4 6937
ip nat inside source static tcp 192.168.1.199 6936 interface FastEthernet4 6936
ip nat inside source static tcp 192.168.1.199 6935 interface FastEthernet4 6935
ip nat inside source static tcp 192.168.1.199 6934 interface FastEthernet4 6934
ip nat inside source static tcp 192.168.1.199 6933 interface FastEthernet4 6933
ip nat inside source static tcp 192.168.1.199 6932 interface FastEthernet4 6932
ip nat inside source static tcp 192.168.1.199 6931 interface FastEthernet4 6931
ip nat inside source static tcp 192.168.1.199 6930 interface FastEthernet4 6930
ip nat inside source static tcp 192.168.1.199 6929 interface FastEthernet4 6929
ip nat inside source static tcp 192.168.1.199 6928 interface FastEthernet4 6928
ip nat inside source static tcp 192.168.1.199 6927 interface FastEthernet4 6927
ip nat inside source static tcp 192.168.1.199 6926 interface FastEthernet4 6926
ip nat inside source static tcp 192.168.1.199 6925 interface FastEthernet4 6925
ip nat inside source static tcp 192.168.1.199 6924 interface FastEthernet4 6924
ip nat inside source static tcp 192.168.1.199 6923 interface FastEthernet4 6923
ip nat inside source static tcp 192.168.1.199 6922 interface FastEthernet4 6922
ip nat inside source static tcp 192.168.1.199 6921 interface FastEthernet4 6921
ip nat inside source static tcp 192.168.1.199 6920 interface FastEthernet4 6920
ip nat inside source static tcp 192.168.1.199 6919 interface FastEthernet4 6919
ip nat inside source static tcp 192.168.1.199 6918 interface FastEthernet4 6918
ip nat inside source static tcp 192.168.1.199 6917 interface FastEthernet4 6917
ip nat inside source static tcp 192.168.1.199 6916 interface FastEthernet4 6916
ip nat inside source static tcp 192.168.1.199 6915 interface FastEthernet4 6915
ip nat inside source static tcp 192.168.1.199 6914 interface FastEthernet4 6914
ip nat inside source static tcp 192.168.1.199 6913 interface FastEthernet4 6913
ip nat inside source static tcp 192.168.1.199 6912 interface FastEthernet4 6912
ip nat inside source static tcp 192.168.1.199 6911 interface FastEthernet4 6911
ip nat inside source static tcp 192.168.1.199 6910 interface FastEthernet4 6910
ip nat inside source static tcp 192.168.1.199 6909 interface FastEthernet4 6909
ip nat inside source static tcp 192.168.1.199 6908 interface FastEthernet4 6908
ip nat inside source static tcp 192.168.1.199 6907 interface FastEthernet4 6907
ip nat inside source static tcp 192.168.1.199 6906 interface FastEthernet4 6906
ip nat inside source static tcp 192.168.1.199 6905 interface FastEthernet4 6905
ip nat inside source static tcp 192.168.1.199 6904 interface FastEthernet4 6904
ip nat inside source static tcp 192.168.1.199 6903 interface FastEthernet4 6903
ip nat inside source static tcp 192.168.1.199 6902 interface FastEthernet4 6902
ip nat inside source static tcp 192.168.1.199 6901 interface FastEthernet4 6901
ip nat inside source static tcp 192.168.1.199 6900 interface FastEthernet4 6900
ip nat inside source static tcp 192.168.1.199 6899 interface FastEthernet4 6899
ip nat inside source static tcp 192.168.1.199 6898 interface FastEthernet4 6898
ip nat inside source static tcp 192.168.1.199 6897 interface FastEthernet4 6897
ip nat inside source static tcp 192.168.1.199 6896 interface FastEthernet4 6896
ip nat inside source static tcp 192.168.1.199 6895 interface FastEthernet4 6895
ip nat inside source static tcp 192.168.1.199 6894 interface FastEthernet4 6894
ip nat inside source static tcp 192.168.1.199 6893 interface FastEthernet4 6893
ip nat inside source static tcp 192.168.1.199 6892 interface FastEthernet4 6892
ip nat inside source static tcp 192.168.1.199 6891 interface FastEthernet4 6891
ip nat inside source static tcp 192.168.1.199 6890 interface FastEthernet4 6890
ip nat inside source static tcp 192.168.1.199 6889 interface FastEthernet4 6889
ip nat inside source static tcp 192.168.1.199 6888 interface FastEthernet4 6888
ip nat inside source static tcp 192.168.1.199 6887 interface FastEthernet4 6887
ip nat inside source static tcp 192.168.1.199 6886 interface FastEthernet4 6886
ip nat inside source static tcp 192.168.1.199 6885 interface FastEthernet4 6885
ip nat inside source static tcp 192.168.1.199 6884 interface FastEthernet4 6884
ip nat inside source static tcp 192.168.1.199 6883 interface FastEthernet4 6883
ip nat inside source static tcp 192.168.1.199 6882 interface FastEthernet4 6882
ip nat inside source static tcp 192.168.1.199 6881 interface FastEthernet4 6881
ip nat inside source static tcp 192.168.1.199 6112 interface FastEthernet4 6112
ip nat inside source static tcp 192.168.1.199 3724 interface FastEthernet4 3724
ip nat inside source static udp 192.168.1.104 12344 interface FastEthernet4 12344
ip nat inside source static tcp 192.168.1.104 12344 interface FastEthernet4 12344
ip nat inside source static tcp 192.168.1.110 13853 interface FastEthernet4 13853
ip nat inside source static tcp 192.168.1.104 13852 interface FastEthernet4 13852
ip nat inside source static tcp 192.168.1.51 631 interface FastEthernet4 10000
ip nat inside source static tcp 192.168.1.109 4711 interface FastEthernet4 4711
ip nat inside source static tcp 192.168.1.109 4662 interface FastEthernet4 4662
ip nat inside source static udp 192.168.1.109 4672 interface FastEthernet4 4672
ip nat inside source static tcp 192.168.1.109 11888 interface FastEthernet4 11888
ip nat inside source static tcp 192.168.1.109 6710 interface FastEthernet4 6710
ip nat inside source static tcp 192.168.1.51 9100 interface FastEthernet4 10001
ip nat inside source static tcp 192.168.1.52 9100 interface FastEthernet4 10002
ip nat inside source static tcp 192.168.1.106 13854 interface FastEthernet4 13854
ip nat inside source static tcp 192.168.1.115 38341 interface FastEthernet4 38341
ip nat inside source static udp 192.168.1.115 38341 interface FastEthernet4 38341
ip nat inside source static udp 192.168.1.106 13854 interface FastEthernet4 13854
ip nat inside source static udp 192.168.1.104 13852 interface FastEthernet4 13852
ip nat inside source static udp 192.168.1.110 13853 interface FastEthernet4 13853
ip nat inside source static udp 192.168.1.110 12345 interface FastEthernet4 12345
ip nat inside source static tcp 192.168.1.110 12345 interface FastEthernet4 12345
ip nat inside source static tcp 192.168.1.109 12346 interface FastEthernet4 12346
ip nat inside source static udp 192.168.1.109 12346 interface FastEthernet4 12346
ip nat inside source static udp 192.168.1.104 6346 interface FastEthernet4 6346
ip nat inside source static tcp 192.168.1.104 6346 interface FastEthernet4 6346
ip nat inside source static tcp 192.168.1.104 5910 interface FastEthernet4 5910
ip nat inside source static tcp 192.168.1.109 9988 interface FastEthernet4 9988
ip nat inside source static tcp 192.168.1.109 10081 interface FastEthernet4 10081
ip nat inside source static udp 192.168.1.109 10081 interface FastEthernet4 10081
ip nat inside source static tcp 192.168.1.109 65500 interface FastEthernet4 65500
ip nat inside source static udp 192.168.1.109 444 interface FastEthernet4 444
ip nat inside source static tcp 192.168.1.109 444 interface FastEthernet4 444
ip nat inside source static udp 192.168.1.104 5500 interface FastEthernet4 5500
ip nat inside source static tcp 192.168.1.104 5500 interface FastEthernet4 5500
ip nat inside source static tcp 192.168.1.109 5905 interface FastEthernet4 5905
!
logging trap debugging
access-list 1 permit 67.170.236.160
access-list 1 remark Auto generated by SDM Management Access feature
access-list 1 remark SDM_ACL Category=1
access-list 1 permit 192.168.1.0 0.0.0.255
access-list 100 remark auto generated by SDM firewall configuration
access-list 100 remark SDM_ACL Category=0
access-list 100 deny ip 208.74.177.96 0.0.0.31 any
access-list 100 deny ip host 255.255.255.255 any
access-list 100 deny ip 127.0.0.0 0.255.255.255 any
access-list 100 permit ip any any
access-list 101 remark CCP_ACL Category=1
access-list 101 permit udp any host 208.74.[redacted] eq 5060
access-list 101 permit udp any host 208.74.[redacted] eq non500-isakmp
access-list 101 permit udp any host 208.74.[redacted] eq isakmp
access-list 101 permit esp any host 208.74.[redacted]
access-list 101 permit ahp any host 208.74.[redacted]
access-list 101 permit udp any host 208.74.[redacted] eq 5199
access-list 101 permit udp any host 208.74.[redacted] eq 3479
access-list 101 permit udp any host 208.74.[redacted] eq 15044
access-list 101 remark auto generated by SDM firewall configuration
access-list 101 permit tcp any host 208.74.[redacted] eq 444
access-list 101 permit udp any host 208.74.[redacted] eq 444
access-list 101 permit tcp host 24.7.127.6 host 208.74.[redacted] eq telnet
access-list 101 permit tcp host 24.7.127.6 host 208.74.[redacted] eq 22
access-list 101 permit tcp host 24.7.127.6 host 208.74.[redacted] eq www
access-list 101 permit tcp host 24.7.127.6 host 208.74.[redacted] eq 443
access-list 101 permit tcp host 24.7.127.6 host 208.74.[redacted] eq cmd
access-list 101 deny udp any host 208.74.[redacted] eq snmp
access-list 101 permit udp host 208.67.222.222 eq domain any
access-list 101 permit udp host 204.11.224.14 eq domain any
access-list 101 permit udp host 204.11.231.14 eq domain any
access-list 101 permit udp host 208.67.220.220 eq domain any
access-list 101 permit udp any host 208.74.[redacted] eq 10081
access-list 101 permit tcp any host 208.74.[redacted] eq 10081
access-list 101 permit tcp any host 208.74.[redacted] eq 9988
access-list 101 permit tcp any host 208.74.[redacted] eq 5500
access-list 101 permit tcp any host 208.74.[redacted] eq 5910
access-list 101 permit tcp any host 208.74.[redacted] eq 6346
access-list 101 permit udp any host 208.74.[redacted] eq 6346
access-list 101 permit udp any host 208.74.[redacted] eq 12346
access-list 101 permit tcp any host 208.74.[redacted] eq 12346
access-list 101 permit tcp any host 208.74.[redacted] eq 12345
access-list 101 permit udp any host 208.74.[redacted] eq 12345
access-list 101 permit udp any host 208.74.[redacted] eq 13853
access-list 101 permit udp any host 208.74.[redacted] eq 13852
access-list 101 permit udp any host 208.74.[redacted] eq 13854
access-list 101 permit udp any host 208.74.[redacted] eq 38341
access-list 101 permit tcp any host 208.74.[redacted] eq 38341
access-list 101 permit tcp any host 208.74.[redacted] eq 13854
access-list 101 permit tcp any host 208.74.[redacted] eq 10001
access-list 101 permit tcp any host 208.74.[redacted] eq 10002
access-list 101 permit tcp any host 208.74.[redacted] eq 6710
