corpdsinc
asked on
Cisco ASA L2L VPNs down after ISP Change
Hello
We just changed ISPs and thus have new IPS. We have a new WAN IP and then a block of IPS (CIDR). After this change our two site to site VPN tunnels stopped working. We changed the IP of the remote site to the new WAN interface IP (on the two remote routers) but the connections still won't work. All of the devices are Cisco ASA apliances. Are we missing something in regards to ACL or routing ? Usually changing the remote site VPN on the remote routers brings things right back up.
Thanks for your help.
We just changed ISPs and thus have new IPS. We have a new WAN IP and then a block of IPS (CIDR). After this change our two site to site VPN tunnels stopped working. We changed the IP of the remote site to the new WAN interface IP (on the two remote routers) but the connections still won't work. All of the devices are Cisco ASA apliances. Are we missing something in regards to ACL or routing ? Usually changing the remote site VPN on the remote routers brings things right back up.
Thanks for your help.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
>Do you think that fact that the 0.0.0.0 0.0.0.0 static route is set to the WAN INT IP instead of the WAN INT gateway could be the problem?
Absolutely! It must point to the next hop, never to your own interface ip!
Absolutely! It must point to the next hop, never to your own interface ip!
ASKER
Ok..my bad. I forgot that i did change the default routes for the WAN INT default gateway yesterday..I was excited about that being the fix...but no luck. Any other ideas?
Pedraq: I have verified that that peer IPs are correct. In fact, I recreated the VPN on one of the remote sites via the wizzard creating new tunnel group and Peer IP etc.
Pedraq: I have verified that that peer IPs are correct. In fact, I recreated the VPN on one of the remote sites via the wizzard creating new tunnel group and Peer IP etc.
ok,
could you do the following on your ASA device:
debug crypto ipsec
debug crypto isakmp
terminal monitor
and try to send traffic from one site to another (traffic which matches the crypto maps), send the debugs.
could you do the following on your ASA device:
debug crypto ipsec
debug crypto isakmp
terminal monitor
and try to send traffic from one site to another (traffic which matches the crypto maps), send the debugs.
ASKER
I was unable to do th debug. But using ASDM monitoring I see that the lan2lan tunnel is established. At the remote side it is passing two way traffic. HOWEVER, at the main site (where the public IP was changed) it is receiving data but not transmitting (0 TX bytes 970 RX bytes)
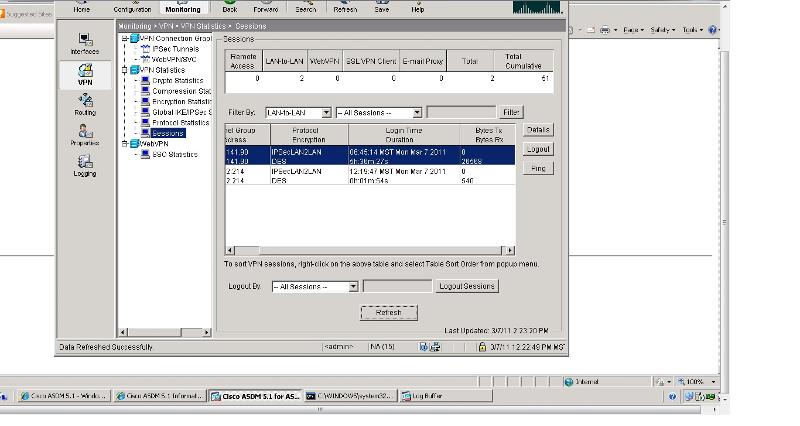
ASKER