inited
asked on
Proxy for Linux with Authentication - everything encrypted!
Hi guys,
I'm currently having a big dilemma and I don't know how to deal with.
My boss travels around the world, so he connects to the Internet from different hotels access points.
What I need to do is setup a proxy for him, that would encrypt EVERYTHING that happens behind that proxy.Links that he visits, everything.
Of course, he has to authenticate in the proxy(encrypted also, I wouldn't like someone to sniff those passwords).
Thought about squid with SSL and authentication, but I'm very afraid that something would go on plain text.
Please give me some ideas and if you had experience with this, some config files to implement this.
Thanks so much for your time!
I'm currently having a big dilemma and I don't know how to deal with.
My boss travels around the world, so he connects to the Internet from different hotels access points.
What I need to do is setup a proxy for him, that would encrypt EVERYTHING that happens behind that proxy.Links that he visits, everything.
Of course, he has to authenticate in the proxy(encrypted also, I wouldn't like someone to sniff those passwords).
Thought about squid with SSL and authentication, but I'm very afraid that something would go on plain text.
Please give me some ideas and if you had experience with this, some config files to implement this.
Thanks so much for your time!
Encryption can be a touchy subject in a number of countries. It can be outright banned or a license required for it's use. This site http://rechten.uvt.nl/koops/cryptolaw/ has info about many countries.
You need to explain a little bit more. Will he be accessing content on your Linux machines? Will he be browsing content over your Linux boxes? If so, you need to implement https. Connections through https will be totally encrypted.
Now it depends upon the content that he may be accessing on your machines.
In network terminology he may be looking for getting tunnels set up for himself. It could be VPN where you can access private content through tunnels. The basic idea behind tunnels is that the entire network traffic travels in packets. Each packet is totally encrypted and a new header is attached onto it, that only tells about destination address, etc.
There could be ssh tunnel as well. You could probably set up Linux based software VPN.
http://www.linuxhomenetworking.com/wiki/index.php/Quick_HOWTO_:_Ch35_:_Configuring_Linux_VPNs
Now it depends upon the content that he may be accessing on your machines.
In network terminology he may be looking for getting tunnels set up for himself. It could be VPN where you can access private content through tunnels. The basic idea behind tunnels is that the entire network traffic travels in packets. Each packet is totally encrypted and a new header is attached onto it, that only tells about destination address, etc.
There could be ssh tunnel as well. You could probably set up Linux based software VPN.
http://www.linuxhomenetworking.com/wiki/index.php/Quick_HOWTO_:_Ch35_:_Configuring_Linux_VPNs
ssh tunneling
http://www.revsys.com/writings/quicktips/ssh-tunnel.html
http://www.revsys.com/writings/quicktips/ssh-tunnel.html
ASKER
DaveBaldwin: the law would be my last problem.
farzanj: He would not access files on the Linux server. He will just use the the Linux server to hide his traffic.
Here are the steps how I see them:
1. Login encrypted into the proxy.
2. Start making traffic via SSL.
farzanj: He would not access files on the Linux server. He will just use the the Linux server to hide his traffic.
Here are the steps how I see them:
1. Login encrypted into the proxy.
2. Start making traffic via SSL.
ASKER
I simply don't understand the concept of SSH tunneling. What should I do? Will I need squid also? How will he browse the internet?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
farzanj, thank you for your effort.
Due my understanding, he will need linux on his box, is that correct?
I mean, he will need ssh on both remote/local computers, isn't it?
Due my understanding, he will need linux on his box, is that correct?
I mean, he will need ssh on both remote/local computers, isn't it?
ASKER
Tried this procedure:
http://www.makeuseof.com/tag/how-to-tunnel-traffic-with-ssh/
I have a Windows box and the remote server that has SSH installed.
The question is, how I must configure putty port forwarding and Firefox? Is the remote port 22 and the local port 80? Am I correct?
http://www.makeuseof.com/tag/how-to-tunnel-traffic-with-ssh/
I have a Windows box and the remote server that has SSH installed.
The question is, how I must configure putty port forwarding and Firefox? Is the remote port 22 and the local port 80? Am I correct?
ASKER
I'm doing something bad. The only result I have is: The proxy server is refusing connections.
