Mulitcasting with Acronis Snap Deploy across 1 vlan
In our Melbourne office we have a managed linksys srw2024 24 port gb switch which connects to a cisco 878 router.
There is a office cubical area which has 4 dumb linksys gb switches which between them connects 10 devices; laptops, our DC box, and our imaging server. The imaging server has acronis snap deploy as well as controlling our MSP anti virus service. This single office area only has 1 patch cable connecting it to the managed linksys switch. The other offices on the floor connect directly to this managed switch.
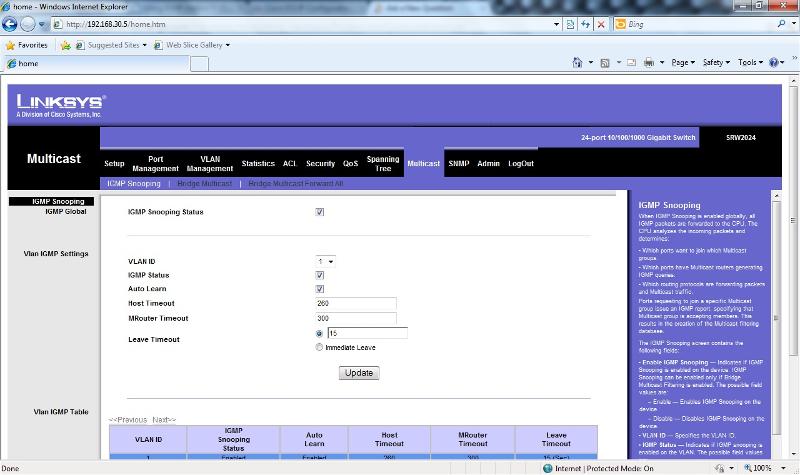
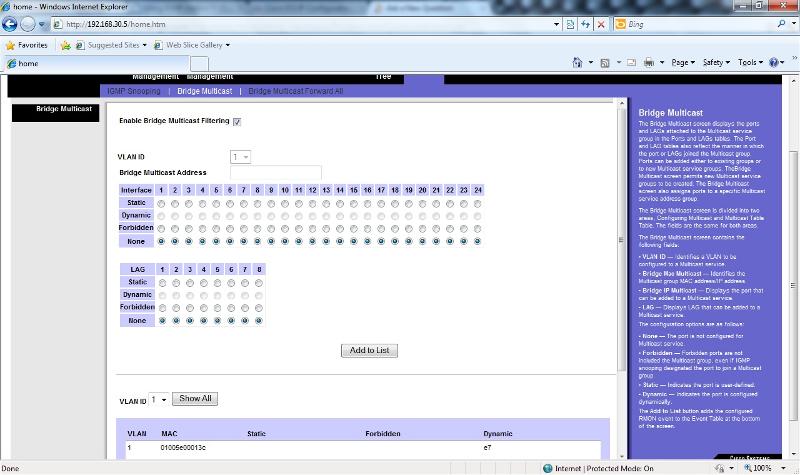
When I use snap deploy to image pc's for rollout it floods our network and our voip phones die also. I have enabled multicasting/igmp snooping on the managed linksys (see screen shots).
On the cisco 878 router we have 2 vlans, vlan1 is for the ppl in the office and vlan2 is for the phones/connection to another switch.
I have read a heap of material on the subject and all of it relates to multiple routers between the multicast source and the host. This isn't my scenario. My multicast source is connected to a dumb switch which in turn is connected to the managed linksys switch.
I have followed article such as this one:
http://www.ciscoarticles.com/Cisco-IOS/1251.html
With out much success..
