Firewalls Failover
how we can make fail over for TWO Different Vendors of Firewalls.
1) Cisco ASA
2) JUNIPER SSG or any other Juniper Firewall
1) Cisco ASA
2) JUNIPER SSG or any other Juniper Firewall
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
its not so clear, please elaborate more...
see this point with below statement ..........................
"Dual firewall architecture will be employed to restrict traffic between the segments
and the internet.
The internal and external firewalls are also chosen from different vendors. The advantage of these would be that in the event that the external firewall was compromised due to vulnerabilities associated with it, the internal network and critical resources would still be protected by the internal
firewall."
see this point with below statement ..........................
"Dual firewall architecture will be employed to restrict traffic between the segments
and the internet.
The internal and external firewalls are also chosen from different vendors. The advantage of these would be that in the event that the external firewall was compromised due to vulnerabilities associated with it, the internal network and critical resources would still be protected by the internal
firewall."
Without more context, that sounds like having firewalls in series
{internet}--[Firewall-a]--
This is not "failover" but rather "defence in depth"
However, it can lead to other issues.
{internet}--[Firewall-a]--
This is not "failover" but rather "defence in depth"
However, it can lead to other issues.
ASKER
how there can be issues, we will use 4 Firewalls as "Defense in Depth"
What the sentence basically mean is that as a recommended secure network architecture; its is good to have one firewall, may be of Ciso as your internal firewall and may be Juniper as the firewalls that connect to Internet.
Check the attached file. There is a very low chance the with the shown connection between firewalls, there will be any downtime issues.
Now if you need, suppose, the core firewalls to be one of Juniper and one of ciso, then you will need a load balancer, but its recommended to go with same vendor when creating a cluster firewall. Drawing1.pdf
Check the attached file. There is a very low chance the with the shown connection between firewalls, there will be any downtime issues.
Now if you need, suppose, the core firewalls to be one of Juniper and one of ciso, then you will need a load balancer, but its recommended to go with same vendor when creating a cluster firewall. Drawing1.pdf
4 layers of NAT ?
Where do VPNs terminate ?
Where do VPNs terminate ?
from your text you will need a total of 4 firewalls
2 Cisco
2 Juniper
2 will face the internet and will be set in active/passive mode
the next 2 will face the first two and also will be set in active/passive mode
that will give 2 layers of firewall with redundancy
2 Cisco
2 Juniper
2 will face the internet and will be set in active/passive mode
the next 2 will face the first two and also will be set in active/passive mode
that will give 2 layers of firewall with redundancy
ASKER
ujitnos: thanks, great design that's what exactly i was hoping.
if i use Parameter Firewalls as JUNIPER and CORE Firewalls as CISCO
what kind of load balancer we can use and where it will be physically placed.
ArneLovius: i think there will be 4 Layer of NAT, what your experience say.
for VPN we can use any SSL VPN appliance like sonicwall in the DMZ , is it ok?
if i use Parameter Firewalls as JUNIPER and CORE Firewalls as CISCO
what kind of load balancer we can use and where it will be physically placed.
ArneLovius: i think there will be 4 Layer of NAT, what your experience say.
for VPN we can use any SSL VPN appliance like sonicwall in the DMZ , is it ok?
If you have two failover pairs, then you've only got a maximum of two layers of NAT, however, if one of your firewalls is either a transparent bridge or a router, then you would only have one layer of NAT. On the general principle that NAT is bad, I would always go for the minimum amount of NAT
You would probably terminate your VPN traffic on your external firewall, and then have it access the internal network through the internal firewall.
I would probably go for Cisco on the external side and use the Cisco Anyconnect client with RADIUS/LDAPS auth for remote access and run Juniper on the internal side. if you need NAT, I would run it on the external side. I wouldn't use Sonicwall.
You might also want to think about using IDS/IPS modules.
If both the Cisco and Juniper devices are each running as clusters (two Ciscos running as a cluster and two Junipers running as a cluster) then although you might need load balancers for internal application balancing, the firewalls won't require them.
You would probably terminate your VPN traffic on your external firewall, and then have it access the internal network through the internal firewall.
