Big...Certificate Services issues
Ill try to make a long story short, and readily I'll admit I did some stupid stuff here..
A few years ago I stood up a new Windows 2008 DC in an existing 2k3 r2 domain. I dcpromod it without issue from memory, backed up the existing root ca info and exported the keys. Installed AD CS on that server, imported the root info and from what I remember everything was cool.
About 4 months later I took one of existing two Win2k3 dc's and demoted it, disjoined form domain. Another 4-6 months later I stood up a new 2k8 dc except this time it was an R2 box, moved all of the FSMO roles as well as AD CS to it. There again, 4-6 months later I demoted and disjoined the last 2k3 DC.
Fast forward to now, 4 days ago I upgraded that first 2k8 DC to R2 (first verifying that none of the FSMO roles were on it), and I've been in the process of watching the event logs since then. Oh BTW the upgrade completed successfully.
So the current issue is that I do not believe I backed up or exported the original Root CA info correctly because in my normal checking this morning I happened to actually click on the "Enterprise PKI" role module in Server Manager and was greeted by a red x. Now I will be totally honest in that i have been working on this for the past 3 hours so far.. with a LARGE helping of Google. Prior to what you see here, there was initially:
2 CA Certificates both OK
2 AIA locations both unable to download
3 CDP Locations 2 Unable to download
2 CRL Locations 1 Unable to download
(DISCLAIMER, the real stupidity starts here)
In the properties of the Root CA itself, under Extensions-AIA there were 2 entries that were apparently invalid, both of which were "http" so I removed the longer of the two which began with something like <serverName>. The other was "http://1st 2k8 servername/ocsp", I changed it to "http://current_2k8r2_server/ocsp" Restarted the CA services then rechecked but that AIA location was still unable to download. So I removed it totally.
Now Managing the AD Containers under Enterprise PKI, I noticed how there were 2 NTAuthCertificates, I checked the Valid from dates and removed the oldest one. Now what I thought was odd at the time was that both of the existing NTAuthCerts were initially created in 2008, they both had a "CRL Distribution Point" pointing to the old 2k3 DC. I wasn't sure what to think about that so I left it alone.
So then I proceeded to remove entries under AIA Container, CDP Container and Certificate Authorities Container that referenced back to that older of the two RootCA cert's.
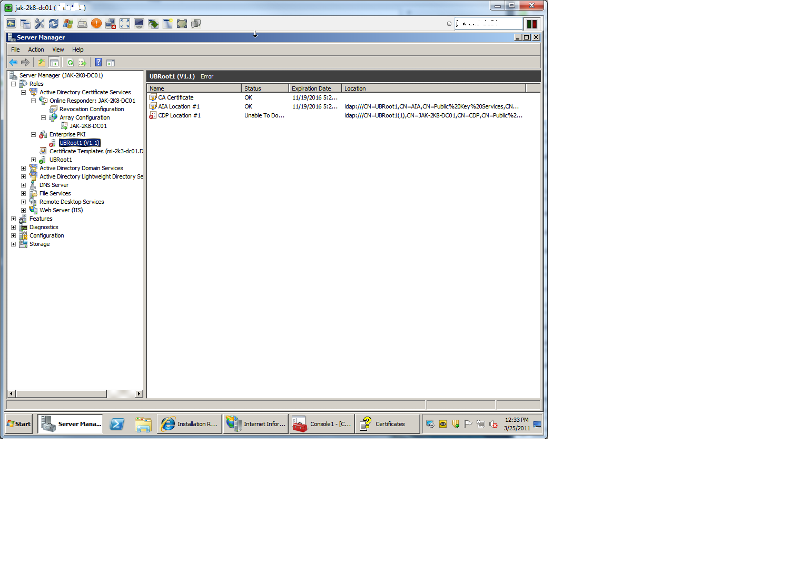
After restarting the services again.. I still have a red X for my Enterprise PKI, but now I'm left with the image attached.
So I thought, "Ok I'll just remove all the Role Services except for Certification Authority, and reinstall them. I probably don't have to say that that did not work either. So now I'm stuck.. I do not know if I should change that CRL Dist Point, revoke the original root ca cert or what really.
