dt3itsteam
asked on
FortiGate 100A DMZ configuration problem
Hi Experts,
I have what i believe is a fairly simple problem, but because i am no expert with Firewalls and certainly not Fortigate firewalls i am having quite a time of it.
First off, Fortinet Support are utterly useless, so dont go there.
The Fortigate 100A has two DMZ interfaces, this server is connected to the DMZ2.
I have policies in place to be able to RDP to that machine from the Internal LAN of the FW.
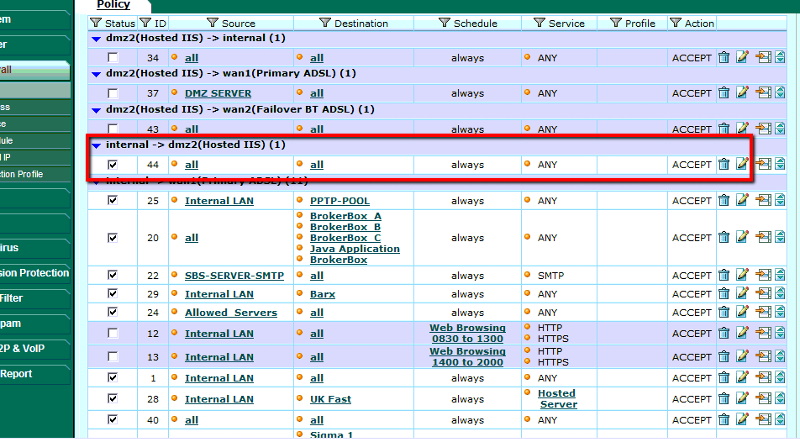
We are implementing an Microsoft IIS server and need to access the server from the trusted LAN to the DMZ2 zone. I have created the rule to allow all LAN traffic to the DMZ zone at all times for all services.
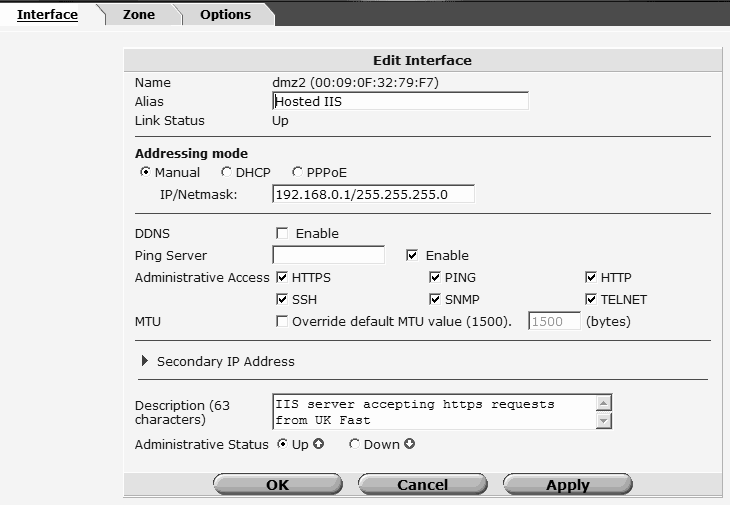
The DMZ interface is configured on 192.168.0.1/24 the DMZ server (windows 2003) is on 192.168.0.2/24
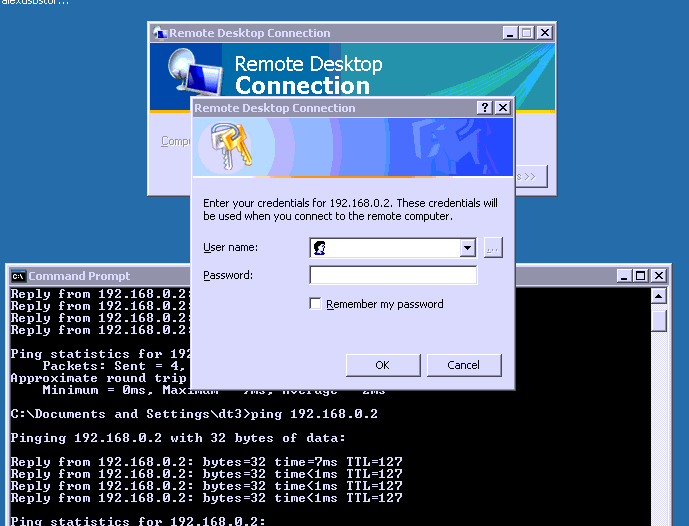
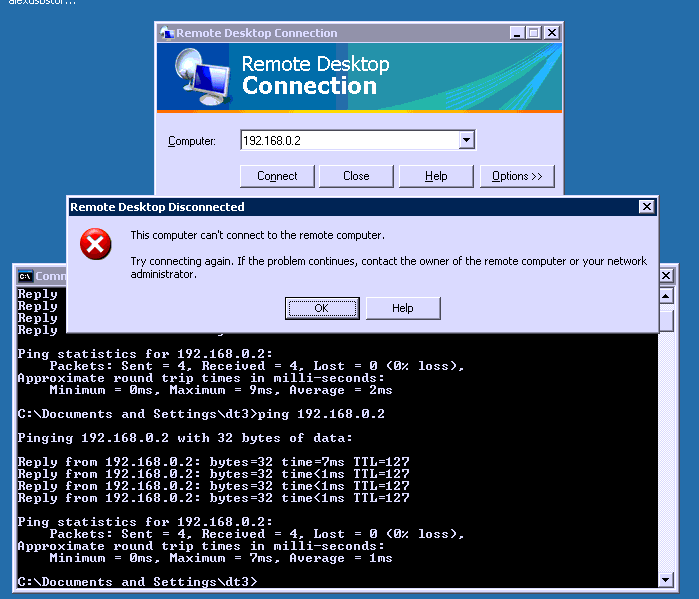
I can receive ping's from the trusted interface to the Windows 2003 server (192.168.0.2), but cannot connect to any available services on this host. (RDP, SMB, etc..). The host also cannot reach the internet.
Some images here for the config of the FW at present.
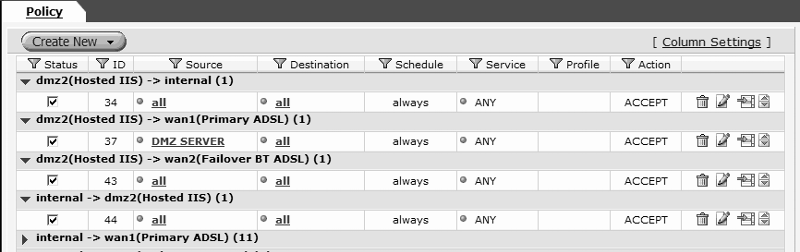
Any ideas how i can get traffic through to this Server?
I have what i believe is a fairly simple problem, but because i am no expert with Firewalls and certainly not Fortigate firewalls i am having quite a time of it.
First off, Fortinet Support are utterly useless, so dont go there.
The Fortigate 100A has two DMZ interfaces, this server is connected to the DMZ2.
I have policies in place to be able to RDP to that machine from the Internal LAN of the FW.