I would probably go for Cisco on the external side and use the Cisco Anyconnect client with RADIUS/LDAPS auth for remote access and run Juniper on the internal side. if you need NAT, I would run it on the external side. I wouldn't use Sonicwall.
You might also want to think about using IDS/IPS modules.
If both the Cisco and Juniper devices are each running as clusters (two Ciscos running as a cluster and two Junipers running as a cluster) then although you might need load balancers for internal application balancing, the firewalls won't require them.
ASKER
ArneLovius: what best places for a inline IPS and how many IDS you recommend to use (each IDS in each zone?)
where you guys RATE the design in PDF?
where you guys RATE the design in PDF?
What bandwidth and CPS are you looking at ?
Cisco ASA devices can do IPS (AIP module, but not on the 5550 or 5580 models).
I would probably run IDS on a monitor/span port between the external and internal firewalls
Post your PDF on here
Cisco ASA devices can do IPS (AIP module, but not on the 5550 or 5580 models).
I would probably run IDS on a monitor/span port between the external and internal firewalls
Post your PDF on here
ASKER
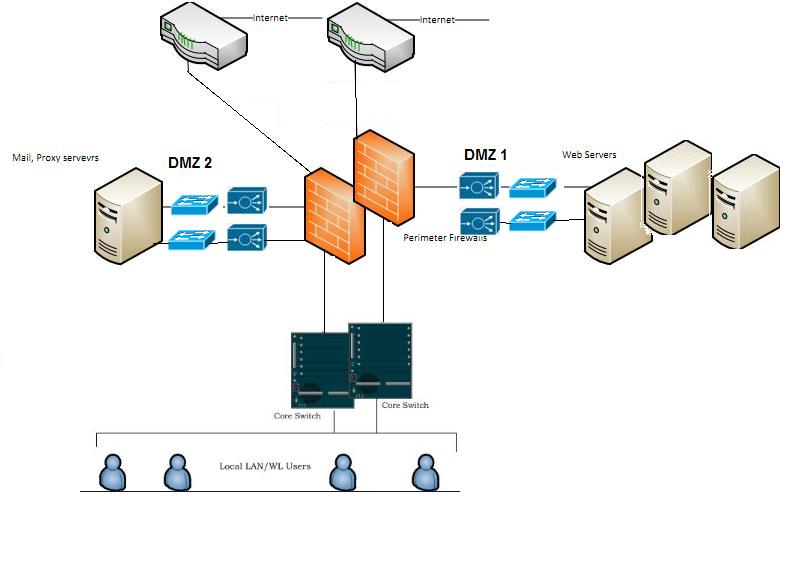
in above comments ujitnos: has posted Drawing1.pdf
presuming that you've have clustered switches as well as firewalls
Drawing1.jpg
Drawing1.jpg
ASKER
clustered switches before the firewall, how come? no router.
strange switches usage
strange switches usage
Dual diverse gig links with LACP, granted they go onto the same ISP core network, so if you want to add BGP to the mix, swap out the L2 switches for L3 ones.
So how would you design it ?
So how would you design it ?
only physical connections shown
dual-firewalls-2.jpg
dual-firewalls-2.jpg
ASKER
my point was that normally, a screening device is always either a Router or a Firewall, how far a Switch can be secured?
if you see the First Design from our friend "ujitnos:" this is what we mostly confront mostly.
i am just trying to digest the idea of using SWITCHES. you are the expert of it so might be able to give some more details on it.
thanks
if you see the First Design from our friend "ujitnos:" this is what we mostly confront mostly.
i am just trying to digest the idea of using SWITCHES. you are the expert of it so might be able to give some more details on it.
thanks
what do you need to secure on the switch ?
routers can have ACL capabilities, but they are designed to route packets, firewalls are designed to filter packets, if you're going to use a firewall to filter packets why use a router to do the same ?
if the switch is an L2 switch, then the VLAN that is used for the ISP connections wouldn't need or have an IP address. the only thing required to "secure it" would be to set the ports as "access" ports with only the native VLAN for the ISP connection allowed. Management can be either out of band over serial, or on a management VLAN with separate firewalls if required.