Now we do not use PKI for domain authentication, user or computer encryption not email signing. I held off on uninstalling CA as a whole just because I am not sure what services or other roles/features depend upon it such as Domain Controller or Exchange certs. And what's more, I don't want cert related messages appearing on user's screens during the middle of the day. I've tried looking up methods of reinstalling CA and I've found some guides and outlines but nothing that really explains the caveats or risks in an established domain.
A few years ago I stood up a new Windows 2008 DC in an existing 2k3 r2 domain. I dcpromod it without issue from memory, backed up the existing root ca info and exported the keys. Installed AD CS on that server, imported the root info and from what I remember everything was cool.
About 4 months later I took one of existing two Win2k3 dc's and demoted it, disjoined form domain. Another 4-6 months later I stood up a new 2k8 dc except this time it was an R2 box, moved all of the FSMO roles as well as AD CS to it. There again, 4-6 months later I demoted and disjoined the last 2k3 DC.
Fast forward to now, 4 days ago I upgraded that first 2k8 DC to R2 (first verifying that none of the FSMO roles were on it), and I've been in the process of watching the event logs since then. Oh BTW the upgrade completed successfully.
So the current issue is that I do not believe I backed up or exported the original Root CA info correctly because in my normal checking this morning I happened to actually click on the "Enterprise PKI" role module in Server Manager and was greeted by a red x. Now I will be totally honest in that i have been working on this for the past 3 hours so far.. with a LARGE helping of Google. Prior to what you see here, there was initially:
2 CA Certificates both OK
2 AIA locations both unable to download
3 CDP Locations 2 Unable to download
2 CRL Locations 1 Unable to download
(DISCLAIMER, the real stupidity starts here)
In the properties of the Root CA itself, under Extensions-AIA there were 2 entries that were apparently invalid, both of which were "http" so I removed the longer of the two which began with something like <serverName>. The other was "http://1st 2k8 servername/ocsp", I changed it to "http://current_2k8r2_server/ocsp" Restarted the CA services then rechecked but that AIA location was still unable to download. So I removed it totally.
Now Managing the AD Containers under Enterprise PKI, I noticed how there were 2 NTAuthCertificates, I checked the Valid from dates and removed the oldest one. Now what I thought was odd at the time was that both of the existing NTAuthCerts were initially created in 2008, they both had a "CRL Distribution Point" pointing to the old 2k3 DC. I wasn't sure what to think about that so I left it alone.
So then I proceeded to remove entries under AIA Container, CDP Container and Certificate Authorities Container that referenced back to that older of the two RootCA cert's.
After restarting the services again.. I still have a red X for my Enterprise PKI, but now I'm left with the image attached.
So I thought, "Ok I'll just remove all the Role Services except for Certification Authority, and reinstall them. I probably don't have to say that that did not work either. So now I'm stuck.. I do not know if I should change that CRL Dist Point, revoke the original root ca cert or what really.
Now we do not use PKI for domain authentication, user or computer encryption not email signing. I held off on uninstalling CA as a whole just because I am not sure what services or other roles/features depend upon it such as Domain Controller or Exchange certs. And what's more, I don't want cert related messages appearing on user's screens during the middle of the day. I've tried looking up methods of reinstalling CA and I've found some guides and outlines but nothing that really explains the caveats or risks in an established domain.

ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I have had no users report issues involving certificates, so I think i'm good now. As the previous DC has been gone for 4 years now I honestly cannot remember if it was Enterprise or not but I do have users and machines auto enrolling now so I might have lucked out on the reinstalling of CE.
Thanks guys!
Thanks guys!
ASKER
I'm accepting mine and his responses because while his advice didn't result in the resolution of my issues.. he didn't offer his help. He must get something for that.
Machine enrollment is controlled by policy.
If you're autoenrolling to a lot of people make sure that you set request handling to "enroll subject without requiring any user input" - or you'll get a lot of support calls the next morning.
Make sure your AIA/CDP/OCSP locations are set before you begin issuing certificates, otherwise you'll not be able to revoke them