millsusaf
asked on
HP 7102dl VPN Multi-Site to Site Tunnel
Hello, I'm back......
Thanks to erniebeek, I have a single point to point VPN tunnel up and running on these two HP 7102dl routers however for the life of me I can't get additional tunnels up in the "hub" router of the hub and spoke configuration.
Here is the original question: 7102dl VPN Site to Site
Every time I try to add another crypto map or encryption statement it doesn't allow for multiples. Everything is pingable between the routers.
What gives?
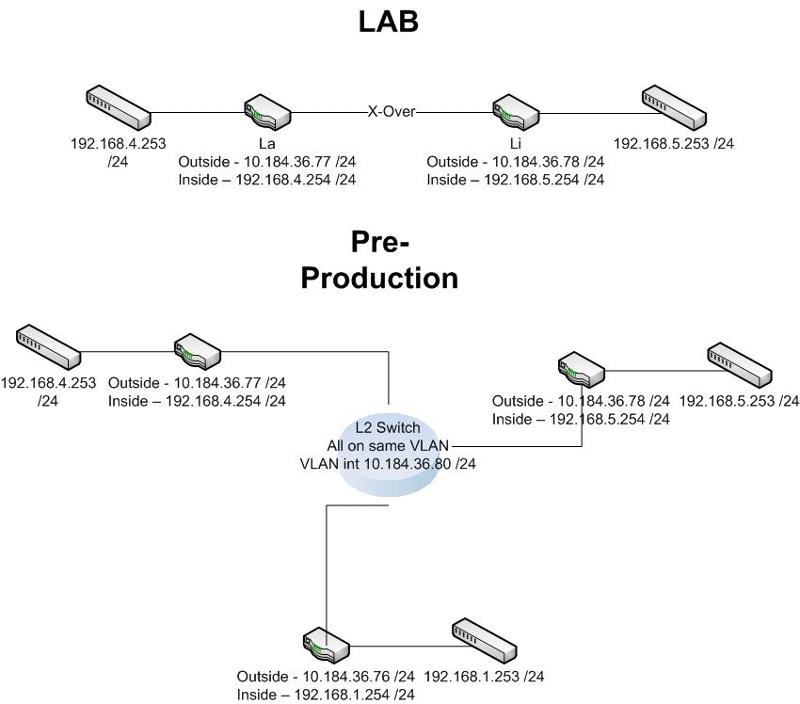
LI Router (hub)
La Router (spoke)
Ft Router (spoke)
And while I'm here I might as well take the next step and ask about external VPN client access. Judging by the trouble I had with the site to site stuff, the VPN client stuff just might do me in.
Thanks!
Thanks to erniebeek, I have a single point to point VPN tunnel up and running on these two HP 7102dl routers however for the life of me I can't get additional tunnels up in the "hub" router of the hub and spoke configuration.
Here is the original question: 7102dl VPN Site to Site
Every time I try to add another crypto map or encryption statement it doesn't allow for multiples. Everything is pingable between the routers.
What gives?

LI Router (hub)
Li Router
!
ip crypto
!
crypto ike policy 100
initiate main
respond anymode
local-id address 10.184.36.78
peer 10.184.36.76
peer 10.184.36.77
attribute 1
encryption 3des
hash md5
authentication pre-share
!
crypto ike remote-id any preshared-key "key" ike-policy 100 crypto map VPN 10 no-mode-config no-xauth
!
crypto ipsec transform-set esp-3des-esp-md5-hmac esp-3des esp-md5-hmac
mode tunnel
!
crypto map VPN 10 ipsec-ike
description Lig2LaG
match address VPN-10-vpn-selectors
set peer 10.184.36.77
set transform-set esp-3des-esp-md5-hmac
ike-policy 100
!
!
!
!
interface eth 0/1
description Inside Interface
ip address 192.168.5.254 255.255.255.0
no shutdown
!
!
interface eth 0/2
description Outside Interface
ip address 10.184.36.78 255.255.255.0
crypto map VPN
no shutdown
!
!
!
!
!
!
!
!
!
!
ip access-list extended VPN-10-vpn-selectors
permit ip 192.168.4.0 0.0.0.255 192.168.5.0 0.0.0.255
permit ip 192.168.5.0 0.0.0.255 192.168.4.0 0.0.0.255
!
!
!
!
ip route 0.0.0.0 0.0.0.0 10.184.36.80
!
Proof the tunnel works:
Li# sho crypto ike sa
Using 1 SAs out of 2000
Peak concurrent SAs: 1
IKE Security Associations:
Peer IP Address: 10.184.36.77
Remote ID: 10.184.36.77
Lifetime: 25537
Status: UP (SA_MATURE)
IKE Policy: 100
NAT-traversal: V2
Detected NAT: No
Dead Peer Detection: Yes
Li# sho crypto ipsec sa
Using 2 SAs out of 4000
Peak concurrent SAs: 2
IPSec Security Associations:
Peer IP Address: 10.184.36.78
Remote ID: 10.184.36.77
Crypto Map: VPN 10
Direction: Inbound
Encapsulation: ESP
SPI: 0xABA090AD (2879426733)
RX Bytes: 0
Selectors: Src:192.168.4.0/255.255.255.0 Port:ANY Proto:ALL IP
Dst:192.168.5.0/255.255.255.0 Port:ANY Proto:ALL IP
Hard Lifetime: 25490
Soft Lifetime: 0
Out-of-Sequence Errors: 0
Peer IP Address: 10.184.36.77
Remote ID: 10.184.36.77
Crypto Map: VPN 10
Direction: Outbound
Encapsulation: ESP
SPI: 0x922ABE14 (2452274708)
TX Bytes: 11640
Selectors: Src:192.168.5.0/255.255.255.0 Port:ANY Proto:ALL IP
Dst:192.168.4.0/255.255.255.0 Port:ANY Proto:ALL IP
Hard Lifetime: 25480
Soft Lifetime: 25420La Router (spoke)
ip crypto
!