access-list 101 permit tcp any host 208.74.[redacted] eq 65500
access-list 101 permit tcp any host 208.74.[redacted] eq 11888
access-list 101 permit udp any host 208.74.[redacted] eq 4672
access-list 101 permit tcp any host 208.74.[redacted] eq 4662
access-list 101 permit tcp any host 208.74.[redacted] eq 4711
access-list 101 permit tcp any host 208.74.[redacted] eq 10000
access-list 101 permit tcp any host 208.74.[redacted] eq 13852
access-list 101 permit tcp any host 208.74.[redacted] eq 5905
access-list 101 permit tcp any host 208.74.[redacted] eq 13853
access-list 101 permit tcp any host 208.74.[redacted] eq 12344
access-list 101 permit udp any host 208.74.[redacted] eq 12344
access-list 101 permit tcp any host 208.74.[redacted] eq 3724
access-list 101 permit tcp any host 208.74.[redacted] eq 6112
access-list 101 permit tcp any host 208.74.[redacted] eq 6881
access-list 101 permit tcp any host 208.74.[redacted] eq 6882
access-list 101 permit tcp any host 208.74.[redacted] eq 6883
access-list 101 permit tcp any host 208.74.[redacted] eq 6884
access-list 101 permit tcp any host 208.74.[redacted] eq 6885
access-list 101 permit tcp any host 208.74.[redacted] eq 6886
access-list 101 permit tcp any host 208.74.[redacted] eq 6887
access-list 101 permit tcp any host 208.74.[redacted] eq 6888
access-list 101 permit tcp any host 208.74.[redacted] eq 6889
access-list 101 permit tcp any host 208.74.[redacted] eq 6890
access-list 101 permit tcp any host 208.74.[redacted] eq 6891
access-list 101 permit tcp any host 208.74.[redacted] eq 6892
access-list 101 permit tcp any host 208.74.[redacted] eq 6893
access-list 101 permit tcp any host 208.74.[redacted] eq 6894
access-list 101 permit tcp any host 208.74.[redacted] eq 6895
access-list 101 permit tcp any host 208.74.[redacted] eq 6896
access-list 101 permit tcp any host 208.74.[redacted] eq 6897
access-list 101 permit tcp any host 208.74.[redacted] eq 6898
access-list 101 permit tcp any host 208.74.[redacted] eq 6899
access-list 101 permit tcp any host 208.74.[redacted] eq 6900
access-list 101 permit tcp any host 208.74.[redacted] eq 6901
access-list 101 permit tcp any host 208.74.[redacted] eq 6902
access-list 101 permit tcp any host 208.74.[redacted] eq 6903
access-list 101 permit tcp any host 208.74.[redacted] eq 6904
access-list 101 permit tcp any host 208.74.[redacted] eq 6905
access-list 101 permit tcp any host 208.74.[redacted] eq 6906
access-list 101 permit tcp any host 208.74.[redacted] eq 6907
access-list 101 permit tcp any host 208.74.[redacted] eq 6908
access-list 101 permit tcp any host 208.74.[redacted] eq 6909
access-list 101 permit tcp any host 208.74.[redacted] eq 6910
access-list 101 permit tcp any host 208.74.[redacted] eq 6911
access-list 101 permit tcp any host 208.74.[redacted] eq 6912
access-list 101 permit tcp any host 208.74.[redacted] eq 6913
access-list 101 permit tcp any host 208.74.[redacted] eq 6914
access-list 101 permit tcp any host 208.74.[redacted] eq 6915
access-list 101 permit tcp any host 208.74.[redacted] eq 6916
access-list 101 permit tcp any host 208.74.[redacted] eq 6917
access-list 101 permit tcp any host 208.74.[redacted] eq 6918
access-list 101 permit tcp any host 208.74.[redacted] eq 6919
access-list 101 permit tcp any host 208.74.[redacted] eq 6920
access-list 101 permit tcp any host 208.74.[redacted] eq 6921
access-list 101 permit tcp any host 208.74.[redacted] eq 6922
access-list 101 permit tcp any host 208.74.[redacted] eq 6923
access-list 101 permit tcp any host 208.74.[redacted] eq 6924
access-list 101 permit tcp any host 208.74.[redacted] eq 6925
access-list 101 permit tcp any host 208.74.[redacted] eq 6926
access-list 101 permit tcp any host 208.74.[redacted] eq 6927
access-list 101 permit tcp any host 208.74.[redacted] eq 6928
access-list 101 permit tcp any host 208.74.[redacted] eq 6929
access-list 101 permit tcp any host 208.74.[redacted] eq 6930
access-list 101 permit tcp any host 208.74.[redacted] eq 6931
access-list 101 permit tcp any host 208.74.[redacted] eq 6932
access-list 101 permit tcp any host 208.74.[redacted] eq 6933
access-list 101 permit tcp any host 208.74.[redacted] eq 6934
access-list 101 permit tcp any host 208.74.[redacted] eq 6935
access-list 101 permit tcp any host 208.74.[redacted] eq 6936
access-list 101 permit tcp any host 208.74.[redacted] eq 6937
access-list 101 permit tcp any host 208.74.[redacted] eq 6938
access-list 101 permit tcp any host 208.74.[redacted] eq 6939
access-list 101 permit tcp any host 208.74.[redacted] eq 6940
access-list 101 permit tcp any host 208.74.[redacted] eq 6941
access-list 101 permit tcp any host 208.74.[redacted] eq 6942
access-list 101 permit tcp any host 208.74.[redacted] eq 6943
access-list 101 permit tcp any host 208.74.[redacted] eq 6944
access-list 101 permit tcp any host 208.74.[redacted] eq 6945
access-list 101 permit tcp any host 208.74.[redacted] eq 6946
access-list 101 permit tcp any host 208.74.[redacted] eq 6947
access-list 101 permit tcp any host 208.74.[redacted] eq 6948
access-list 101 permit tcp any host 208.74.[redacted] eq 6949
access-list 101 permit tcp any host 208.74.[redacted] eq 6950
access-list 101 permit tcp any host 208.74.[redacted] eq 6951
access-list 101 permit tcp any host 208.74.[redacted] eq 6952
access-list 101 permit tcp any host 208.74.[redacted] eq 6953
access-list 101 permit tcp any host 208.74.[redacted] eq 6954
access-list 101 permit tcp any host 208.74.[redacted] eq 6955
access-list 101 permit tcp any host 208.74.[redacted] eq 6956
access-list 101 permit tcp any host 208.74.[redacted] eq 6957
access-list 101 permit tcp any host 208.74.[redacted] eq 6958
access-list 101 permit tcp any host 208.74.[redacted] eq 6959
access-list 101 permit tcp any host 208.74.[redacted] eq 6960
access-list 101 permit tcp any host 208.74.[redacted] eq 6961
access-list 101 permit tcp any host 208.74.[redacted] eq 6962
access-list 101 permit tcp any host 208.74.[redacted] eq 6963
access-list 101 permit tcp any host 208.74.[redacted] eq 6964
access-list 101 permit tcp any host 208.74.[redacted] eq 6965
access-list 101 permit tcp any host 208.74.[redacted] eq 6966
access-list 101 permit tcp any host 208.74.[redacted] eq 6967
access-list 101 permit tcp any host 208.74.[redacted] eq 6968
access-list 101 permit tcp any host 208.74.[redacted] eq 6969
access-list 101 permit tcp any host 208.74.[redacted] eq 6970
access-list 101 permit tcp any host 208.74.[redacted] eq 6971
access-list 101 permit tcp any host 208.74.[redacted] eq 6972
access-list 101 permit tcp any host 208.74.[redacted] eq 6973
access-list 101 permit tcp any host 208.74.[redacted] eq 6974
access-list 101 permit tcp any host 208.74.[redacted] eq 6975
access-list 101 permit tcp any host 208.74.[redacted] eq 6976
access-list 101 permit tcp any host 208.74.[redacted] eq 6977
access-list 101 permit tcp any host 208.74.[redacted] eq 6978
access-list 101 permit tcp any host 208.74.[redacted] eq 6979
access-list 101 permit tcp any host 208.74.[redacted] eq 6980
access-list 101 permit tcp any host 208.74.[redacted] eq 6981
access-list 101 permit tcp any host 208.74.[redacted] eq 6982
access-list 101 permit tcp any host 208.74.[redacted] eq 6983
access-list 101 permit tcp any host 208.74.[redacted] eq 6984
access-list 101 permit tcp any host 208.74.[redacted] eq 6985
access-list 101 permit tcp any host 208.74.[redacted] eq 6986
access-list 101 permit tcp any host 208.74.[redacted] eq 6987
access-list 101 permit tcp any host 208.74.[redacted] eq 6988
access-list 101 permit tcp any host 208.74.[redacted] eq 6989
access-list 101 permit tcp any host 208.74.[redacted] eq 6990
access-list 101 permit tcp any host 208.74.[redacted] eq 6991
access-list 101 permit tcp any host 208.74.[redacted] eq 6992
access-list 101 permit tcp any host 208.74.[redacted] eq 6993
access-list 101 permit tcp any host 208.74.[redacted] eq 6994
access-list 101 permit tcp any host 208.74.[redacted] eq 6995
access-list 101 permit tcp any host 208.74.[redacted] eq 6996
access-list 101 permit tcp any host 208.74.[redacted] eq 6997
access-list 101 permit tcp any host 208.74.[redacted] eq 6998
access-list 101 permit tcp any host 208.74.[redacted] eq 6999
access-list 101 permit gre any host 208.74.[redacted]
access-list 101 remark Auto generated by SDM for NTP (123) 216.39.144.207
access-list 101 permit udp host 216.39.144.207 eq ntp host 208.74.[redacted] eq ntp
access-list 101 deny ip 192.168.1.0 0.0.0.255 any
access-list 101 permit icmp any host 208.74.[redacted] echo-reply
access-list 101 permit icmp any host 208.74.[redacted] time-exceeded
access-list 101 permit icmp any host 208.74.[redacted] unreachable
access-list 101 deny ip 10.0.0.0 0.255.255.255 any
access-list 101 deny ip 172.16.0.0 0.15.255.255 any
access-list 101 deny ip 192.168.0.0 0.0.255.255 any
access-list 101 deny ip 127.0.0.0 0.255.255.255 any
access-list 101 deny ip host 255.255.255.255 any
access-list 101 deny ip host 0.0.0.0 any
access-list 101 deny ip any any log
access-list 102 remark SDM_ACL Category=129
access-list 102 permit ip 192.168.1.0 0.0.0.255 any
access-list 102 permit ip host 67.170.236.160 any
access-list 102 permit udp any host 208.74.[redacted] eq 10081
access-list 102 permit tcp any host 208.74.[redacted] eq 10081
access-list 102 permit tcp any host 208.74.[redacted] eq 9988
access-list 102 permit tcp any host 208.74.[redacted] eq 5910
access-list 102 permit tcp any host 208.74.[redacted] eq 6346
access-list 102 permit udp any host 208.74.[redacted] eq 6346
access-list 102 permit udp any host 208.74.[redacted] eq 12346
access-list 102 permit tcp any host 208.74.[redacted] eq 12346
access-list 102 permit tcp any host 208.74.[redacted] eq 12345
access-list 102 permit udp any host 208.74.[redacted] eq 12345
access-list 102 permit udp any host 208.74.[redacted] eq 13853
access-list 102 permit udp any host 208.74.[redacted] eq 13852
access-list 102 permit udp any host 208.74.[redacted] eq 13854
access-list 102 permit udp any host 208.74.[redacted] eq 38341
access-list 102 permit tcp any host 208.74.[redacted] eq 38341
access-list 102 permit tcp any host 208.74.[redacted] eq 13854
access-list 102 permit tcp any host 208.74.[redacted] eq 10001
access-list 102 permit tcp any host 208.74.[redacted] eq 10002
access-list 102 permit tcp any host 208.74.[redacted] eq 6710
access-list 102 permit tcp any host 208.74.[redacted] eq 11888
access-list 102 permit udp any host 208.74.[redacted] eq 4672
access-list 102 permit tcp any host 208.74.[redacted] eq 4662
access-list 102 permit tcp any host 208.74.[redacted] eq 4711
