jameskane
asked on
Database Update Security
I have a database update facility, updating a website with images and text. The updating is restricted to a couple of people (customers). The database has been interfered with - text changed and images removed for supporting folder.
The setup includes a secure folder on the server I use - challenging for a UN/PW to access the editor. I have checked with the Server people and they confirm that I have set it up correctly and that everything is correct at their end. The suggest the hacking occurs at the backend.
I notice that the server 'challenge window' contains a warning - see attached image
Server people say the problem is not theirs, but that someone accessed the editor through the backend - I do not understand this. I am attaching an image, which says that the server is requesting that un/pw be sent in an insecure manner.
I am using Coldfusion 9
The database is msaccess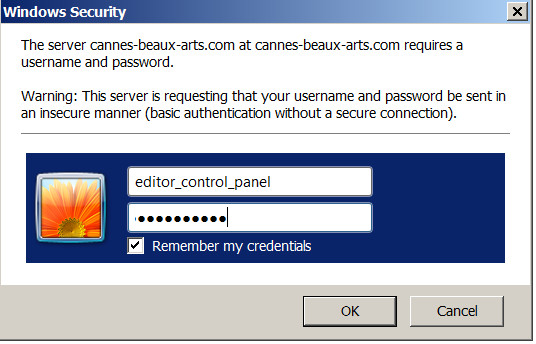
This is the link to the editor
http://cannes-beaux-arts.com/abac_new/security/EditingFacility.cfm
Many thanks for any help.
The setup includes a secure folder on the server I use - challenging for a UN/PW to access the editor. I have checked with the Server people and they confirm that I have set it up correctly and that everything is correct at their end. The suggest the hacking occurs at the backend.
I notice that the server 'challenge window' contains a warning - see attached image
Server people say the problem is not theirs, but that someone accessed the editor through the backend - I do not understand this. I am attaching an image, which says that the server is requesting that un/pw be sent in an insecure manner.
I am using Coldfusion 9
The database is msaccess

This is the link to the editor
http://cannes-beaux-arts.com/abac_new/security/EditingFacility.cfm
Many thanks for any help.

ASKER
Thanks for reply foofragger,
This will show my amateur status !!! Can you say more about your question ?
This will show my amateur status !!! Can you say more about your question ?
ASKER
http://localhost:8500/ABAC_New/FORM%20TEXTAREA/FORM_update_journalPages.cfm?title=seven
Foofragger, after a bit of reading, here is where my thoughts are :
Problem occurs during an update session, where updater has successfully accessed the update facility in the server. Perhaps the update connection has been left on by the updater.
The relating hacking is some sort of 'sql injection' - you see at the top the method of accessing the database via the user clicking a specific page.
Maybe the solution is as simple as making sure the editor is disconnected after an editing session - which should only last for around 30 minutes.
??
James
Foofragger, after a bit of reading, here is where my thoughts are :
Problem occurs during an update session, where updater has successfully accessed the update facility in the server. Perhaps the update connection has been left on by the updater.
The relating hacking is some sort of 'sql injection' - you see at the top the method of accessing the database via the user clicking a specific page.
Maybe the solution is as simple as making sure the editor is disconnected after an editing session - which should only last for around 30 minutes.
??
James
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks SidFishes, I just ran scrawlr and got no vunerabilities. I have been using cfqueryparam religiously, which probably explains why.
I note the warning message on the login page (with IE, but not with Firefox) as per image attached above. But that is not mentioned on scrawlr.
The Server people tell me that I have set up the login correctly. So, maybe its just that the updater left the editor connection live and that allowed access by some hacker ?
I note the warning message on the login page (with IE, but not with Firefox) as per image attached above. But that is not mentioned on scrawlr.
The Server people tell me that I have set up the login correctly. So, maybe its just that the updater left the editor connection live and that allowed access by some hacker ?
from IE7 & up, directory basic authentication will -by design- give you this warning.
It's basic because Uname & pwd are sent in the clear. If someone was monitoring traffic they could have sniffed the password to the directory. This wouldn't necessarily need any db access. They could simply get to the folder and delete files. However, if you've used -your- un/pwd combination for testing and it's the same as the un/pwd combination for the admin interface or db, then the hackers would not have needed SQLi - they would simply log in as you. This is all a guess, but it is a definite possibility.
That being said, you should run scrubbr to make sure your db is not compromised and change your un/pwd.
It's basic because Uname & pwd are sent in the clear. If someone was monitoring traffic they could have sniffed the password to the directory. This wouldn't necessarily need any db access. They could simply get to the folder and delete files. However, if you've used -your- un/pwd combination for testing and it's the same as the un/pwd combination for the admin interface or db, then the hackers would not have needed SQLi - they would simply log in as you. This is all a guess, but it is a definite possibility.
That being said, you should run scrubbr to make sure your db is not compromised and change your un/pwd.
ASKER
Many thanks for your time SidFishes
One last follow on - My server company does backups, so I got back to a database just before the corruption happened. I am using that now. Is is necessary to run scrubbr in this situation ? I have already changed the un/pw.
James
One last follow on - My server company does backups, so I got back to a database just before the corruption happened. I am using that now. Is is necessary to run scrubbr in this situation ? I have already changed the un/pw.
James
I would as i'd be nervous about when the problem started. Could have happened long before anything was actually done. Hackers often use bots to compromise sites which are flagged for "personal attention" which may take some time to get to.
ASKER
Ah, I see - ok I will do the scrubbing !!
Lots of thanks once again,
james
Lots of thanks once again,
james
I received a similar error when I enter a page that is running https, but logging in unencrypted ....