DMZ IP Addressing
Hi All,
I'm in the middle of planning a new network infrastructure. Please see the attached diagram.
I'm not really sure how the IP Addressing in the DMZ should be. My internal LAN is on the 192.168.1.x/24 subnet. Within the DMZ area, should these IP Addresses be the public IP Addresses we were given from AT&T or should they be on a different private IP Subnet, such as 10.10.10.x/24?
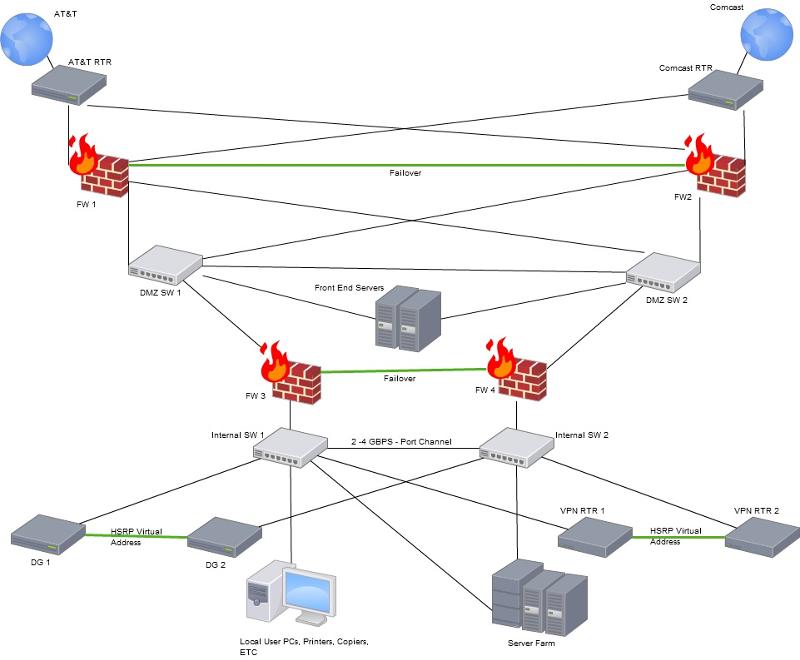
I'm in the middle of planning a new network infrastructure. Please see the attached diagram.
I'm not really sure how the IP Addressing in the DMZ should be. My internal LAN is on the 192.168.1.x/24 subnet. Within the DMZ area, should these IP Addresses be the public IP Addresses we were given from AT&T or should they be on a different private IP Subnet, such as 10.10.10.x/24?

Normally you give the DMZ a separate private range and do the NATting on the firewall(s).
I would agree with Erniebeek.. No reason to share the actual ip address of the server on the dmz with the public. Use a private block. What I normally do is use something different than my internal block so it sticks out at me. So since you are already using 192.168.x.x on the inside, use something from the 172.16 to 172.31 block on the DMZ.
ASKER
That is what I was thinking, but I have a follow up question to that. Within the DMZ, I plan to use a 10.10.10.x/24 IP subnet. NAT will be done on the firewalls (FW1 and FW2) so outside hosts can hit my front end servers, so if you look at my internal network you'll see VPN Routers. Hosts on the internet connecting to the VPN will have to go through two NATS, such as:
PUBLIC IP -------- 10.10.10.1/24 (NAT IP) ---------- 192.168.1.50 (VPN ROUTER)
So ultimately it's HOST to AT&T RTR to FW1 (NAT) to FW3 (another NAT) and then VPN Router. Is that a good idea, or is the double-NAT a problem?
PUBLIC IP -------- 10.10.10.1/24 (NAT IP) ---------- 192.168.1.50 (VPN ROUTER)
So ultimately it's HOST to AT&T RTR to FW1 (NAT) to FW3 (another NAT) and then VPN Router. Is that a good idea, or is the double-NAT a problem?
Is there a specific reason you use a separate VPN router? You could also terminate the VPN on a firewall (then there's only one NAT traversal).
Well it definitely adds to the complexity of the whole thing. The more complex things are translates into more time spent troubleshooting problems. I don't see why you have to NAT the VPN traffic until it exist the last firewall though. There is no reason to nat the vpn traffic at the first entry firewalls. I am assuming that these are ASA firewalls. Do you have any of the security modules in these ASA that you are trying to utilize in this?
ASKER
There is no specific reason to use a separate VPN router, I know the FW can do it, and most likely should.
How can I not NAT the VPN traffic at FW1? How will it pass through the FW1 unchanged?