We are implementing an Microsoft IIS server and need to access the server from the trusted LAN to the DMZ2 zone. I have created the rule to allow all LAN traffic to the DMZ zone at all times for all services.
The DMZ interface is configured on 192.168.0.1/24 the DMZ server (windows 2003) is on 192.168.0.2/24
I can receive ping's from the trusted interface to the Windows 2003 server (192.168.0.2), but cannot connect to any available services on this host. (RDP, SMB, etc..). The host also cannot reach the internet.
Some images here for the config of the FW at present.


Any ideas how i can get traffic through to this Server?
Is this server physically connected to the DMZ2 interface to via a switch? Also is there a route table some where on the FW? I have no experince of Fortigate however I am assuing it is not much different then the old style Sonicwall UI.
Is your IIS server on DMZ2 able to connect to the internet without issue?
Are you RDP'ing to the server name or IP from the internal?
Maybe try turning on NAT on int -> DMZ2 and see if you get different results.
Are you RDP'ing to the server name or IP from the internal?
Maybe try turning on NAT on int -> DMZ2 and see if you get different results.
ASKER
Apologies for late return, one has been busy! But thanks for your responses!
Sun12345:
Server is plugged directly into the interface on the FW, no switch.
I have attached, what i think is the info you are looking for :) (blanked ex IPs)
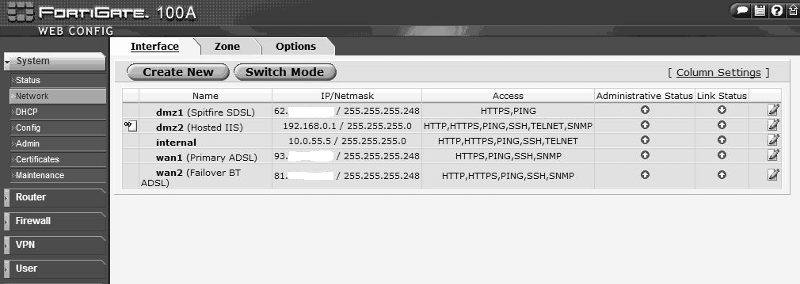
iworks-uworks:
- no internet access at all
- tried RDP via hostname and IP no results on either. I get a login prompt tho, but fails after i "login". Pings are constant tho. RDP is enabled on the Server and the Windows FW is off.