if the switch is a L3 switch, then you would need to configure an ACL on the management interface, but this is on the control-plane, not the data-plane so it is not applied to flows "through" the switch, just to connections to the management interface. Just as above management can be either out of band over serial, or on a management VLAN with separate firewalls if required.
routers can have ACL capabilities, but they are designed to route packets, firewalls are designed to filter packets, if you're going to use a firewall to filter packets why use a router to do the same ?
if the switch is an L2 switch, then the VLAN that is used for the ISP connections wouldn't need or have an IP address. the only thing required to "secure it" would be to set the ports as "access" ports with only the native VLAN for the ISP connection allowed. Management can be either out of band over serial, or on a management VLAN with separate firewalls if required.
if the switch is a L3 switch, then you would need to configure an ACL on the management interface, but this is on the control-plane, not the data-plane so it is not applied to flows "through" the switch, just to connections to the management interface. Just as above management can be either out of band over serial, or on a management VLAN with separate firewalls if required.
ASKER
Master ArneLovius: can you suggest some specific reading material on this Design
Go through the attached dig. This should be a good design to start with. The firewalls are in cluster and can be of any vendor of your specifications. Implement IPS on all important zones like web dmz zone etc.
You can create VLANs in the core switch to connect the devices, replacing the switches at interior level.
IT-Security---Network.jpg
You can create VLANs in the core switch to connect the devices, replacing the switches at interior level.
IT-Security---Network.jpg
@ujitnos nice picture!
@osloboy there is no specific materiel over such a conceptual design except to understand how switches can be clustered and how firewalls can be clustered to create a highly available design. When you start having layered firewalls and demilitarised zones and possibly bringing load balancers into the mix, then you need to understand the intricacies of how the individual parts work as well as how they will work as a whole.
That said, here are some links that may be useful to you
http://blog.ioshints.info/2011/02/how-did-we-ever-get-into-this-switching.html
http://codeidol.com/security/firewall/Where-Firewalls-Fit-in-a-Network/Dual-Firewall-Architecture/
http://www.cisco.com/en/US/products/ps6120/index.html
http://www.cisco.com/en/US/products/ps5729/Products_Sub_Category_Home.html
http://www.techrepublic.com/blog/networking/fundamentals-five-ways-to-secure-your-cisco-routers-and-switches/470
http://msdn.microsoft.com/en-us/library/ff648651.aspx
@osloboy there is no specific materiel over such a conceptual design except to understand how switches can be clustered and how firewalls can be clustered to create a highly available design. When you start having layered firewalls and demilitarised zones and possibly bringing load balancers into the mix, then you need to understand the intricacies of how the individual parts work as well as how they will work as a whole.
That said, here are some links that may be useful to you
http://blog.ioshints.info/2011/02/how-did-we-ever-get-into-this-switching.html
http://codeidol.com/security/firewall/Where-Firewalls-Fit-in-a-Network/Dual-Firewall-Architecture/
http://www.cisco.com/en/US/products/ps6120/index.html
http://www.cisco.com/en/US/products/ps5729/Products_Sub_Category_Home.html
http://www.techrepublic.com/blog/networking/fundamentals-five-ways-to-secure-your-cisco-routers-and-switches/470
http://msdn.microsoft.com/en-us/library/ff648651.aspx
ASKER
ujitnos:
great effort, thanks a lot.
Question as a Manager are below as
why to use 6 firewalls?
what about IPS? where to place them.
how to do Reverse Proxy in DMZ
great effort, thanks a lot.
Question as a Manager are below as
why to use 6 firewalls?
what about IPS? where to place them.
how to do Reverse Proxy in DMZ
In reality you can use just 4 firewalls (2 core - 2 perimeter), the other 2 firewalls is shown to be web application firewalls that can look into web application related attacks lke SQL Injection, cross-site scripting etc. which a normal firewall wont be able to do. If you have plans to place an IPS in the web server zone, then there is no need for this web application firewalls.