The scenario is:
- Windows computer, that would like to connect over SSH for both HTTP and DNS protocols
- Linux server, that has the SSH installed listening on port 22
Please help me to configure the options in Putty:
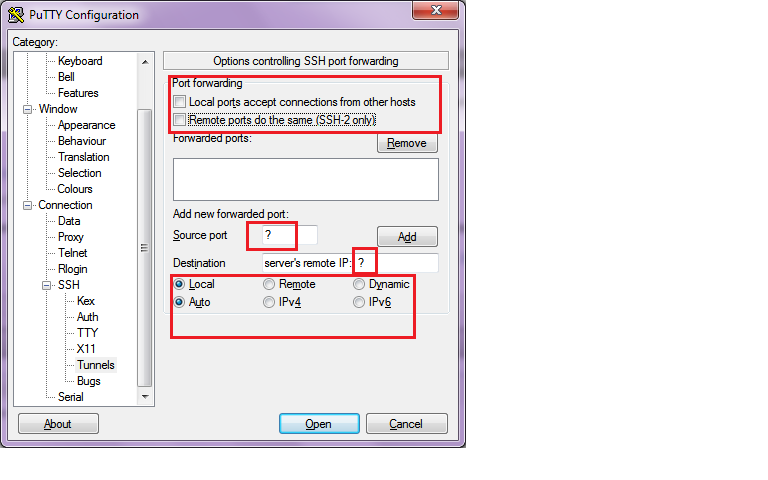
and Firefox:

Thank you!
The scenario is:
- Windows computer, that would like to connect over SSH for both HTTP and DNS protocols
- Linux server, that has the SSH installed listening on port 22
Please help me to configure the options in Putty:

and Firefox:

Thank you!
Here you go:
http://realprogrammers.com/how_to/set_up_an_ssh_tunnel_with_putty.html
Your best bet is getting VNC server on Linux machine and VNC viewer on Windows machine. Windows will see Linux desktop and you can encrypt the communication using ssh tunneling.
http://realprogrammers.com/how_to/set_up_an_ssh_tunnel_with_putty.html
Your best bet is getting VNC server on Linux machine and VNC viewer on Windows machine. Windows will see Linux desktop and you can encrypt the communication using ssh tunneling.
"He will just use the the Linux server to hide his traffic."
I think your req is not completelly defined yet .
if your boss is in Singapoore and he wants to browse www.ibm.com completelly hidding (encrypting) his traffic that cannot be done with an ssh tunnel actually it cannot be done at all if the destination web page does not support some kind of encryption like i.e. https...
A different thing would be if your boss accepts to browse ibm.com with let say "half-leg privacy";
Then you need a "secure proxy" where the traffic between your boss' hotel (the unsecure place ) and the secure proxy at your company (the trusted zone) goes completely encrypted but the traffic from the secure proxy to www.ibm.com would go as plain http...
This way you protect your boss traffic up to the "trusted zone", from the trusted zone and on the traffic goes like http/https/ftp or what ever your boss was originally trying to get.
It would be like having your boss always browsing Internet from "inside" your company. I think this is what your boss really needs.
This set up can be implemented with Squid.
this is just a link, probably not the best one but this guy gives the guide line for implementing a secure proxy
http://www.sajalkayan.com/secure-proxy-using-squid.html
I think your req is not completelly defined yet .
if your boss is in Singapoore and he wants to browse www.ibm.com completelly hidding (encrypting) his traffic that cannot be done with an ssh tunnel actually it cannot be done at all if the destination web page does not support some kind of encryption like i.e. https...
A different thing would be if your boss accepts to browse ibm.com with let say "half-leg privacy";
Then you need a "secure proxy" where the traffic between your boss' hotel (the unsecure place ) and the secure proxy at your company (the trusted zone) goes completely encrypted but the traffic from the secure proxy to www.ibm.com would go as plain http...
This way you protect your boss traffic up to the "trusted zone", from the trusted zone and on the traffic goes like http/https/ftp or what ever your boss was originally trying to get.
It would be like having your boss always browsing Internet from "inside" your company. I think this is what your boss really needs.
This set up can be implemented with Squid.
this is just a link, probably not the best one but this guy gives the guide line for implementing a secure proxy
http://www.sajalkayan.com/secure-proxy-using-squid.html
do not implement secure remote desktop strategies, they demand a lot of bandwith; hotels and airports are famous for slow Internet acces, your boss will complain about speed...
ASKER
"if your boss is in Singapoore and he wants to browse www.ibm.com completelly hidding (encrypting) his traffic that cannot be done with an ssh tunnel actually it cannot be done at all if the destination web page does not support some kind of encryption like i.e. https..."
pmasotta, what do you mean? From my understanding you can browse any website via the SSH tunnel. You don't need https for that.
pmasotta, what do you mean? From my understanding you can browse any website via the SSH tunnel. You don't need https for that.
if you connect to a pure http site (non https enabled) let say http://www.xxx.com how are you going to encrypt the traffic reaching te xxx web server? how is going xxx web server to decrypt your traffic if it is just only a plain http server??
an ssh tunnel can be set when at both ends of the tunnel there are available ssh encrypt/decrypt capabilities...
then you cannot set an ssh tunnel from your boss hotel up to let say http://www.ibm.com server...
an ssh tunnel can be set when at both ends of the tunnel there are available ssh encrypt/decrypt capabilities...
then you cannot set an ssh tunnel from your boss hotel up to let say http://www.ibm.com server...