This is where I need some advice or understand of what I need to do to get imaging working on our network without causing the network to 'go down' (extremely slow web browsing, copying files, voip phones go silence etc)
The 878 router is 192.168.30.1
The managed linksys is 192.68.30.5
The imaging box is 192.168.30.248
Acronis Snap Deploy uses the multicast address of 239.255.219.45 or essentially 239.0.0.0 0.255.255.255
Part of the router config:
ip name-server 192.168.30.243
ip name-server 192.168.30.1
ip multicast-routing
interface FastEthernet0
!
interface FastEthernet1
!
interface FastEthernet2
switchport access vlan 2
!
interface FastEthernet3
switchport access vlan 2
interface Vlan1
ip address 192.168.30.1 255.255.255.0
ip nbar protocol-discovery
ip flow ingress
ip flow egress
ip pim sparse-dense-mode
ip nat inside
ip virtual-reassembly
ip route-cache flow
ip igmp version 3
load-interval 60
priority-group 1
!
interface Vlan2
ip address 10.11.80.5 255.255.0.0
ip access-group 102 in
ip nbar protocol-discovery
ip nat inside
ip virtual-reassembly
load-interval 60
priority-group 1
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 Dialer1
ip route 192.168.31.0 255.255.255.0 192.168.30.2
ip route 192.168.32.0 255.255.255.0 192.168.30.2
ip route 192.168.33.0 255.255.255.0 192.168.30.2
ip route 192.168.34.0 255.255.255.0 192.168.30.2
ip route 192.168.35.0 255.255.255.0 Dialer1
ip route 210.247.203.161 255.255.255.255 Dialer1
ip http access-class 70
ip http secure-server
ip pim rp-address 192.168.30.1
ip pim ssm range 19
ip nat translation timeout 3600
no ip nat service sip tcp port 5060
no ip nat service sip udp port 5060
....
access-list 19 permit 239.0.0.0 0.255.255.255
access-list 110 remark HIGH PRIORITY TRAFFIC
access-list 110 permit tcp any any eq 6100
access-list 110 permit udp any any eq 6000
access-list 110 permit udp any any range 9000 9001
access-list 110 permit udp any any range 30000 30031
access-list 110 permit icmp any any echo
access-list 110 permit udp any any eq 5060
access-list 110 permit tcp any any eq 5180
access-list 110 permit tcp any any eq 8000
access-list 110 permit tcp any any range 10000 10100
access-list 110 permit tcp any any eq 3389
access-list 111 remark MEDIUM PRIORITY TRAFFIC
access-list 111 permit tcp any any eq telnet
access-list 111 permit tcp any any eq 22
access-list 111 permit tcp any any eq smtp
access-list 111 permit tcp any any eq pop3
access-list 111 permit tcp any any eq www
access-list 111 permit tcp any any eq 443
access-list 111 permit tcp any any eq 1723
access-list 111 permit tcp any any eq 49400
access-list 111 permit tcp any any eq 3306
access-list 111 permit tcp any any eq ftp
access-list 111 permit tcp any any eq ftp-data
access-list 111 permit tcp any any eq 3389
dialer-list 1 protocol ip permit
priority-list 1 protocol ip high list 110
priority-list 1 protocol ip medium list 111
As you can see I am lost.. when I run any commands to such as:
A17#sh ip igmp groups
IGMP Connected Group Membership
Group Address Interface Uptime Expires Last Reporter Group Accounted
224.0.1.60 Vlan1 1w1d 00:02:27 192.168.30.205
224.0.1.40 Vlan1 1w1d stopped 192.168.30.1
It doesn't show my hosts...I would expect this?
Help!!
 linksys-multicasting-3.jpg
linksys-multicasting-3.jpg
There is a office cubical area which has 4 dumb linksys gb switches which between them connects 10 devices; laptops, our DC box, and our imaging server. The imaging server has acronis snap deploy as well as controlling our MSP anti virus service. This single office area only has 1 patch cable connecting it to the managed linksys switch. The other offices on the floor connect directly to this managed switch.
When I use snap deploy to image pc's for rollout it floods our network and our voip phones die also. I have enabled multicasting/igmp snooping on the managed linksys (see screen shots).
