Adding Redundancy with MPLS and Sonic Firewall
I'm searching their db to see if there are any other solutions resembling the issue I'm trying to get a solution for. Below you will notice the setup; not the most ideal solution; but in a nutshell
The CISCO routers are managed by the carrier additionally the carrier has the Cisco devices programmed so that if MPLS link goes down on the WAN side route all traffic back to the LAN side of the Cisco which will forward all traffic to the X0 interface IP of the Sonicwall. The Sonicwall has VPN tunnels configured from remote to HQ site in this case let's say HQ is 10.0.13.0
The default gateway for all clients in a node will be the Cisco (CE) device. problem is that when we test failover to the Sonicwall the Cisco sends traffic to the Sonicwall; but the Sonicwall will not receive a response back from the remote Sonicwall I believe the end node may be trying to route the information via the MPLS network at HQ since all clients are programmed for the CISCO to be the default gateway. If I set all clients to route traffic to the Sonicwall as a default would I be able to configure 2 redundant routes and if link is down failover to the VPN tunnel as secondary?
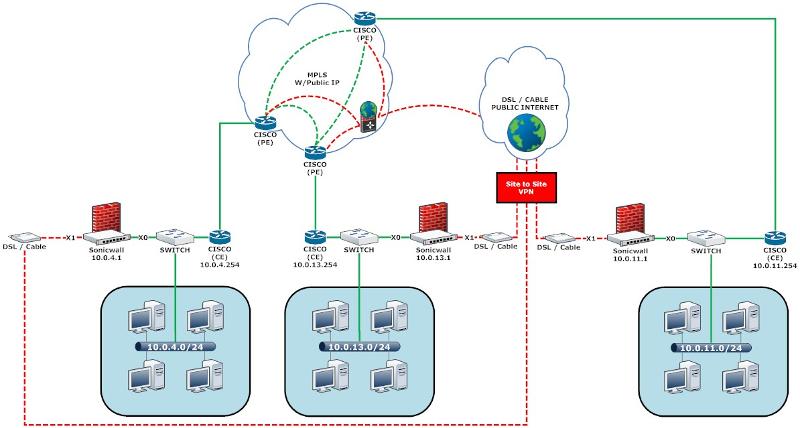
The CISCO routers are managed by the carrier additionally the carrier has the Cisco devices programmed so that if MPLS link goes down on the WAN side route all traffic back to the LAN side of the Cisco which will forward all traffic to the X0 interface IP of the Sonicwall. The Sonicwall has VPN tunnels configured from remote to HQ site in this case let's say HQ is 10.0.13.0
The default gateway for all clients in a node will be the Cisco (CE) device. problem is that when we test failover to the Sonicwall the Cisco sends traffic to the Sonicwall; but the Sonicwall will not receive a response back from the remote Sonicwall I believe the end node may be trying to route the information via the MPLS network at HQ since all clients are programmed for the CISCO to be the default gateway. If I set all clients to route traffic to the Sonicwall as a default would I be able to configure 2 redundant routes and if link is down failover to the VPN tunnel as secondary?

ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
that's describing your situation exactly. it's what i would have recommended. i've not come across this configuration before.
ASKER
quick one I guess
there is a way to setup to gateways and configure a route to be disabled if the interface goes offline. however, in this case, you might have some challenges if the cisco router stays online but the mpls "down" issue is beyond the cisco router and the sonicwall can't detect that.