access-list 102 permit tcp any host 208.74.[redacted] eq 10000
access-list 102 permit tcp any host 208.74.[redacted] eq 13852
access-list 102 permit tcp any host 208.74.[redacted] eq 13853
access-list 102 permit tcp any host 208.74.[redacted] eq 12344
access-list 102 permit udp any host 208.74.[redacted] eq 12344
access-list 102 permit tcp any host 208.74.[redacted] eq 3724
access-list 102 permit tcp any host 208.74.[redacted] eq 6112
access-list 102 permit tcp any host 208.74.[redacted] eq 6881
access-list 102 permit tcp any host 208.74.[redacted] eq 6882
access-list 102 permit tcp any host 208.74.[redacted] eq 6883
access-list 102 permit tcp any host 208.74.[redacted] eq 6884
access-list 102 permit tcp any host 208.74.[redacted] eq 6885
access-list 102 permit tcp any host 208.74.[redacted] eq 6886
access-list 102 permit tcp any host 208.74.[redacted] eq 6887
access-list 102 permit tcp any host 208.74.[redacted] eq 6888
access-list 102 permit tcp any host 208.74.[redacted] eq 6889
access-list 102 permit tcp any host 208.74.[redacted] eq 6890
access-list 102 permit tcp any host 208.74.[redacted] eq 6891
access-list 102 permit tcp any host 208.74.[redacted] eq 6892
access-list 102 permit tcp any host 208.74.[redacted] eq 6893
access-list 102 permit tcp any host 208.74.[redacted] eq 6894
access-list 102 permit tcp any host 208.74.[redacted] eq 6895
access-list 102 permit tcp any host 208.74.[redacted] eq 6896
access-list 102 permit tcp any host 208.74.[redacted] eq 6897
access-list 102 permit tcp any host 208.74.[redacted] eq 6898
access-list 102 permit tcp any host 208.74.[redacted] eq 6899
access-list 102 permit tcp any host 208.74.[redacted] eq 6900
access-list 102 permit tcp any host 208.74.[redacted] eq 6901
access-list 102 permit tcp any host 208.74.[redacted] eq 6902
access-list 102 permit tcp any host 208.74.[redacted] eq 6903
access-list 102 permit tcp any host 208.74.[redacted] eq 6904
access-list 102 permit tcp any host 208.74.[redacted] eq 6905
access-list 102 permit tcp any host 208.74.[redacted] eq 6906
access-list 102 permit tcp any host 208.74.[redacted] eq 6907
access-list 102 permit tcp any host 208.74.[redacted] eq 6908
access-list 102 permit tcp any host 208.74.[redacted] eq 6909
access-list 102 permit tcp any host 208.74.[redacted] eq 6910
access-list 102 permit tcp any host 208.74.[redacted] eq 6911
access-list 102 permit tcp any host 208.74.[redacted] eq 6912
access-list 102 permit tcp any host 208.74.[redacted] eq 6913
access-list 102 permit tcp any host 208.74.[redacted] eq 6914
access-list 102 permit tcp any host 208.74.[redacted] eq 6915
access-list 102 permit tcp any host 208.74.[redacted] eq 6916
access-list 102 permit tcp any host 208.74.[redacted] eq 6917
access-list 102 permit tcp any host 208.74.[redacted] eq 6918
access-list 102 permit tcp any host 208.74.[redacted] eq 6919
access-list 102 permit tcp any host 208.74.[redacted] eq 6920
access-list 102 permit tcp any host 208.74.[redacted] eq 6921
access-list 102 permit tcp any host 208.74.[redacted] eq 6922
access-list 102 permit tcp any host 208.74.[redacted] eq 6923
access-list 102 permit tcp any host 208.74.[redacted] eq 6924
access-list 102 permit tcp any host 208.74.[redacted] eq 6925
access-list 102 permit tcp any host 208.74.[redacted] eq 6926
access-list 102 permit tcp any host 208.74.[redacted] eq 6927
access-list 102 permit tcp any host 208.74.[redacted] eq 6928
access-list 102 permit tcp any host 208.74.[redacted] eq 6929
access-list 102 permit tcp any host 208.74.[redacted] eq 6930
access-list 102 permit tcp any host 208.74.[redacted] eq 6931
access-list 102 permit tcp any host 208.74.[redacted] eq 6932
access-list 102 permit tcp any host 208.74.[redacted] eq 6933
access-list 102 permit tcp any host 208.74.[redacted] eq 6934
access-list 102 permit tcp any host 208.74.[redacted] eq 6935
access-list 102 permit tcp any host 208.74.[redacted] eq 6936
access-list 102 permit tcp any host 208.74.[redacted] eq 6937
access-list 102 permit tcp any host 208.74.[redacted] eq 6938
access-list 102 permit tcp any host 208.74.[redacted] eq 6939
access-list 102 permit tcp any host 208.74.[redacted] eq 6940
access-list 102 permit tcp any host 208.74.[redacted] eq 6941
access-list 102 permit tcp any host 208.74.[redacted] eq 6942
access-list 102 permit tcp any host 208.74.[redacted] eq 6943
access-list 102 permit tcp any host 208.74.[redacted] eq 6944
access-list 102 permit tcp any host 208.74.[redacted] eq 6945
access-list 102 permit tcp any host 208.74.[redacted] eq 6946
access-list 102 permit tcp any host 208.74.[redacted] eq 6947
access-list 102 permit tcp any host 208.74.[redacted] eq 6948
access-list 102 permit tcp any host 208.74.[redacted] eq 6949
access-list 102 permit tcp any host 208.74.[redacted] eq 6950
access-list 102 permit tcp any host 208.74.[redacted] eq 6951
access-list 102 permit tcp any host 208.74.[redacted] eq 6952
access-list 102 permit tcp any host 208.74.[redacted] eq 6953
access-list 102 permit tcp any host 208.74.[redacted] eq 6954
access-list 102 permit tcp any host 208.74.[redacted] eq 6955
access-list 102 permit tcp any host 208.74.[redacted] eq 6956
access-list 102 permit tcp any host 208.74.[redacted] eq 6957
access-list 102 permit tcp any host 208.74.[redacted] eq 6958
access-list 102 permit tcp any host 208.74.[redacted] eq 6959
access-list 102 permit tcp any host 208.74.[redacted] eq 6960
access-list 102 permit tcp any host 208.74.[redacted] eq 6961
access-list 102 permit tcp any host 208.74.[redacted] eq 6962
access-list 102 permit tcp any host 208.74.[redacted] eq 6963
access-list 102 permit tcp any host 208.74.[redacted] eq 6964
access-list 102 permit tcp any host 208.74.[redacted] eq 6965
access-list 102 permit tcp any host 208.74.[redacted] eq 6966
access-list 102 permit tcp any host 208.74.[redacted] eq 6967
access-list 102 permit tcp any host 208.74.[redacted] eq 6968
access-list 102 permit tcp any host 208.74.[redacted] eq 6969
access-list 102 permit tcp any host 208.74.[redacted] eq 6970
access-list 102 permit tcp any host 208.74.[redacted] eq 6971
access-list 102 permit tcp any host 208.74.[redacted] eq 6972
access-list 102 permit tcp any host 208.74.[redacted] eq 6973
access-list 102 permit tcp any host 208.74.[redacted] eq 6974
access-list 102 permit tcp any host 208.74.[redacted] eq 6975
access-list 102 permit tcp any host 208.74.[redacted] eq 6976
access-list 102 permit tcp any host 208.74.[redacted] eq 6977
access-list 102 permit tcp any host 208.74.[redacted] eq 6978
access-list 102 permit tcp any host 208.74.[redacted] eq 6979
access-list 102 permit tcp any host 208.74.[redacted] eq 6980
access-list 102 permit tcp any host 208.74.[redacted] eq 6981
access-list 102 permit tcp any host 208.74.[redacted] eq 6982
access-list 102 permit tcp any host 208.74.[redacted] eq 6983
access-list 102 permit tcp any host 208.74.[redacted] eq 6984
access-list 102 permit tcp any host 208.74.[redacted] eq 6985
access-list 102 permit tcp any host 208.74.[redacted] eq 6986
access-list 102 permit tcp any host 208.74.[redacted] eq 6987
access-list 102 permit tcp any host 208.74.[redacted] eq 6988
access-list 102 permit tcp any host 208.74.[redacted] eq 6989
access-list 102 permit tcp any host 208.74.[redacted] eq 6990
access-list 102 permit tcp any host 208.74.[redacted] eq 6991
access-list 102 permit tcp any host 208.74.[redacted] eq 6992
access-list 102 permit tcp any host 208.74.[redacted] eq 6993
access-list 102 permit tcp any host 208.74.[redacted] eq 6994
access-list 102 permit tcp any host 208.74.[redacted] eq 6995
access-list 102 permit tcp any host 208.74.[redacted] eq 6996
access-list 102 permit tcp any host 208.74.[redacted] eq 6997
access-list 102 permit tcp any host 208.74.[redacted] eq 6998
access-list 102 permit tcp any host 208.74.[redacted] eq 6999
access-list 102 permit udp host 208.67.222.222 eq domain host 208.74.[redacted]
access-list 102 permit udp host 208.67.220.220 eq domain host 208.74.[redacted]
access-list 102 permit ip any any
access-list 2051 remark Auto generated by SDM Management Access feature
access-list 2051 remark SDM_ACL Category=1
access-list 2051 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq telnet
access-list 2051 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq 22
access-list 2051 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq www
access-list 2051 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq 443
access-list 2051 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq cmd
access-list 2051 deny tcp any host 192.168.1.1 eq telnet
access-list 2051 deny tcp any host 192.168.1.1 eq 22
access-list 2051 deny tcp any host 192.168.1.1 eq www
access-list 2051 deny tcp any host 192.168.1.1 eq 443
access-list 2051 deny tcp any host 192.168.1.1 eq cmd
access-list 2051 deny udp any host 192.168.1.1 eq snmp
access-list 2051 permit ip any any
no cdp run
!
!
!
!
control-plane
!
banner exec ^CCCCCCCCCCCCCCCCCCC
% Password expiration warning.
--------------------------
Cisco Router and Security Device Manager (SDM) is installed on this device and
it provides the default username "cisco" for one-time use. If you have already
used the username "cisco" to login to the router and your IOS image supports the
"one-time" user option, then this username has already expired. You will not be
able to login to the router with this username after you exit this session.
It is strongly suggested that you create a new username with a privilege level
of 15 using the following command.
username <myuser> privilege 15 secret 0 <mypassword>
Replace <myuser> and <mypassword> with the username and password you want to
use.
--------------------------
^C
banner login ^CCCCCCCCCCCCCCCCCCCAuthor
Disconnect IMMEDIATELY if you are not an authorized user!^C
!
line con 0
login authentication local_authen
no modem enable
transport output telnet
line aux 0
login authentication local_authen
transport output telnet
line vty 0 4
access-class 102 in
authorization exec local_author
login authentication local_authen
transport input telnet ssh
!
scheduler max-task-time 5000
scheduler allocate 4000 1000
scheduler interval 500
ntp clock-period 17175088
ntp server 129.6.15.28 source FastEthernet4 prefer
end
-----
version 12.4
no service pad
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
service password-encryption
service sequence-numbers
!
hostname nohostbar
!
boot-start-marker
boot-end-marker
!
security authentication failure rate 3 log
security passwords min-length 6
logging buffered 51200
logging console critical
enable secret 5 [redacted]
!
aaa new-model
!
