TMG with many Vlans blocking subnets (IP spoof)
hi guys
i installed a fresh TMG server at a client
internet was working for the Server Vlan ( same subnet as the TMG server) (10.10.3.x)
but for all the users the internet did not work (10.10.4.x)
i added the 10.10.4.x range to the internal network in TMG yet is still didnt work
i checked the logs and it was blocking traffic from those IP addresses saying it was a IP spoof attack
please help
i installed a fresh TMG server at a client
internet was working for the Server Vlan ( same subnet as the TMG server) (10.10.3.x)
but for all the users the internet did not work (10.10.4.x)
i added the 10.10.4.x range to the internal network in TMG yet is still didnt work
i checked the logs and it was blocking traffic from those IP addresses saying it was a IP spoof attack
please help
Add the .0 and the .255 addresses of eah subnet on the internal local address table as well.
ASKER
yeah i added the full Range from .0-.255
Please check :
http://support.microsoft.com/kb/838114
http://support.microsoft.com/kb/838114
Can you post a screenshot of how you have entered the local address table?
ASKER
yeah this fixit didnt work:-(
is this a common issue with TMG??
is this a common issue with TMG??
Yes - but not sure why you think it would have fixed anything. The Fixit is to enable the spoof detection - and you already have it enabled.
PS - it is not an issue with TMG, it is an issue with your configuration
Thanks - behind the screen shot I could see that you have a permiter network that looked like it had a start address of x.x.x.1.
Spoofing can also be caused from other defined networks and the rules are the same for each - the whole subnet must be defined. Check the perimeter network local address table and make sure this also has the .0 through to the .255 address defined.
Also, run up the best practice analyser for FTMG and this will tell you exactly where the spoof issue is being reported from.
Spoofing can also be caused from other defined networks and the rules are the same for each - the whole subnet must be defined. Check the perimeter network local address table and make sure this also has the .0 through to the .255 address defined.
Also, run up the best practice analyser for FTMG and this will tell you exactly where the spoof issue is being reported from.
ASKER
ok is there a real use for a permiter network? as all i have is users- TMG-firewal-router-interne
so in the first setup should i select Edge firewall or back firelwall?? because in this instalation i selected back firewall..
so in the first setup should i select Edge firewall or back firelwall?? because in this instalation i selected back firewall..
Please correct me if I understand wrong:
1.you have VLANs
2. VLANs configured on L3 switch or router.
3.then this router routes traffic to TMG server then Internet.
4. you network topology looks like VLANs --> Router--> TMG server--> internet.
If that the case then TMG will service a-only its VLAN. and will identify the other VLANs as spoofed addresses. because TMG server will try to resolve the source ip address to MAC address. in your case all other VLANs addresses will be resolve to the router MAC address. thats why TMG/ISA identify that traffic as spoof attack.
the link provided to disable spoof detection should solve the problem, you may need to restart FW service.
Thanks,
Suliman
1.you have VLANs
2. VLANs configured on L3 switch or router.
3.then this router routes traffic to TMG server then Internet.
4. you network topology looks like VLANs --> Router--> TMG server--> internet.
If that the case then TMG will service a-only its VLAN. and will identify the other VLANs as spoofed addresses. because TMG server will try to resolve the source ip address to MAC address. in your case all other VLANs addresses will be resolve to the router MAC address. thats why TMG/ISA identify that traffic as spoof attack.
the link provided to disable spoof detection should solve the problem, you may need to restart FW service.
Thanks,
Suliman
ASKER
well its users> vlans > TMG > Firewall> router > internet
but the problem is it is there are a few vlans
so the TMG allowes traffic on its vlan but not on other vlans??
but the problem is it is there are a few vlans
so the TMG allowes traffic on its vlan but not on other vlans??
There is no issue about internal vlans, all FTMG will care about is knowing that ALL ip addresses that are contactable through the internal interface are listed inside the internal nic LAT within the FTMG gui. Disabling spoof protection fixes nothing - you simply stop being notified about the threat or configurration error.
A backend firewall or frontend firewall template is decided by how you want to use the product and the placement of other equipment.
A backend firewall or frontend firewall template is decided by how you want to use the product and the placement of other equipment.
I see.