I was thinking I'd have to setup a 1-1 static NAT on FW1 (public to 10.10.10.1/24), then have to do another NAT at FW3 (10.10.10.1/24 to 192.168.1.x/24).
How can I bypass the NAT on FW1 for VPN traffic?
How can I not NAT the VPN traffic at FW1? How will it pass through the FW1 unchanged?
I was thinking I'd have to setup a 1-1 static NAT on FW1 (public to 10.10.10.1/24), then have to do another NAT at FW3 (10.10.10.1/24 to 192.168.1.x/24).
How can I bypass the NAT on FW1 for VPN traffic?
Too many short forms used in question. When you post questions please use as littile short forms as possible. I think some of the short forms u used are your company specefic
ASKER
Macksm- I don't follow, what shortform did I use?
So the VPN traffic will go through FW3 or 4 before it goes through FW1 or 2. I would nat it at FW1 or 2 and let it pass through at FW3 or 4. So this sounds funny, but the way to let it go through without natting would be to set up a static nat for the networks. So in order not to nat - define a static nat. Its just that the static nat would look something like this:
static (inside,outisde) 192.168.255.0 192.168.255.0 netmask 255.255.255.0
This in essence says the address 192.168.255 on the inside network will also be known as 192.168.255 on the outside segment as well. You normally do this when you are allowing traffic inbound, but the statement works for traffic in both directions. Now having said that. That example line only applies to ASA 8.2.x and lower. It is different on 8.3 and above but I don't have that syntax in my head at the moment.
Now after re-reading through your statement I am not sure I completely understand what you are trying to accomplish. You said "So ultimately it's HOST to AT&T RTR to FW1 (NAT) to FW3 (another NAT) and then VPN Router. Is that a good idea, or is the double-NAT a problem?"
So is ATT the internet here? wait now i understand where you are going here. So a vpn user on the internet needs to terminate the VPN on the vpn router that is two firewalls deep in your network.
Ok if that is correct I get it now.
The deal here is I would do one of 2 things.
#1) Move the VPN router so they have an inside and outside connection. The outside connection will get a straight public ip address and be on the same segment as the outside of FW#1. The inside can do 1 of 2 things. It can either connect directly to the inside of your network so it would be in parallel with the FW1 &2, or you could take the inside of the dmz routers and put them on a new vpn-dmz segment which would connect to FW3&4. This way the vpn clients connect directly to the vpn router, they then are sent through the FW3&4 before hitting your inside network giving you a bit more protections since the traffic will be unencrypted by the time it hits FW3&4.
#2) Terminate VPN on the ASA instead of vpn routers. This really depends on a lot more info. Are these ipsec vpns, are they GRE, are they DMVPN? This factors in heavily in this decision.
Another thing to do would be to re-do the whole deal and collapse it to two firewalls. Have 4 really isn't doing much for you other than adding to the complexity. You can still have all of the security of your DMZ without having all traffic going to and from the internet having to cross the dmz segment.
static (inside,outisde) 192.168.255.0 192.168.255.0 netmask 255.255.255.0
This in essence says the address 192.168.255 on the inside network will also be known as 192.168.255 on the outside segment as well. You normally do this when you are allowing traffic inbound, but the statement works for traffic in both directions. Now having said that. That example line only applies to ASA 8.2.x and lower. It is different on 8.3 and above but I don't have that syntax in my head at the moment.
Now after re-reading through your statement I am not sure I completely understand what you are trying to accomplish. You said "So ultimately it's HOST to AT&T RTR to FW1 (NAT) to FW3 (another NAT) and then VPN Router. Is that a good idea, or is the double-NAT a problem?"
So is ATT the internet here? wait now i understand where you are going here. So a vpn user on the internet needs to terminate the VPN on the vpn router that is two firewalls deep in your network.
Ok if that is correct I get it now.
The deal here is I would do one of 2 things.
#1) Move the VPN router so they have an inside and outside connection. The outside connection will get a straight public ip address and be on the same segment as the outside of FW#1. The inside can do 1 of 2 things. It can either connect directly to the inside of your network so it would be in parallel with the FW1 &2, or you could take the inside of the dmz routers and put them on a new vpn-dmz segment which would connect to FW3&4. This way the vpn clients connect directly to the vpn router, they then are sent through the FW3&4 before hitting your inside network giving you a bit more protections since the traffic will be unencrypted by the time it hits FW3&4.
#2) Terminate VPN on the ASA instead of vpn routers. This really depends on a lot more info. Are these ipsec vpns, are they GRE, are they DMVPN? This factors in heavily in this decision.
