Excessive Login Failures
Hello,
We are running SBS 2003 with Service Pack 2. Lately we have been getting hammered by people trying to gain access. Last night there were over 9,000 failed attempts. Is there a way to counter this by locking out an IP address after a certain number of failures? Or any other ideas? We've increased our password complexity but I would like to cut off the excessive attempts if possible.
Thanks,
Steve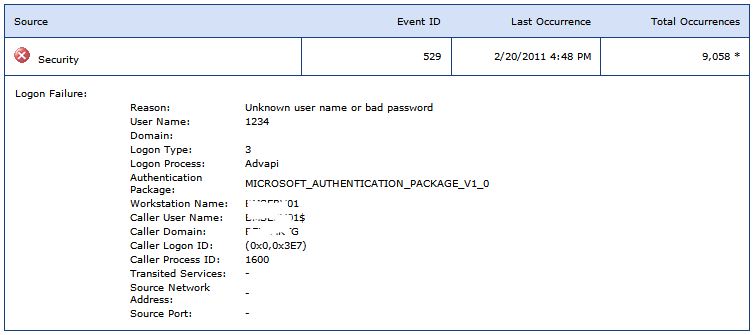
We are running SBS 2003 with Service Pack 2. Lately we have been getting hammered by people trying to gain access. Last night there were over 9,000 failed attempts. Is there a way to counter this by locking out an IP address after a certain number of failures? Or any other ideas? We've increased our password complexity but I would like to cut off the excessive attempts if possible.
Thanks,
Steve
ASKER
So I own a small company and wear many hats including IT guy. My IT knowledge is a bit limited. Your solution sounds good but you didn't say how to do it. Details?
Please have a read of my two blogs:
http://alanhardisty.wordpress.com/2010/09/28/increase-in-frequency-of-security-alerts-on-servers-from-hackers-trying-brute-force-password-programs/
http://alanhardisty.wordpress.com/2010/12/01/increase-in-hacker-attempts-on-windows-exchange-servers-one-way-to-slow-them-down/
You need to figure out what process PID 1600 is on your server and that will help you figure out how the hackers are trying to access your systems. I have removed Basic & Integrated SMTP authentication from ALL of my SBS 2003 servers that I manage and it has massively lowered the number of hacking attempts on each server.
http://alanhardisty.wordpress.com/2010/09/28/increase-in-frequency-of-security-alerts-on-servers-from-hackers-trying-brute-force-password-programs/
http://alanhardisty.wordpress.com/2010/12/01/increase-in-hacker-attempts-on-windows-exchange-servers-one-way-to-slow-them-down/
You need to figure out what process PID 1600 is on your server and that will help you figure out how the hackers are trying to access your systems. I have removed Basic & Integrated SMTP authentication from ALL of my SBS 2003 servers that I manage and it has massively lowered the number of hacking attempts on each server.
ASKER
Thanks both of you for the help. I read both of the links above. There is a lot of good information there on the steps I should be taking. Unfortunately for me there wasn't much information on "how" to take them.
Maybe if I explain a little more about how we access our server, you can point me in the appropriate direction.
Aside from the client computers accessing from within the LAN at the office, our 5 employees can access the server in the following ways:
1. via VPN.
2. via Outlook Web Access (rarely)
3. via iPhone (Exchange)
Our inbound email is directed to a Barracuda Networks Spam & Virus Firewall. The Barracuda then sends the email to our SBS 2003 Exchange server.
Our outbound email is send from our SBS 2003 Exchange server straight to our ISP (Qwest)
Does that help? Any ideas? Thank in advance.
Maybe if I explain a little more about how we access our server, you can point me in the appropriate direction.
Aside from the client computers accessing from within the LAN at the office, our 5 employees can access the server in the following ways:
1. via VPN.
2. via Outlook Web Access (rarely)
3. via iPhone (Exchange)
Our inbound email is directed to a Barracuda Networks Spam & Virus Firewall. The Barracuda then sends the email to our SBS 2003 Exchange server.
Our outbound email is send from our SBS 2003 Exchange server straight to our ISP (Qwest)
Does that help? Any ideas? Thank in advance.
Have you worked out what Process ID 1600 is? If so - please advise.
To reveal this, bring up Task Manager, Add in the PID column and then sort on the process ID column, then you can advise what the process is that is running on Process ID 1600.
OWA can be a target. SMTP can be a target. Remote Desktop can be a target.
To reveal this, bring up Task Manager, Add in the PID column and then sort on the process ID column, then you can advise what the process is that is running on Process ID 1600.
OWA can be a target. SMTP can be a target. Remote Desktop can be a target.
ASKER
This is strange.The server has been running for 14 days 6 hours, so no restarts since my first post. I brought up Task Manager and sorted the PID column. There isn't a 1600 listed. The PID ranges in value from 4306 to 9140.