I order to for VLANs to be able to communicate with each other, there should be a router ( or L3 switch ) connects all VLANs. so It should be like:
users> vlans (router ) > TMG > Firewall> router > internet
make sure the TMG can reach all VLANs.
had you disable spoof detection ? I had the same issue and that resolved it for me.
I order to for VLANs to be able to communicate with each other, there should be a router ( or L3 switch ) connects all VLANs. so It should be like:
users> vlans (router ) > TMG > Firewall> router > internet
make sure the TMG can reach all VLANs.
had you disable spoof detection ? I had the same issue and that resolved it for me.
We can always discuss this further off-line if you wish. You are correct, there has to be 'something' inside at the layer 3 that can interface all of the vlans together but as long as ISA/FTMG can talk to that L3 device, then that is all that is needed, ie the L3 acts as the router for the FTMG tarffic. As long as FTMG knows about all the IP addresses associated with ALL of the internal vlans then that is fine.
The definition of a spoof attack from FTMG's perspective is the receipt of traffic at an FTMG interface when it was not expected. For example, the FTMG INTERNAL nic sees traffic arrive from 10.10.3.9 when 10.10.3.9 is not included in any of the local adress tables within the FTMG gui.
The definition of a spoof attack from FTMG's perspective is the receipt of traffic at an FTMG interface when it was not expected. For example, the FTMG INTERNAL nic sees traffic arrive from 10.10.3.9 when 10.10.3.9 is not included in any of the local adress tables within the FTMG gui.
http://technet.microsoft.com/en-us/library/bb794735.aspx
"Before blocking this suspect IP address, ISA Server validates that the source IP address is not spoofed. If the source IP address is found to be malicious, ISA Server triggers an alert with information about the attack and about the attacker. From this point, ISA Server limits traffic from the offending host for one minute. After one minute, ISA Server again allows traffic from that IP address. If the threshold is again exceeded, and if you manually reset the alert, an alert is again triggered and traffic is blocked."
"Before blocking this suspect IP address, ISA Server validates that the source IP address is not spoofed. If the source IP address is found to be malicious, ISA Server triggers an alert with information about the attack and about the attacker. From this point, ISA Server limits traffic from the offending host for one minute. After one minute, ISA Server again allows traffic from that IP address. If the threshold is again exceeded, and if you manually reset the alert, an alert is again triggered and traffic is blocked."
I give up - Yolanie, please run the best practice analyser and post the results regarding the spoofing configuration error.
ASKER
lol thanks for all your help guys...
@Keith
i have run the setup as the documentation says and all i ran was the web access wizard..and added the other Vlans subnets to the internal ranges within the TMG gui... the reson i ask what tropology i should select is because maybe i am selecting the wrong one to start with in your opinion which would you select for this users> Vlans > TMG >Firewall > Router > internet the two that make the most sense for me are back firewall and edge firewall?? thanks for your help
@Sulimanw
the Vlans all communicate with each other as the servers are on on and the users are on another and i am able to ping all the vlans for the TMG server.. i dont think its a communication problem i think its the TMG blocking the requests
regarding the IP spoof fixit i figured that it would just be for alerts
@Keith
i have run the setup as the documentation says and all i ran was the web access wizard..and added the other Vlans subnets to the internal ranges within the TMG gui... the reson i ask what tropology i should select is because maybe i am selecting the wrong one to start with in your opinion which would you select for this users> Vlans > TMG >Firewall > Router > internet the two that make the most sense for me are back firewall and edge firewall?? thanks for your help
@Sulimanw
the Vlans all communicate with each other as the servers are on on and the users are on another and i am able to ping all the vlans for the TMG server.. i dont think its a communication problem i think its the TMG blocking the requests
regarding the IP spoof fixit i figured that it would just be for alerts
Backend/frontend is not relevant to spoofing. The BPA will advise on the cause.
http://www.microsoft.com/downloads/en/details.aspx?FamilyID=8aa01cb0-da96-46d9-a50a-b245e47e6b8b
http://www.microsoft.com/downloads/en/details.aspx?FamilyID=8aa01cb0-da96-46d9-a50a-b245e47e6b8b
ASKER
hi guys..
i have run the BPA it doenst mention anything about spoofing??
what access rule or exception would i have to add to allow other subnets to be allowed to access the internet??