On the cisco 878 router we have 2 vlans, vlan1 is for the ppl in the office and vlan2 is for the phones/connection to another switch.
I have read a heap of material on the subject and all of it relates to multiple routers between the multicast source and the host. This isn't my scenario. My multicast source is connected to a dumb switch which in turn is connected to the managed linksys switch.
I have followed article such as this one:
http://www.ciscoarticles.com/Cisco-IOS/1251.html
With out much success..
This is where I need some advice or understand of what I need to do to get imaging working on our network without causing the network to 'go down' (extremely slow web browsing, copying files, voip phones go silence etc)
The 878 router is 192.168.30.1
The managed linksys is 192.68.30.5
The imaging box is 192.168.30.248
Acronis Snap Deploy uses the multicast address of 239.255.219.45 or essentially 239.0.0.0 0.255.255.255
Part of the router config:
ip name-server 192.168.30.243
ip name-server 192.168.30.1
ip multicast-routing
interface FastEthernet0
!
interface FastEthernet1
!
interface FastEthernet2
switchport access vlan 2
!
interface FastEthernet3
switchport access vlan 2
interface Vlan1
ip address 192.168.30.1 255.255.255.0
ip nbar protocol-discovery
ip flow ingress
ip flow egress
ip pim sparse-dense-mode
ip nat inside
ip virtual-reassembly
ip route-cache flow
ip igmp version 3
load-interval 60
priority-group 1
!
interface Vlan2
ip address 10.11.80.5 255.255.0.0
ip access-group 102 in
ip nbar protocol-discovery
ip nat inside
ip virtual-reassembly
load-interval 60
priority-group 1
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 Dialer1
ip route 192.168.31.0 255.255.255.0 192.168.30.2
ip route 192.168.32.0 255.255.255.0 192.168.30.2
ip route 192.168.33.0 255.255.255.0 192.168.30.2
ip route 192.168.34.0 255.255.255.0 192.168.30.2
ip route 192.168.35.0 255.255.255.0 Dialer1
ip route 210.247.203.161 255.255.255.255 Dialer1
ip http access-class 70
ip http secure-server
ip pim rp-address 192.168.30.1
ip pim ssm range 19
ip nat translation timeout 3600
no ip nat service sip tcp port 5060
no ip nat service sip udp port 5060
....
access-list 19 permit 239.0.0.0 0.255.255.255
access-list 110 remark HIGH PRIORITY TRAFFIC
access-list 110 permit tcp any any eq 6100
access-list 110 permit udp any any eq 6000
access-list 110 permit udp any any range 9000 9001
access-list 110 permit udp any any range 30000 30031
access-list 110 permit icmp any any echo
access-list 110 permit udp any any eq 5060
access-list 110 permit tcp any any eq 5180
access-list 110 permit tcp any any eq 8000
access-list 110 permit tcp any any range 10000 10100
access-list 110 permit tcp any any eq 3389
access-list 111 remark MEDIUM PRIORITY TRAFFIC
access-list 111 permit tcp any any eq telnet
access-list 111 permit tcp any any eq 22
access-list 111 permit tcp any any eq smtp
access-list 111 permit tcp any any eq pop3
access-list 111 permit tcp any any eq www
access-list 111 permit tcp any any eq 443
access-list 111 permit tcp any any eq 1723
access-list 111 permit tcp any any eq 49400
access-list 111 permit tcp any any eq 3306
access-list 111 permit tcp any any eq ftp
access-list 111 permit tcp any any eq ftp-data
access-list 111 permit tcp any any eq 3389
dialer-list 1 protocol ip permit
priority-list 1 protocol ip high list 110
priority-list 1 protocol ip medium list 111
As you can see I am lost.. when I run any commands to such as:
A17#sh ip igmp groups
IGMP Connected Group Membership
Group Address Interface Uptime Expires Last Reporter Group Accounted
224.0.1.60 Vlan1 1w1d 00:02:27 192.168.30.205
224.0.1.40 Vlan1 1w1d stopped 192.168.30.1
It doesn't show my hosts...I would expect this?
