JustinGSEIWI
asked on
How to lock down an hosted 2008 R2 web server
I have a hosted 2008 R2 web server that I need to make PCI compliant. This server will process credit card transactions so I am running the external vulnerability scans against it. Below are the results from the most recent scan. Below you will also see the remaining enabled firewall rules.
In response to the scan results below, I disabled all core networking and networking rules in the firewall. I am not sure how much this may or may not of taken care of yet b/c a new scan takes 24-72 hours to get done.
I need to make sure I have removed all of these vulnerabilities and would like some advice on how to go about doing that. I think I am close, I just need a little more help.
Thanks,
Justin
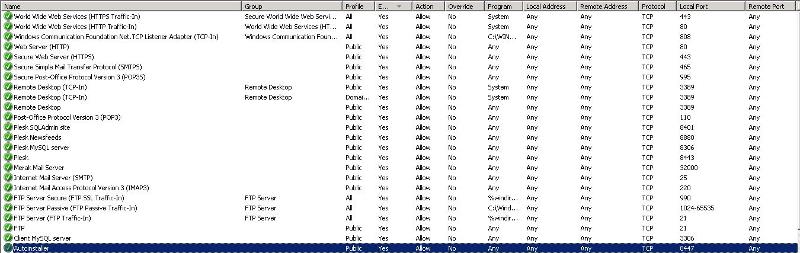
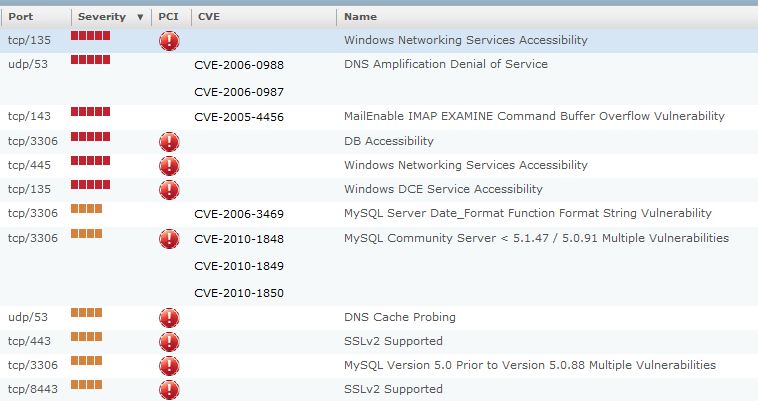
In response to the scan results below, I disabled all core networking and networking rules in the firewall. I am not sure how much this may or may not of taken care of yet b/c a new scan takes 24-72 hours to get done.
I need to make sure I have removed all of these vulnerabilities and would like some advice on how to go about doing that. I think I am close, I just need a little more help.
Thanks,
Justin
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
allow traffic for those ports only from the specific ip`s that it needs access from/to
ASKER
I will do that for the services that are accessed by my web admin and myself. However, I would like to correct the outlined issues above first and then restrict by IP address.
Thanks,
Justin
Thanks,
Justin
Do you need to have this server enabled as a DNS server? From your requirements it doesn`t look like it so stop and disable the dns server service. In case you need it disable recursive queries
Make sure your MailEnable application is up to date from your scan it doesnt look like it is
Upgrade your mysql.
That should solve most of them Do a scan after this and send us an update
Make sure your MailEnable application is up to date from your scan it doesnt look like it is
Upgrade your mysql.
That should solve most of them Do a scan after this and send us an update
ASKER
I wasn't sure how to disable recursive DNS. So to do that, I just need to stop and disable the DNS service? I though it would be taken care of if I blocked DNS in the firewall but I guess now.
I disputed the MailEnable one because it is already up to date.
I want to update mysql but I don't want to cause any issues with the current database. Can I just download MySQL and update it in place without trouble? Basically, I don't want to risk a problem with this.
Thanks,
Justin
I disputed the MailEnable one because it is already up to date.
I want to update mysql but I don't want to cause any issues with the current database. Can I just download MySQL and update it in place without trouble? Basically, I don't want to risk a problem with this.
Thanks,
Justin
You can either remove the dns service or disable the service under administrative tools -> services
Make a backup of the current mysql database and then upgrade it and do a restore.
You should take a snapshot or a backup of the machine before you start doing anything so you can get back to a previous state if needed.
Make a backup of the current mysql database and then upgrade it and do a restore.
You should take a snapshot or a backup of the machine before you start doing anything so you can get back to a previous state if needed.
ASKER
I checked DNS and their is just a DNS client service and it is set to manual and is stopped. I don't think that takes care of the recursive issue?
I don't thinK I can make an image of the machine. It is hosted and I don't think that option is available.
I don't thinK I can make an image of the machine. It is hosted and I don't think that option is available.
In server manager under roles, remove the dns server role.
ASKER
I checked, their role is not enabled. The only role enabled is IIS.
then im not sure why that error is there about dns... can you try to telnet to port 53 on that server and nslookup using that server?
ASKER
Maybe it is a false positive? Telnet is blocked and not enabled on the remote server. I did an NSlookup and appeared to receive good results.
you checking it wrong :)
open command prompt from another machine that has telnet installed
type in telnet ip 53
to check dns with nslookup
open command prompt
nslookup
>server ip
>google.com
open command prompt from another machine that has telnet installed
type in telnet ip 53
to check dns with nslookup
open command prompt
nslookup
>server ip
>google.com
ASKER
I tried to telnet and I get nothing. I am assuming that is good. I did NSlookup and received a proper response for server and address.
However, I just found out that disabling the firewall rule in Windows 2008 R2 server is not the same as enabling the rule and then blocking the protocol. I enabled all the rules for the protocols outlined in the scan results and then I blocked all of them. I am doing a rescan now and i'll report back when I know if this corrected my issue or not.
Thanks,
Justin
However, I just found out that disabling the firewall rule in Windows 2008 R2 server is not the same as enabling the rule and then blocking the protocol. I enabled all the rules for the protocols outlined in the scan results and then I blocked all of them. I am doing a rescan now and i'll report back when I know if this corrected my issue or not.
Thanks,
Justin
ASKER
I blocked all the protocol's in the firewall that were listed in the report above and did another scan last night. It only removed two of the port 3306 issues. The rest of them remain. Since all the ports are blocked, i'm not sure what I am missing here.
can you try ussing another product to scan it? like nessus maybe? or nmap?
ASKER
I suppose I could try but those are internal scans and what I need are external scans. Are you thinking they would provide me with different information? I do have another company that did a separate external scan but the information they provided was not much better.
Thanks,
Justin
Thanks,
Justin
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
oh, if you do an internal scan those are always going to show up because they are wide open to the local system, you need to do an external scan to check if the firewall is actually working.
you could award some points you know... :)
ASKER
I was not sure if I could give partial points or not. I can give you some points for your first answer. It wasn't exactly what I was looking for but it is pointing in the correct direction.
well were all here to help so whatever you feel is best
ASKER
I gave a B grade because the solution was generic and didn't fully provide instruction on how to obtain the results needed. It was correct though.
Thanks for all the help!
Thanks for all the help!
ASKER
I need to know what else I can safely block without breaking that functionality.
Thanks,
Justin