!
aaa authentication login local_authen local
aaa authentication login ciscocp_vpn_xauth_ml_1 local
aaa authorization exec local_author local
aaa authorization network ciscocp_vpn_group_ml_1 local
!
!
aaa session-id common
clock timezone PST -8
clock summer-time PDT recurring
no ip source-route
no ip gratuitous-arps
ip cef
!
!
no ip dhcp use vrf connected
ip dhcp excluded-address 192.168.1.1 192.168.1.99
ip dhcp excluded-address 192.168.1.135 192.168.1.254
!
ip dhcp pool sdm-pool1
import all
network 192.168.1.0 255.255.255.0
dns-server 68.87.76.182 68.87.78.134
default-router 192.168.1.253
!
ip dhcp pool WINKY
host 192.168.1.106 255.255.255.0
client-identifier 0100.1903.0030.c4
!
ip dhcp pool ChairmanWIRED
host 192.168.1.107 255.255.255.0
client-identifier 0100.0f1f.1812.d2
!
ip dhcp pool SARA
host 192.168.1.110 255.255.255.0
client-identifier 0100.123f.aeed.3b
!
ip dhcp pool AVLP2
host 192.168.1.111 255.255.255.0
client-identifier 0100.a0b0.6556.90
!
ip dhcp pool MEDIABOY
host 192.168.1.109 255.255.255.0
client-identifier 0100.1320.48cd.9d
!
ip dhcp pool DLINKALI
host 192.168.1.103 255.255.255.0
client-identifier 0100.1195.b726.d2
!
ip dhcp pool DLINKMPT
host 192.168.1.100 255.255.255.0
client-identifier 0100.1195.ca38.e0
!
ip dhcp pool DLINKFR
host 192.168.1.102 255.255.255.0
client-identifier 0100.1195.eb66.15
!
ip dhcp pool ChairmanWIRELESS
host 192.168.1.108 255.255.255.0
client-identifier 0100.0b6b.358d.42
!
ip dhcp pool ALFA
host 192.168.1.114 255.255.255.0
client-identifier 0100.c0ca.26c7.55
!
ip dhcp pool SARALAPWL
host 192.168.1.116 255.255.255.0
client-identifier 0100.166f.be13.8e
!
ip dhcp pool SARALAP
host 192.168.1.117 255.255.255.0
client-identifier 0100.16d3.2f61.49
!
ip dhcp pool PHILBIN
host 192.168.1.104 255.255.255.0
client-identifier 0100.1c23.1f08.61
!
ip dhcp pool PHILBINWL
host 192.168.1.105 255.255.255.0
client-identifier 0100.1644.bc35.47
!
ip dhcp pool IPHONE3G
host 192.168.1.119 255.255.255.0
client-identifier 0100.21e9.4ff0.8b
!
ip dhcp pool SARAMACETH
host 192.168.1.120 255.255.255.0
client-identifier 0158.b035.f73a.6f
!
ip dhcp pool SARAMACWLESS
host 192.168.1.121 255.255.255.0
client-identifier 0158.b035.7d8b.1e
!
ip dhcp pool LauraTouch
host 192.168.1.122 255.255.255.0
client-identifier 0100.1ec2.532e.9d
!
ip dhcp pool APPLETV
host 192.168.1.123 255.255.255.0
client-identifier 0100.1f5b.a96f.ee
!
ip dhcp pool VLPPHONE
host 192.168.1.124 255.255.255.0
hardware-address 0004.f2a5.8985
!
ip dhcp pool DISHTVFR
host 192.168.1.112 255.255.255.0
client-identifier 0100.0889.8e20.ed
!
ip dhcp pool DISHTVBR
host 192.168.1.113 255.255.255.0
client-identifier 0100.0889.502d.af
!
ip dhcp pool IPHONE3GS
host 192.168.1.115 255.255.255.0
client-identifier 01c4.2c03.67a7.37
!
ip dhcp pool SaraIphone
host 192.168.1.101 255.255.255.0
client-identifier 01f8.1edf.4e85.db
!
ip dhcp pool PORTAROUTER
host 192.168.1.125 255.255.255.0
client-identifier 0100.2401.3d11.e4
!
ip dhcp pool NIKKI
host 192.168.1.126 255.255.255.0
client-identifier 0100.1b63.c0be.36
!
ip dhcp pool BLURAY
host 192.168.1.118 255.255.255.0
client-identifier 0100.16fb.0099.03
!
ip dhcp pool SamDS
host 192.168.1.127 255.255.255.0
client-identifier 0100.25a0.f1ac.7a
!
ip dhcp pool SaraTouch
host 192.168.1.128 255.255.255.0
client-identifier 0100.2332.5891.f2
!
ip dhcp pool AriIphone4
host 192.168.1.129 255.255.255.0
client-identifier 017c.c537.3bd2.f5
!
ip dhcp pool GRACIELLA
host 192.168.1.130 255.255.255.0
client-identifier 01e0.cb4e.b124.b8
!
ip dhcp pool CELTOWER
host 192.168.1.131 255.255.255.0
client-identifier 0144.5829.3ef3.ba
!
ip dhcp pool blackwii
host 192.168.1.132 255.255.255.0
client-identifier 018c.56c5.38c9.f3
!
ip dhcp pool LAURALAPWL
host 192.168.1.133 255.255.255.0
client-identifier 0100.24d7.5644.28
!
ip dhcp pool LAURALAPWIRED
host 192.168.1.134 255.255.255.0
client-identifier 015c.260a.151b.93
!
!
ip tcp synwait-time 10
no ip bootp server
ip name-server 208.67.220.220
ip name-server 208.67.222.222
ip ssh time-out 60
ip ssh authentication-retries 2
ip inspect max-incomplete high 20000000
ip inspect max-incomplete low 20000000
ip inspect one-minute high 100000000
ip inspect one-minute low 100000000
ip inspect tcp max-incomplete host 100000 block-time 0
ip inspect name SDM_LOW cuseeme
ip inspect name SDM_LOW dns
ip inspect name SDM_LOW ftp
ip inspect name SDM_LOW h323
ip inspect name SDM_LOW https
ip inspect name SDM_LOW icmp
ip inspect name SDM_LOW netshow
ip inspect name SDM_LOW rcmd
ip inspect name SDM_LOW realaudio
ip inspect name SDM_LOW rtsp
ip inspect name SDM_LOW sqlnet
ip inspect name SDM_LOW streamworks
ip inspect name SDM_LOW tftp
ip inspect name SDM_LOW tcp
ip inspect name SDM_LOW udp
ip inspect name SDM_LOW vdolive
!
multilink bundle-name authenticated
!
crypto pki trustpoint TP-self-signed-404758651
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certifi
revocation-check none
rsakeypair TP-self-signed-404758651
!
!
crypto pki certificate chain TP-self-signed-404758651
certificate self-signed 01
3082023F 308201A8 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
30312E30 2C060355 04031325 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 34303437 35383635 31301E17 0D313030 36313631 33313332
305A170D 32303031 30313030 30303030 5A303031 2E302C06 03550403 1325494F
532D5365 6C662D53 69676E65 642D4365 72746966 69636174 652D3430 34373538
36353130 819F300D 06092A86 4886F70D 01010105 0003818D 00308189 02818100
CA33ACAA A539309F 93478CB8 6710746D C0137632 AE9BC625 12A4E324 CEAC8FC1
B22A96B9 AA6B32CB 5A486AEC BE2BB54E 02A03228 83365EE9 72BEE864 A0739C5B
49C839FB 271F0B05 BD3A4DE0 B382B646 18CB5781 839337D2 42B3B024 FBD575D1
FDF7AD72 10429EDF 5974761A 836BE80B C12840EE D7B96156 61382343 AB066991
02030100 01A36930 67300F06 03551D13 0101FF04 05300301 01FF3014 0603551D
11040D30 0B82096E 6F686F73 74626172 301F0603 551D2304 18301680 147C1814
601ABAAD 1933D0ED CBE030DD 3D4F2B36 BD301D06 03551D0E 04160414 7C181460
1ABAAD19 33D0EDCB E030DD3D 4F2B36BD 300D0609 2A864886 F70D0101 04050003
8181006C D6D7527A 82EBE362 452EE6EC 594BA7D8 CFD0E0FD 22058F21 47AA7437
C181D428 938E008F 3E2CDA95 FDD284AE F80E6DB4 35082372 F97A84ED 5358883B
BD07DE1B A35EDCEB C466E19B E4396107 AC6A52A2 717704A9 8A14B3BF 012C5BD7
4F840B2B ECEA9F35 42B1A37F 7FC87538 B7011EE4 66B8D679 E17D3134 7D0DFC0A B7C36A
quit
crypto ctcp port 10000
!
!
username admin privilege 15 secret 5 [redacted]
username akahan privilege 15 secret 5 [redacted]
!
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
!
crypto isakmp client configuration group vpnusers
key [redacted]
pool SDM_POOL_1
include-local-lan
max-users 10
netmask 255.255.255.0
crypto isakmp profile ciscocp-ike-profile-1
match identity group vpnusers
client authentication list ciscocp_vpn_xauth_ml_1
isakmp authorization list ciscocp_vpn_group_ml_1
client configuration address respond
virtual-template 1
!
!
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
!
crypto ipsec profile CiscoCP_Profile1
set transform-set ESP-3DES-SHA
set isakmp-profile ciscocp-ike-profile-1
!
!
!
!
!
interface Null0
no ip unreachables
!
interface FastEthernet0
!
interface FastEthernet1
!
interface FastEthernet2
!
interface FastEthernet3
!
interface FastEthernet4
description $ES_WAN$$ETH-WAN$$FW_OUTSI
ip address 208.74.[redacted] 255.255.255.224
ip access-group 101 in
ip verify unicast reverse-path
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat outside
ip inspect SDM_LOW out
ip virtual-reassembly
ip route-cache flow
duplex auto
speed auto
!
interface Virtual-Template1 type tunnel
ip unnumbered FastEthernet4
tunnel mode ipsec ipv4
tunnel protection ipsec profile CiscoCP_Profile1
!
interface Vlan1
description $ETH-SW-LAUNCH$$INTF-INFO-
ip address 192.168.1.1 255.255.255.0
ip access-group 2051 in
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat inside
ip virtual-reassembly
ip route-cache flow
ip tcp adjust-mss 1452
!
ip local pool SDM_POOL_1 192.168.55.1 192.168.55.20
ip route 0.0.0.0 0.0.0.0 208.74.177.97 10
ip route 0.0.0.0 0.0.0.0 192.168.1.253 20
!
