Dell PowerConnect 2748 Issue
Due to costs, I have setup a router-on-a-stick network using a Cisco ASA5510 connected to three interconnected PowerConnect 2748's. Last friday night I setup the VLANs on the all three and everything works great. My only issue, I am unable to ping / connect to any of the switches on the 192.168.100.2 (or any VLAN network for that matter other than the default VLAN 1) network even when my machine I am trying to ping / connect to is on the same network. I am currently able to make changes to the config by leaving port 45 untagged on all three swithced and left alone on the default VLAN 1. Below is what I did to set this up....
Thoughts?
Switch 192.168.100.2
- VLAN Membership page: click "Create VLAN" radio button, enter 2 in the vlan field, set port 1 to 'T' (for tagged), set port 48 to 'T' (for tagged), set ports 2 through 44 to 'U' for untagged, click "Apply Changes"
- VLAN Membership page: click "Create VLAN" radio button, enter 3 in the vlan field, set port 1 to 'T' (for tagged), set port 48 to 'T' (for tagged), click "Apply Changes"
- VLAN Membership page: click "Create VLAN" radio button, enter 4 in the vlan field, set port 1 to 'T' (for tagged), set port 48 to 'T' (for tagged), click "Apply Changes"
- VLAN Port Setting page (Apply for ports 2 through 44): Change "Interface" to "Port #", set "PVID" to 2, click "Apply Changes"
- VLAN Port Setting page (Apply for ports 1 & 48): Change "Interface" to "Port #", set "PVID" to 2, set to “Allow All” and click "Apply Changes"
Switch 192.168.100.3
- VLAN Membership page: click "Create VLAN" radio button, enter 2 in the vlan field, set port 48 to 'T' (for tagged), set port 47 to 'T' (for tagged), set ports 1 through 44 to 'U' for untagged, click "Apply Changes"
- VLAN Membership page: click "Create VLAN" radio button, enter 3 in the vlan field, set port 48 to 'T' (for tagged), set port 47 to 'T' (for tagged), click "Apply Changes"
- VLAN Membership page: click "Create VLAN" radio button, enter 4 in the vlan field, set port 48 to 'T' (for tagged), set port 47 to 'T' (for tagged), click "Apply Changes"
- VLAN Port Setting page (Apply for ports 1 through 44): Change "Interface" to "Port #", set "PVID" to 2, click "Apply Changes"
- VLAN Port Setting page (Apply for port 47): Change "Interface" to "Port # 47", set "PVID" to 2, set to “Allow All” and click "Apply Changes"
- VLAN Port Setting page (Apply for port 48): Change "Interface" to "Port # 48", set "PVID" to 2, set to “Allow All” and click "Apply Changes"
Switch 192.168.100.4
- VLAN Membership page: click "Create VLAN" radio button, enter 2 in the vlan field, set port 48 to 'T' (for tagged), click "Apply Changes"
- VLAN Membership page: click "Create VLAN" radio button, enter 3 in the vlan field, set port 48 to 'T' (for tagged), set ports 1 through 36 to 'U' for untagged, click "Apply Changes"
- VLAN Membership page: click "Create VLAN" radio button, enter 4 in the vlan field, set port 48 to 'T' (for tagged), set ports 37 through 44 to 'U' for untagged, click "Apply Changes"
- VLAN Port Setting page (Apply for ports 1 through 36): Change "Interface" to "Port #", set "PVID" to 3, click "Apply Changes"
- VLAN Port Setting page (Apply for ports 37 through 44): Change "Interface" to "Port #", set "PVID" to 4, click "Apply Changes"
- VLAN Port Setting page (Apply for port 48): Change "Interface" to "Port # 48", set "PVID" to 2, set to “Allow All” and click "Apply Changes"
Thoughts?