The PID may have been and gone by now (are you showing all processes from all users?). Keep an eye on the logs and then marry up the service to the event log entry and then advise what the process is please.
ASKER
Yesterday afternoon I was thinking about the different ways someone could be trying to log into our server. I decided to shut off as many avenues as possible to see if it made any difference. I went into the SBS 2003 firewall settings and turned off Outlook Web Access, Remote Web Workplace and Business Web Site (wwwroot). The only services running are E-mail, VPN and Outlook Mobile Access.
I also changed the account lockout feature to only allow 5 attempts before locking out the account for 10 minutes. I also found that our server was responding to pings. I turned that off as well.
Last night there were over 8,000 failed logon attempts. Below is a screen shot of my Server Performance Report. On a good note I was able to determine that PID=inetinfo.exe
Any more ideas?
Thanks,
Steve
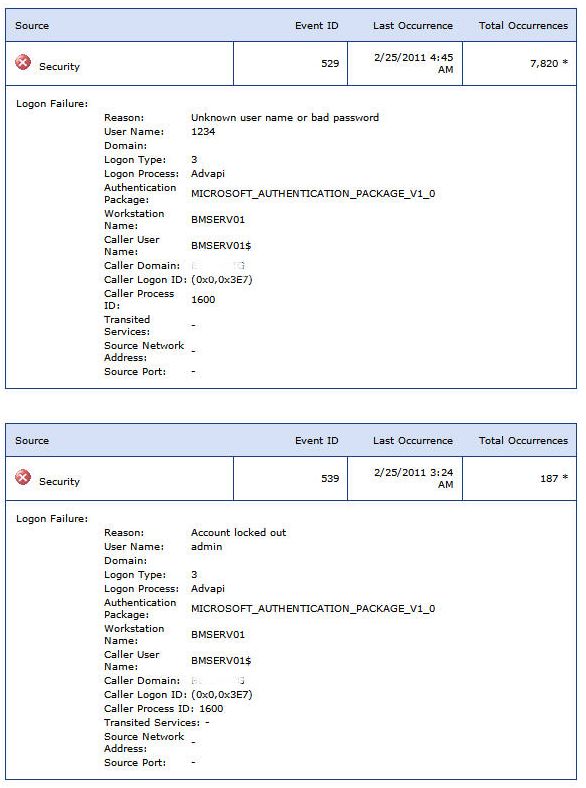
I also changed the account lockout feature to only allow 5 attempts before locking out the account for 10 minutes. I also found that our server was responding to pings. I turned that off as well.
Last night there were over 8,000 failed logon attempts. Below is a screen shot of my Server Performance Report. On a good note I was able to determine that PID=inetinfo.exe
Any more ideas?
Thanks,
Steve
And still no Process ID 1600 showing on your server?
ASKER
Yes. I mentioned in my previous post that PID 1600=inetinfo.exe
Thanks
Thanks
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I'm jealous. I want to go on holiday :)
Your blog was very good. I just disabled Basic & Integrated Windows Authentication on our server.
After doing a little more reading this morning on the internet blogs, I learned of one more thing I could do. I didn’t mention before that we were running a Barracuda Networks Spam & Virus Firewall. I have our DNS MX record pointing all incoming email there, and then after it is processed, the Barracuda sends it to our server. After digging around in the server I found that the virtual smtp server was still set to accept mail from any IP address. I changed that to only accept mail from the Barracuda IP and IP addresses within our LAN.
I’ll give it a few days to see if all that works, but I’m feeling pretty good about it.
Thanks for all your help!
Your blog was very good. I just disabled Basic & Integrated Windows Authentication on our server.
After doing a little more reading this morning on the internet blogs, I learned of one more thing I could do. I didn’t mention before that we were running a Barracuda Networks Spam & Virus Firewall. I have our DNS MX record pointing all incoming email there, and then after it is processed, the Barracuda sends it to our server. After digging around in the server I found that the virtual smtp server was still set to accept mail from any IP address. I changed that to only accept mail from the Barracuda IP and IP addresses within our LAN.
I’ll give it a few days to see if all that works, but I’m feeling pretty good about it.
Thanks for all your help!
Sorry - over in England with all our Grey weather - we need some sunshine!!
The Barracuda is a good Ace to have had up your sleeve ; )
The Authentication would have cut down the problem, but having a Barracuda to play with and restricting the IP's would be the final nail in the coffin (with that particular method of hacking).
Your Reports should be much happier now.
Alan
The Barracuda is a good Ace to have had up your sleeve ; )
The Authentication would have cut down the problem, but having a Barracuda to play with and restricting the IP's would be the final nail in the coffin (with that particular method of hacking).
Your Reports should be much happier now.
Alan
Disable that and your problem is solved.
If you have to have people log in from the outside, then have them go through a VPN of some sort, then allow them access to the server.