!
ip http server
ip http access-class 1
ip http authentication local
ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
ip nat inside source list 1 interface FastEthernet4 overload
ip nat inside source static udp 192.168.1.124 5060 interface FastEthernet4 5060
ip nat inside source static udp 192.168.1.124 5199 interface FastEthernet4 5199
ip nat inside source static udp 192.168.1.124 3479 interface FastEthernet4 3479
ip nat inside source static udp 192.168.1.124 15044 interface FastEthernet4 15044
ip nat inside source static tcp 192.168.1.199 6999 interface FastEthernet4 6999
ip nat inside source static tcp 192.168.1.199 6998 interface FastEthernet4 6998
ip nat inside source static tcp 192.168.1.199 6997 interface FastEthernet4 6997
ip nat inside source static tcp 192.168.1.199 6996 interface FastEthernet4 6996
ip nat inside source static tcp 192.168.1.199 6995 interface FastEthernet4 6995
ip nat inside source static tcp 192.168.1.199 6994 interface FastEthernet4 6994
ip nat inside source static tcp 192.168.1.199 6993 interface FastEthernet4 6993
ip nat inside source static tcp 192.168.1.199 6992 interface FastEthernet4 6992
ip nat inside source static tcp 192.168.1.199 6991 interface FastEthernet4 6991
ip nat inside source static tcp 192.168.1.199 6990 interface FastEthernet4 6990
ip nat inside source static tcp 192.168.1.199 6989 interface FastEthernet4 6989
ip nat inside source static tcp 192.168.1.199 6988 interface FastEthernet4 6988
ip nat inside source static tcp 192.168.1.199 6987 interface FastEthernet4 6987
ip nat inside source static tcp 192.168.1.199 6986 interface FastEthernet4 6986
ip nat inside source static tcp 192.168.1.199 6985 interface FastEthernet4 6985
ip nat inside source static tcp 192.168.1.199 6984 interface FastEthernet4 6984
ip nat inside source static tcp 192.168.1.199 6983 interface FastEthernet4 6983
ip nat inside source static tcp 192.168.1.199 6982 interface FastEthernet4 6982
ip nat inside source static tcp 192.168.1.199 6981 interface FastEthernet4 6981
ip nat inside source static tcp 192.168.1.199 6980 interface FastEthernet4 6980
ip nat inside source static tcp 192.168.1.199 6979 interface FastEthernet4 6979
ip nat inside source static tcp 192.168.1.199 6978 interface FastEthernet4 6978
ip nat inside source static tcp 192.168.1.199 6977 interface FastEthernet4 6977
ip nat inside source static tcp 192.168.1.199 6976 interface FastEthernet4 6976
ip nat inside source static tcp 192.168.1.199 6975 interface FastEthernet4 6975
ip nat inside source static tcp 192.168.1.199 6974 interface FastEthernet4 6974
ip nat inside source static tcp 192.168.1.199 6973 interface FastEthernet4 6973
ip nat inside source static tcp 192.168.1.199 6972 interface FastEthernet4 6972
ip nat inside source static tcp 192.168.1.199 6971 interface FastEthernet4 6971
ip nat inside source static tcp 192.168.1.199 6970 interface FastEthernet4 6970
ip nat inside source static tcp 192.168.1.199 6969 interface FastEthernet4 6969
ip nat inside source static tcp 192.168.1.199 6968 interface FastEthernet4 6968
ip nat inside source static tcp 192.168.1.199 6967 interface FastEthernet4 6967
ip nat inside source static tcp 192.168.1.199 6966 interface FastEthernet4 6966
ip nat inside source static tcp 192.168.1.199 6965 interface FastEthernet4 6965
ip nat inside source static tcp 192.168.1.199 6964 interface FastEthernet4 6964
ip nat inside source static tcp 192.168.1.199 6963 interface FastEthernet4 6963
ip nat inside source static tcp 192.168.1.199 6962 interface FastEthernet4 6962
ip nat inside source static tcp 192.168.1.199 6961 interface FastEthernet4 6961
ip nat inside source static tcp 192.168.1.199 6960 interface FastEthernet4 6960
ip nat inside source static tcp 192.168.1.199 6959 interface FastEthernet4 6959
ip nat inside source static tcp 192.168.1.199 6958 interface FastEthernet4 6958
ip nat inside source static tcp 192.168.1.199 6957 interface FastEthernet4 6957
ip nat inside source static tcp 192.168.1.199 6956 interface FastEthernet4 6956
ip nat inside source static tcp 192.168.1.199 6955 interface FastEthernet4 6955
ip nat inside source static tcp 192.168.1.199 6954 interface FastEthernet4 6954
ip nat inside source static tcp 192.168.1.199 6953 interface FastEthernet4 6953
ip nat inside source static tcp 192.168.1.199 6952 interface FastEthernet4 6952
ip nat inside source static tcp 192.168.1.199 6951 interface FastEthernet4 6951
ip nat inside source static tcp 192.168.1.199 6950 interface FastEthernet4 6950
ip nat inside source static tcp 192.168.1.199 6949 interface FastEthernet4 6949
ip nat inside source static tcp 192.168.1.199 6948 interface FastEthernet4 6948
ip nat inside source static tcp 192.168.1.199 6947 interface FastEthernet4 6947
ip nat inside source static tcp 192.168.1.199 6946 interface FastEthernet4 6946
ip nat inside source static tcp 192.168.1.199 6945 interface FastEthernet4 6945
ip nat inside source static tcp 192.168.1.199 6944 interface FastEthernet4 6944
ip nat inside source static tcp 192.168.1.199 6943 interface FastEthernet4 6943
ip nat inside source static tcp 192.168.1.199 6942 interface FastEthernet4 6942
ip nat inside source static tcp 192.168.1.199 6941 interface FastEthernet4 6941
ip nat inside source static tcp 192.168.1.199 6940 interface FastEthernet4 6940
ip nat inside source static tcp 192.168.1.199 6939 interface FastEthernet4 6939
ip nat inside source static tcp 192.168.1.199 6938 interface FastEthernet4 6938
ip nat inside source static tcp 192.168.1.199 6937 interface FastEthernet4 6937
ip nat inside source static tcp 192.168.1.199 6936 interface FastEthernet4 6936
ip nat inside source static tcp 192.168.1.199 6935 interface FastEthernet4 6935
ip nat inside source static tcp 192.168.1.199 6934 interface FastEthernet4 6934
ip nat inside source static tcp 192.168.1.199 6933 interface FastEthernet4 6933
ip nat inside source static tcp 192.168.1.199 6932 interface FastEthernet4 6932
ip nat inside source static tcp 192.168.1.199 6931 interface FastEthernet4 6931
ip nat inside source static tcp 192.168.1.199 6930 interface FastEthernet4 6930
ip nat inside source static tcp 192.168.1.199 6929 interface FastEthernet4 6929
ip nat inside source static tcp 192.168.1.199 6928 interface FastEthernet4 6928
ip nat inside source static tcp 192.168.1.199 6927 interface FastEthernet4 6927
ip nat inside source static tcp 192.168.1.199 6926 interface FastEthernet4 6926
ip nat inside source static tcp 192.168.1.199 6925 interface FastEthernet4 6925
ip nat inside source static tcp 192.168.1.199 6924 interface FastEthernet4 6924
ip nat inside source static tcp 192.168.1.199 6923 interface FastEthernet4 6923
ip nat inside source static tcp 192.168.1.199 6922 interface FastEthernet4 6922
ip nat inside source static tcp 192.168.1.199 6921 interface FastEthernet4 6921
ip nat inside source static tcp 192.168.1.199 6920 interface FastEthernet4 6920
ip nat inside source static tcp 192.168.1.199 6919 interface FastEthernet4 6919
ip nat inside source static tcp 192.168.1.199 6918 interface FastEthernet4 6918
ip nat inside source static tcp 192.168.1.199 6917 interface FastEthernet4 6917
ip nat inside source static tcp 192.168.1.199 6916 interface FastEthernet4 6916
ip nat inside source static tcp 192.168.1.199 6915 interface FastEthernet4 6915
ip nat inside source static tcp 192.168.1.199 6914 interface FastEthernet4 6914
ip nat inside source static tcp 192.168.1.199 6913 interface FastEthernet4 6913
ip nat inside source static tcp 192.168.1.199 6912 interface FastEthernet4 6912
ip nat inside source static tcp 192.168.1.199 6911 interface FastEthernet4 6911
ip nat inside source static tcp 192.168.1.199 6910 interface FastEthernet4 6910
ip nat inside source static tcp 192.168.1.199 6909 interface FastEthernet4 6909
ip nat inside source static tcp 192.168.1.199 6908 interface FastEthernet4 6908
ip nat inside source static tcp 192.168.1.199 6907 interface FastEthernet4 6907
ip nat inside source static tcp 192.168.1.199 6906 interface FastEthernet4 6906
ip nat inside source static tcp 192.168.1.199 6905 interface FastEthernet4 6905
ip nat inside source static tcp 192.168.1.199 6904 interface FastEthernet4 6904
ip nat inside source static tcp 192.168.1.199 6903 interface FastEthernet4 6903
ip nat inside source static tcp 192.168.1.199 6902 interface FastEthernet4 6902
ip nat inside source static tcp 192.168.1.199 6901 interface FastEthernet4 6901
ip nat inside source static tcp 192.168.1.199 6900 interface FastEthernet4 6900
ip nat inside source static tcp 192.168.1.199 6899 interface FastEthernet4 6899
ip nat inside source static tcp 192.168.1.199 6898 interface FastEthernet4 6898
ip nat inside source static tcp 192.168.1.199 6897 interface FastEthernet4 6897
ip nat inside source static tcp 192.168.1.199 6896 interface FastEthernet4 6896
ip nat inside source static tcp 192.168.1.199 6895 interface FastEthernet4 6895
ip nat inside source static tcp 192.168.1.199 6894 interface FastEthernet4 6894
ip nat inside source static tcp 192.168.1.199 6893 interface FastEthernet4 6893
ip nat inside source static tcp 192.168.1.199 6892 interface FastEthernet4 6892
ip nat inside source static tcp 192.168.1.199 6891 interface FastEthernet4 6891
ip nat inside source static tcp 192.168.1.199 6890 interface FastEthernet4 6890
ip nat inside source static tcp 192.168.1.199 6889 interface FastEthernet4 6889
ip nat inside source static tcp 192.168.1.199 6888 interface FastEthernet4 6888
ip nat inside source static tcp 192.168.1.199 6887 interface FastEthernet4 6887
ip nat inside source static tcp 192.168.1.199 6886 interface FastEthernet4 6886
ip nat inside source static tcp 192.168.1.199 6885 interface FastEthernet4 6885
ip nat inside source static tcp 192.168.1.199 6884 interface FastEthernet4 6884
ip nat inside source static tcp 192.168.1.199 6883 interface FastEthernet4 6883
ip nat inside source static tcp 192.168.1.199 6882 interface FastEthernet4 6882
ip nat inside source static tcp 192.168.1.199 6881 interface FastEthernet4 6881
ip nat inside source static tcp 192.168.1.199 6112 interface FastEthernet4 6112
ip nat inside source static tcp 192.168.1.199 3724 interface FastEthernet4 3724
ip nat inside source static udp 192.168.1.104 12344 interface FastEthernet4 12344
ip nat inside source static tcp 192.168.1.104 12344 interface FastEthernet4 12344
ip nat inside source static tcp 192.168.1.110 13853 interface FastEthernet4 13853
ip nat inside source static tcp 192.168.1.104 13852 interface FastEthernet4 13852
ip nat inside source static tcp 192.168.1.51 631 interface FastEthernet4 10000
ip nat inside source static tcp 192.168.1.109 4711 interface FastEthernet4 4711
ip nat inside source static tcp 192.168.1.109 4662 interface FastEthernet4 4662
ip nat inside source static udp 192.168.1.109 4672 interface FastEthernet4 4672
ip nat inside source static tcp 192.168.1.109 11888 interface FastEthernet4 11888
ip nat inside source static tcp 192.168.1.109 6710 interface FastEthernet4 6710
ip nat inside source static tcp 192.168.1.51 9100 interface FastEthernet4 10001
ip nat inside source static tcp 192.168.1.52 9100 interface FastEthernet4 10002
ip nat inside source static tcp 192.168.1.106 13854 interface FastEthernet4 13854
ip nat inside source static tcp 192.168.1.115 38341 interface FastEthernet4 38341
ip nat inside source static udp 192.168.1.115 38341 interface FastEthernet4 38341
ip nat inside source static udp 192.168.1.106 13854 interface FastEthernet4 13854
ip nat inside source static udp 192.168.1.104 13852 interface FastEthernet4 13852
ip nat inside source static udp 192.168.1.110 13853 interface FastEthernet4 13853
ip nat inside source static udp 192.168.1.110 12345 interface FastEthernet4 12345
ip nat inside source static tcp 192.168.1.110 12345 interface FastEthernet4 12345
ip nat inside source static tcp 192.168.1.109 12346 interface FastEthernet4 12346
ip nat inside source static udp 192.168.1.109 12346 interface FastEthernet4 12346
ip nat inside source static udp 192.168.1.104 6346 interface FastEthernet4 6346
ip nat inside source static tcp 192.168.1.104 6346 interface FastEthernet4 6346
ip nat inside source static tcp 192.168.1.104 5910 interface FastEthernet4 5910
ip nat inside source static tcp 192.168.1.109 9988 interface FastEthernet4 9988
ip nat inside source static tcp 192.168.1.109 10081 interface FastEthernet4 10081
ip nat inside source static udp 192.168.1.109 10081 interface FastEthernet4 10081
ip nat inside source static tcp 192.168.1.109 65500 interface FastEthernet4 65500
ip nat inside source static udp 192.168.1.109 444 interface FastEthernet4 444
ip nat inside source static tcp 192.168.1.109 444 interface FastEthernet4 444
ip nat inside source static udp 192.168.1.104 5500 interface FastEthernet4 5500
ip nat inside source static tcp 192.168.1.104 5500 interface FastEthernet4 5500
ip nat inside source static tcp 192.168.1.109 5905 interface FastEthernet4 5905
!