Switch 192.168.100.2
- VLAN Membership page: click "Create VLAN" radio button, enter 2 in the vlan field, set port 1 to 'T' (for tagged), set port 48 to 'T' (for tagged), set ports 2 through 44 to 'U' for untagged, click "Apply Changes"
- VLAN Membership page: click "Create VLAN" radio button, enter 3 in the vlan field, set port 1 to 'T' (for tagged), set port 48 to 'T' (for tagged), click "Apply Changes"
- VLAN Membership page: click "Create VLAN" radio button, enter 4 in the vlan field, set port 1 to 'T' (for tagged), set port 48 to 'T' (for tagged), click "Apply Changes"
- VLAN Port Setting page (Apply for ports 2 through 44): Change "Interface" to "Port #", set "PVID" to 2, click "Apply Changes"
- VLAN Port Setting page (Apply for ports 1 & 48): Change "Interface" to "Port #", set "PVID" to 2, set to “Allow All” and click "Apply Changes"
Switch 192.168.100.3
- VLAN Membership page: click "Create VLAN" radio button, enter 2 in the vlan field, set port 48 to 'T' (for tagged), set port 47 to 'T' (for tagged), set ports 1 through 44 to 'U' for untagged, click "Apply Changes"
- VLAN Membership page: click "Create VLAN" radio button, enter 3 in the vlan field, set port 48 to 'T' (for tagged), set port 47 to 'T' (for tagged), click "Apply Changes"
- VLAN Membership page: click "Create VLAN" radio button, enter 4 in the vlan field, set port 48 to 'T' (for tagged), set port 47 to 'T' (for tagged), click "Apply Changes"
- VLAN Port Setting page (Apply for ports 1 through 44): Change "Interface" to "Port #", set "PVID" to 2, click "Apply Changes"
- VLAN Port Setting page (Apply for port 47): Change "Interface" to "Port # 47", set "PVID" to 2, set to “Allow All” and click "Apply Changes"
- VLAN Port Setting page (Apply for port 48): Change "Interface" to "Port # 48", set "PVID" to 2, set to “Allow All” and click "Apply Changes"
Switch 192.168.100.4
- VLAN Membership page: click "Create VLAN" radio button, enter 2 in the vlan field, set port 48 to 'T' (for tagged), click "Apply Changes"
- VLAN Membership page: click "Create VLAN" radio button, enter 3 in the vlan field, set port 48 to 'T' (for tagged), set ports 1 through 36 to 'U' for untagged, click "Apply Changes"
- VLAN Membership page: click "Create VLAN" radio button, enter 4 in the vlan field, set port 48 to 'T' (for tagged), set ports 37 through 44 to 'U' for untagged, click "Apply Changes"
- VLAN Port Setting page (Apply for ports 1 through 36): Change "Interface" to "Port #", set "PVID" to 3, click "Apply Changes"
- VLAN Port Setting page (Apply for ports 37 through 44): Change "Interface" to "Port #", set "PVID" to 4, click "Apply Changes"
- VLAN Port Setting page (Apply for port 48): Change "Interface" to "Port # 48", set "PVID" to 2, set to “Allow All” and click "Apply Changes"
You'll need to assign an IP interface for each switch on each VLAN. I'm not sure if the 2700 series firmware has the ability to do this or not.
er... assign an IP address to each VLAN interface on each switch.
Grammar failing - must have coffee...
Grammar failing - must have coffee...
Here's an example from a 3500 series (CLI based, you'll have to do the equivelent in the web interface on the 2700)
interface vlan 1
ip address 172.16.1.1 255.255.255.0
exit
ip default-gateway 172.16.1.254ASKER
So essentially its about the default gateway? Because currently I have it set 192.168.100.1 which is ASA5510.
Not necessarily. It's about setting the IP address (and optionally, default gateway) for the management interface of each VLAN.
Since you've set each port in the vlan to use a PVID, there is no way for frames from a port in 1 VLAN to pass to another VLAN without going through a router or an L3 switch first.
Think of it this way:
Each VLAN is a separate network.
Each switch within each VLAN has to have a management IP address.
To be able to view the webserver, you need to either :
be in the management VLAN (typically VLAN 1) and have an IP address set on each switch for the for the switch as a whole,
-or-
Put a management IP address on the webserver for that switch within each VLAN that you want to be able to access the admin page from.
-or-
Create a 5th VLAN for untagged packets that goes nowhere, and enforce VLAN tagging on all your endstations, then add a management IP address for the switch in that VLAN.
Since you've set each port in the vlan to use a PVID, there is no way for frames from a port in 1 VLAN to pass to another VLAN without going through a router or an L3 switch first.
