Snow Leopard Server Single Sign-On Not Working
First, a disclaimer: I don't know Macs very well but I need to setup a Mac Mini Server for a small Mac network. I've setup dozens of Windows servers and most times, the setup goes well but setting up this Mac server has been quite a challenge. So please be patient with me if I give you "dumb" responses to your suggestions.
With the disclaimer in place, on to the problem...
Server is a Mac Mini Server running Snow Leopard Server. DHCP installed and working. DNS installed and working. Configured to be Open Directory Master. Client machine being used for testing is a MacBook Pro running Leopard.
I added the MacBook to the directory using Directory Utility and was able to logon to the MacBook as a directory user but as soon as I try to browse to the server in Finder, I get asked for credentials.
It's my understanding that when you configure the server to be an Open Directory Master and have users configured, the server automatically becomes a KDC and should look after the authentication request in the background so I shouldn't have been prompted for credentials.
Am I understanding this correctly? Is there something else that I need to configure?
Any help would be great.
With the disclaimer in place, on to the problem...
Server is a Mac Mini Server running Snow Leopard Server. DHCP installed and working. DNS installed and working. Configured to be Open Directory Master. Client machine being used for testing is a MacBook Pro running Leopard.
I added the MacBook to the directory using Directory Utility and was able to logon to the MacBook as a directory user but as soon as I try to browse to the server in Finder, I get asked for credentials.
It's my understanding that when you configure the server to be an Open Directory Master and have users configured, the server automatically becomes a KDC and should look after the authentication request in the background so I shouldn't have been prompted for credentials.
Am I understanding this correctly? Is there something else that I need to configure?
Any help would be great.
ASKER
My apologies but here is the first of my dumb responses.
I forgot to mention that not only are Macs fairly new to me but I've also never used Unix (10 years of Windows networking but no Linux or Unix).
I open terminal windows and changed to /System/Library/CoreServic
Also, in System preferences->Accounts->Log

I forgot to mention that not only are Macs fairly new to me but I've also never used Unix (10 years of Windows networking but no Linux or Unix).
I open terminal windows and changed to /System/Library/CoreServic
Also, in System preferences->Accounts->Log

Click the options button.
ASKER
Aha,
your client isn't running on Snow Leopard, right? This part of networking is a little bit different in 10.5... Anyway, you should have an Open Directory Utility in /Applications/Utilities. Navigate there, open LDAP and bind client to server
your client isn't running on Snow Leopard, right? This part of networking is a little bit different in 10.5... Anyway, you should have an Open Directory Utility in /Applications/Utilities. Navigate there, open LDAP and bind client to server
ASKER
You need to bind the client to OD using using Directory Utility.
ASKER
I thought binding took place when I added the OD server to the client as shown in the screen shot. Am I misundertanding this?
You need to click Services, LDAPv3 and enter auth details there
ASKER
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Is this a one-time configuration that applies to all users or does it need to be configured for each directory user? If it's a one-time thing, I assume I should use an administrative username & password.
Also, is there a way to make this happen automatically to save a few steps on each client when the server gets deployed?
Also, is there a way to make this happen automatically to save a few steps on each client when the server gets deployed?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
I am afraid you are going to spin your wheels unless you have a look at the OS X Server manuals. They are online at apple.com.
ASKER
I thought setting it up would be pretty straight forward (given that I'm very comfortable with Active Directory) and that I could avoid reading 500 pages of manuals.
Thanks for your help.
Thanks for your help.
Actually Mac OS X Server is a UNIX based server with additional features to ease OS X clients administration. It's not a click and forget solution even Apple's PR dept is trying hard to change it :)
IIRC 500 pages is just one manual, and there is more than 13 of them :)
IIRC 500 pages is just one manual, and there is more than 13 of them :)
You may not have to read 500 pages of manuals, but you sure should have a look at them, at least. One can't even avoid referring to the manual for a new TV or washing machine.
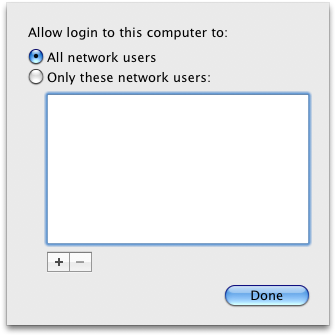
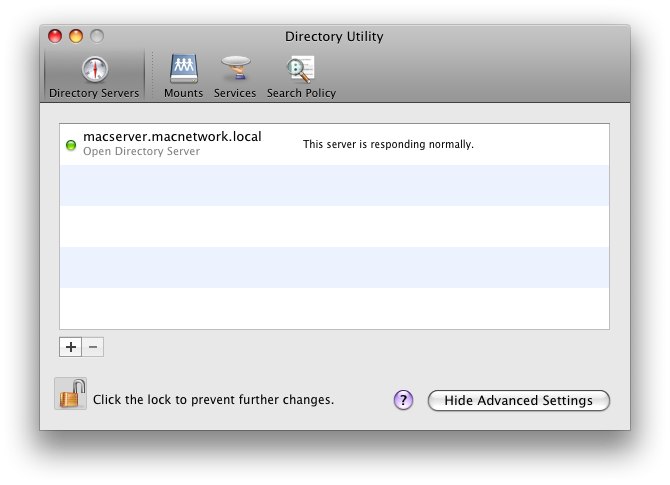
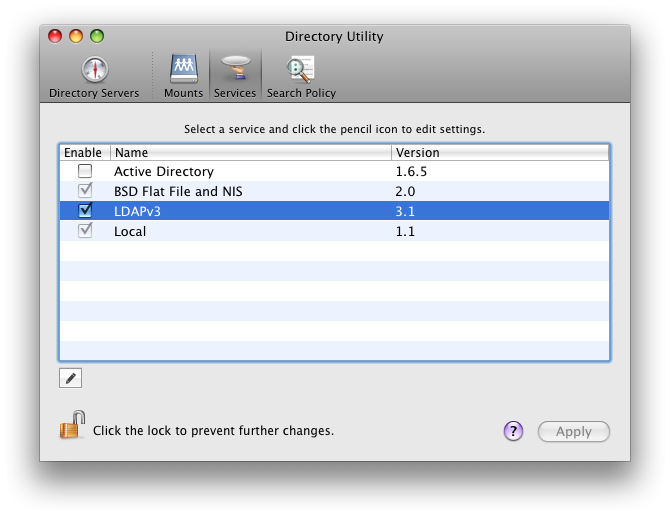
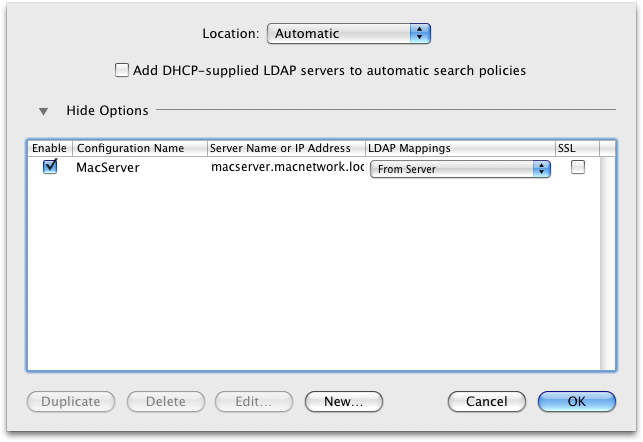
After successful login check if you got a ticket. Also, the machine must be bound to OD. (System preferences->Accounts->Log
Click your server, Edit ->Security