> "if your boss is in Singapoore and he wants to browse www.ibm.com completelly hidding (encrypting) > his traffic that cannot be done with an ssh tunnel actually it cannot be done at all if the destination web > page does not support some kind of encryption like i.e. https..."
This is incorrect. When you enable SOCKS proxy over the SSH and you setup your proxy to use SOCKS over the localhost all your traffic including FTP, HTTP and HTTPS will go through the SSH server..
So you have 2 options:
- Setup a VPN on your company (you can install an easy to install, maintain and manage VPN with 2 free licenses of connections you cna go gfor OpenVPN-AS
- You go over SSH and SOCKS and encrypt all your Web traffic through SOCKS. If you want to encrypt mail too you can't achieve this if your boss uses Outlook. But then again Both SMTP and POP3 (or imap for that matters) support SSL and they can always be used encrypted anywhere.
IF you have other traffic that needs to be encrypted I'd suggest you to go directly with OpenVPN or OpenVPN-AS depending on how you're ready for D-I-Y.
Cheers,
K:
This is incorrect. When you enable SOCKS proxy over the SSH and you setup your proxy to use SOCKS over the localhost all your traffic including FTP, HTTP and HTTPS will go through the SSH server..
So you have 2 options:
- Setup a VPN on your company (you can install an easy to install, maintain and manage VPN with 2 free licenses of connections you cna go gfor OpenVPN-AS
- You go over SSH and SOCKS and encrypt all your Web traffic through SOCKS. If you want to encrypt mail too you can't achieve this if your boss uses Outlook. But then again Both SMTP and POP3 (or imap for that matters) support SSL and they can always be used encrypted anywhere.
IF you have other traffic that needs to be encrypted I'd suggest you to go directly with OpenVPN or OpenVPN-AS depending on how you're ready for D-I-Y.
Cheers,
K:
"if your boss is in Singapoore and he wants to browse www.ibm.com completelly hidding (encrypting) > his traffic that cannot be done with an ssh tunnel actually it cannot be done at all if the destination web page does not support some kind of encryption like i.e. https..."
This is correct.
"This is incorrect. When you enable SOCKS proxy over the SSH and you setup your proxy to use SOCKS over the localhost all your traffic including FTP, HTTP and HTTPS will go through the SSH server.. "
you are providing a false sense of security: the objective of SOCKS is to facilitate user traffic across firewalls (from an administering point of view). The security that SOCKS + SSH can give is between the 2 peers that understand SOCKS but as I said before if I want to reach www.ibm.com and that server only understand HTTP even using a SOCKS server in the middle the leg going from the SOCKS server to the HTTP server will be completelly plain HTTP. Let say www.ibm.com asks for an HTTP authentication, well that name and password will hit the net in plain ascii between the SOCKS server and htttp://www.ibm.com
SOCKS is not made for what inited needs.
VPNs are not made for what inited needs.
This is correct.
"This is incorrect. When you enable SOCKS proxy over the SSH and you setup your proxy to use SOCKS over the localhost all your traffic including FTP, HTTP and HTTPS will go through the SSH server.. "
you are providing a false sense of security: the objective of SOCKS is to facilitate user traffic across firewalls (from an administering point of view). The security that SOCKS + SSH can give is between the 2 peers that understand SOCKS but as I said before if I want to reach www.ibm.com and that server only understand HTTP even using a SOCKS server in the middle the leg going from the SOCKS server to the HTTP server will be completelly plain HTTP. Let say www.ibm.com asks for an HTTP authentication, well that name and password will hit the net in plain ascii between the SOCKS server and htttp://www.ibm.com
SOCKS is not made for what inited needs.
VPNs are not made for what inited needs.
ASKER
guys,
pmasotta,
If the final destination website supports only HTTP, the client would go to the server over SSH tunnel.
Is that correct?
I mean, nothing is plain text and not all the websites should have HTTPS, because the traffic is done via SSH tunnel, am I correct?
pmasotta,
If the final destination website supports only HTTP, the client would go to the server over SSH tunnel.
Is that correct?
