Inherited permissions from root can't be found?
Using SBS 2008 and Windows Fax Service.
I've got a folder setup to hold Faxes located at D:\Data\Faxes. For some reason, one user has special permissions for this folder only that are, supposedly, inherited from the root of Drive D.
See screenshot on right of Advanced Settings, user Ron.... (Note: there is another user, R Dono... that has explicit deny permissions that I intentionally created, so this can be ignored)
However, as the left screenshot also shows, the user Ron does not have any security settings at the root.
So where are the settings coming from? I know I must be missing something obvious and don't want to mess around with the inheritence until I understand where things are coming from.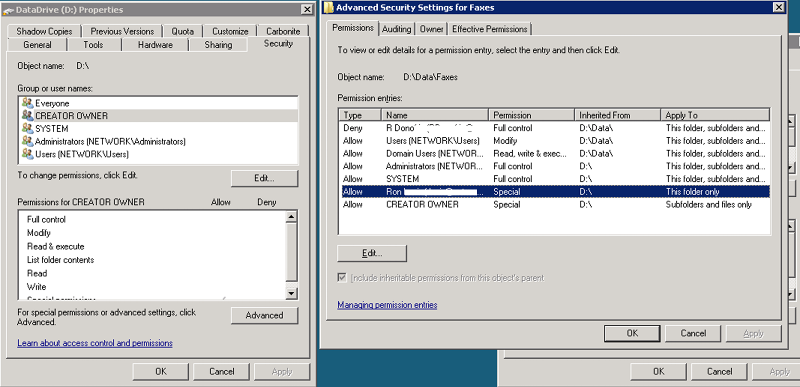
I've got a folder setup to hold Faxes located at D:\Data\Faxes. For some reason, one user has special permissions for this folder only that are, supposedly, inherited from the root of Drive D.
See screenshot on right of Advanced Settings, user Ron.... (Note: there is another user, R Dono... that has explicit deny permissions that I intentionally created, so this can be ignored)
However, as the left screenshot also shows, the user Ron does not have any security settings at the root.
So where are the settings coming from? I know I must be missing something obvious and don't want to mess around with the inheritence until I understand where things are coming from.

ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Cool no problem bud, the quick fixes are always the best :)
ASKER
Bingo! He is listed as the current owner - no idea why. Could swear I checked that but guess I didn't...
I'll change it to Administrators. Thanks for the quick reply!