logging trap debugging
access-list 1 permit 67.170.236.160
access-list 1 remark Auto generated by SDM Management Access feature
access-list 1 remark SDM_ACL Category=1
access-list 1 permit 192.168.1.0 0.0.0.255
access-list 100 remark auto generated by SDM firewall configuration
access-list 100 remark SDM_ACL Category=0
access-list 100 deny ip 208.74.177.96 0.0.0.31 any
access-list 100 deny ip host 255.255.255.255 any
access-list 100 deny ip 127.0.0.0 0.255.255.255 any
access-list 100 permit ip any any
access-list 101 remark CCP_ACL Category=1
access-list 101 permit udp any host 208.74.[redacted] eq 5060
access-list 101 permit udp any host 208.74.[redacted] eq non500-isakmp
access-list 101 permit udp any host 208.74.[redacted] eq isakmp
access-list 101 permit esp any host 208.74.[redacted]
access-list 101 permit ahp any host 208.74.[redacted]
access-list 101 permit udp any host 208.74.[redacted] eq 5199
access-list 101 permit udp any host 208.74.[redacted] eq 3479
access-list 101 permit udp any host 208.74.[redacted] eq 15044
access-list 101 remark auto generated by SDM firewall configuration
access-list 101 permit tcp any host 208.74.[redacted] eq 444
access-list 101 permit udp any host 208.74.[redacted] eq 444
access-list 101 permit tcp host 24.7.127.6 host 208.74.[redacted] eq telnet
access-list 101 permit tcp host 24.7.127.6 host 208.74.[redacted] eq 22
access-list 101 permit tcp host 24.7.127.6 host 208.74.[redacted] eq www
access-list 101 permit tcp host 24.7.127.6 host 208.74.[redacted] eq 443
access-list 101 permit tcp host 24.7.127.6 host 208.74.[redacted] eq cmd
access-list 101 deny udp any host 208.74.[redacted] eq snmp
access-list 101 permit udp host 208.67.222.222 eq domain any
access-list 101 permit udp host 204.11.224.14 eq domain any
access-list 101 permit udp host 204.11.231.14 eq domain any
access-list 101 permit udp host 208.67.220.220 eq domain any
access-list 101 permit udp any host 208.74.[redacted] eq 10081
access-list 101 permit tcp any host 208.74.[redacted] eq 10081
access-list 101 permit tcp any host 208.74.[redacted] eq 9988
access-list 101 permit tcp any host 208.74.[redacted] eq 5500
access-list 101 permit tcp any host 208.74.[redacted] eq 5910
access-list 101 permit tcp any host 208.74.[redacted] eq 6346
access-list 101 permit udp any host 208.74.[redacted] eq 6346
access-list 101 permit udp any host 208.74.[redacted] eq 12346
access-list 101 permit tcp any host 208.74.[redacted] eq 12346
access-list 101 permit tcp any host 208.74.[redacted] eq 12345
access-list 101 permit udp any host 208.74.[redacted] eq 12345
access-list 101 permit udp any host 208.74.[redacted] eq 13853
access-list 101 permit udp any host 208.74.[redacted] eq 13852
access-list 101 permit udp any host 208.74.[redacted] eq 13854
access-list 101 permit udp any host 208.74.[redacted] eq 38341
access-list 101 permit tcp any host 208.74.[redacted] eq 38341
access-list 101 permit tcp any host 208.74.[redacted] eq 13854
access-list 101 permit tcp any host 208.74.[redacted] eq 10001
access-list 101 permit tcp any host 208.74.[redacted] eq 10002
access-list 101 permit tcp any host 208.74.[redacted] eq 6710
access-list 101 permit tcp any host 208.74.[redacted] eq 65500
access-list 101 permit tcp any host 208.74.[redacted] eq 11888
access-list 101 permit udp any host 208.74.[redacted] eq 4672
access-list 101 permit tcp any host 208.74.[redacted] eq 4662
access-list 101 permit tcp any host 208.74.[redacted] eq 4711
access-list 101 permit tcp any host 208.74.[redacted] eq 10000
access-list 101 permit tcp any host 208.74.[redacted] eq 13852
access-list 101 permit tcp any host 208.74.[redacted] eq 5905
access-list 101 permit tcp any host 208.74.[redacted] eq 13853
access-list 101 permit tcp any host 208.74.[redacted] eq 12344
access-list 101 permit udp any host 208.74.[redacted] eq 12344
access-list 101 permit tcp any host 208.74.[redacted] eq 3724
access-list 101 permit tcp any host 208.74.[redacted] eq 6112
access-list 101 permit tcp any host 208.74.[redacted] eq 6881
access-list 101 permit tcp any host 208.74.[redacted] eq 6882
access-list 101 permit tcp any host 208.74.[redacted] eq 6883
access-list 101 permit tcp any host 208.74.[redacted] eq 6884
access-list 101 permit tcp any host 208.74.[redacted] eq 6885
access-list 101 permit tcp any host 208.74.[redacted] eq 6886
access-list 101 permit tcp any host 208.74.[redacted] eq 6887
access-list 101 permit tcp any host 208.74.[redacted] eq 6888
access-list 101 permit tcp any host 208.74.[redacted] eq 6889
access-list 101 permit tcp any host 208.74.[redacted] eq 6890
access-list 101 permit tcp any host 208.74.[redacted] eq 6891
access-list 101 permit tcp any host 208.74.[redacted] eq 6892
access-list 101 permit tcp any host 208.74.[redacted] eq 6893
access-list 101 permit tcp any host 208.74.[redacted] eq 6894
access-list 101 permit tcp any host 208.74.[redacted] eq 6895
access-list 101 permit tcp any host 208.74.[redacted] eq 6896
access-list 101 permit tcp any host 208.74.[redacted] eq 6897
access-list 101 permit tcp any host 208.74.[redacted] eq 6898
access-list 101 permit tcp any host 208.74.[redacted] eq 6899
access-list 101 permit tcp any host 208.74.[redacted] eq 6900
access-list 101 permit tcp any host 208.74.[redacted] eq 6901
access-list 101 permit tcp any host 208.74.[redacted] eq 6902
access-list 101 permit tcp any host 208.74.[redacted] eq 6903
access-list 101 permit tcp any host 208.74.[redacted] eq 6904
access-list 101 permit tcp any host 208.74.[redacted] eq 6905
access-list 101 permit tcp any host 208.74.[redacted] eq 6906
access-list 101 permit tcp any host 208.74.[redacted] eq 6907
access-list 101 permit tcp any host 208.74.[redacted] eq 6908
access-list 101 permit tcp any host 208.74.[redacted] eq 6909
access-list 101 permit tcp any host 208.74.[redacted] eq 6910
access-list 101 permit tcp any host 208.74.[redacted] eq 6911
access-list 101 permit tcp any host 208.74.[redacted] eq 6912
access-list 101 permit tcp any host 208.74.[redacted] eq 6913
access-list 101 permit tcp any host 208.74.[redacted] eq 6914
access-list 101 permit tcp any host 208.74.[redacted] eq 6915
access-list 101 permit tcp any host 208.74.[redacted] eq 6916
access-list 101 permit tcp any host 208.74.[redacted] eq 6917
access-list 101 permit tcp any host 208.74.[redacted] eq 6918
access-list 101 permit tcp any host 208.74.[redacted] eq 6919
access-list 101 permit tcp any host 208.74.[redacted] eq 6920
access-list 101 permit tcp any host 208.74.[redacted] eq 6921
access-list 101 permit tcp any host 208.74.[redacted] eq 6922
access-list 101 permit tcp any host 208.74.[redacted] eq 6923
access-list 101 permit tcp any host 208.74.[redacted] eq 6924
access-list 101 permit tcp any host 208.74.[redacted] eq 6925
access-list 101 permit tcp any host 208.74.[redacted] eq 6926
access-list 101 permit tcp any host 208.74.[redacted] eq 6927
access-list 101 permit tcp any host 208.74.[redacted] eq 6928
access-list 101 permit tcp any host 208.74.[redacted] eq 6929
access-list 101 permit tcp any host 208.74.[redacted] eq 6930
access-list 101 permit tcp any host 208.74.[redacted] eq 6931
access-list 101 permit tcp any host 208.74.[redacted] eq 6932
access-list 101 permit tcp any host 208.74.[redacted] eq 6933
access-list 101 permit tcp any host 208.74.[redacted] eq 6934
access-list 101 permit tcp any host 208.74.[redacted] eq 6935
access-list 101 permit tcp any host 208.74.[redacted] eq 6936
access-list 101 permit tcp any host 208.74.[redacted] eq 6937
access-list 101 permit tcp any host 208.74.[redacted] eq 6938
access-list 101 permit tcp any host 208.74.[redacted] eq 6939
access-list 101 permit tcp any host 208.74.[redacted] eq 6940
access-list 101 permit tcp any host 208.74.[redacted] eq 6941
access-list 101 permit tcp any host 208.74.[redacted] eq 6942
access-list 101 permit tcp any host 208.74.[redacted] eq 6943
access-list 101 permit tcp any host 208.74.[redacted] eq 6944
access-list 101 permit tcp any host 208.74.[redacted] eq 6945
access-list 101 permit tcp any host 208.74.[redacted] eq 6946
access-list 101 permit tcp any host 208.74.[redacted] eq 6947
access-list 101 permit tcp any host 208.74.[redacted] eq 6948
access-list 101 permit tcp any host 208.74.[redacted] eq 6949
access-list 101 permit tcp any host 208.74.[redacted] eq 6950
access-list 101 permit tcp any host 208.74.[redacted] eq 6951
access-list 101 permit tcp any host 208.74.[redacted] eq 6952
access-list 101 permit tcp any host 208.74.[redacted] eq 6953
access-list 101 permit tcp any host 208.74.[redacted] eq 6954
access-list 101 permit tcp any host 208.74.[redacted] eq 6955
access-list 101 permit tcp any host 208.74.[redacted] eq 6956
access-list 101 permit tcp any host 208.74.[redacted] eq 6957
access-list 101 permit tcp any host 208.74.[redacted] eq 6958
access-list 101 permit tcp any host 208.74.[redacted] eq 6959
access-list 101 permit tcp any host 208.74.[redacted] eq 6960
access-list 101 permit tcp any host 208.74.[redacted] eq 6961
access-list 101 permit tcp any host 208.74.[redacted] eq 6962
access-list 101 permit tcp any host 208.74.[redacted] eq 6963
access-list 101 permit tcp any host 208.74.[redacted] eq 6964
access-list 101 permit tcp any host 208.74.[redacted] eq 6965
access-list 101 permit tcp any host 208.74.[redacted] eq 6966
access-list 101 permit tcp any host 208.74.[redacted] eq 6967
access-list 101 permit tcp any host 208.74.[redacted] eq 6968
access-list 101 permit tcp any host 208.74.[redacted] eq 6969
access-list 101 permit tcp any host 208.74.[redacted] eq 6970
access-list 101 permit tcp any host 208.74.[redacted] eq 6971
access-list 101 permit tcp any host 208.74.[redacted] eq 6972
access-list 101 permit tcp any host 208.74.[redacted] eq 6973
access-list 101 permit tcp any host 208.74.[redacted] eq 6974
access-list 101 permit tcp any host 208.74.[redacted] eq 6975
access-list 101 permit tcp any host 208.74.[redacted] eq 6976
access-list 101 permit tcp any host 208.74.[redacted] eq 6977
access-list 101 permit tcp any host 208.74.[redacted] eq 6978
access-list 101 permit tcp any host 208.74.[redacted] eq 6979
access-list 101 permit tcp any host 208.74.[redacted] eq 6980
access-list 101 permit tcp any host 208.74.[redacted] eq 6981
access-list 101 permit tcp any host 208.74.[redacted] eq 6982
access-list 101 permit tcp any host 208.74.[redacted] eq 6983