I mean, nothing is plain text and not all the websites should have HTTPS, because the traffic is done via SSH tunnel, am I correct?
you are wrong.
encryped http traffic is only possible between peers that can encrypt/decrypt traffic. A web site that only supports HTML cannot be the end of an SSH tunnel.
If your boss goes to http://www.ibm.com passing by a "secure proxy" or a server using SOCKS+SSH the only segment of the communication that is encrypted is from your boss browser at his hotel up to the secure proxy or SOCKS server at your company. From there to ibm's http server the communication has to be plain HTML.
Then if the http://www.ibm.com site has a market area where your boss is asked to provide his credit card info for buying xx product, please tell your boss that even when you set-up a very secure system for him to browse the net he SHOULD NEVER give his credit card info on such conditions.
If you ask why? the answer is because the communication between the secure proxy and the destination http server is exposed, then a CC sniffer could very well gather your boss cc's info.
Then, avoid giving to your boss a false sense of security; implementing a secure proxy or a SOCKS alternative will not add security to a plain HTML server and your boss has to know that.
Beside all of this SOCKS is ment for a different thing, if I were you I'd explain to your boss how the security of a secure proxy works.
He's going to be protected about people at his hotel/bar knowing where your boss is browsing an the content of that browse, but the comunication security AFTER the secure proxy will always rely/depend on the destination web page security.
encryped http traffic is only possible between peers that can encrypt/decrypt traffic. A web site that only supports HTML cannot be the end of an SSH tunnel.
If your boss goes to http://www.ibm.com passing by a "secure proxy" or a server using SOCKS+SSH the only segment of the communication that is encrypted is from your boss browser at his hotel up to the secure proxy or SOCKS server at your company. From there to ibm's http server the communication has to be plain HTML.
Then if the http://www.ibm.com site has a market area where your boss is asked to provide his credit card info for buying xx product, please tell your boss that even when you set-up a very secure system for him to browse the net he SHOULD NEVER give his credit card info on such conditions.
If you ask why? the answer is because the communication between the secure proxy and the destination http server is exposed, then a CC sniffer could very well gather your boss cc's info.
Then, avoid giving to your boss a false sense of security; implementing a secure proxy or a SOCKS alternative will not add security to a plain HTML server and your boss has to know that.
Beside all of this SOCKS is ment for a different thing, if I were you I'd explain to your boss how the security of a secure proxy works.
He's going to be protected about people at his hotel/bar knowing where your boss is browsing an the content of that browse, but the comunication security AFTER the secure proxy will always rely/depend on the destination web page security.
ASKER
pmasotta,
Let's take the examemple attached in the topology i have draw-ed. Please take a look.
My boss is at a hotel doing a http querry over the HTTP tunel.
My only goal is that the traffic not to be sniffed between his computer and the hotel's gateway (or wireless router in this example).
It's obvios that the SSH Server will forward text in plain text from the SSH server to the HTTP server.
BUT, at least the guys from the hotel/airport/any other traps on the way will see junk text.
AM I CORRECT?
Hotel-Example.png
Let's take the examemple attached in the topology i have draw-ed. Please take a look.
My boss is at a hotel doing a http querry over the HTTP tunel.
My only goal is that the traffic not to be sniffed between his computer and the hotel's gateway (or wireless router in this example).
It's obvios that the SSH Server will forward text in plain text from the SSH server to the HTTP server.
BUT, at least the guys from the hotel/airport/any other traps on the way will see junk text.
AM I CORRECT?
Hotel-Example.png
ASKER
ROFL I meant PLAIN TEXT TRAFFIC in the drawing, NOT PAIN text traffic. Now it's a pain that's a fact.
Can anyone please confirm that my topology is correct? I mean, the administrator of the hotel's gateway would see no HTTP traffic, isn't it?
Can anyone please confirm that my topology is correct? I mean, the administrator of the hotel's gateway would see no HTTP traffic, isn't it?
1) your topology is correct
2) Now it sounds obvious to you that the SSH Server will forward text in plain text from the SSH server to the HTTP server. But it didn't sound so obvious at ID:36174081 nor at ID:27187770 either when you asked everything encrypted behind the proxy...
2) Now it sounds obvious to you that the SSH Server will forward text in plain text from the SSH server to the HTTP server. But it didn't sound so obvious at ID:36174081 nor at ID:27187770 either when you asked everything encrypted behind the proxy...
ASKER
Thank you farzanj.
ASKER
pmasotta, I have understood your point of view now.
Thank you, your comment was helpful.
Thank you, your comment was helpful.
no you didn't.
ASKER
pmasotta, what do you mean?