Think of it this way:
Each VLAN is a separate network.
Each switch within each VLAN has to have a management IP address.
To be able to view the webserver, you need to either :
be in the management VLAN (typically VLAN 1) and have an IP address set on each switch for the for the switch as a whole,
-or-
Put a management IP address on the webserver for that switch within each VLAN that you want to be able to access the admin page from.
-or-
Create a 5th VLAN for untagged packets that goes nowhere, and enforce VLAN tagging on all your endstations, then add a management IP address for the switch in that VLAN.
I'm not familiar with the ASA, but if it were my network, I'd see if it can act as a GVRP server and use it to dynamically assign the VLANs based on the endstation user and/or endstation MAC.
ASKER
"Put a management IP address on the webserver for that switch within each VLAN that you want to be able to access the admin page from."
I have given each switch an IP address from the VLAN network that I want access from and I still can't ping/connect to the web interface...
I have given each switch an IP address from the VLAN network that I want access from and I still can't ping/connect to the web interface...
Oh, and you'll want to set the port(s) that feed to the ASA to trunk mode
ASKER
Right and I have already done that too. Everything works ok except this one thing...WEIRD!
Which port(s) are you using to uplink to the ASA and the next switch in the physical LAN?
Is there any situation where the ASA would send untagged frames?
Is there any situation where the ASA would send untagged frames?
ASKER
I am using port1 on the main switch as a Trunk to the ASA then I have a trunk on port 48 on the same switch then on switch two i have trunk ports on 47 and 48 and another trunk on port 48 on switch three.
OK, I believe I have a solution, but I want to make sure my assumptions are correct. Let me know if any of the following statements are wrong:
Each VLAN is in a different IP subnet and the ASA handles all inter-VLAN routing
All traffic from the ASA is tagged
All ports except the Trunk ports are in Access mode
Ports e45-e47 on all switches except SW2 (192.168.100.3) e47 are in the Management VLAN (VLAN 1) and may talk to each other
All ports except the management and trunk ports may only talk to within their assigned VLAN
Physical access to the segments on the Management ports is secure
Devices in the management VLAN may talk to devices outside the management VLAN without using the ASA, but only if the traffic is tagged
Oops, almost forgot:
Only devices in the management VLAN may access the switches' configuration page
Just found your previous question, and I think I understand what you're wanting to do now.
To allow any device in VLAN 2 to control the switches, set the IP address of the switch to something in VLAN2's range (which I assume you did), and set the Interface to VLAN2, then hit "Apply Changes"
Here's a screenshot from a 3524:
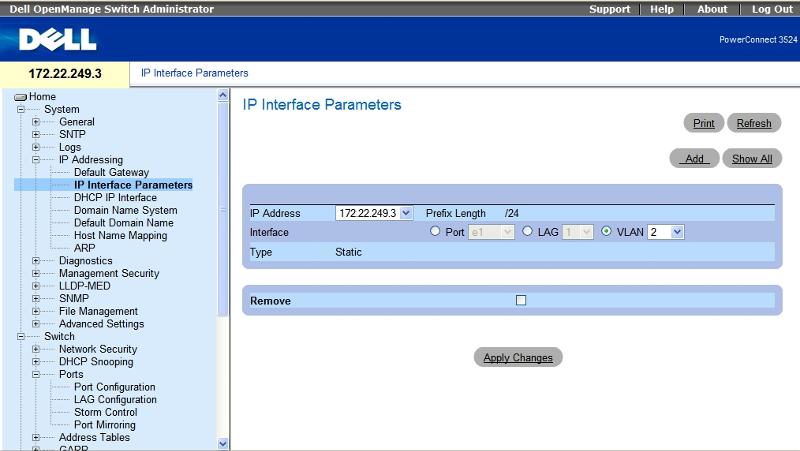
To allow any device in VLAN 2 to control the switches, set the IP address of the switch to something in VLAN2's range (which I assume you did), and set the Interface to VLAN2, then hit "Apply Changes"
Here's a screenshot from a 3524:

ASKER
That looks more like. I will try tomorrow and let you know. thanks!
ASKER
This is exactly what I need to do but this option is not available on the 2748...Thanks for you help on this. I really appreciate it.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Great idea. Thanks!