Help!!


 linksys-multicasting-3.jpg
linksys-multicasting-3.jpg
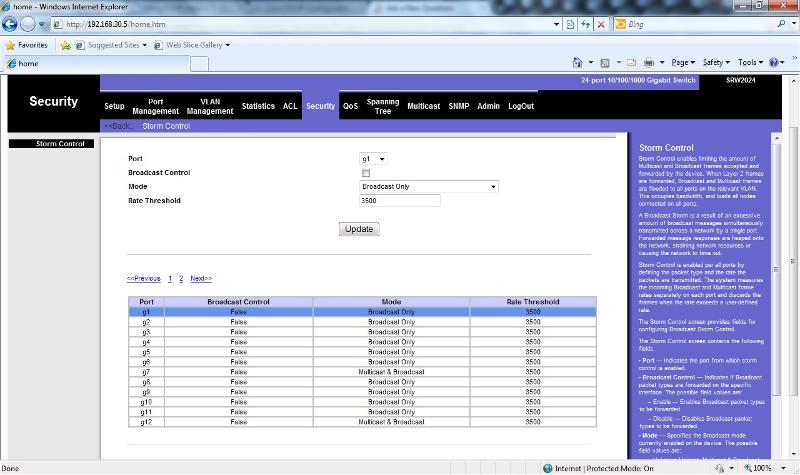
Have you checked that the "dumb linksys gb switches" doesn't have broadcast storm prevention as default?
ASKER
The 8 port linksys gb switches don't have any interfaces to them. From my understanding the multicast packets should pass through. The only reference I have to broadcast storm are from the screen shots attached (which I can only assume what I have enabled is correct).
Regarding the separate VLAN, due to the cabling to the office area it can only be on the same VLAN. From everything I have read this shouldn't be a problem as IGMP snooping should stop multicast packets flooding the network.
If that's the only way then I will have the organise another cable run etc which will be very expensive...hence why I am looking down this route.
Regarding the separate VLAN, due to the cabling to the office area it can only be on the same VLAN. From everything I have read this shouldn't be a problem as IGMP snooping should stop multicast packets flooding the network.
If that's the only way then I will have the organise another cable run etc which will be very expensive...hence why I am looking down this route.
Because of the volume of traffic generated by multicast imaging, If you can't segregate the traffic, you're going to have these issues.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
wiziah need to check out the problem I wrote about on Cisco's site and srw2024. And to add to that Acronis seems to have a history of not playing nice with mc and certain networks.
If there is a problem with slow network when deploying a multicast source on the very same network I can see only two logical explanations. High bandwidth usage on shared resource or multicast treated as broadcast from the perspective of the switch.
If there is a problem with slow network when deploying a multicast source on the very same network I can see only two logical explanations. High bandwidth usage on shared resource or multicast treated as broadcast from the perspective of the switch.
If the author doesn't respond, I think the question should be deleted with no refund.
I had a peek at wiziah's earlier questions and he don't seem to be in the habit of abandon them. And there's always things in our lifes that get in the way. So, if I have some say in this I'd give the guy some time to respond. I have no problem with a month or so.
ASKER
Sorry guys with the delay, I have been away and been freakish busy being eoy etc..
Anyway, export1010 I have followed up on your post. There seems to be a possible incompatibility as you suggested. We have looking at getting a managed Cisco router into the office to keep platform the same and I will then create a separate VLAN.
I'll award the points to you..
oh, the annoying factor is Acronis support aren't any help with this either unfortunately.
Anyway, export1010 I have followed up on your post. There seems to be a possible incompatibility as you suggested. We have looking at getting a managed Cisco router into the office to keep platform the same and I will then create a separate VLAN.
I'll award the points to you..
oh, the annoying factor is Acronis support aren't any help with this either unfortunately.
The only alternative that I can think of is to implement QOS.