Another thing to do would be to re-do the whole deal and collapse it to two firewalls. Have 4 really isn't doing much for you other than adding to the complexity. You can still have all of the security of your DMZ without having all traffic going to and from the internet having to cross the dmz segment.
ASKER
kenboonejr,
I think you are on the right track.
I don't want to NAT 2x, however I wasn't sure that putting my VPN router outside the internal network was a good idea.
I think what I'll do is add two switches before FW1 and FW2 so that I can get the VPN routers at the same level the FW1 and FW2 are on. The VPN routers will get a public IP, the other interface on each will get a private 192.168.1.x IP. That is how it is right now, but I wasn't sure if I should change that.
I think you are on the right track.
I don't want to NAT 2x, however I wasn't sure that putting my VPN router outside the internal network was a good idea.
I think what I'll do is add two switches before FW1 and FW2 so that I can get the VPN routers at the same level the FW1 and FW2 are on. The VPN routers will get a public IP, the other interface on each will get a private 192.168.1.x IP. That is how it is right now, but I wasn't sure if I should change that.
Yea so you just need to lock down those vpn routers. Not sure if this is client vpn or lan to lan vpn tunnels you have here, but you will want to lock them down so that only vpn related protocols are entering this router from the outside. Make sure the vty ports are not accessible to the outside, etc..
ASKER
Yes, currently no VTY lines are accessible unless it is from our private LAN.
The VPNs are both site-to-site VPNs as well as client-to-site vpn.
I'm going to post an updated net doc with the VPN router changes. After reviewing the document, I realized the items that were supposed to be in the DMZ are not needed any longer. So the DMZ will be removed.
The VPNs are both site-to-site VPNs as well as client-to-site vpn.
I'm going to post an updated net doc with the VPN router changes. After reviewing the document, I realized the items that were supposed to be in the DMZ are not needed any longer. So the DMZ will be removed.
ASKER
Hello again.
I was working on the network diagram, but came across some issues. If I move the two VPN routers to be parallel to FW1 and FW2, then I cannot do VPN redundancy (HSRP/GLBP/VRRP). I cannot do that because the two VPN routers will be in different IP subnets (different ISP). Do you have any suggestions?
I was working on the network diagram, but came across some issues. If I move the two VPN routers to be parallel to FW1 and FW2, then I cannot do VPN redundancy (HSRP/GLBP/VRRP). I cannot do that because the two VPN routers will be in different IP subnets (different ISP). Do you have any suggestions?
So are you not using BGP between the ISPs and advertising the same subnets out both providers?
ASKER
Hi Ken,
I'm not doing anything right now. I need to plan this upgrade carefully. From everything I'm reading, it looks like I'll need BGP.
I would like to cut any possibility of downtime. That means everything in the network needs redundancy. I'm not sure how to do that in some cases. For example, a router cannot connect two of it's interfaces on the same ip subnet.... So I'm not sure what to do there.
Also, inbound connections to the front-end servers, and vpn routers, cannot be interrupted if either ISP fail.
is BGP my only option?
I'm not doing anything right now. I need to plan this upgrade carefully. From everything I'm reading, it looks like I'll need BGP.
I would like to cut any possibility of downtime. That means everything in the network needs redundancy. I'm not sure how to do that in some cases. For example, a router cannot connect two of it's interfaces on the same ip subnet.... So I'm not sure what to do there.
Also, inbound connections to the front-end servers, and vpn routers, cannot be interrupted if either ISP fail.
is BGP my only option?
Well normally you would run BGP and advertise one subnet out both of the ISPs. So now there is one block of public IP addresses that can take either path outbound. Your outside firewalls would then connect to the same networks, i.e. inside, outside and dmz.
You could put the VPN routers on a vpn-dmz off of the firewalls as well. so they would connect to the outside segment and the vpn-dmz segment on the firewall. You would still have the redundancy you want.
You could put the VPN routers on a vpn-dmz off of the firewalls as well. so they would connect to the outside segment and the vpn-dmz segment on the firewall. You would still have the redundancy you want.
ASKER
advertising one subnet to both ISPs? Won't that cause some routing problems? If ISP-A is on the 10.20.30.0/24 network and the ISP-B is on 124.12.13.0/24, that won't cause problems advertising the two subnets to both ISPs?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Great. So that will give redundancy to all my publicly accessible servers without having to translate multiple public IPs to single internal. Sounds like what I need.
Thanks,
Thanks,