TMG range 10.10.3.x (can browse the internet)
user range 10.10.4.x (currently cant browse the internet)
all i have done was run the web access wizard and added the 10.10.4.x range to the internal network..
anything else?
i have run the BPA it doenst mention anything about spoofing??
what access rule or exception would i have to add to allow other subnets to be allowed to access the internet??
TMG range 10.10.3.x (can browse the internet)
user range 10.10.4.x (currently cant browse the internet)
all i have done was run the web access wizard and added the 10.10.4.x range to the internal network..
anything else?
Did you add the range 10.10.4.x to internal network ranges ? please see attached.
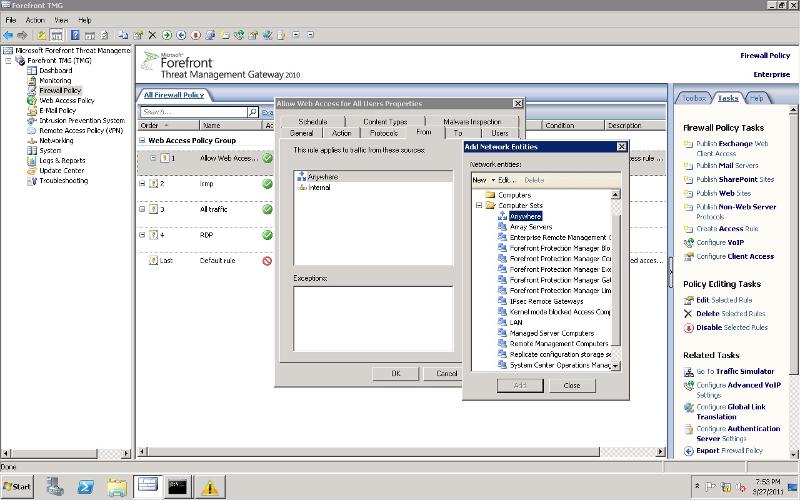
Do you have in the access rule "internal" network in the from tab?
a.PNG
Do you have in the access rule "internal" network in the from tab?
a.PNG
ASKER
yup i have added it in the internal properties:)
ASKER
Any particular reason no one has said,..."Add a static route on the ISA/TMG so that it know what routing device to use to get to the other subnets?.
Adding the range to the Internal Network Definition (LAT) is not enough,...the static route is required too,...otherwise you are telling the ISA/TMG that the Internal network has ranges that are part of it that are not reachable from the Internal Nic
Adding the range to the Internal Network Definition (LAT) is not enough,...the static route is required too,...otherwise you are telling the ISA/TMG that the Internal network has ranges that are part of it that are not reachable from the Internal Nic
....hence the spoofing alerts....
Why does he need a static route if he can already ping all the addresses from the FTMG?
Ok, no problem. But I scanned through the thread looking to see if a route was added and couldn't see that is was and didn't see that he could ping the other segments. But the symptoms sure implied that there was no route.
Actually you may be right - there have been a whole flurry of these over the past couple of days :)
ASKER
so the routes could be the issue??
i would have to add them on the TMG server right?
i would have to add them on the TMG server right?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
yeah this is the case..
i feel the traffic is getting to the TMG server but it is being blocked from there..
but i have added the subnets to the internal network.... this should work then right?
i feel the traffic is getting to the TMG server but it is being blocked from there..
but i have added the subnets to the internal network.... this should work then right?
ASKER
No,..."anywhere",...is not going to do "anything",...in this context. It is not even related to this.
You cannot have the idea that you are never going to see any "denies" in the log,...there are always going to be "denies",...even when everything is working and everything is allowed that is supposed to be allowed there will be "denies" as part of the normal authentication process. You have to judge things by whether or not something is truely broken,...not by simply seeing a "deny" in the log.
ASKER
well the denies in the log are from and internal IP address on a different subnet that doenst have internet...
so its not working if this is the case...
i have contacted microsoft with this issue im sure they can help
thanks for all your help
so its not working if this is the case...
i have contacted microsoft with this issue im sure they can help
thanks for all your help
ASKER
thanks seams to be a problem with the routing... even though the routing table was up to date TMG did not see that so after the routes where added i had to re add the access rule
So basically I was right, even though I only got a "B" for it.