access-list 101 permit tcp any host 208.74.[redacted] eq 6984
access-list 101 permit tcp any host 208.74.[redacted] eq 6985
access-list 101 permit tcp any host 208.74.[redacted] eq 6986
access-list 101 permit tcp any host 208.74.[redacted] eq 6987
access-list 101 permit tcp any host 208.74.[redacted] eq 6988
access-list 101 permit tcp any host 208.74.[redacted] eq 6989
access-list 101 permit tcp any host 208.74.[redacted] eq 6990
access-list 101 permit tcp any host 208.74.[redacted] eq 6991
access-list 101 permit tcp any host 208.74.[redacted] eq 6992
access-list 101 permit tcp any host 208.74.[redacted] eq 6993
access-list 101 permit tcp any host 208.74.[redacted] eq 6994
access-list 101 permit tcp any host 208.74.[redacted] eq 6995
access-list 101 permit tcp any host 208.74.[redacted] eq 6996
access-list 101 permit tcp any host 208.74.[redacted] eq 6997
access-list 101 permit tcp any host 208.74.[redacted] eq 6998
access-list 101 permit tcp any host 208.74.[redacted] eq 6999
access-list 101 permit gre any host 208.74.[redacted]
access-list 101 remark Auto generated by SDM for NTP (123) 216.39.144.207
access-list 101 permit udp host 216.39.144.207 eq ntp host 208.74.[redacted] eq ntp
access-list 101 deny ip 192.168.1.0 0.0.0.255 any
access-list 101 permit icmp any host 208.74.[redacted] echo-reply
access-list 101 permit icmp any host 208.74.[redacted] time-exceeded
access-list 101 permit icmp any host 208.74.[redacted] unreachable
access-list 101 deny ip 10.0.0.0 0.255.255.255 any
access-list 101 deny ip 172.16.0.0 0.15.255.255 any
access-list 101 deny ip 192.168.0.0 0.0.255.255 any
access-list 101 deny ip 127.0.0.0 0.255.255.255 any
access-list 101 deny ip host 255.255.255.255 any
access-list 101 deny ip host 0.0.0.0 any
access-list 101 deny ip any any log
access-list 102 remark SDM_ACL Category=129
access-list 102 permit ip 192.168.1.0 0.0.0.255 any
access-list 102 permit ip host 67.170.236.160 any
access-list 102 permit udp any host 208.74.[redacted] eq 10081
access-list 102 permit tcp any host 208.74.[redacted] eq 10081
access-list 102 permit tcp any host 208.74.[redacted] eq 9988
access-list 102 permit tcp any host 208.74.[redacted] eq 5910
access-list 102 permit tcp any host 208.74.[redacted] eq 6346
access-list 102 permit udp any host 208.74.[redacted] eq 6346
access-list 102 permit udp any host 208.74.[redacted] eq 12346
access-list 102 permit tcp any host 208.74.[redacted] eq 12346
access-list 102 permit tcp any host 208.74.[redacted] eq 12345
access-list 102 permit udp any host 208.74.[redacted] eq 12345
access-list 102 permit udp any host 208.74.[redacted] eq 13853
access-list 102 permit udp any host 208.74.[redacted] eq 13852
access-list 102 permit udp any host 208.74.[redacted] eq 13854
access-list 102 permit udp any host 208.74.[redacted] eq 38341
access-list 102 permit tcp any host 208.74.[redacted] eq 38341
access-list 102 permit tcp any host 208.74.[redacted] eq 13854
access-list 102 permit tcp any host 208.74.[redacted] eq 10001
access-list 102 permit tcp any host 208.74.[redacted] eq 10002
access-list 102 permit tcp any host 208.74.[redacted] eq 6710
access-list 102 permit tcp any host 208.74.[redacted] eq 11888
access-list 102 permit udp any host 208.74.[redacted] eq 4672
access-list 102 permit tcp any host 208.74.[redacted] eq 4662
access-list 102 permit tcp any host 208.74.[redacted] eq 4711
access-list 102 permit tcp any host 208.74.[redacted] eq 10000
access-list 102 permit tcp any host 208.74.[redacted] eq 13852
access-list 102 permit tcp any host 208.74.[redacted] eq 13853
access-list 102 permit tcp any host 208.74.[redacted] eq 12344
access-list 102 permit udp any host 208.74.[redacted] eq 12344
access-list 102 permit tcp any host 208.74.[redacted] eq 3724
access-list 102 permit tcp any host 208.74.[redacted] eq 6112
access-list 102 permit tcp any host 208.74.[redacted] eq 6881
access-list 102 permit tcp any host 208.74.[redacted] eq 6882
access-list 102 permit tcp any host 208.74.[redacted] eq 6883
access-list 102 permit tcp any host 208.74.[redacted] eq 6884
access-list 102 permit tcp any host 208.74.[redacted] eq 6885
access-list 102 permit tcp any host 208.74.[redacted] eq 6886
access-list 102 permit tcp any host 208.74.[redacted] eq 6887
access-list 102 permit tcp any host 208.74.[redacted] eq 6888
access-list 102 permit tcp any host 208.74.[redacted] eq 6889
access-list 102 permit tcp any host 208.74.[redacted] eq 6890
access-list 102 permit tcp any host 208.74.[redacted] eq 6891
access-list 102 permit tcp any host 208.74.[redacted] eq 6892
access-list 102 permit tcp any host 208.74.[redacted] eq 6893
access-list 102 permit tcp any host 208.74.[redacted] eq 6894
access-list 102 permit tcp any host 208.74.[redacted] eq 6895
access-list 102 permit tcp any host 208.74.[redacted] eq 6896
access-list 102 permit tcp any host 208.74.[redacted] eq 6897
access-list 102 permit tcp any host 208.74.[redacted] eq 6898
access-list 102 permit tcp any host 208.74.[redacted] eq 6899
access-list 102 permit tcp any host 208.74.[redacted] eq 6900
access-list 102 permit tcp any host 208.74.[redacted] eq 6901
access-list 102 permit tcp any host 208.74.[redacted] eq 6902
access-list 102 permit tcp any host 208.74.[redacted] eq 6903
access-list 102 permit tcp any host 208.74.[redacted] eq 6904
access-list 102 permit tcp any host 208.74.[redacted] eq 6905
access-list 102 permit tcp any host 208.74.[redacted] eq 6906
access-list 102 permit tcp any host 208.74.[redacted] eq 6907
access-list 102 permit tcp any host 208.74.[redacted] eq 6908
access-list 102 permit tcp any host 208.74.[redacted] eq 6909
access-list 102 permit tcp any host 208.74.[redacted] eq 6910
access-list 102 permit tcp any host 208.74.[redacted] eq 6911
access-list 102 permit tcp any host 208.74.[redacted] eq 6912
access-list 102 permit tcp any host 208.74.[redacted] eq 6913
access-list 102 permit tcp any host 208.74.[redacted] eq 6914
access-list 102 permit tcp any host 208.74.[redacted] eq 6915
access-list 102 permit tcp any host 208.74.[redacted] eq 6916
access-list 102 permit tcp any host 208.74.[redacted] eq 6917
access-list 102 permit tcp any host 208.74.[redacted] eq 6918
access-list 102 permit tcp any host 208.74.[redacted] eq 6919
access-list 102 permit tcp any host 208.74.[redacted] eq 6920
access-list 102 permit tcp any host 208.74.[redacted] eq 6921
access-list 102 permit tcp any host 208.74.[redacted] eq 6922
access-list 102 permit tcp any host 208.74.[redacted] eq 6923
access-list 102 permit tcp any host 208.74.[redacted] eq 6924
access-list 102 permit tcp any host 208.74.[redacted] eq 6925
access-list 102 permit tcp any host 208.74.[redacted] eq 6926
access-list 102 permit tcp any host 208.74.[redacted] eq 6927
access-list 102 permit tcp any host 208.74.[redacted] eq 6928
access-list 102 permit tcp any host 208.74.[redacted] eq 6929
access-list 102 permit tcp any host 208.74.[redacted] eq 6930
access-list 102 permit tcp any host 208.74.[redacted] eq 6931
access-list 102 permit tcp any host 208.74.[redacted] eq 6932
access-list 102 permit tcp any host 208.74.[redacted] eq 6933
access-list 102 permit tcp any host 208.74.[redacted] eq 6934
access-list 102 permit tcp any host 208.74.[redacted] eq 6935
access-list 102 permit tcp any host 208.74.[redacted] eq 6936
access-list 102 permit tcp any host 208.74.[redacted] eq 6937
access-list 102 permit tcp any host 208.74.[redacted] eq 6938
access-list 102 permit tcp any host 208.74.[redacted] eq 6939
access-list 102 permit tcp any host 208.74.[redacted] eq 6940
access-list 102 permit tcp any host 208.74.[redacted] eq 6941
access-list 102 permit tcp any host 208.74.[redacted] eq 6942
access-list 102 permit tcp any host 208.74.[redacted] eq 6943
access-list 102 permit tcp any host 208.74.[redacted] eq 6944
access-list 102 permit tcp any host 208.74.[redacted] eq 6945
access-list 102 permit tcp any host 208.74.[redacted] eq 6946
access-list 102 permit tcp any host 208.74.[redacted] eq 6947
access-list 102 permit tcp any host 208.74.[redacted] eq 6948
access-list 102 permit tcp any host 208.74.[redacted] eq 6949
access-list 102 permit tcp any host 208.74.[redacted] eq 6950
access-list 102 permit tcp any host 208.74.[redacted] eq 6951
access-list 102 permit tcp any host 208.74.[redacted] eq 6952
access-list 102 permit tcp any host 208.74.[redacted] eq 6953
access-list 102 permit tcp any host 208.74.[redacted] eq 6954
access-list 102 permit tcp any host 208.74.[redacted] eq 6955
access-list 102 permit tcp any host 208.74.[redacted] eq 6956
access-list 102 permit tcp any host 208.74.[redacted] eq 6957
access-list 102 permit tcp any host 208.74.[redacted] eq 6958
access-list 102 permit tcp any host 208.74.[redacted] eq 6959
access-list 102 permit tcp any host 208.74.[redacted] eq 6960
access-list 102 permit tcp any host 208.74.[redacted] eq 6961
access-list 102 permit tcp any host 208.74.[redacted] eq 6962
access-list 102 permit tcp any host 208.74.[redacted] eq 6963
access-list 102 permit tcp any host 208.74.[redacted] eq 6964
access-list 102 permit tcp any host 208.74.[redacted] eq 6965
access-list 102 permit tcp any host 208.74.[redacted] eq 6966
access-list 102 permit tcp any host 208.74.[redacted] eq 6967
access-list 102 permit tcp any host 208.74.[redacted] eq 6968
access-list 102 permit tcp any host 208.74.[redacted] eq 6969
access-list 102 permit tcp any host 208.74.[redacted] eq 6970
access-list 102 permit tcp any host 208.74.[redacted] eq 6971
access-list 102 permit tcp any host 208.74.[redacted] eq 6972
access-list 102 permit tcp any host 208.74.[redacted] eq 6973
access-list 102 permit tcp any host 208.74.[redacted] eq 6974
access-list 102 permit tcp any host 208.74.[redacted] eq 6975
access-list 102 permit tcp any host 208.74.[redacted] eq 6976
access-list 102 permit tcp any host 208.74.[redacted] eq 6977
access-list 102 permit tcp any host 208.74.[redacted] eq 6978
access-list 102 permit tcp any host 208.74.[redacted] eq 6979
access-list 102 permit tcp any host 208.74.[redacted] eq 6980
access-list 102 permit tcp any host 208.74.[redacted] eq 6981
access-list 102 permit tcp any host 208.74.[redacted] eq 6982
access-list 102 permit tcp any host 208.74.[redacted] eq 6983
access-list 102 permit tcp any host 208.74.[redacted] eq 6984
access-list 102 permit tcp any host 208.74.[redacted] eq 6985