IPS/IDS can be placed to monitor traffic to your critical Zone. In case of web server zone you can go in for an host based IPS/IDS that will sit on each web server and look for malicious activity. I would not place the IPS/IDS just below my routers. Configure your firewalls to allow only specific ports from the internet to internal network. IPS/IDS can be placed as you have shown, except after router.
In your network diagram, you can configure the router in a cluster like your firewall, but can be in active-active mode with HSRP between them. Rest looks good. You can go in for just one IPS/IDS in the different zones. (if two icons in your diagram mean two IPS/IDS device)
You can use ISA for reverse proxy.
IPS/IDS can be placed to monitor traffic to your critical Zone. In case of web server zone you can go in for an host based IPS/IDS that will sit on each web server and look for malicious activity. I would not place the IPS/IDS just below my routers. Configure your firewalls to allow only specific ports from the internet to internal network. IPS/IDS can be placed as you have shown, except after router.
In your network diagram, you can configure the router in a cluster like your firewall, but can be in active-active mode with HSRP between them. Rest looks good. You can go in for just one IPS/IDS in the different zones. (if two icons in your diagram mean two IPS/IDS device)
You can use ISA for reverse proxy.
ASKER
IPS are only after the parameter Router as inline.
in DMZ1 , DMZ2,....... the pair of 2 devices each are LoadBalancers
do you think it is a good idea to use Loadbalancers with in the DMZ ?
should not use the loadbalancers after and before the external and internal firewalls? i.e total of 8 loadbalancsers
in DMZ1 , DMZ2,....... the pair of 2 devices each are LoadBalancers
do you think it is a good idea to use Loadbalancers with in the DMZ ?
should not use the loadbalancers after and before the external and internal firewalls? i.e total of 8 loadbalancsers
There is no need to use loadbalancers in the DMZ zones. You can configure your servers in cluster for high availability and load sharing.
But still u can go in load balancers for your web servers, for rest of servers like database and application servers u dont need a loadbalancer
But still u can go in load balancers for your web servers, for rest of servers like database and application servers u dont need a loadbalancer
ASKER
thanks, can you please provide any supporting document for your last comment
""""But still u can go in load balancers for your web servers, for rest of servers like database and application servers u dont need a loadbalancer"""""
2) if we are using LOAD BALANCER with 2 Switches, what kind of Load balacning it will be? L3 or ?
""""But still u can go in load balancers for your web servers, for rest of servers like database and application servers u dont need a loadbalancer"""""
2) if we are using LOAD BALANCER with 2 Switches, what kind of Load balacning it will be? L3 or ?
The only "load balancing" for the two switches is LACP.
You could use VRRP/HSRP to the "internal" switches if you want to them as the internal default gateway.
You could use VRRP/HSRP to the "internal" switches if you want to them as the internal default gateway.
ASKER
so its means it is useless to use Cisco LB (Load Balancer ACE 4700) with switches.
see i have received the above draft from one of consultant where he is using 2 Cisco LB with 2 switches for each 4 DMZs.
am trying to digest the idea, coz what i understand is the LB are old tech now.
please give me some solid points about why not using LB in each DMZ
see i have received the above draft from one of consultant where he is using 2 Cisco LB with 2 switches for each 4 DMZs.
am trying to digest the idea, coz what i understand is the LB are old tech now.
please give me some solid points about why not using LB in each DMZ
the load balancers are to distribute traffic across the servers
VRRP or HSRP on the L3 switches would be to have a common default gateway for outbound traffic
these are two different technologies for two different tasks
The Cisco ACE XML gateway is EOL but I think the 4710 is still current.
You might want to look at F5 as an alternative
VRRP or HSRP on the L3 switches would be to have a common default gateway for outbound traffic
these are two different technologies for two different tasks
The Cisco ACE XML gateway is EOL but I think the 4710 is still current.
You might want to look at F5 as an alternative
ASKER
except Traffic Distribution, do you see any Value added feature to use the LB (e.g any Security Feature , Reverse Proxy? etc)
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
thanks

as per ujitnos you would need a 3rd party load balancer in front of the firewalls and behind the firewalls, but this would not work for IPSec traffic.