crypto ike policy 100
initiate main
respond anymode
local-id address 10.184.36.77
peer 10.184.36.78
attribute 1
encryption 3des
hash md5
authentication pre-share
!
crypto ike remote-id any preshared-key "key" ike-policy 100 crypto map VPN 10 no-mode-config no-xauth
!
crypto ipsec transform-set esp-3des-esp-md5-hmac esp-3des esp-md5-hmac
mode tunnel
!
crypto map VPN 10 ipsec-ike
description Site2Site
match address VPN-10-vpn-selectors
set peer 10.184.36.78
set transform-set esp-3des-esp-md5-hmac
ike-policy 100
!
!
!
!
interface eth 0/1
description Inside Interface
ip address 192.168.4.254 255.255.255.0
no shutdown
!
!
interface eth 0/2
description Outside Interface
ip address 10.184.36.77 255.255.255.0
crypto map VPN
no shutdown
!
!
!
!
!
!
!
!
!
!
ip access-list extended VPN-10-vpn-selectors
permit ip 192.168.4.0 0.0.0.255 192.168.5.0 0.0.0.255
permit ip 192.168.5.0 0.0.0.255 192.168.4.0 0.0.0.255
!
!
!
!
ip route 0.0.0.0 0.0.0.0 10.184.36.80
Proof the tunnel work:
La#sho crypto ike sa
Using 1 SAs out of 2000
Peak concurrent SAs: 2
IKE Security Associations:
Peer IP Address:104.184.36.78
Remote ID: 10.184.36.78
Lifetime: 25247
Status: UP (SA_MATURE)
IKE Policy: 100
NAT-traversal: V2
Detected NAT: No
Dead Peer Detection: Yes
La#sho crypto ipsec sa
Using 2 SAs out of 4000
Peak concurrent SAs: 2
IPSec Security Associations:
Peer IP Address: 10.184.36.77
Remote ID: 10.184.36.78
Crypto Map: VPN 10
Direction: Inbound
Encapsulation: ESP
SPI: 0x922ABE14 (2452274708)
RX Bytes: 0
Selectors: Src:192.168.5.0/255.255.255.0 Port:ANY Proto:ALL IP
Dst:192.168.4.0/255.255.255.0 Port:ANY Proto:ALL IP
Hard Lifetime: 25210
Soft Lifetime: 0
Out-of-Sequence Errors: 0
Peer IP Address: 10.184.36.78
Remote ID: 10.184.36.78
Crypto Map: VPN 10
Direction: Outbound
Encapsulation: ESP
SPI: 0xABA090AD (2879426733)
TX Bytes: 0
Selectors: Src:192.168.4.0/255.255.255.0 Port:ANY Proto:ALL IP
Dst:192.168.5.0/255.255.255.0 Port:ANY Proto:ALL IP
Hard Lifetime: 25210
Soft Lifetime: 25130Ft Router (spoke)
ip crypto
!
crypto ike policy 100
initiate main
respond anymode
local-id address 10.184.36.76
peer 10.184.36.78
attribute 1
encryption 3des
hash md5
authentication pre-share
!
crypto ike remote-id any preshared-key "key" ike-policy 100 crypto map VPN 10 no-mode-config no-xauth
!
crypto ipsec transform-set esp-3des-esp-md5-hmac esp-3des esp-md5-hmac
mode tunnel
!
crypto map VPN 10 ipsec-ike
description Site2Site
match address VPN-10-vpn-selectors
set peer 10.184.36.78
set transform-set esp-3des-esp-md5-hmac
ike-policy 100
!
!
!
interface eth 0/1
description Inside Interface
ip address 192.168.1.254 255.255.255.0
no shutdown
!
!
interface eth 0/2
description Outside Interface
ip address 10.184.36.76 255.255.255.0
crypto map VPN
no shutdown
!
!
!
!
!
!
!
!
!
!
ip access-list extended VPN-10-vpn-selectors
permit ip 192.168.1.0 0.0.0.255 192.168.4.0 0.0.0.255
permit ip 192.168.1.0 0.0.0.255 192.168.5.0 0.0.0.255
!
!
!
ip route 0.0.0.0 0.0.0.0 10.184.36.80
NO TUNNEL to .78 though. : /And while I'm here I might as well take the next step and ask about external VPN client access. Judging by the trouble I had with the site to site stuff, the VPN client stuff just might do me in.
Thanks!
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Note to all....do not buy HP 7102dl routers if you intend to do VPN tunnels. They are a POS, the tunnels will not stay up or even come up reliably.