- I will try the NAT thing.
Sun12345:
Server is plugged directly into the interface on the FW, no switch.
I have attached, what i think is the info you are looking for :) (blanked ex IPs)

iworks-uworks:
- no internet access at all
- tried RDP via hostname and IP no results on either. I get a login prompt tho, but fails after i "login". Pings are constant tho. RDP is enabled on the Server and the Windows FW is off.
- I will try the NAT thing.
Can you post a screenshot of your policy config under firewall? That will show us why you can't ping or get out to the internet.
Let me clarify (you already posted the ruels config), but can you post the config of each policy that we are dealing with? Thanks.
ASKER
So you can ping now? And RDP?
So what's left, just having that machine on DMZ2 connect out through the internet?
So what's left, just having that machine on DMZ2 connect out through the internet?
ASKER
Ive always been able to ping, nothing else.
RDP brings up a login box but goes no where after that.
:)
RDP brings up a login box but goes no where after that.
:)
You get the login box as shown below (RDP-Login), but when you type a username/password nothing happens? No error message?
When your DMZ2 to WAN1 rule is enabled, can you confirm your rule is configured as the screen shot below (NAT enabled, and make it all to all to test in case there is a problem with your address).
RDP-Login.PNG
DMZ-WAN1.PNG
When your DMZ2 to WAN1 rule is enabled, can you confirm your rule is configured as the screen shot below (NAT enabled, and make it all to all to test in case there is a problem with your address).
RDP-Login.PNG
DMZ-WAN1.PNG
I do not see an issue with configuration. Silly suggestion. Can you please confirm if you can RDP to the server from same LAN (connect a switch to this server and a PC). I have waisted more then a day trying to toubleshoot a issue on router only to realized that Windows firewall on laptop was not letting me ping.
Sun has a good suggestion. Could you also post IPCONFIG from that server?
ASKER
Morning Gents!
I will give that a go, but please note:
1) I can ping the server ok, through the FW.
2) Windows FW is disabled on DMZ server
3) I do not have physical access to the DMZ server at the moment, which i will need to get the IPCONFIG details.
It will take a few days to get that info because of that and the fact that i have another project about to kick off.
I will post as soon as i have the info for you.
Thanks again Gentleman!
I will give that a go, but please note:
1) I can ping the server ok, through the FW.
2) Windows FW is disabled on DMZ server
3) I do not have physical access to the DMZ server at the moment, which i will need to get the IPCONFIG details.
It will take a few days to get that info because of that and the fact that i have another project about to kick off.
I will post as soon as i have the info for you.
Thanks again Gentleman!
ASKER
Right, i got access sooner than i thought.
IPconfig:
Also, RDP from the same subnet works 100% ok. I stuck a switch on DMZ and connected Server + Laptop to Switch and could RDP to Server from laptop ok. No problems.
IPconfig:
C:\Documents and Settings\Administrator>ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . . : HFL0066
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Unknown
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
Ethernet adapter DMZ:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Broadcom NetXtreme Gigabit Ethernet #2
Physical Address. . . . . . . . . : 00-18-8B-F9-5A-A0
DHCP Enabled. . . . . . . . . . . : No
IP Address. . . . . . . . . . . . : 192.168.0.2
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.0.1
DNS Servers . . . . . . . . . . . : 192.168.0.1
8.8.8.8
C:\Documents and Settings\Administrator>
Also, RDP from the same subnet works 100% ok. I stuck a switch on DMZ and connected Server + Laptop to Switch and could RDP to Server from laptop ok. No problems.
Here is from the Fortigate admin guide:
Status Select the check box to enable a policy or deselect it to disable a policy.
If you look at the Firewall policy screenshot that you have posted on 11/23/10 07:18 AM, ID: 34197212, the policies for DMZ are not selected. It seems when you do not have a check box against them, there status is disable.
Check this and let us know how it goes?
Status Select the check box to enable a policy or deselect it to disable a policy.
If you look at the Firewall policy screenshot that you have posted on 11/23/10 07:18 AM, ID: 34197212, the policies for DMZ are not selected. It seems when you do not have a check box against them, there status is disable.
Check this and let us know how it goes?
dt3itsteam: Any update on this? Curious if it was only the check box missing on ACLs.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Got the solution from the 3rd party Support desk