access-list 102 permit tcp any host 208.74.[redacted] eq 6986
access-list 102 permit tcp any host 208.74.[redacted] eq 6987
access-list 102 permit tcp any host 208.74.[redacted] eq 6988
access-list 102 permit tcp any host 208.74.[redacted] eq 6989
access-list 102 permit tcp any host 208.74.[redacted] eq 6990
access-list 102 permit tcp any host 208.74.[redacted] eq 6991
access-list 102 permit tcp any host 208.74.[redacted] eq 6992
access-list 102 permit tcp any host 208.74.[redacted] eq 6993
access-list 102 permit tcp any host 208.74.[redacted] eq 6994
access-list 102 permit tcp any host 208.74.[redacted] eq 6995
access-list 102 permit tcp any host 208.74.[redacted] eq 6996
access-list 102 permit tcp any host 208.74.[redacted] eq 6997
access-list 102 permit tcp any host 208.74.[redacted] eq 6998
access-list 102 permit tcp any host 208.74.[redacted] eq 6999
access-list 102 permit udp host 208.67.222.222 eq domain host 208.74.[redacted]
access-list 102 permit udp host 208.67.220.220 eq domain host 208.74.[redacted]
access-list 102 permit ip any any
access-list 2051 remark Auto generated by SDM Management Access feature
access-list 2051 remark SDM_ACL Category=1
access-list 2051 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq telnet
access-list 2051 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq 22
access-list 2051 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq www
access-list 2051 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq 443
access-list 2051 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq cmd
access-list 2051 deny tcp any host 192.168.1.1 eq telnet
access-list 2051 deny tcp any host 192.168.1.1 eq 22
access-list 2051 deny tcp any host 192.168.1.1 eq www
access-list 2051 deny tcp any host 192.168.1.1 eq 443
access-list 2051 deny tcp any host 192.168.1.1 eq cmd
access-list 2051 deny udp any host 192.168.1.1 eq snmp
access-list 2051 permit ip any any
no cdp run
!
!
!
!
control-plane
!
banner exec ^CCCCCCCCCCCCCCCCCCC
% Password expiration warning.
--------------------------
Cisco Router and Security Device Manager (SDM) is installed on this device and
it provides the default username "cisco" for one-time use. If you have already
used the username "cisco" to login to the router and your IOS image supports the
"one-time" user option, then this username has already expired. You will not be
able to login to the router with this username after you exit this session.
It is strongly suggested that you create a new username with a privilege level
of 15 using the following command.
username <myuser> privilege 15 secret 0 <mypassword>
Replace <myuser> and <mypassword> with the username and password you want to
use.
--------------------------
^C
banner login ^CCCCCCCCCCCCCCCCCCCAuthor
Disconnect IMMEDIATELY if you are not an authorized user!^C
!
line con 0
login authentication local_authen
no modem enable
transport output telnet
line aux 0
login authentication local_authen
transport output telnet
line vty 0 4
access-class 102 in
authorization exec local_author
login authentication local_authen
transport input telnet ssh
!
scheduler max-task-time 5000
scheduler allocate 4000 1000
scheduler interval 500
ntp clock-period 17175088
ntp server 129.6.15.28 source FastEthernet4 prefer
end
Akahan, as I can see you're not familiar with the Cisco CLI.
I think that this document will help a lot.
All you can do through the CCA.
CCA can for free download from the Cisco site
SBCS-Teleworker-using-871W-ISR-3.pdf
I think that this document will help a lot.
All you can do through the CCA.
CCA can for free download from the Cisco site
SBCS-Teleworker-using-871W-ISR-3.pdf
ASKER
uniplast,
That's not really very helpful, since the system described in that document involves another piece of hardware, a UC520, and it's the UC520 that seems to have the critical configuration option, "Enable internet access on remote site."
That's not really very helpful, since the system described in that document involves another piece of hardware, a UC520, and it's the UC520 that seems to have the critical configuration option, "Enable internet access on remote site."
Are you trying to access devices that have static nat's? Are you able to ping anything that does not have a static nat?
On you cisco vpn client, go to status menu, click statistics... on the route details tab, what are the secured routes?
Your ACL's and static NAT's are gigantic...
On you cisco vpn client, go to status menu, click statistics... on the route details tab, what are the secured routes?
Your ACL's and static NAT's are gigantic...
ASKER
Hi -
I know, the ACL's and static NATs are gigantic. :( Each device on my network is assigned a static nat, so I "always know where it is," and the DHCP pool is limited to the number of devices for which there are static nats, so no device can join the network without me knowing about it and assigning a static nat to it.
The ACL's are big, too, because a bunch of ports have to be forwarded for eMule and the like.
I'm not actually interested in accessing ANY devices on the network via the VPN. The ONLY thing I want the VPN to do is allow me to connect to the router from outside the network (e.g., a coffee shop) and relay internet communications through the router, so that I have a secure internet connection from the coffee shop.
Attached is a screenshot of the route details tab in the Cisco vpn client... it DOES seem that this is the problem, actually, or part of it.
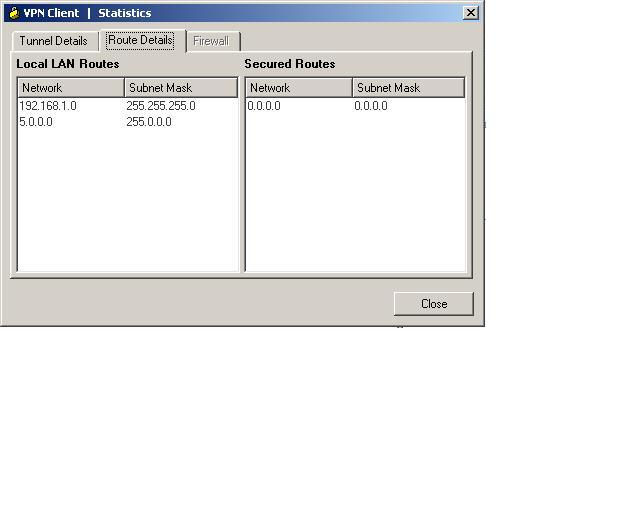
I know, the ACL's and static NATs are gigantic. :( Each device on my network is assigned a static nat, so I "always know where it is," and the DHCP pool is limited to the number of devices for which there are static nats, so no device can join the network without me knowing about it and assigning a static nat to it.
The ACL's are big, too, because a bunch of ports have to be forwarded for eMule and the like.
I'm not actually interested in accessing ANY devices on the network via the VPN. The ONLY thing I want the VPN to do is allow me to connect to the router from outside the network (e.g., a coffee shop) and relay internet communications through the router, so that I have a secure internet connection from the coffee shop.
Attached is a screenshot of the route details tab in the Cisco vpn client... it DOES seem that this is the problem, actually, or part of it.

The only traffic that's going to be encrypted is the traffic that traverses the tunnel. I don't think this is going to accomplish what you want it to accomplish the way you have it configured. When I initially responded to your post, I apparently missed the fact that you want all of your internet traffic to relay through your router...
Anyway, you're going to have to do a loopback config that creates a "router on a stick" topology.
This should cover everything:
http://www.cisco.com/en/US/products/sw/secursw/ps2308/products_configuration_example09186a008073b06b.shtml
As for your current config; your interesting traffic isn't defined correctly, and isn't being passed to your client. If you do "show crypto ipsec sa", you'll probably see encaps but no decaps, which indicates one-way traffic. Probably not worth fixing though, since your whole configuration is going to change.
Anyway, you're going to have to do a loopback config that creates a "router on a stick" topology.
This should cover everything:
http://www.cisco.com/en/US/products/sw/secursw/ps2308/products_configuration_example09186a008073b06b.shtml
As for your current config; your interesting traffic isn't defined correctly, and isn't being passed to your client. If you do "show crypto ipsec sa", you'll probably see encaps but no decaps, which indicates one-way traffic. Probably not worth fixing though, since your whole configuration is going to change.
ASKER
Thanks very much. So here's my plan: I'll get rid of all the stuff in my current configuration that was inserted to set up the VPN, and keep my current LAN address range of 192.168.1.XXX, and then add the VPN in the manner described by the document you've referred me to.
I have a few questions about particular lines in that document:
"!--- Apply the crypto map on the interface.
interface FastEthernet1/0
ip address 172.16.1.1 255.255.255.0"
Would I want to substitute my router's WAN address in place of 172.16.1.1? Or is that something else?
-------
!--- Create a pool of addresses to be
!--- assigned to the VPN Clients.
!
ip local pool ippool 192.168.1.1 192.168.1.2
ip http server
no ip http secure-server
Is this right, given that my existing LAN is in the 192.168.1.XXX range? Would I just omit this section, since I already have an internal LAN defined? The "network diagram" that appears at the top of the document you've referred me to doesn't mention a 192.168.... network at all, so I'm not sure how this fits in.
------------------------
Thanks! I really appreciate your patience with me, and with this. If I get it working, I wish there was a way to award 2,000 points.
I have a few questions about particular lines in that document:
"!--- Apply the crypto map on the interface.
interface FastEthernet1/0
ip address 172.16.1.1 255.255.255.0"
Would I want to substitute my router's WAN address in place of 172.16.1.1? Or is that something else?
-------
!--- Create a pool of addresses to be
!--- assigned to the VPN Clients.
!
ip local pool ippool 192.168.1.1 192.168.1.2
ip http server
no ip http secure-server
Is this right, given that my existing LAN is in the 192.168.1.XXX range? Would I just omit this section, since I already have an internal LAN defined? The "network diagram" that appears at the top of the document you've referred me to doesn't mention a 192.168.... network at all, so I'm not sure how this fits in.
------------------------
Thanks! I really appreciate your patience with me, and with this. If I get it working, I wish there was a way to award 2,000 points.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Working on it, sorry for the delay, will keep you posted...
ASKER
I expect your solution is probably right...but I ended up installing OpenVPN (free!) on an unused laptop I have sitting around, and that gave me a VPN of exactly the type I want in minutes, no fuss, no muss.
Unless the 871 offers a clientless VPN like SSL you will need some client software on your XP laptop,